SM2 elliptic curve public key cryptosystem optimization method
A public key cryptosystem and optimization method technology, applied in the field of SM2 elliptic curve public key cryptosystem optimization, can solve problems such as complex mathematical operations and complex implementation of optimization techniques, and achieve the effects of improving multiplication efficiency, improving efficiency, and easy reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings, but the present invention is not limited to these embodiments.
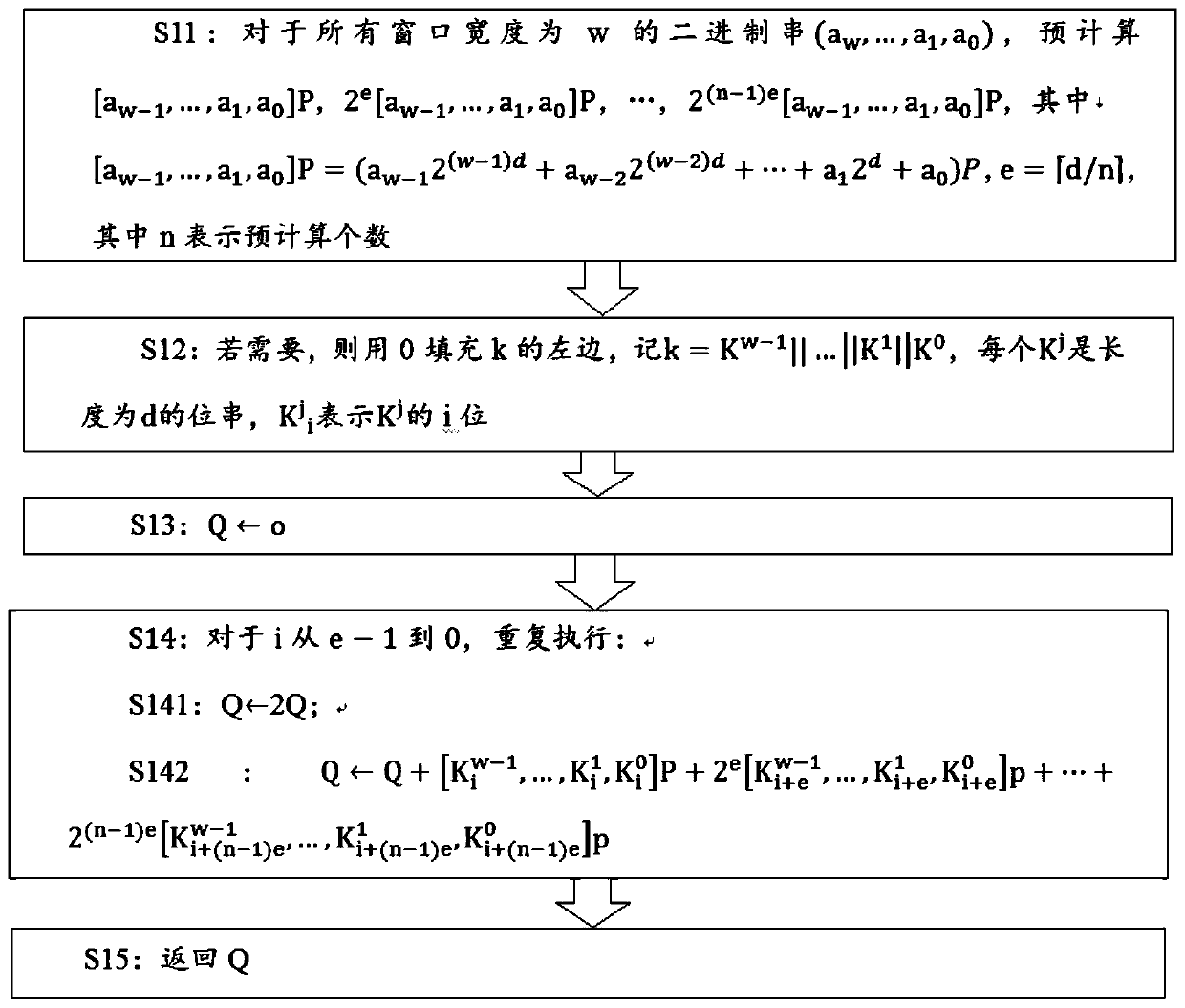
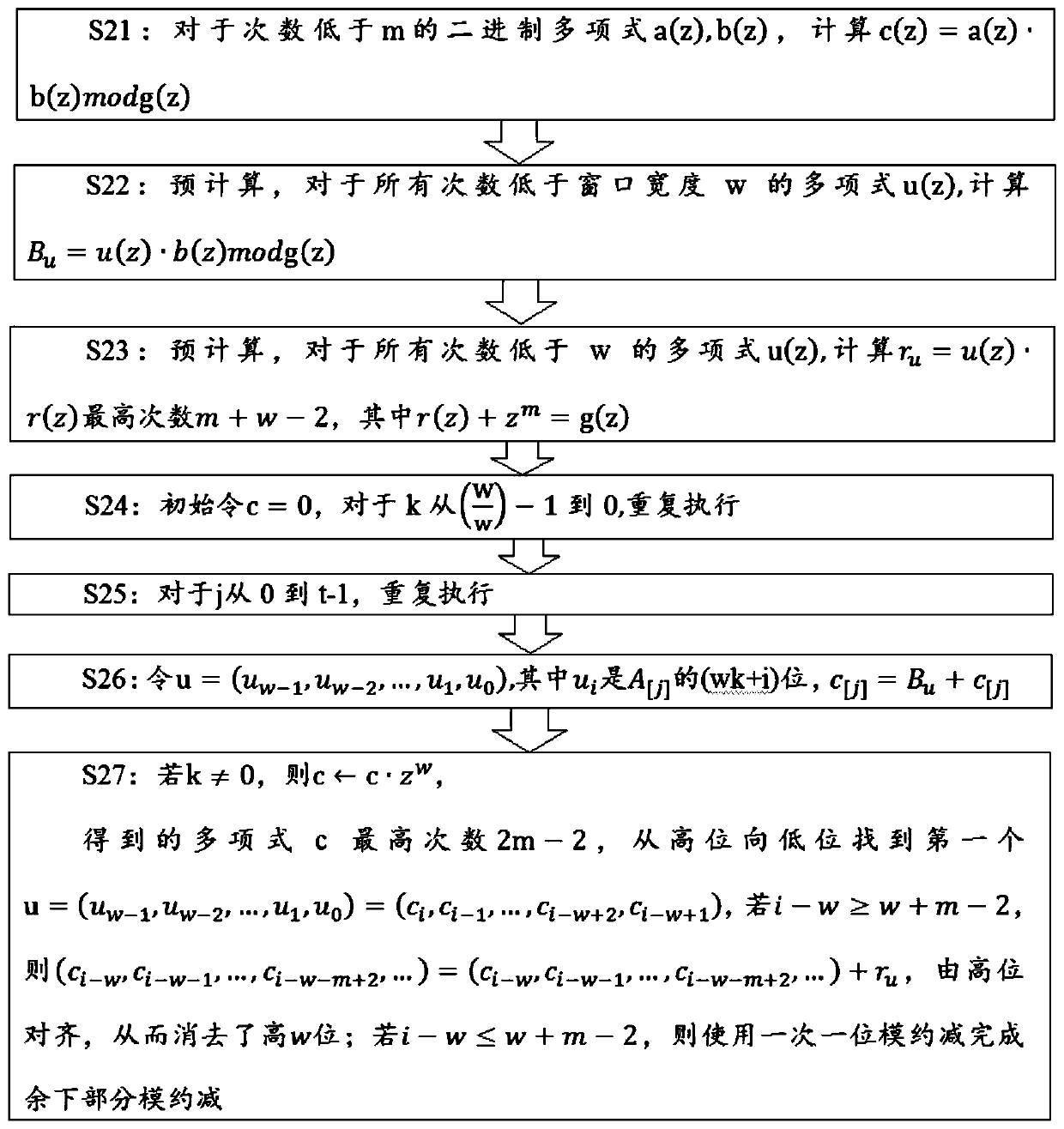
[0038] The basic idea of the embodiment of the present invention is to optimize the fixed-point multi-point operation in the SM2 digital signature algorithm by using the comb algorithm of two pre-stored tables; for the fixed-point multi-point operation in the SM2 public key encryption algorithm, use two Optimize the comb algorithm of a pre-stored table; for E(GF 2 m) The unfixed point multi-point operation on the curve is optimized by using the multi-point Montgomery method; for E(GF p ) unfixed point multi-point operation on the curve, using the projective coordinate algorithm for optimization. The invention improves the operation efficiency by optimizing the algorithm, and optimizes the performances of digital signature, key exchange and data encryption.
[0039] Based on th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com