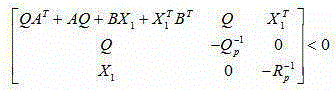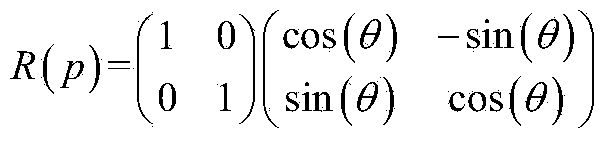Patents
Literature
59results about How to "Improve execution time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
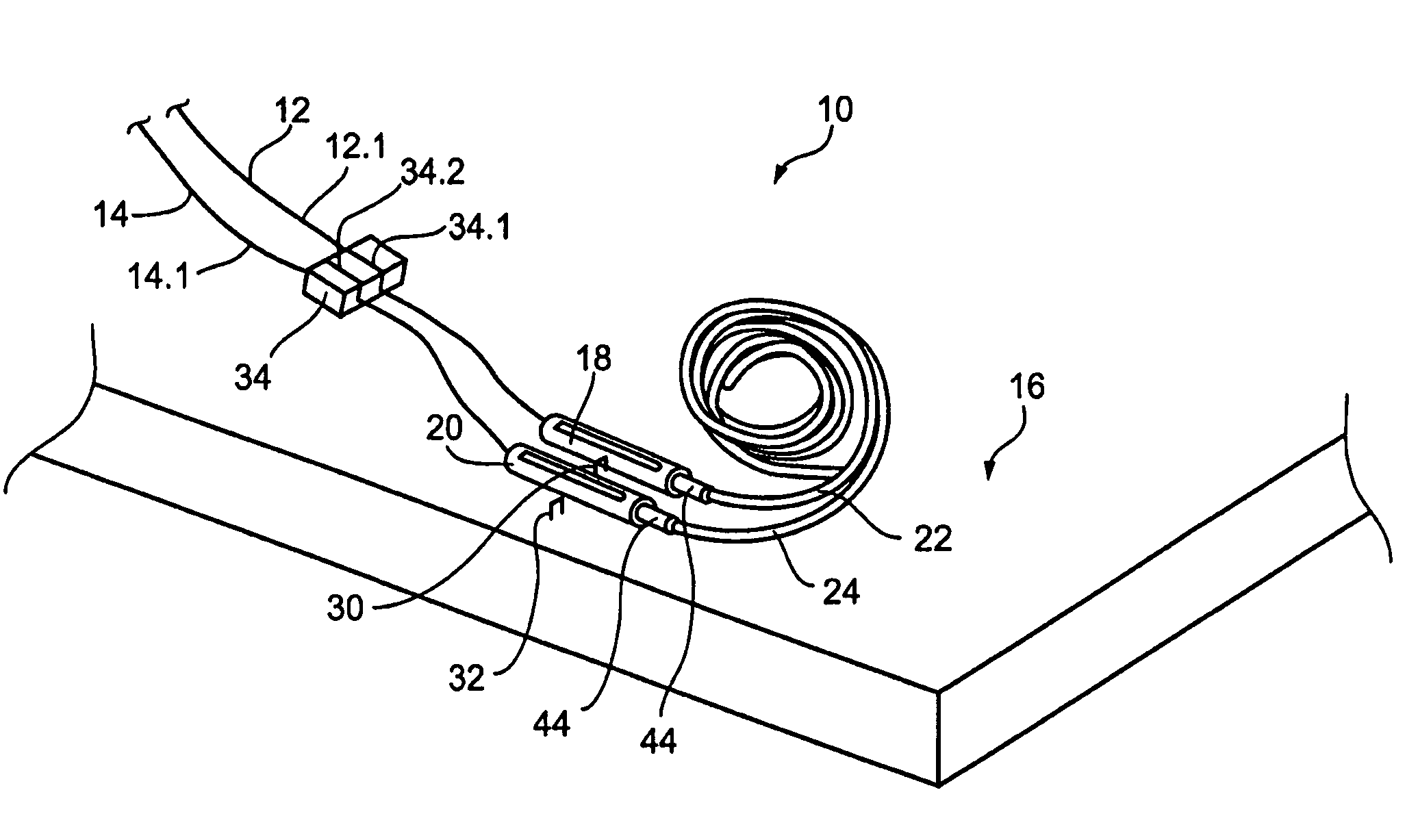
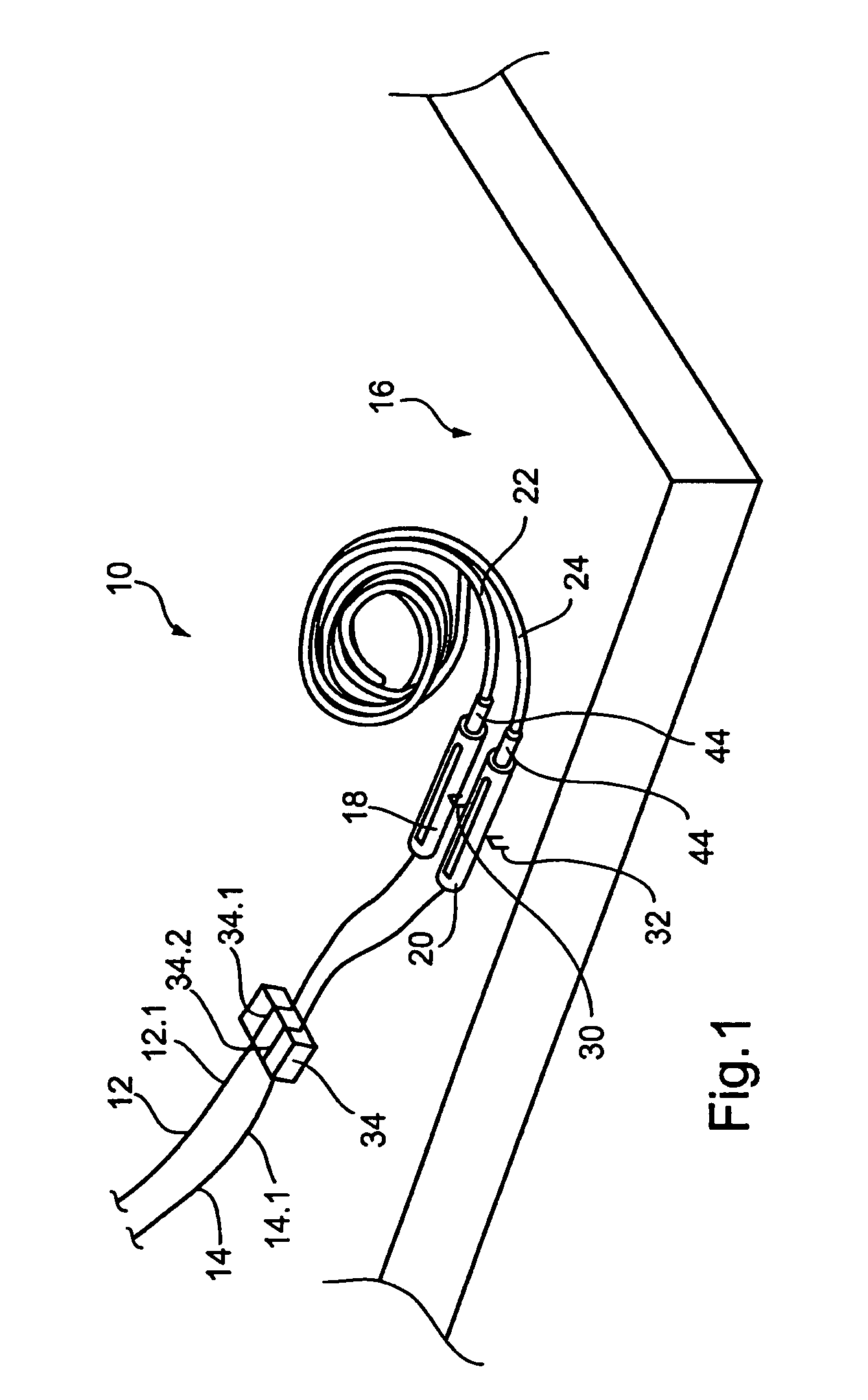
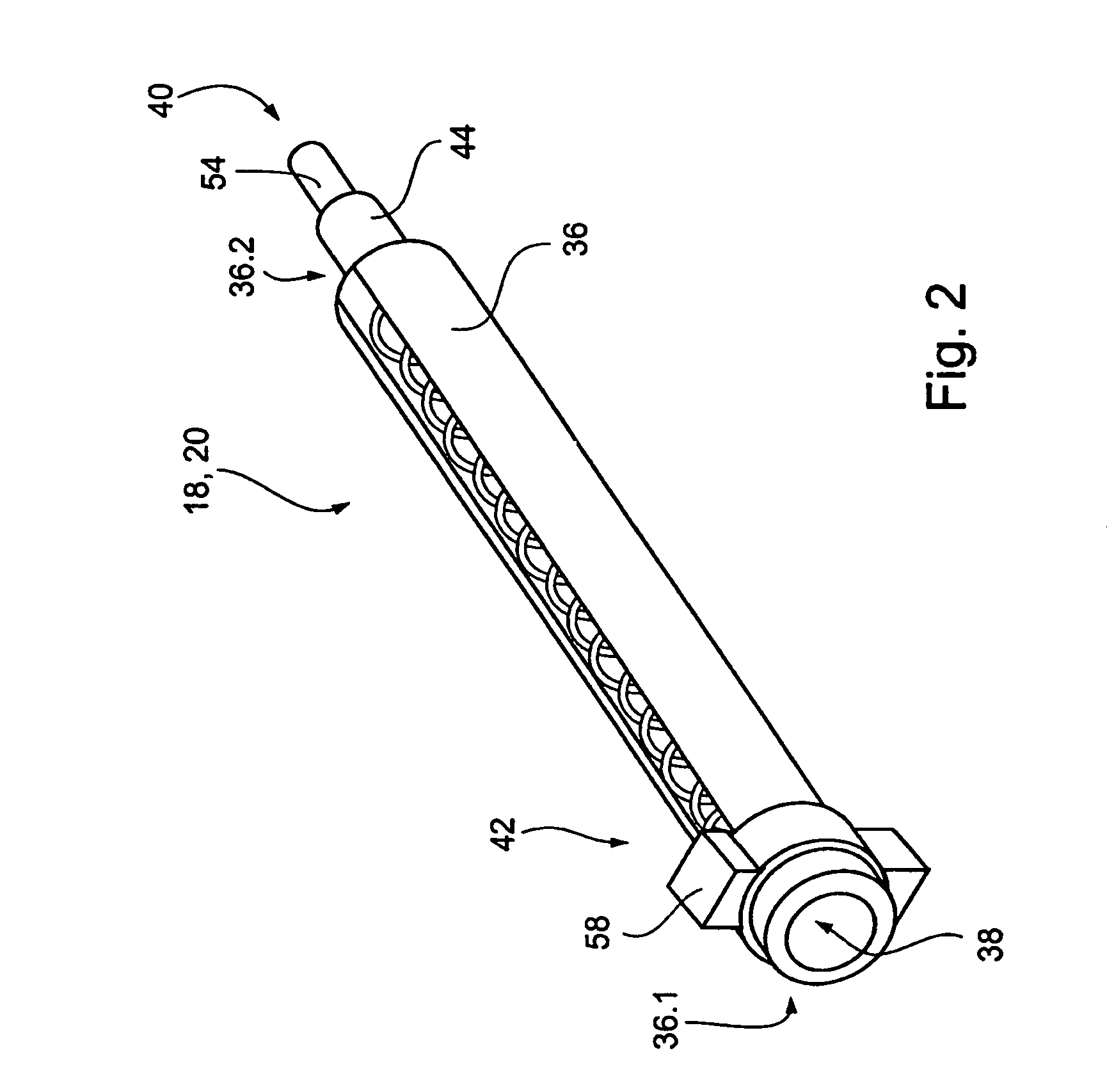
Guidewire management devices and methods
InactiveUS7544170B2Good curative effectImprove execution timeGuide wiresInfusion syringesEngineeringLiving body
A method of performing a medical procedure on a living body is provided. The method comprises inserting a leading end portion of a guidewire into the living body and advancing a trailing end portion of the guidewire into a container, the container being arranged to coil the trailing end portion of the guidewire as the trailing end portion is advanced into the container. The invention extends to an advancing device operable to cause a trailing end portion of a guidewire to advance into a container. The advancing device comprises a body, an engaging mechanism on the body, the engaging mechanism being arranged releasably to engage the guidewire and to move relative to the body while engaging the guidewire thereby to cause the guidewire to advance through the body.
