Intellectual property protection method and system based on blockchain technology
A technology for intellectual property and protection systems, applied in the fields of digital data protection, computer security devices, structured data retrieval, etc., can solve problems such as disadvantages and adverse effects on the interests of rights holders, and achieve the effect of ensuring authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
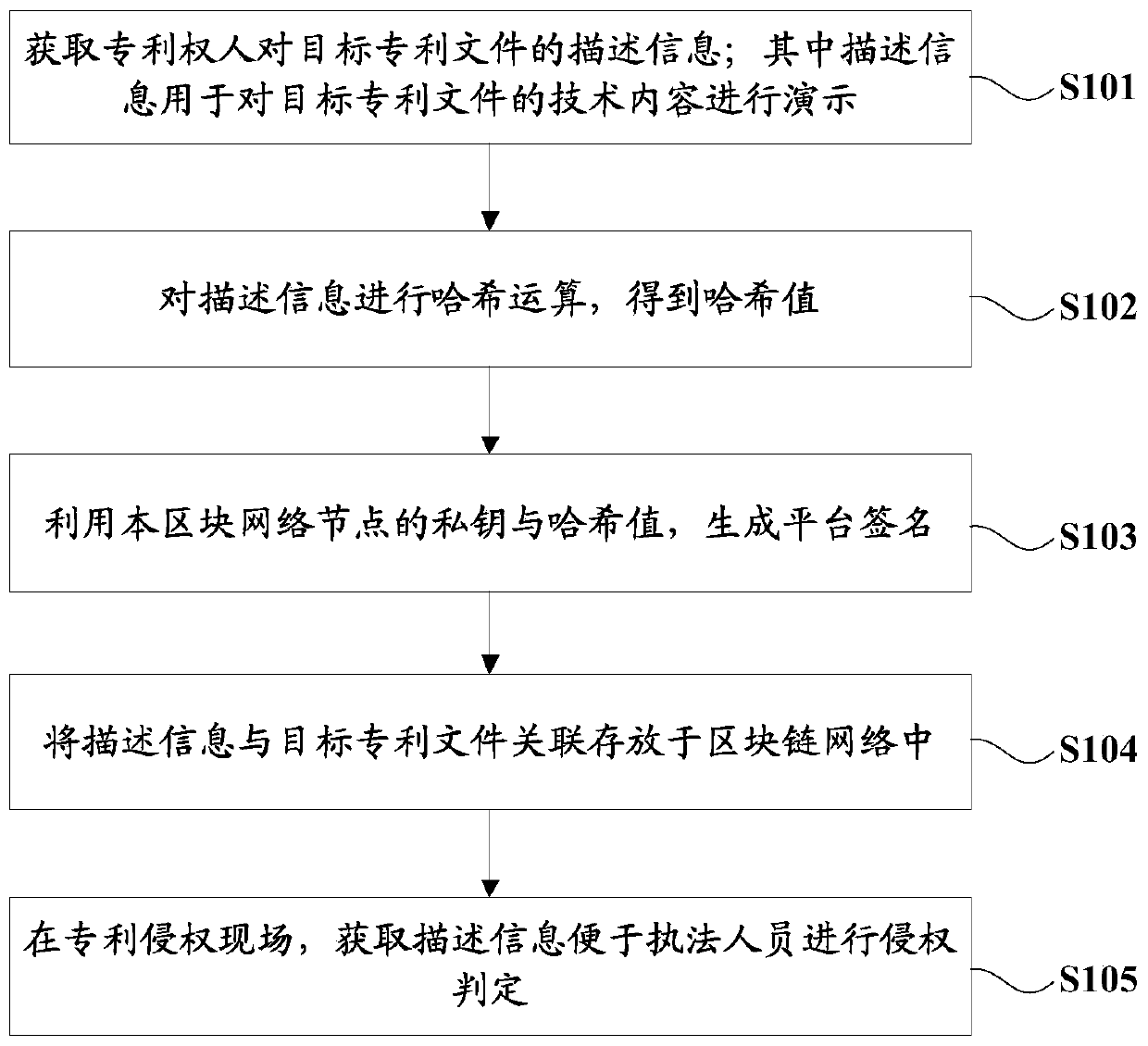
[0027] See figure 1 , figure 1 It is a schematic flow chart of the intellectual property protection method based on blockchain technology in this embodiment, and the method mainly includes the following steps:
[0028] S101. Obtain the description information of the patentee on the target patent document; the description information is used to demonstrate the technical content of the target patent document.
