Attack method for big data processing platform Hadoop
A technology of big data processing and hadoop clusters, applied in electrical components, transmission systems, etc., can solve the problems of no security vulnerability analysis, no specific implementation plan for attacks, etc., and achieve the effect of low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
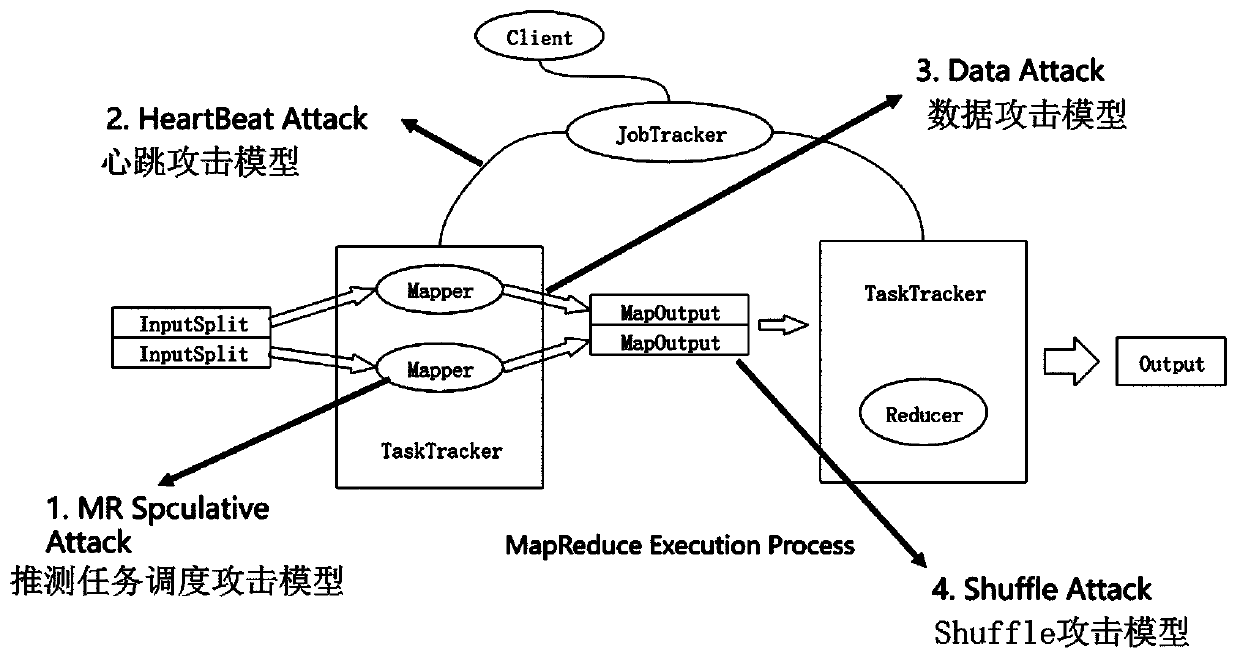
[0064] The present invention assumes that the cluster has deployed some defense mechanisms, and the proposed attack will follow the security policy set by the cluster. In this invention, the Hadoop data processing framework is used as the target platform of the attack, but the attack can also be applied to other similar frameworks.