Owner:BOSTON SCI SCIMED INC
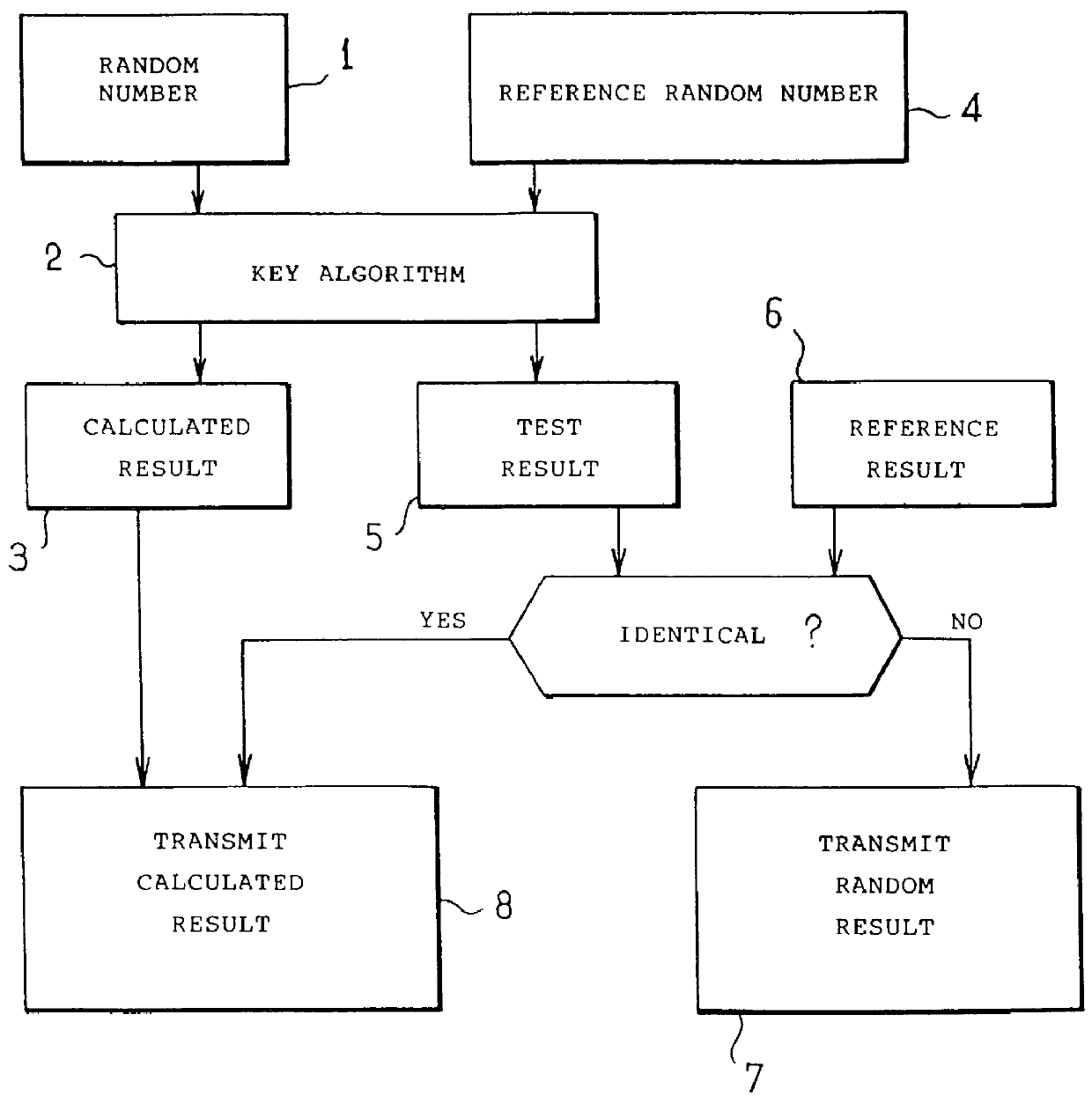
Security method for making secure an authentication method that uses a secret key algorithm
InactiveUS6101254AShorten the timeImprove execution timeUser identity/authority verificationSecret communicationComputer hardwareAuthentication
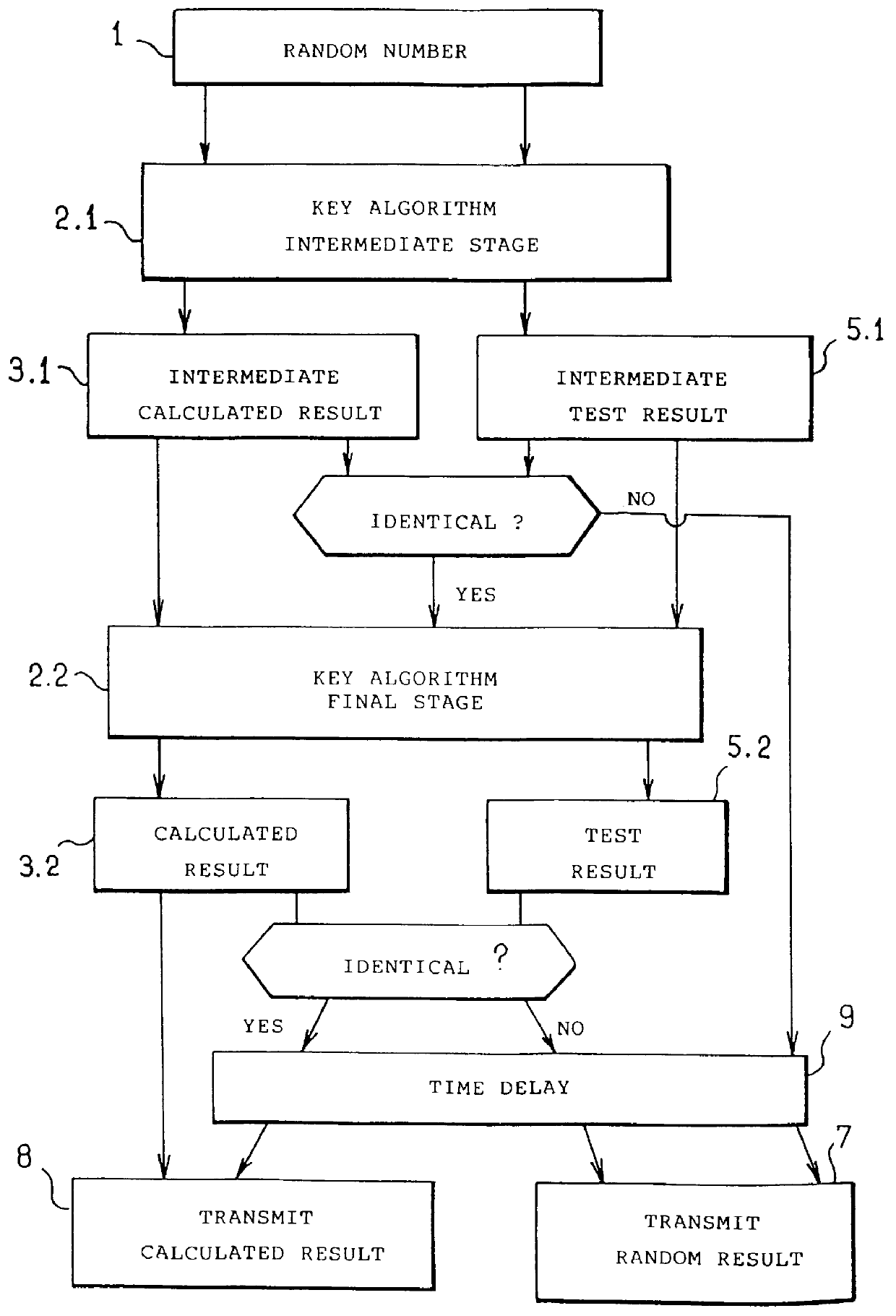
The security method is associated with an authentication method comprising steps of obtaining a calculated result from a random number subjected to a secret key algorithm, the security method includes