A BLE Bluetooth communication data encryption method, terminal and system
A technology of data encryption and Bluetooth communication, which is applied in digital transmission systems, wireless communications, transmission systems, etc., and can solve problems such as data capture and brute force cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
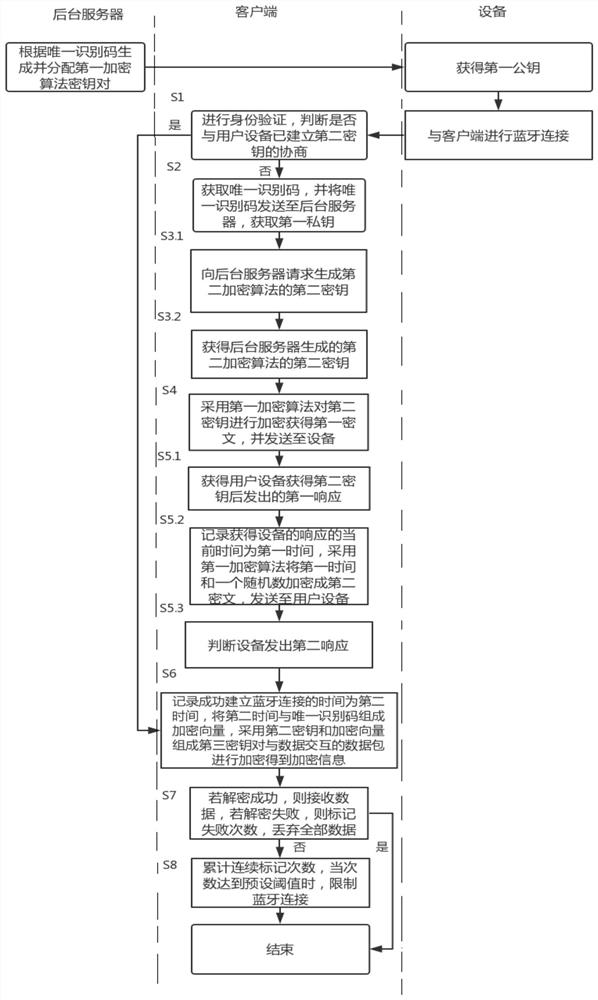
[0051] Such as figure 1 Shown, a kind of bluetooth communication data encryption method of BLE, this method comprises the following steps:
[0052] Step S1: Make a Bluetooth connection with the user equipment 7, and perform identity verification, and judge whether the negotiation of the second key has been established, if yes, execute step S6, and if not, execute step S2.
[0053] Specifically, the client 6 and the user equipment 7 need to establish the negotiation of the second key to complete the sending of the second key and the calibration of the time of the user equipment 7; Connection or the first Bluetooth connection with the client 6 after the user resets the user equipment 7 to factory settings, the client 6 needs to redistribute the second key to the user equipment 7 and calibrate the time of the user equipment 7.
[0054] Step S2: Obtain the unique identification code of the user equipment 7 through the Bluetooth broadcast, and send the unique identification code t...
