An information security evaluation method, device and computer based on multi-factor authentication
An information security, multi-factor technology, applied in the direction of computing, data processing applications, instruments, etc., can solve problems such as inconsistent plans, non-standard security evaluation, incomplete evidence collection data, etc., to enhance non-repudiation, save manpower products, and guarantee authenticity effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below in conjunction with the accompanying drawings and examples, but the present invention is not limited in any way. Any changes or improvements made based on the teaching of the present invention belong to the protection scope of the present invention.
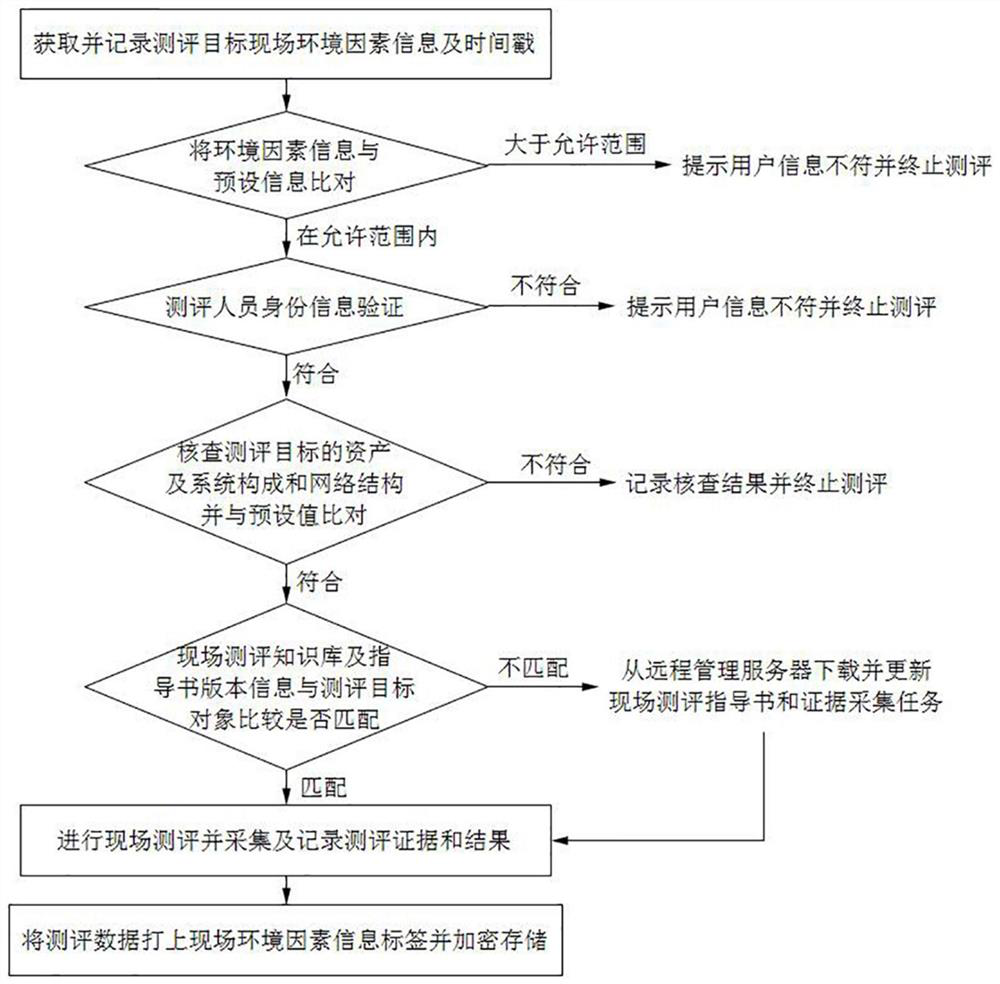
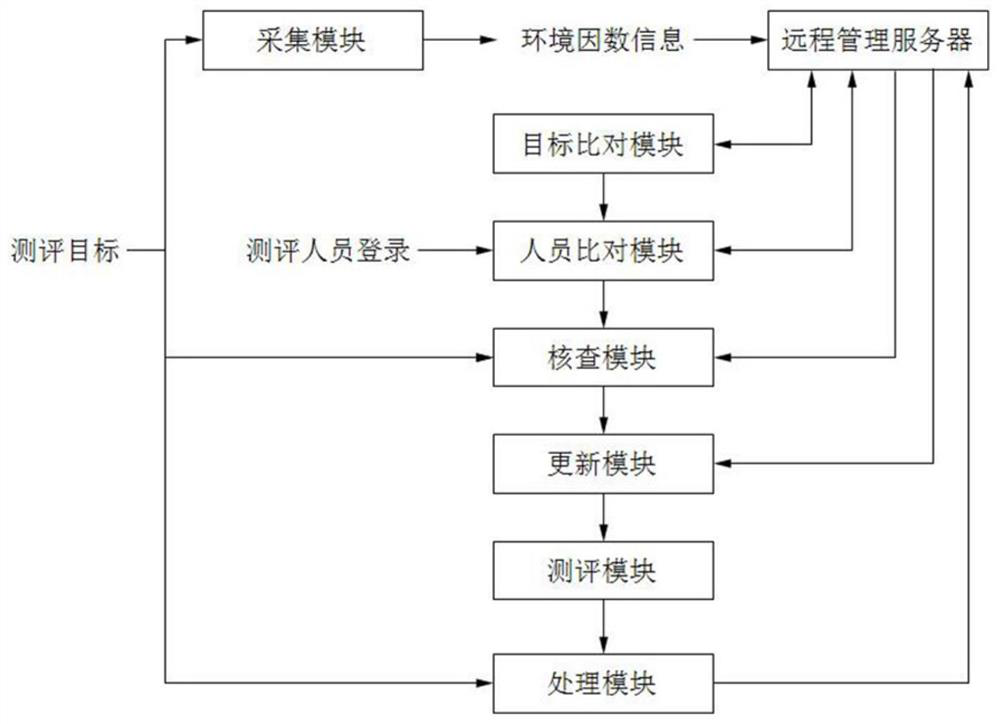
[0019] Such as figure 1 As shown, the information security evaluation method based on multi-factor verification of the present invention is characterized in that it includes collection, target comparison, personnel comparison, verification, update, evaluation, and processing steps, specifically including:
[0020] A. Collection: Obtain the on-site environmental factor information of the evaluation target, and record the acquired information and time stamp on the on-site and remote management servers;
[0021] B. Target comparison: compare the evaluation target environmental factor information obtained on site with the preset environmental factor information on the remot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com