steps of calculating a test result from a reference random number subjected to the secret key algorithm, of comparing the test result with a reference result, and of ensuring that the calculated result is transmitted only when the test result is identical to the reference result.
Owner:GEMPLU
Periodic task reliability control method based on watchdog and timer
InactiveCN101216798AOperational Reliability MonitoringReduce misjudgmentHardware monitoringDependabilityRunning time
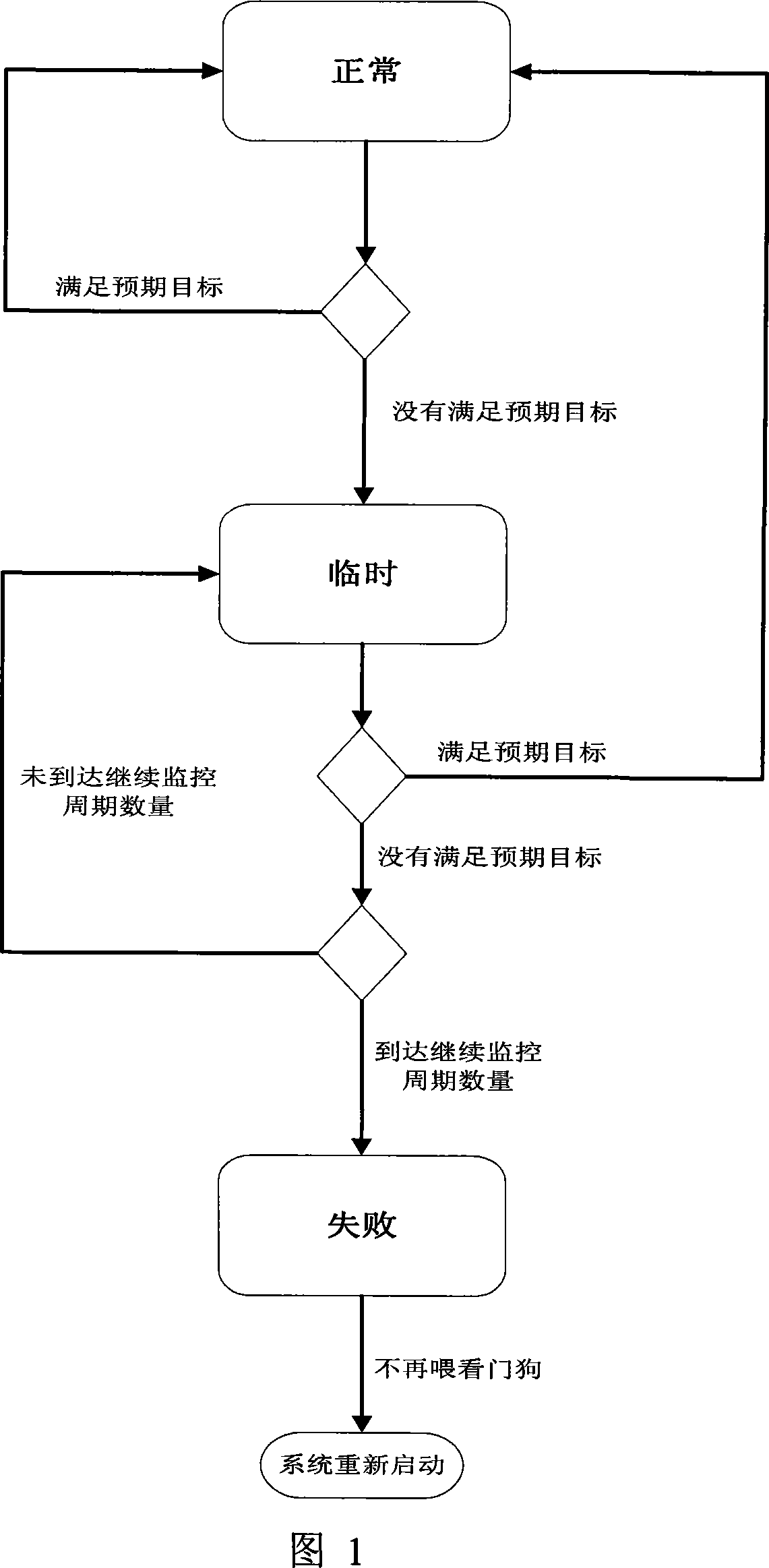
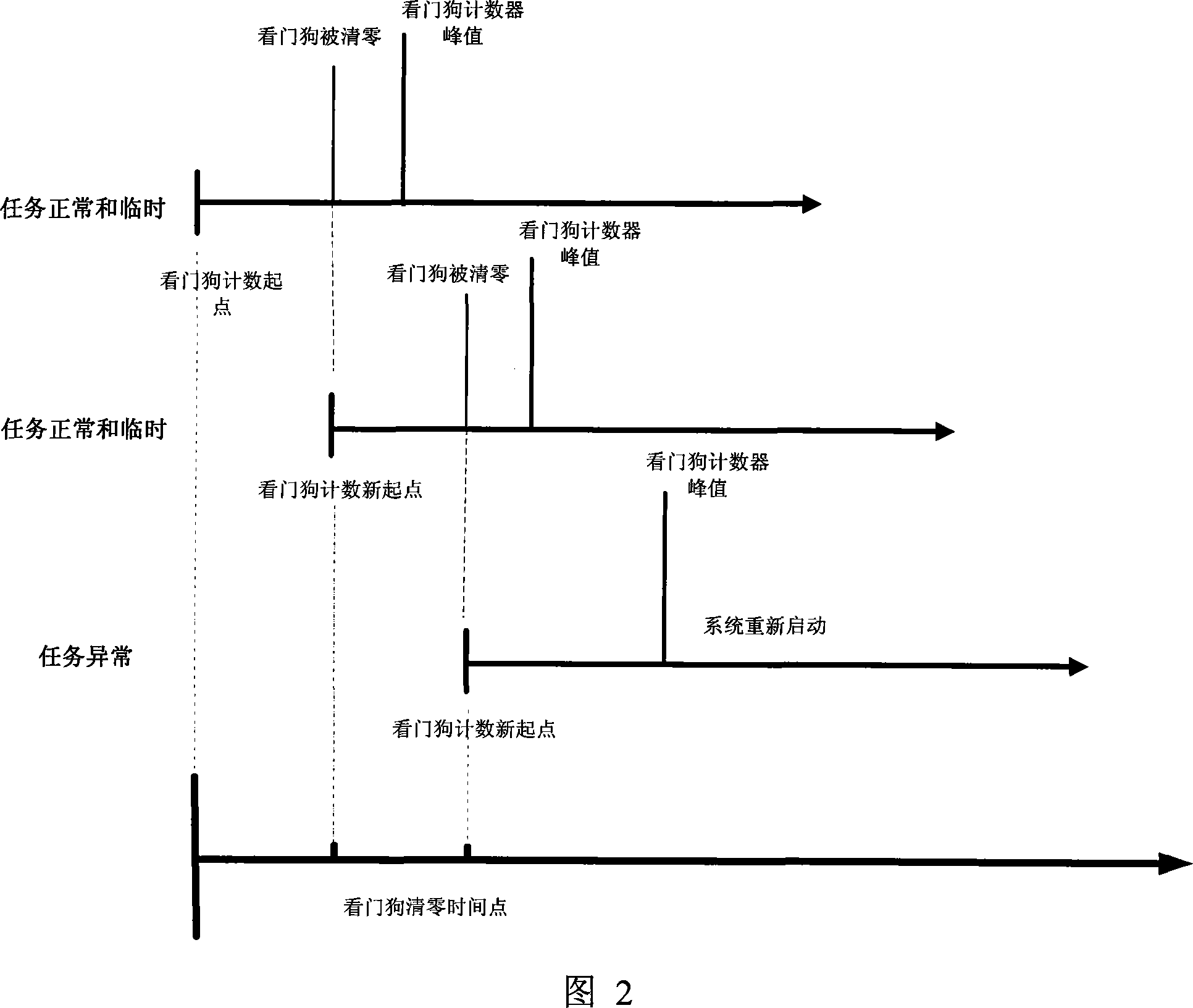
