Cloud identification method for abnormal behaviors of Internet of Things equipment
An Internet of Things device and identification method technology, which is applied in the field of cloud identification of abnormal behavior of Internet of Things devices, can solve problems such as the difficulty of security analysis programs, and achieve the effects of reducing preliminary preparation work, facilitating calls, and reducing false positives and missed negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
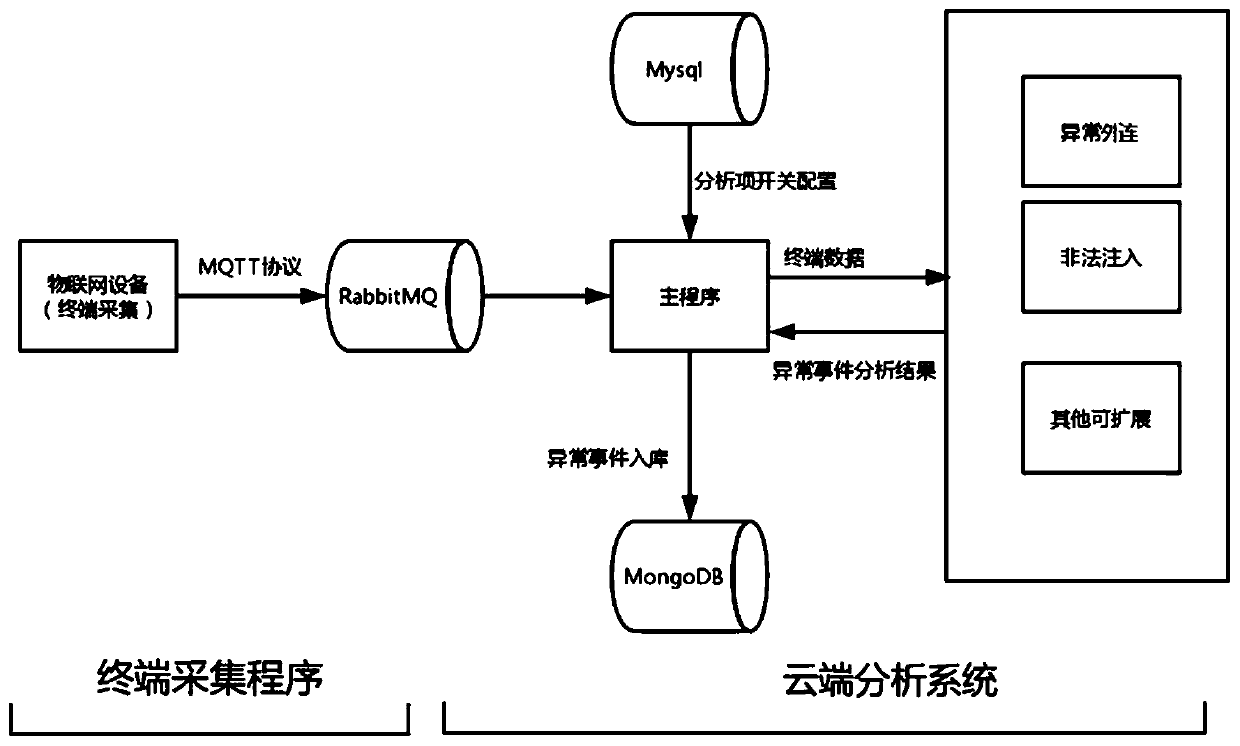
[0045] combined with figure 1 As shown, a cloud-based identification method for abnormal behavior of IoT devices uses terminal data collection and cloud threat analysis decoupling and analysis program modularization to solve the problem of continuous security protection for various IoT devices. It mainly includes IoT terminal operation service for status information collection, IoT terminal using mqtt protocol for status information transmission, cloud using RabbitMQ to add components to support mqtt protocol for data reception, cloud using sub-module program for threat analysis, cloud analysis sub-module (abnormal External links, botnets, illegal injection, and other scalable) analysis rules and cloud analysis results are regularly stored in the database.
[0046] Specifically include:
[0047] 1. Terminal data collection
[0048] The terminal agent adopts the form of Android Service, which performs periodic data collection as the background service of the Android terminal....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com