User key generation method and device, equipment and storage medium
A key generation and user key technology, applied in the field of computer communication and information security, can solve problems such as hidden dangers of user information security, cumbersome process of requesting verification of user identity, etc., and achieve the effect of improving reliability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
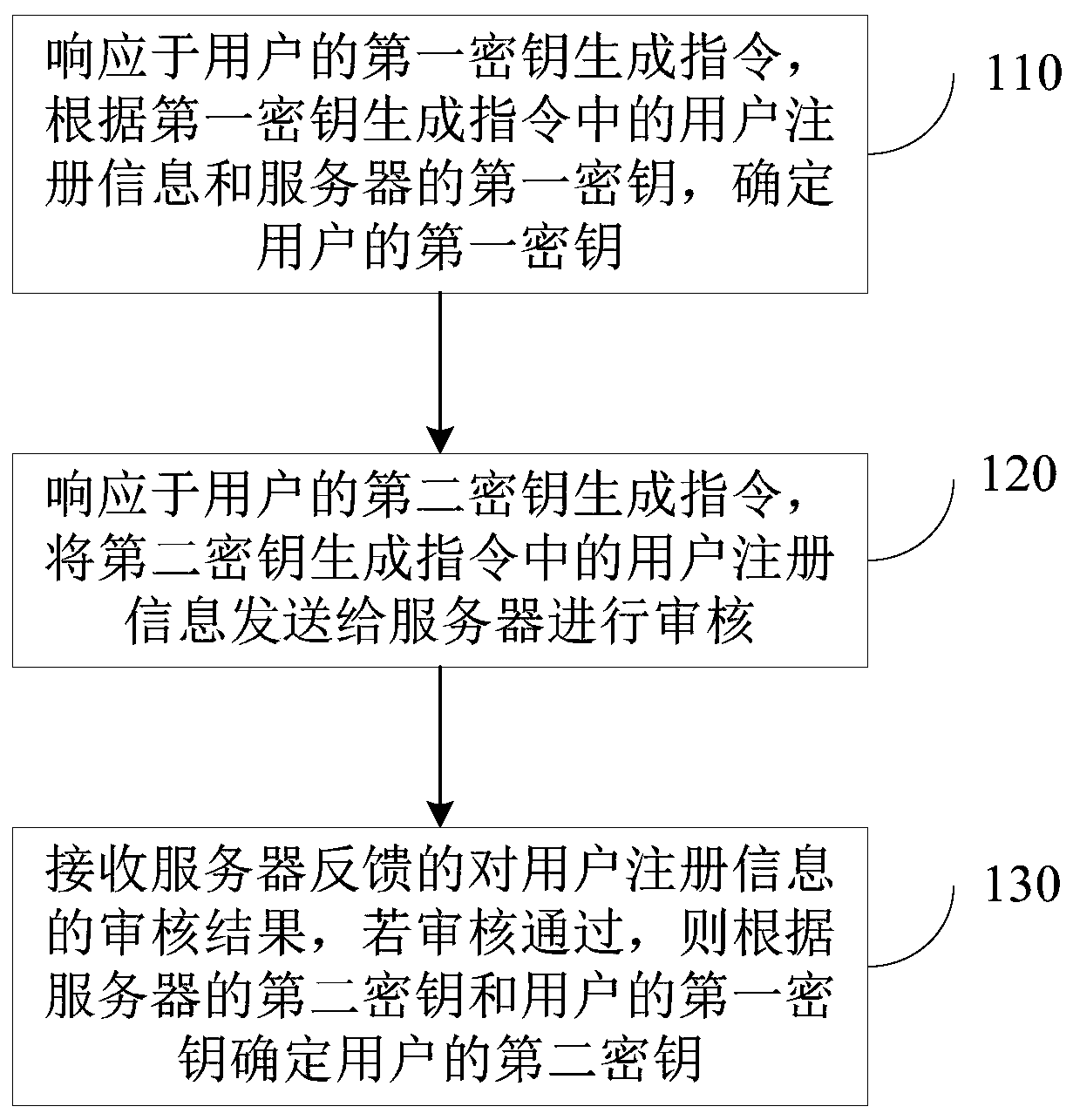
[0042] figure 1 It is a schematic flowchart of a method for generating a user key provided in Embodiment 1 of the present invention. This embodiment is applicable to the case of generating a key, and the method can be executed by a user key generating device configured in a key parser . Such as figure 1 As shown, the method specifically includes the following steps:
[0043] Step 110: In response to the user's first key generation instruction, determine the user's first key according to the user registration information in the first key generation instruction and the server's first key.