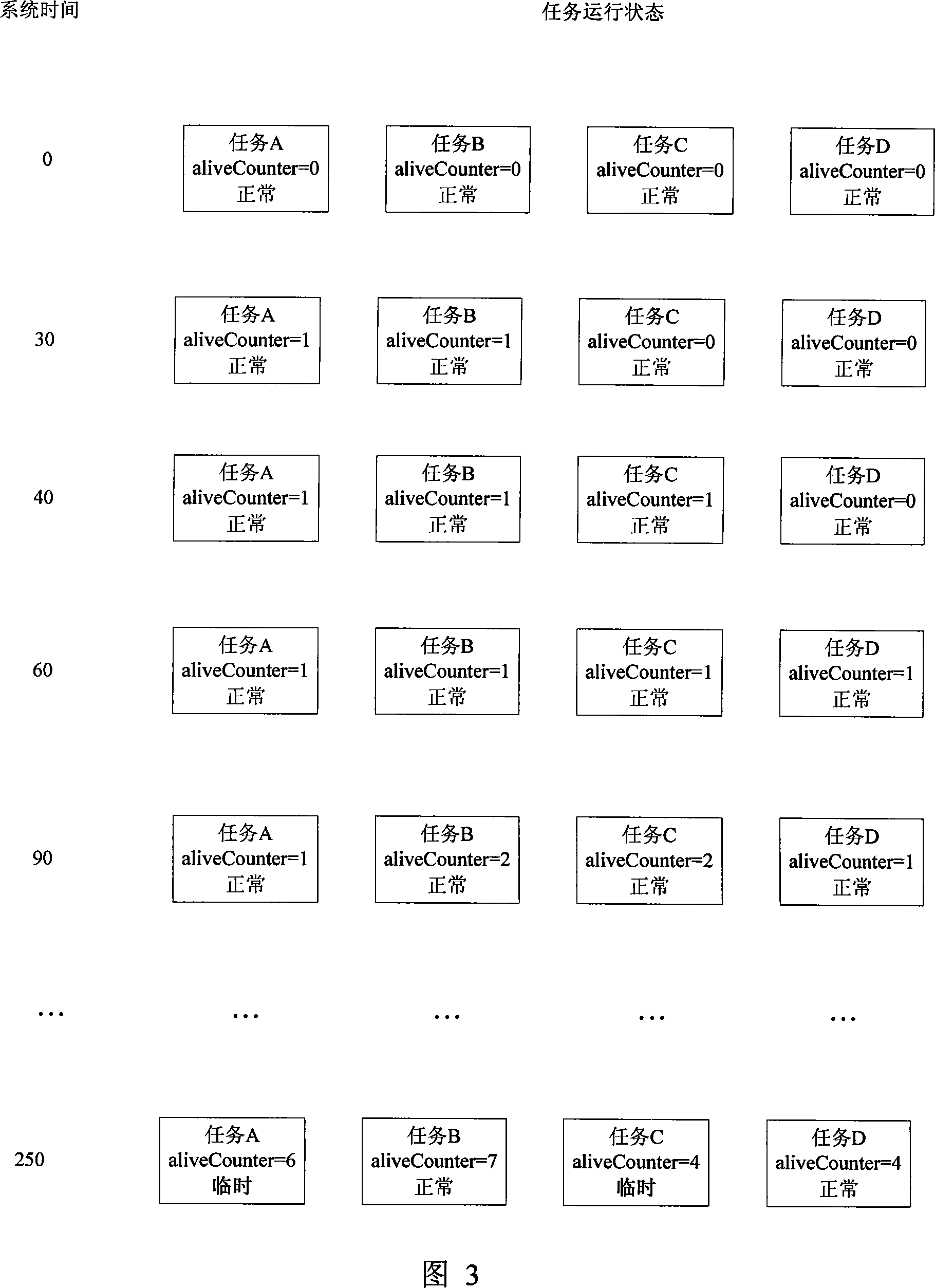
The invention discloses a monitoring method for periodic task reliability based on a watchdog and a timer. The invention adopts a task multi-mode management method which allows the task to have temporary state and a task report mechanism; in addition, the invention increases the execution time of the periodic task measured by using the timer, and enhances the running reliability monitoring to the periodic task, through combining with the recovery system function completed by overtime restarting of the watchdog and the timing function of the timer. Based on the automatic restart function of the watchdog, the invention ensures that the system can recover automatically under an abnormal condition at the same time; whether the running time of the periodic task corresponds to the requirements is monitored; the number of periodic task reports of the configuration is allowed to have difference; the accessorial temporary state greatly decreases the abnormity misjudgment in the periodic task, thereby reducing the wrong restart of the system.
