Method for detecting power grid false data injection attacks
A technology of injecting attacks and fake data, applied in electrical components, biological neural network models, instruments, etc., can solve problems such as threats to the stable operation of power grids, power outage losses, and impact on smart grids, achieving simple construction, fast convergence, and improved detection efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
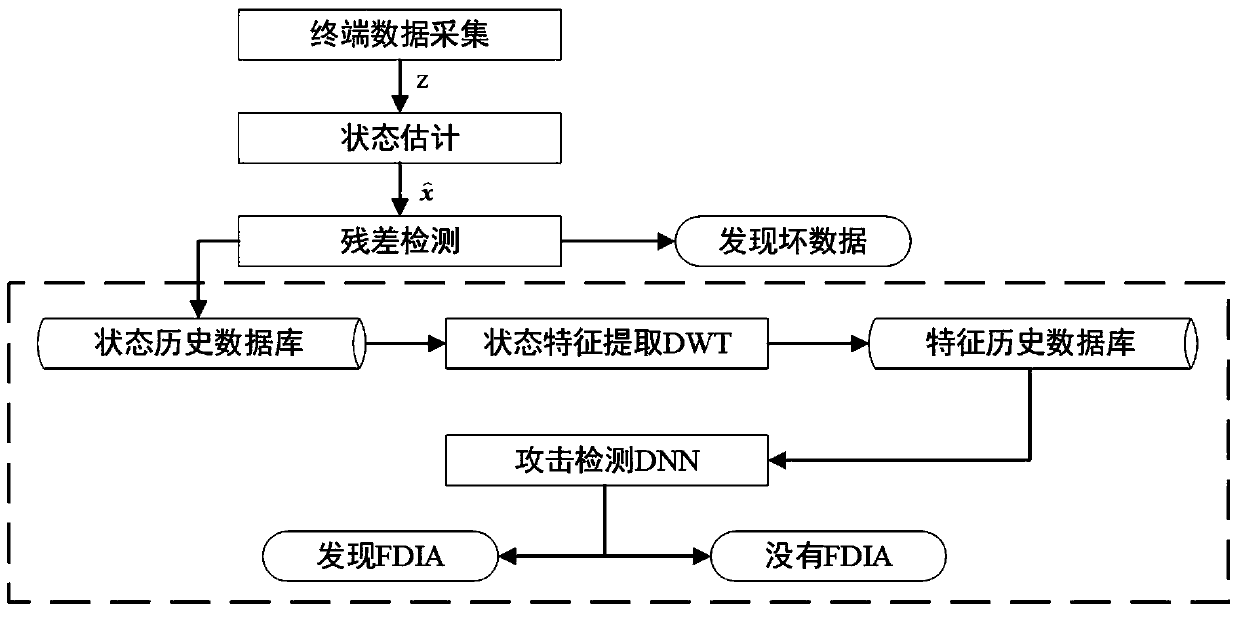
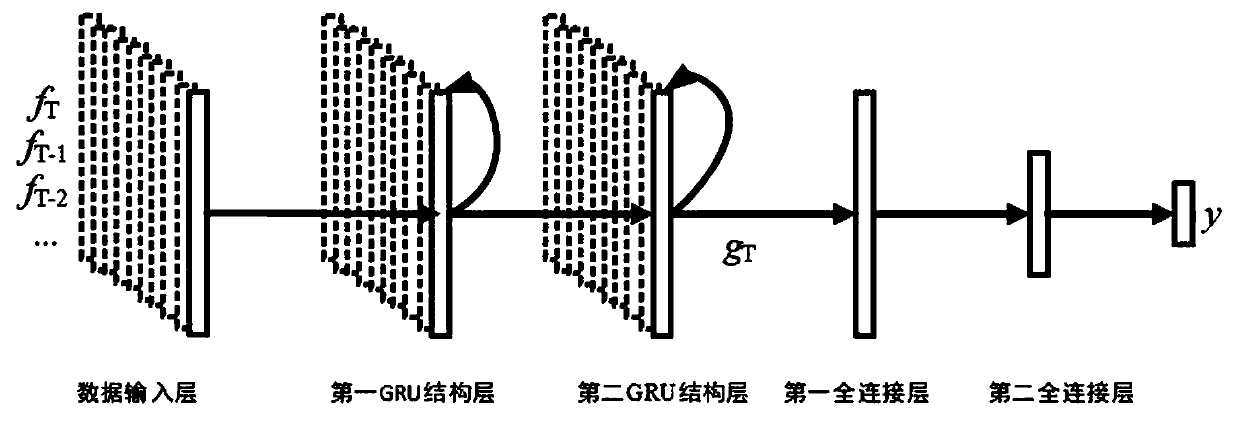
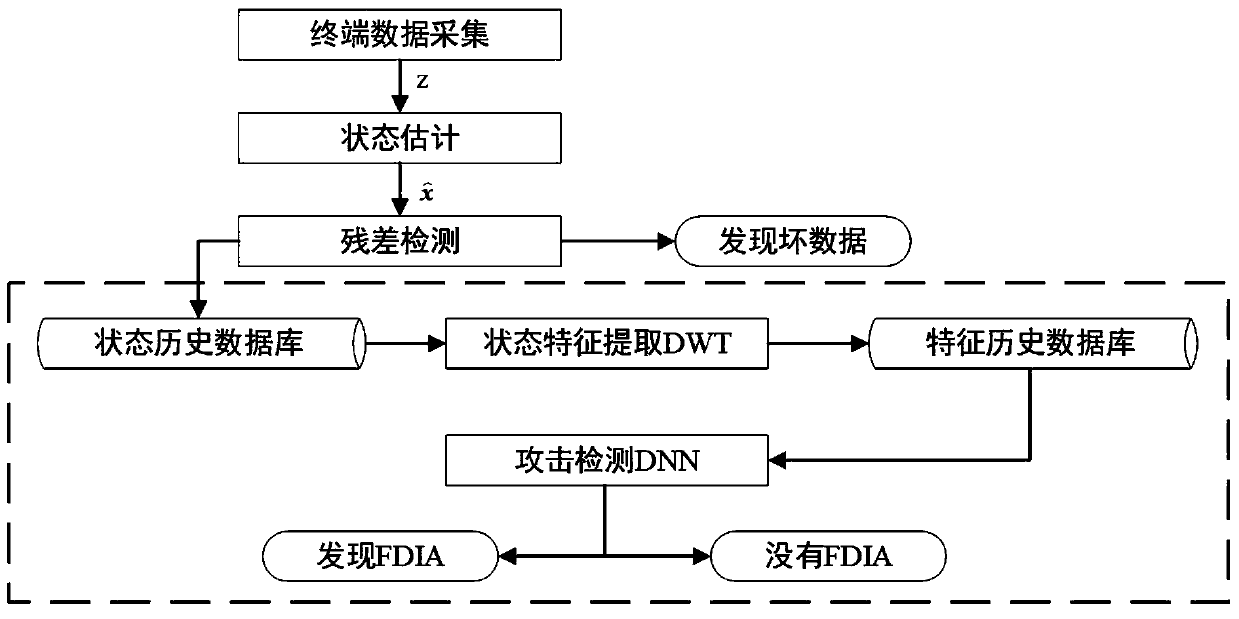
[0035] The false data injection attack detection model proposed by the present invention is divided into two links of training and detection. The purpose of training is to determine the relevant parameters in the deep neural network to realize online detection of fake data injection attacks. Therefore, the two links are similar in process. The difference is that the unknown parameters in the deep neural network are determined first in the training link, and then the trained deep neural network is used for online detection in the detection link, that is, the presence / absence of false data injection is realized. Attacks on binary classification problems.
[0036] figure 1 It is a flow chart of the false data injection attack detection method proposed by the present invention. The power grid terminal uploads the collected operating state information to ...
PUM
| Property | Measurement | Unit |
|---|---|---|
| Length | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com