[0044] Wherein, the user registers the user on the application side, and saves the user registration information in the server, wherein the user registration information may include a user account number and a user password. The key resolver responds to the first key generation instruction issued by the user on the application side, obtains the user registration information and the server'...
Embodiment 2
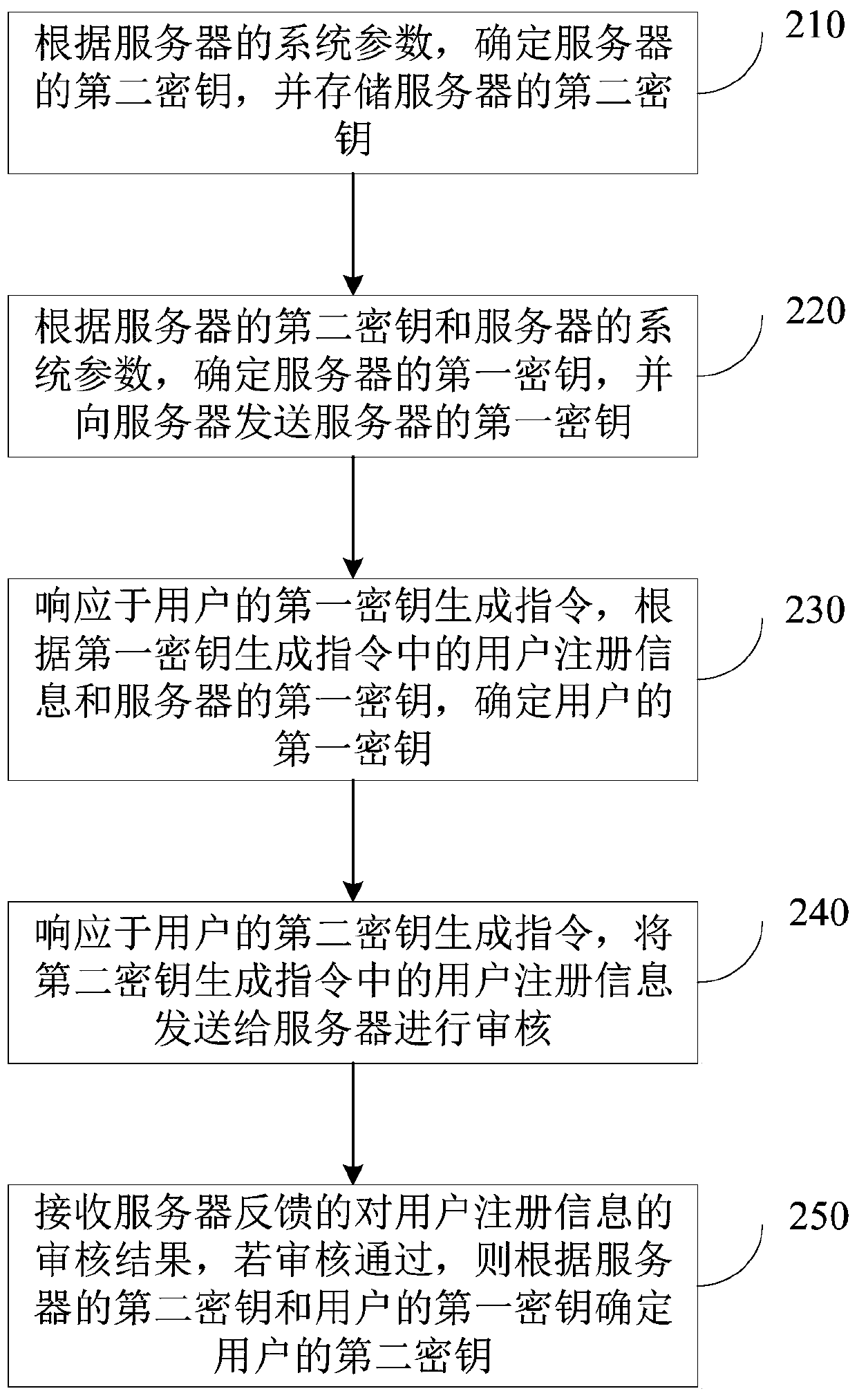
[0058] figure 2 It is a schematic flowchart of a method for generating a user key provided in Embodiment 2 of the present invention. This embodiment is further optimized on the basis of the above-mentioned embodiment. This method can be generated by the user key configured in the key resolver. device to execute. Such as figure 2 As shown, the method specifically includes the following steps:
[0059] Step 210: Determine the second key of the server according to the system parameters of the server, and store the second key of the server.
