Malicious software assembly format detection method based on deep learning
A malware and detection method technology, applied in neural learning methods, computer components, character and pattern recognition, etc., can solve the problems of low detection accuracy, achieve good detection results, improve detection accuracy, good applicability and accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings.
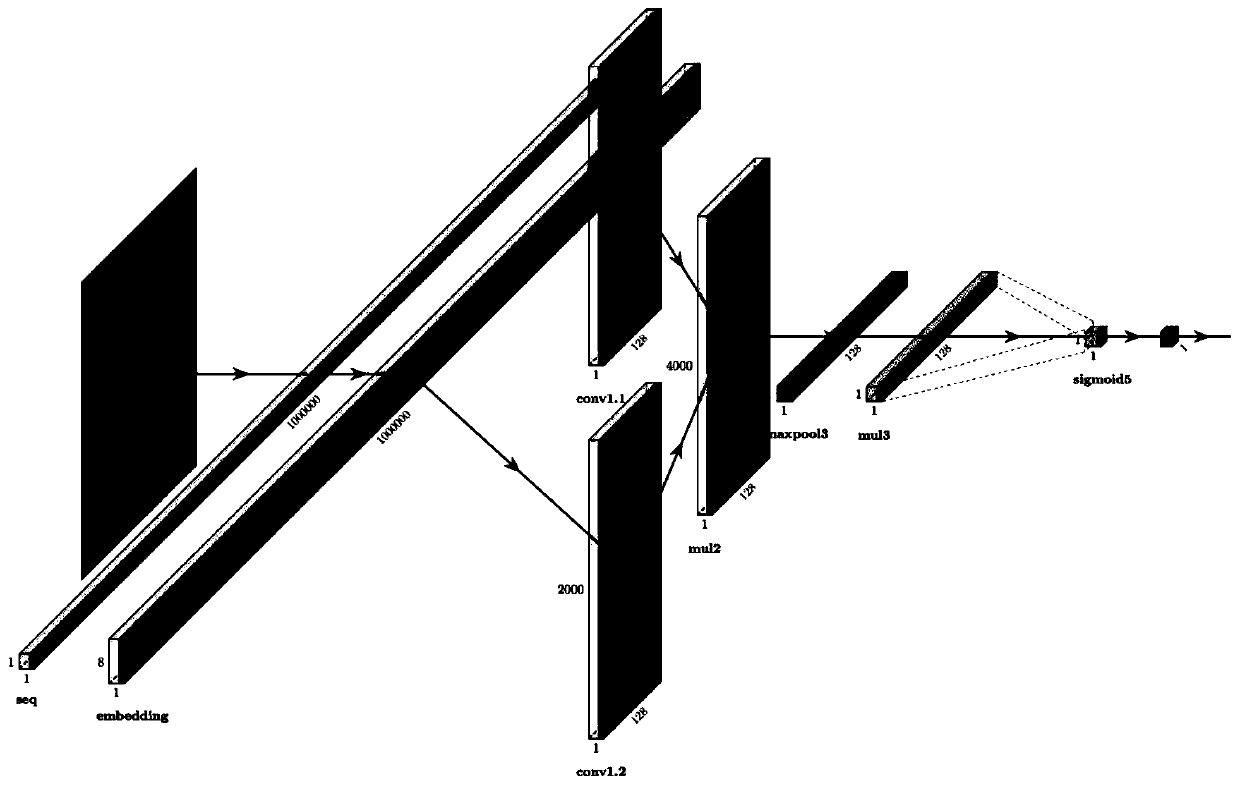
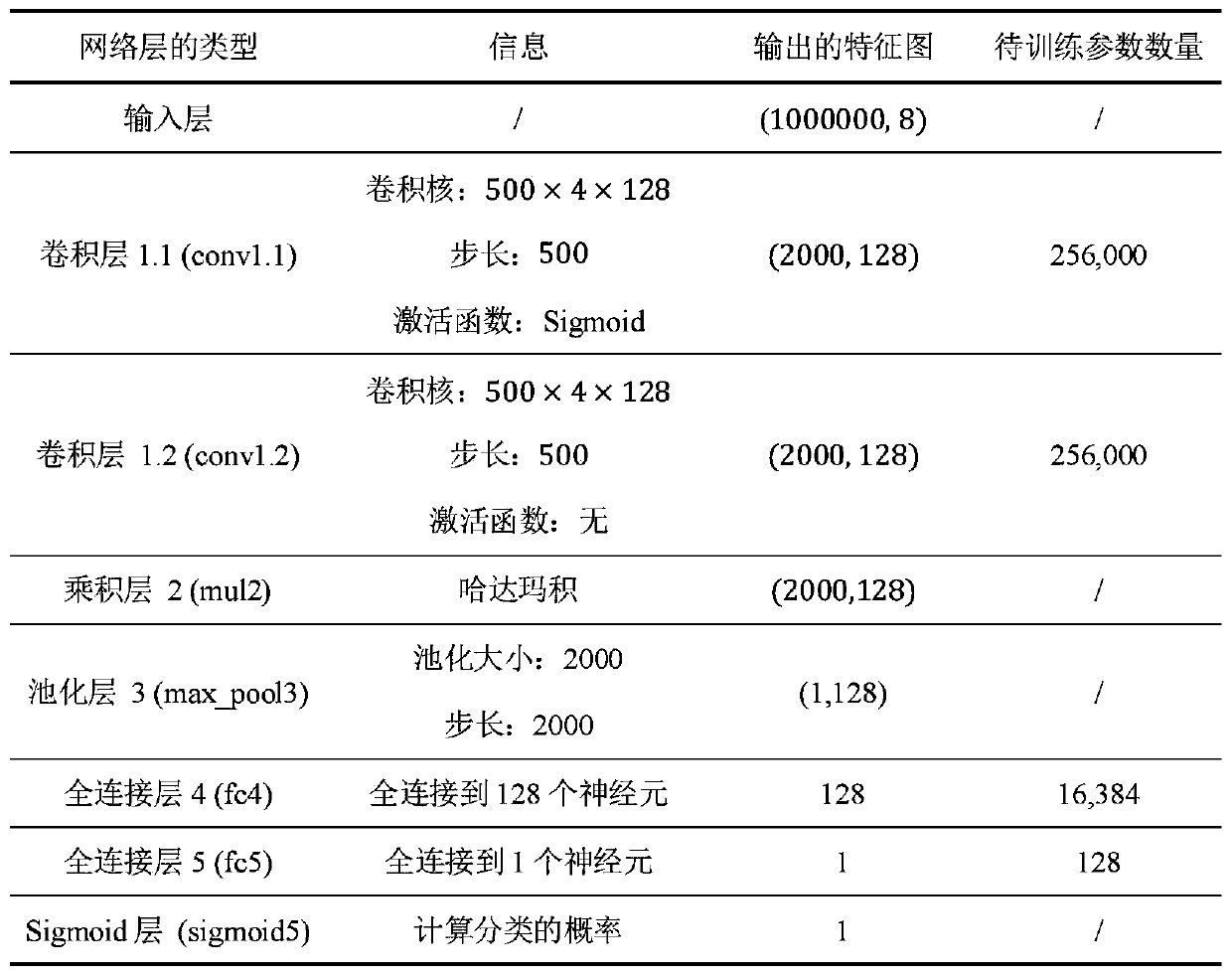
[0027] refer to Figure 1 to Figure 3 , a deep learning-based detection method for malware assembly format, comprising the following steps:
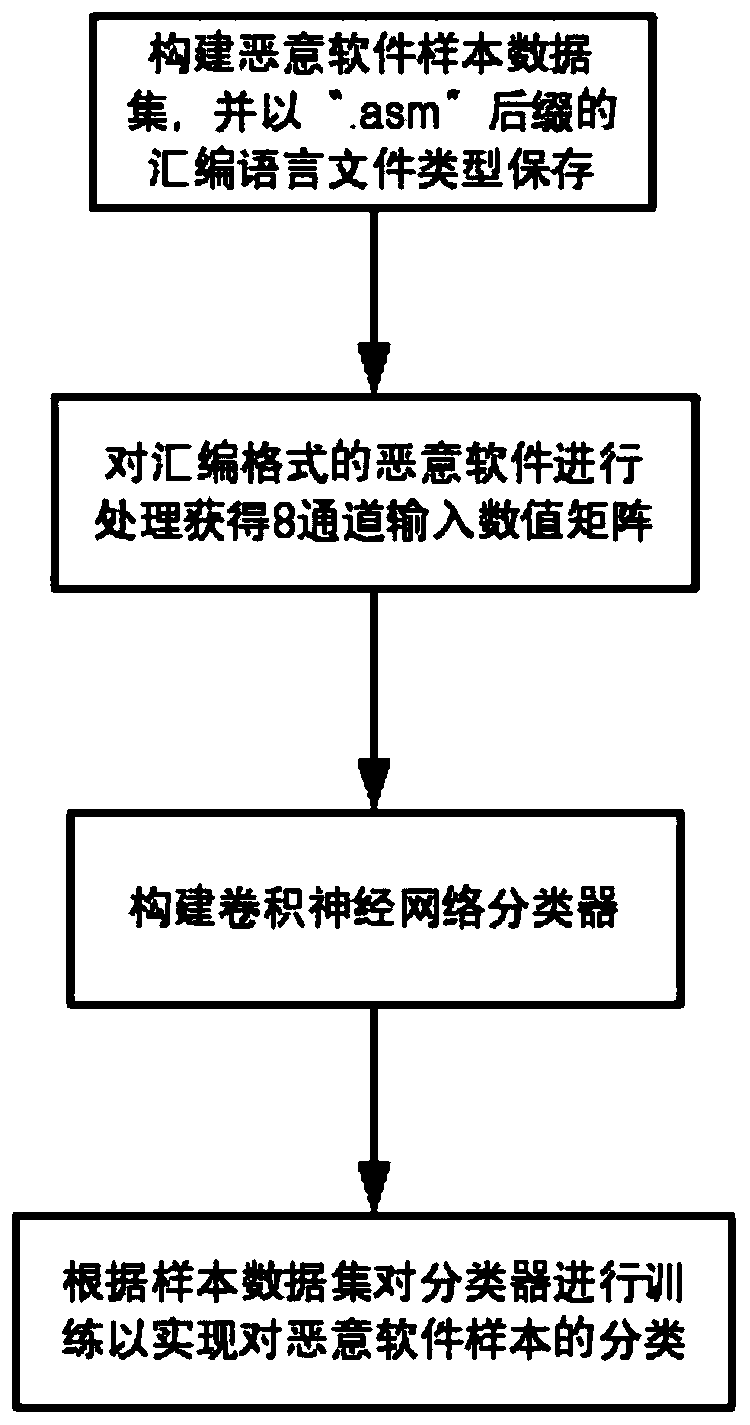
[0028] 1) Construct a dataset of malware samples. The process is as follows:
[0029] 1.1) Collect sample data sets of each malware family, and save the data in the assembly language file type with the ".asm" suffix;
[0030] Malware in assembly language, where each character is a letter or a number, can also be mapped to a number using ASCII to convert the text into a long array. Since a lot of key information is likely to be lost by cutting and splicing the converted array into a picture, it is considered to directly perform text analysis on the original file in the malware assembly language format.
[0031] 1.2) Considering the difference in the number of samples of each category and for the convenience of subsequent work,...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap