Man-machine interaction application method in cryptology field based on contact connection control instruction
A technology of control instructions and human-computer interaction, applied to encryption devices with shift registers/memory, key distribution, can solve the problems of difficulty in protection, long passwords, and high input time cost, and reduce the number of deciphered. risk, increase the strength of the password, improve the effectiveness of the protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
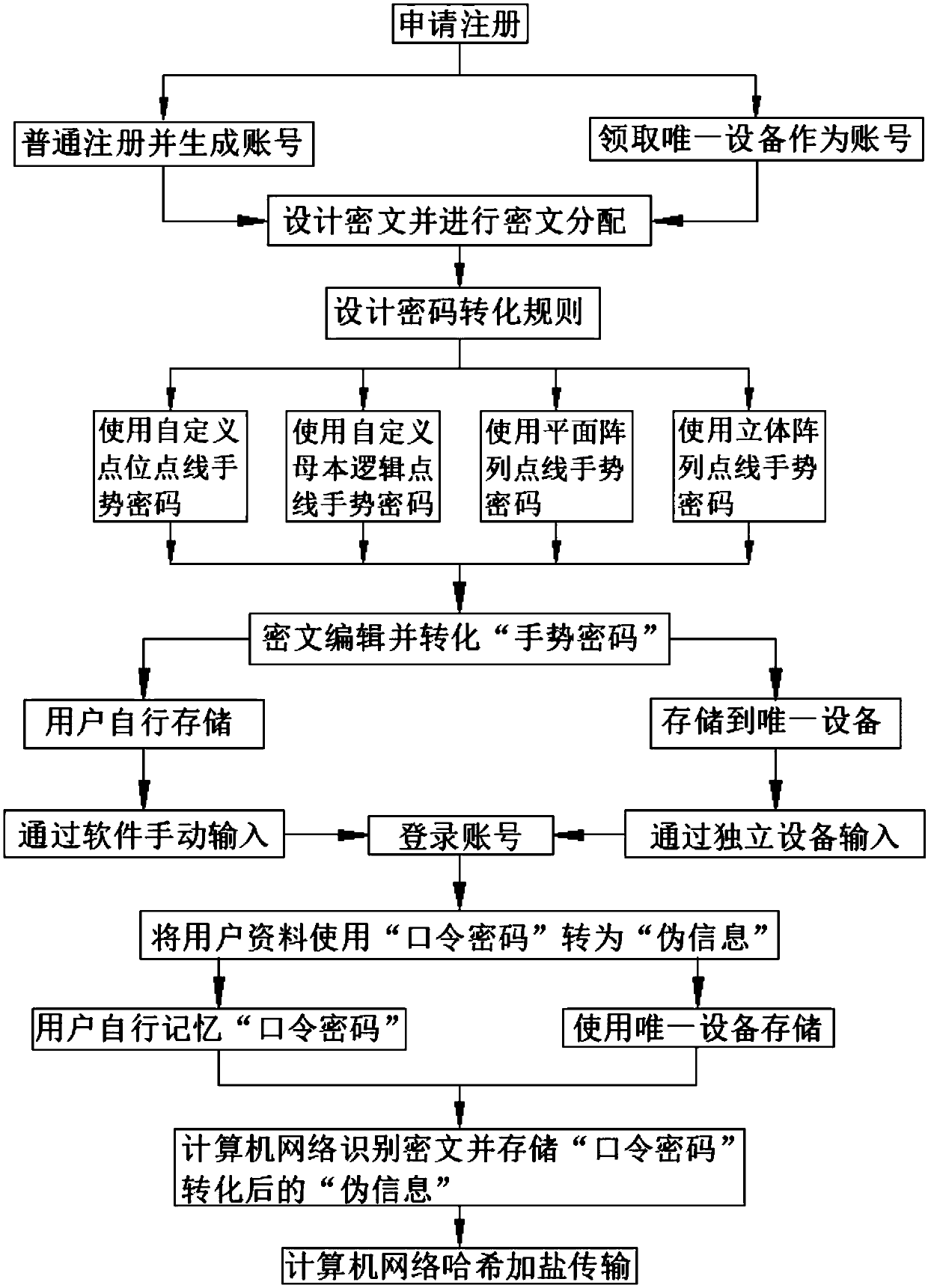
[0036] see figure 1 , figure 2 , image 3 , Figure 4 with Figure 5 , the present invention provides a technical solution: a human-computer interaction application method in the field of cryptography based on contact connection control instructions, comprising the following steps:
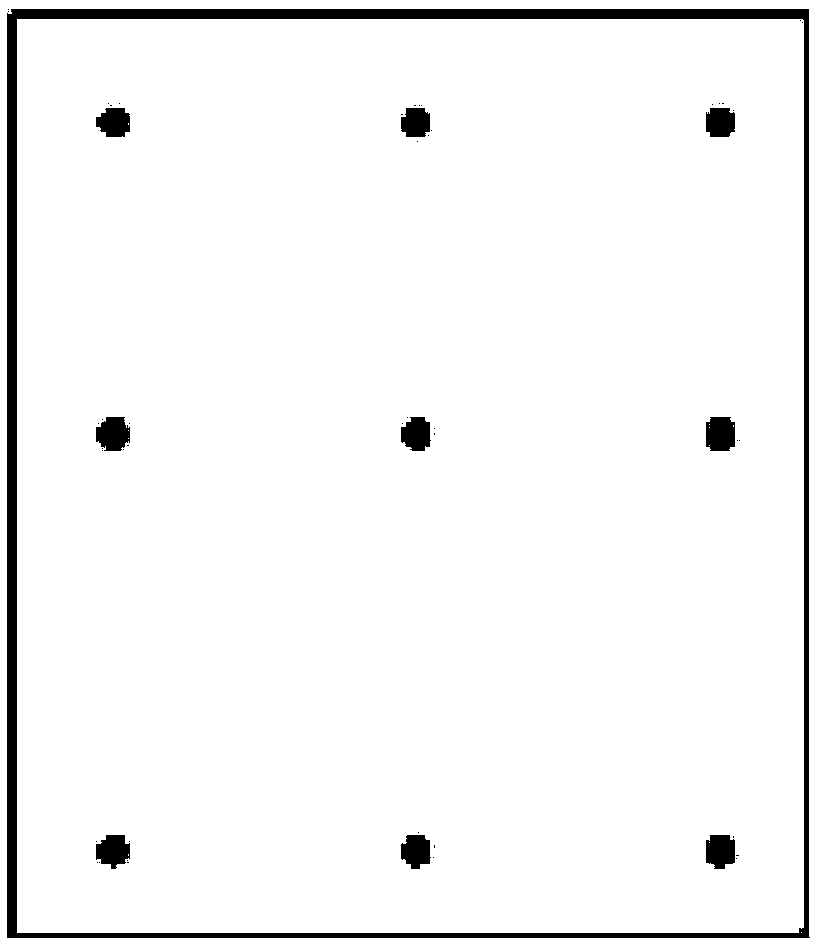
[0037] In order to facilitate the use of ordinary security level users, through the point and line command method, users can directly use the designed "custom point point point line gesture password", the password possibility is: 9 kinds of characters^9 dot matrix sequences^9 The combination of points and lines to the power of 1.9662705047555291361807590852691e+77 is the possibility of this super large value.
[0038] Step 1: Log in to the platform through the network, register and receive the "unique terminal device" according to the rules, and the "unique terminal device" is used as the only login account and password input device;
[0039] Step 2: Start the user's "unique terminal device"...
Embodiment 2
[0052] see figure 1 , figure 2 , image 3 , Image 6 , Figure 7 with Figure 8 , a human-computer interaction application method in the field of cryptography based on a contact connection control instruction, comprising the following steps:
