Digital certificate generation method, authentication method and electronic equipment
A technology for digital certificates and authentication methods, applied in digital transmission systems, electrical components, user identity/authority verification, etc. The effect of reducing redundancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
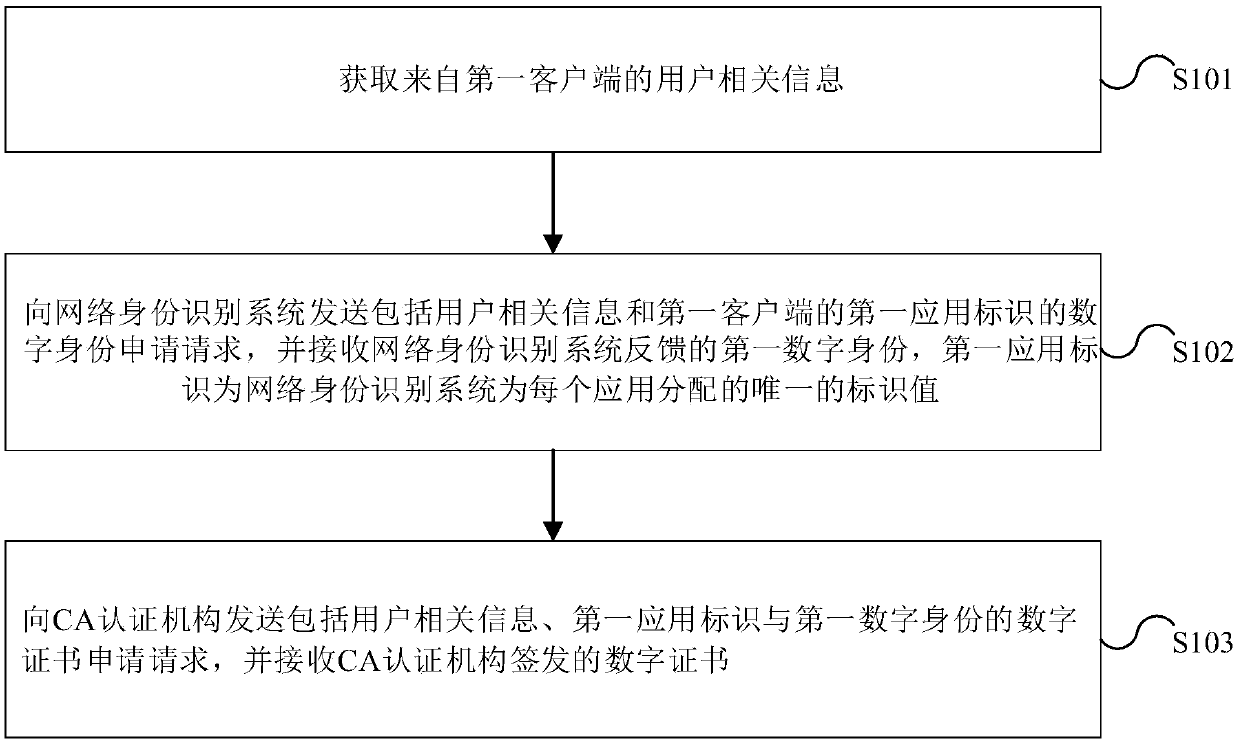
[0066] The embodiment of this application provides a digital identity-based digital certificate generation method, such as figure 1 As shown, the method may include the following steps:
[0067] Step S101, acquiring user-related information from the first client;
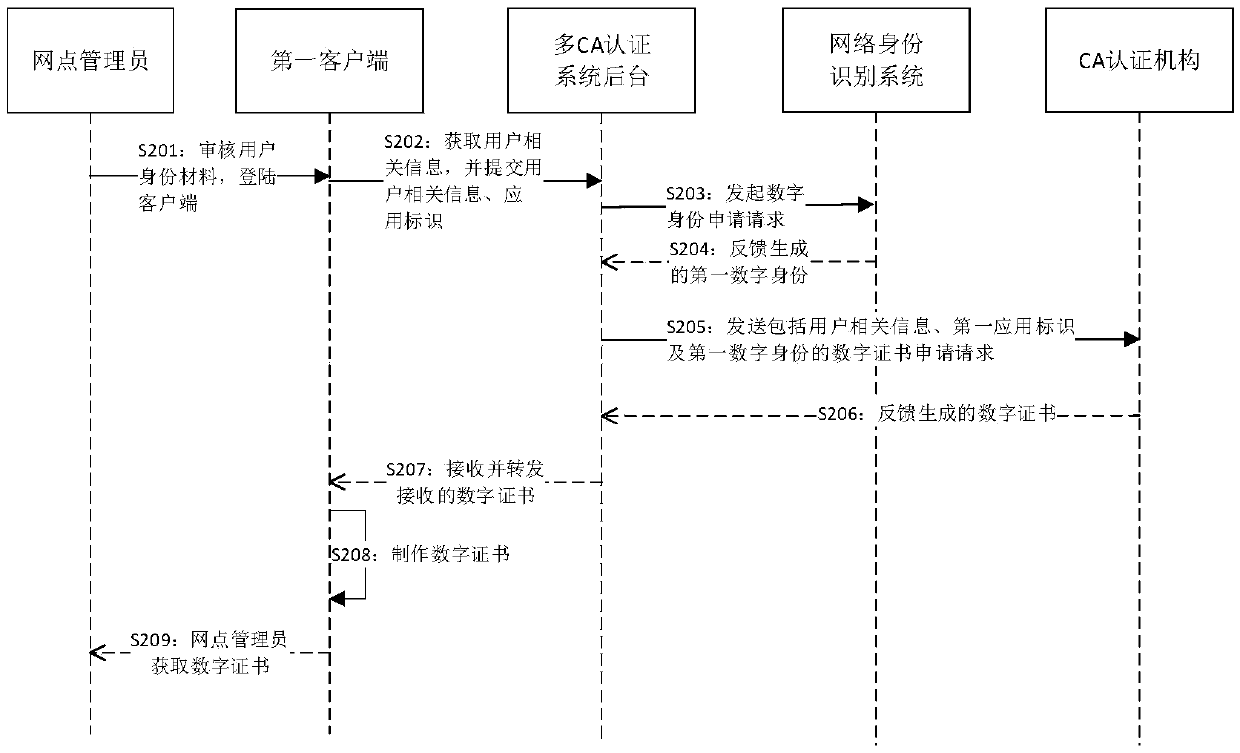
[0068] For this embodiment of the application, the user-related information from the first client is acquired, wherein the first client in the embodiment of the The CA authentication system applies for a digital certificate, wherein at least one site administrator can be assigned to each first client, and the site administrator can verify the authenticity of the user-related information materials submitted by the digital certificate applicant, and then pass the first client Send a corresponding request, where the request carries the applicant's user-related information, which can be the citizen's name and ID number.
[0069] Step S102, sending a digital identity application request including user-related informati...
Embodiment 2
[0091] Based on the same inventive concept, the embodiment of this application provides an authentication method based on digital certificates, including:
[0092] Step S301, sending the password input by the user to the digital certificate carrier to activate the digital certificate carrier, the digital certificate carrier carries a private key and a digital certificate, and the digital certificate carries a public key;
[0093] For the embodiment of this application, the password entered by the user through the terminal device is sent to the digital certificate carrier. If the input password is consistent with the activation password of the digital certificate carrier, the digital certificate carrier is activated. The digital certificate issuing network is making the digital certificate When using the carrier, perform the operation of allowing the user to set a password. When using the digital certificate carrier, the digital certificate carrier can only activate the digital ...