Embodiment 2
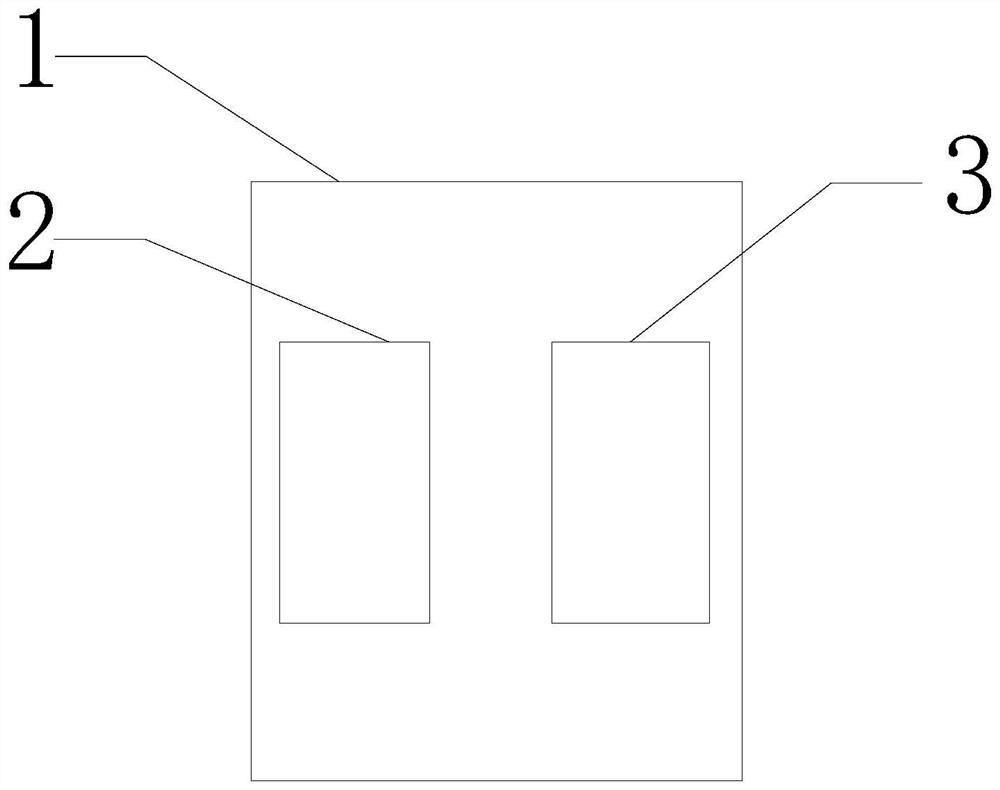
[0070] Such as figure 2 As shown, a Bluetooth communication data encryption terminal 1 of BLE includes:
[0071] Memory 2, used to store program instructions;
[0072] The processor 3 is configured to run the program instructions to execute the steps described in the first embodiment.
Embodiment 3
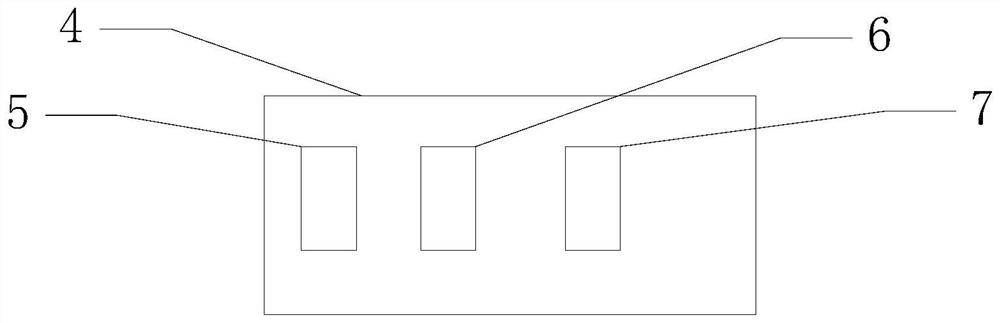
[0074] Such as image 3 Shown, a kind of bluetooth communication data encryption system 4 of BLE, described system comprises: background server 5, client 6 and user equipment 7;
[0075] The background server 5 is used to obtain the unique identification code of the user equipment 7, generate the first key pair of the first encryption algorithm, and save the first private key in the first key pair in the database, and store the first key pair in the database. The first public key in the key pair is distributed in the user equipment 7, and the unique identification code issued by the client 6 is obtained, and the first private key corresponding to the unique identification code in the database is sent to the client 6, and the client 6 is obtained. The request for generating the second key of the second encryption algorithm is sent, and the second key of the second encryption algorithm is generated and sent to the client 6;
[0076]The client 6 is used to carry out Bluetooth co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com