[0060] Wherein, the key resolver obtains system parameters stored in the server, and the key resolver can be divided into a trusted execution module and a trusted storage module. The trusted execution module is a module that obtains user registration information and server system parameters to calculate the key. The trusted storage module is a trusted execution environment that is used to store the second key of the server and ensure the...
Embodiment 3
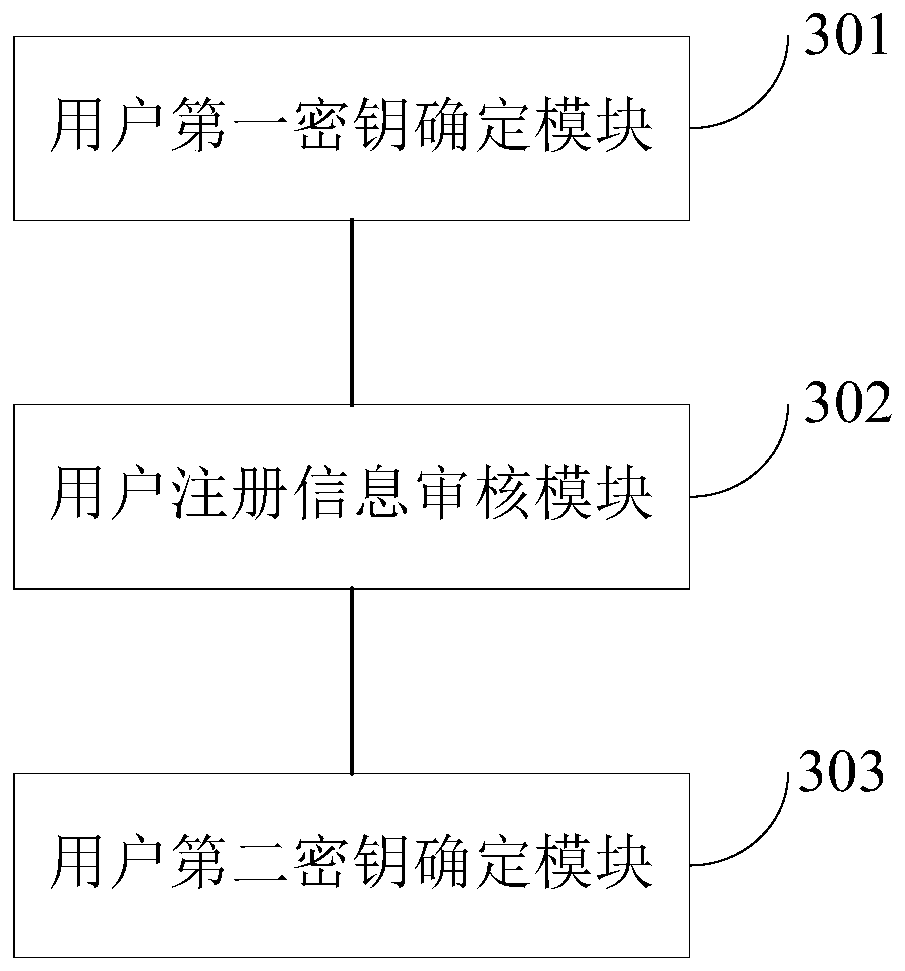
[0072] image 3 It is a structural block diagram of a user key generation device provided by an embodiment of the present invention, configured in a key parser, capable of executing a user key generation method provided by any embodiment of the present invention, and having corresponding functions for executing the method Functional modules and beneficial effects. Such as image 3 As shown, the device specifically includes:
[0073] The user's first key determination module 301 is configured to determine the user's first key according to the user's registration information in the first key generation command and the server's first key in response to the user's first key generation instruction;
[0074] The user registration information review module 302 is configured to send the user registration information in the second key generation instruction to the server for review in response to the user's second key generation instruction;
[0075] The user's second key determinat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com