Embodiment 3
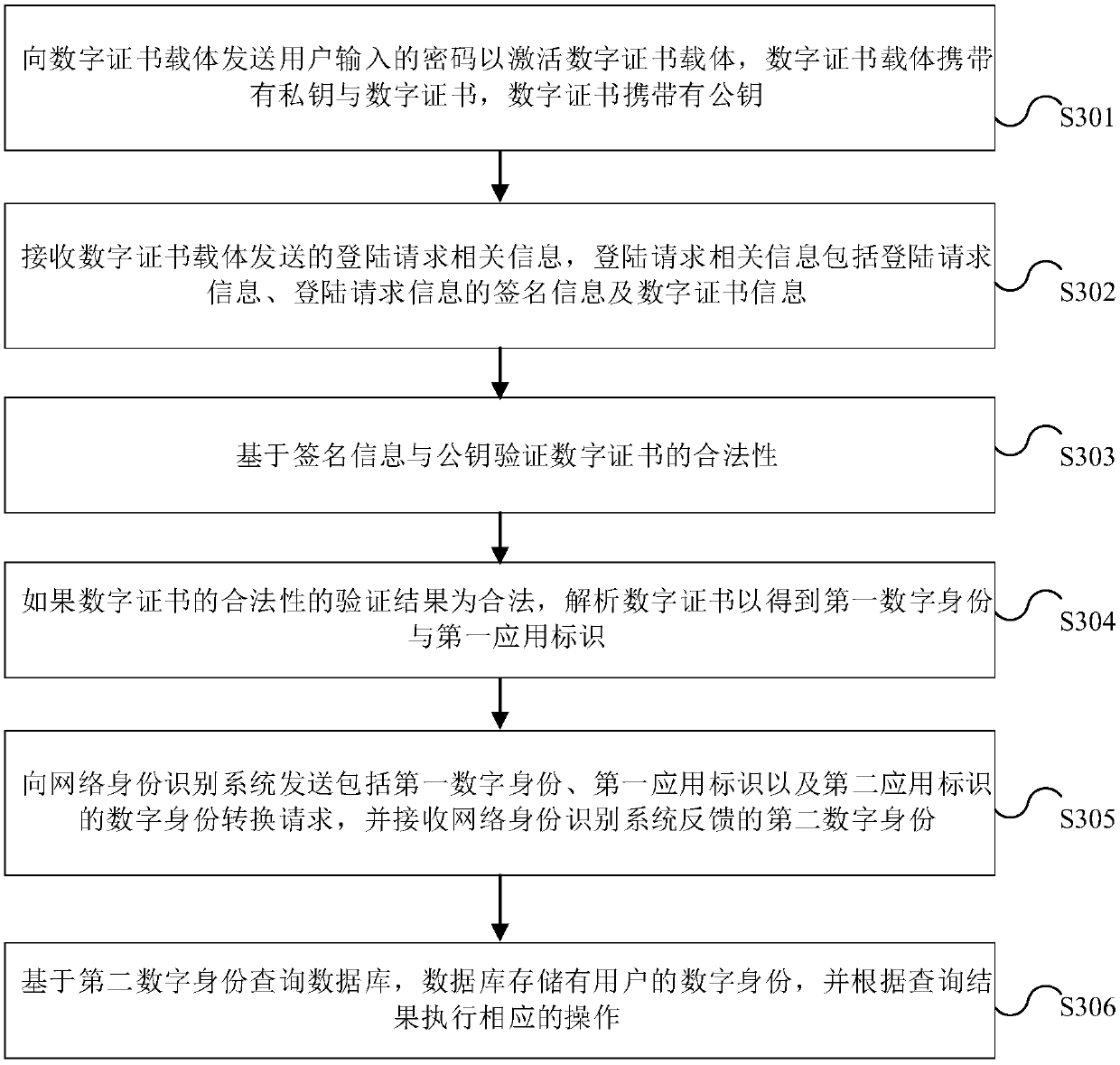
[0127] Based on the same inventive concept, the embodiment of this application provides another authentication method based on digital certificates, such as Figure 5 As shown, the method includes:
[0128] Step S501, acquiring user-related information;
[0129] For this embodiment of the application, the user-related information input by the user through the corresponding terminal device is obtained, where the user-related information may be the user's name and ID number.
[0130] Step S502, obtaining the digital certificate sent by the digital certificate carrier, and obtaining the signature information that the digital certificate carrier executes signing on the user-related information;
[0131] For this embodiment of the application, the digital certificate carrier may be a USBkey (also known as USB-Shield), or other forms of carriers capable of realizing the functions of this application, which are not limited here.
[0132] Step S503, verifying the legitimacy of the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com