Time domain-based encryption and strategy updating method for edge environment
An encryption method and time domain technology, applied in the field of ciphertext policy attribute base encryption method and policy update field, can solve the problems of system crash and long distribution time for obtaining a private key, and achieve the effect of reducing computational pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
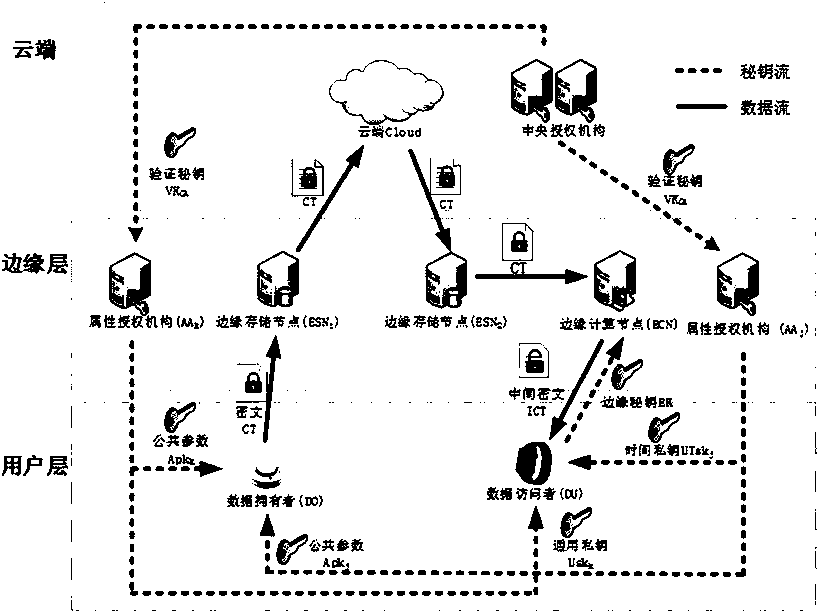
[0080] Such as figure 1 As shown, the components of the present invention include:
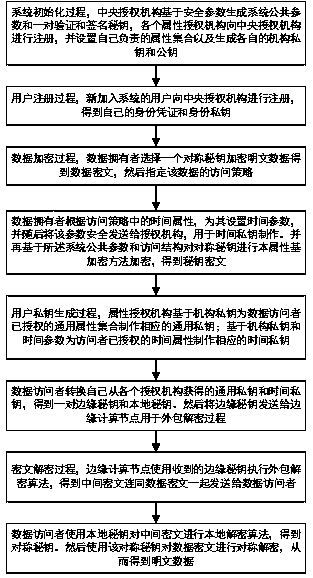
[0081] Central Authority (CA): CA is a trusted participant. It is not responsible for distributing any attribute public and private keys, but only responsible for the setting of system public parameters and the registration of users and attribute authorities.
[0082] Cloud: Cloud provides the function of permanently storing the ciphertext for all users in the system, and is also responsible for distributing the updated secret key of the old ciphertext to all storage nodes that have cached the old ciphertext. In this patent, it is assumed that it is semi-honest, that is, it will correctly execute the request sent by the user or edge node, but will be curious about the content of the user's stored information.
[0083] Attribute Authority (AA): Each AA will be assigned a set of attributes in its domain. These attributes can exist in two states, general attributes and time attributes. AA is responsib...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com