[0053] In order to facilitate the use of users with a higher security level, users can use the "custom parent logical point-line gesture password" through the command method of point and line. The possibility of forming a password is: 70 kinds of characters^9 dot matrix sequences^9 The dot-line combination of power may=2.8375350918001070782446106276312e+149 super large number possibility password.
[0054] Step 1: Log in to the platform through the network, register and receive the "unique terminal device" according to the rules, and the "unique terminal device" is used as the only login account and password input device;
[0055] Step 2: Start the user's "unique terminal device" to connect to the smart device or computer, and ope...
Embodiment 3
[0069] see figure 1 , figure 2 , image 3 , Figure 9 with Figure 10 , a human-computer interaction application method in the field of cryptography based on a contact connection control instruction, comprising the following steps:
[0070] In order to better improve the user's security level, the user can use the "plane array dot-line gesture password", and the possibility of forming the password is: 70 kinds of characters^81-bit password^9 dot matrix sequences^9 dotted lines Combination possibility = a super strong password for a super large number (which cannot be calculated by the computer's built-in calculator).
[0071] Step 1: Log in to the platform through the network, register and receive the "unique terminal device" according to the rules, and the "unique terminal device" is used as the only login account and password input device;
[0072] Step 2: Start the user's "unique terminal device" to connect to the smart device or computer, and open the platform throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com