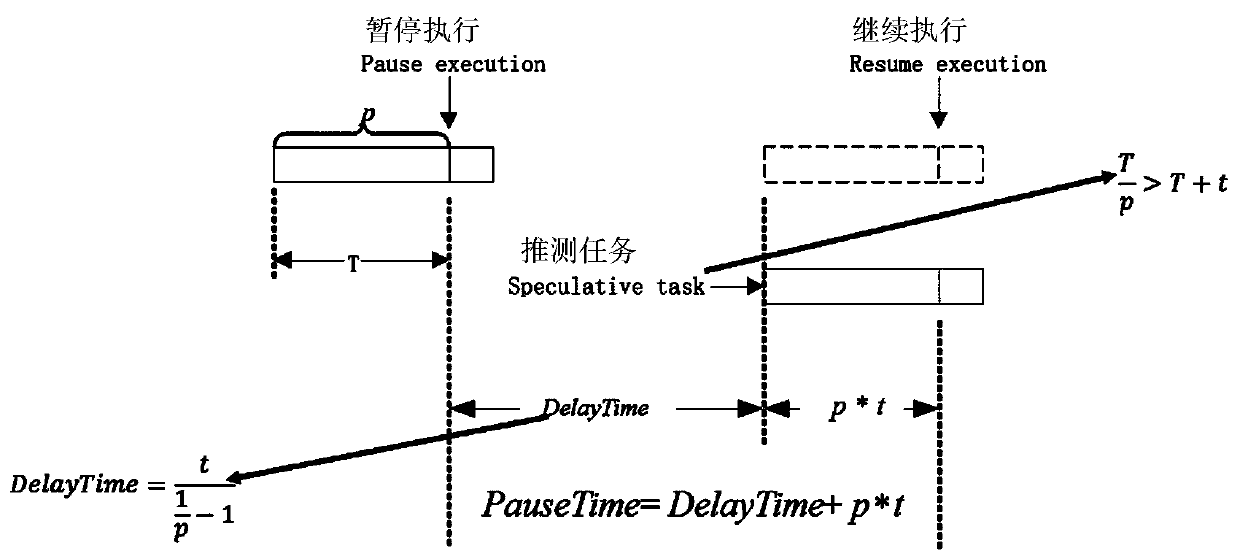
[0065] The first attack model, MR speculative task scheduling attack (MR Speculative Attack), is a scheduling algorithm for mapreduce speculative tasks [4]; it uses the loopholes in hadoop scheduling method to extend the execution time of jobs.
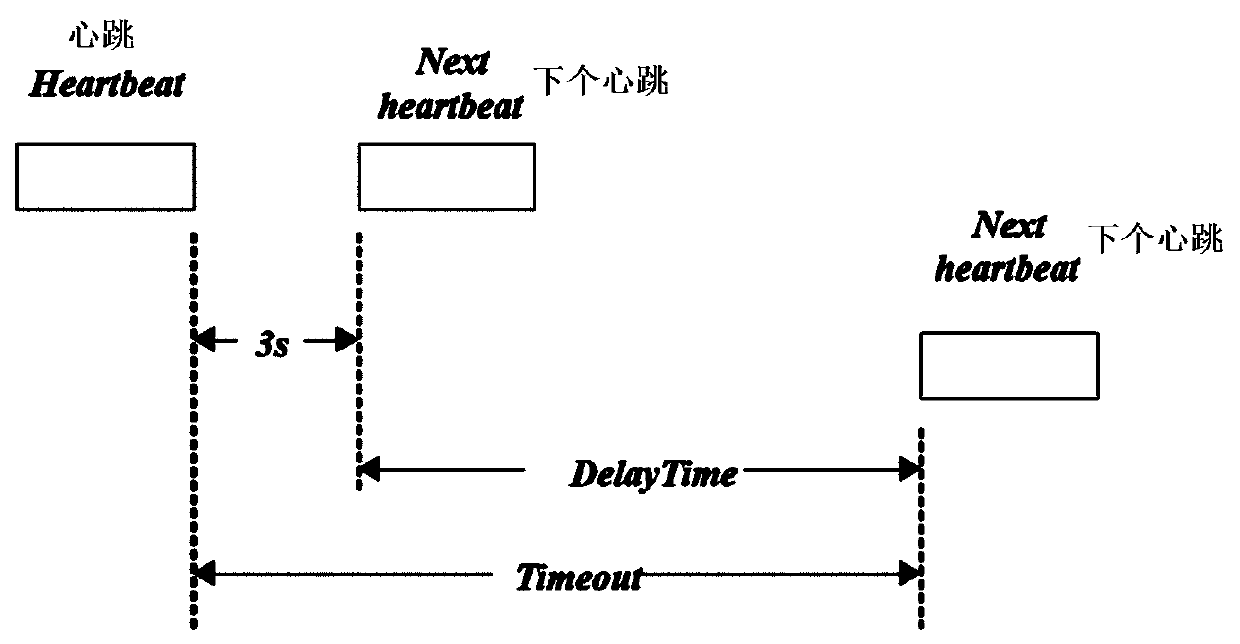
[0066] The second attack model, HeartBeat Attack, is aimed at the communication mechanism between the master node and the slave node; the scheduling time of map and reduce tasks is increased by extending the heartbeat time.
[0067] The third attack model data attack (Dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com