[0029] Wherein, the description information includes at least one of video, animation, and picture. Through videos, animations, pictures and other forms, the content of the patented technology is intuitively demonstrated, which is simple and clear, so that law enforcement personnel who are not in the technical field can also understand the technology of the target patent.
[0030] The types of target patents include inventions and utility models; when the type of target patent is an invention patent, the description information includes videos and animations; for exampl...
Embodiment 2
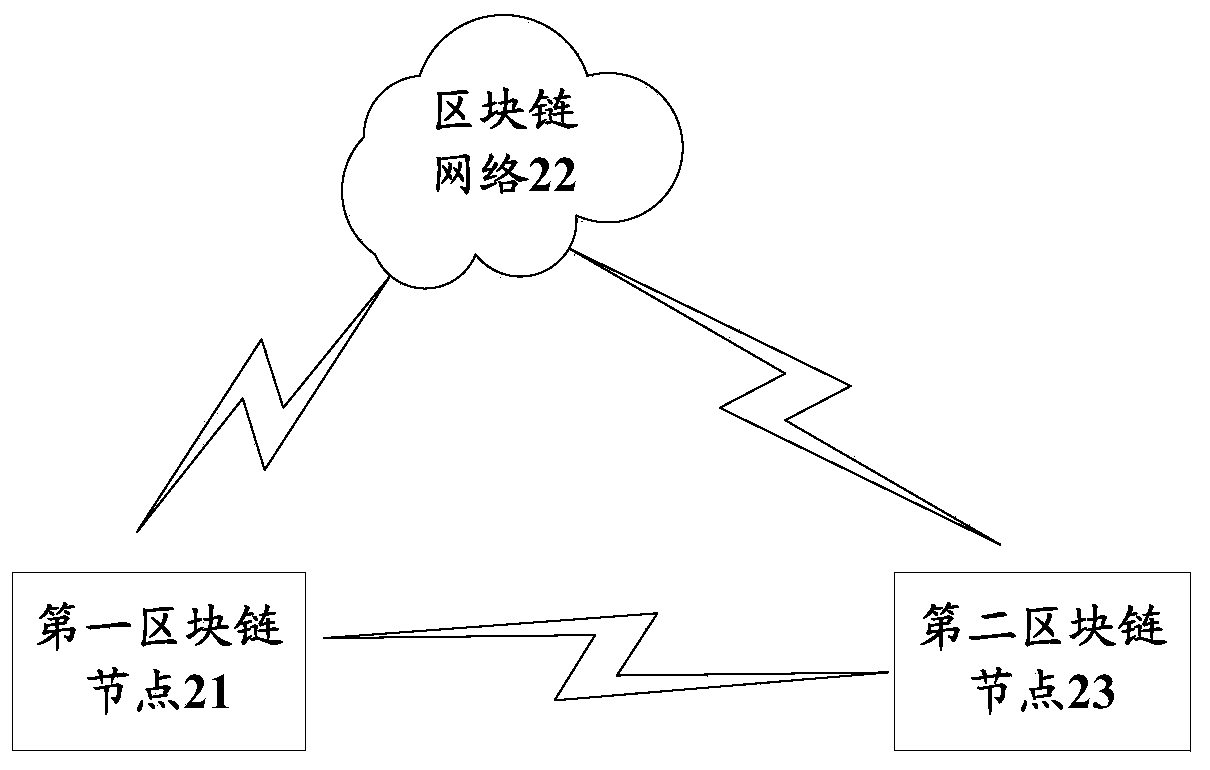
[0041] On the basis of the first embodiment above, this embodiment provides an intellectual property protection system based on blockchain technology. The patent infringement system is implemented in a blockchain network, and all network nodes can participate. See figure 2 , the patent infringement identification system mainly includes:
[0042] The first block chain node 21 is used to obtain the description information of the patentee on the target patent document; the description information is used to demonstrate the technical content of the target patent document; the hash operation is performed on the description information to obtain the hash value; The private key and hash value of the network node of this block generate a platform signature; and send the description information and the target patent file to the block chain network; the description information includes at least one of video, animation, and picture.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com