Owner:ZHEJIANG UNIV
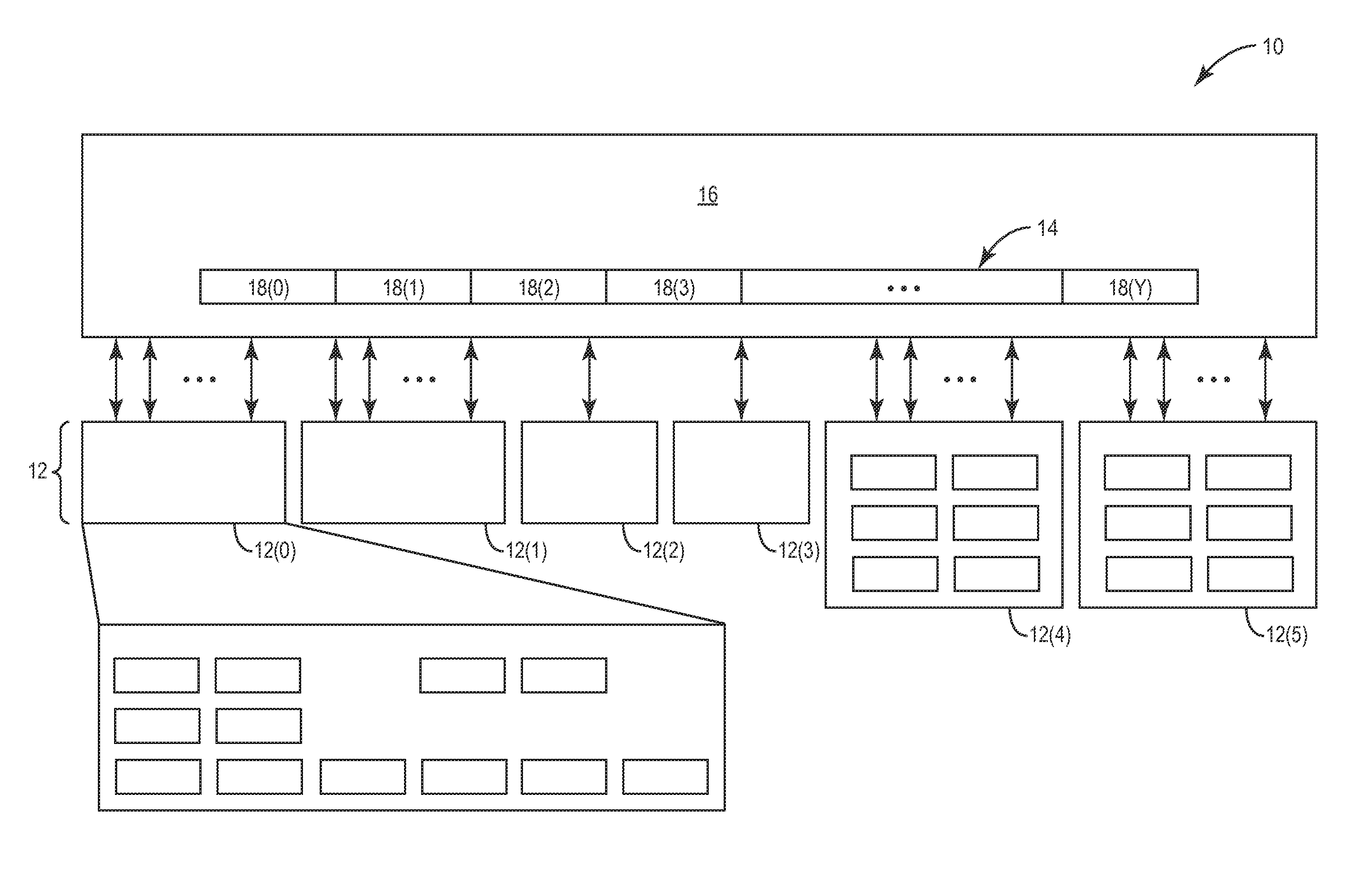
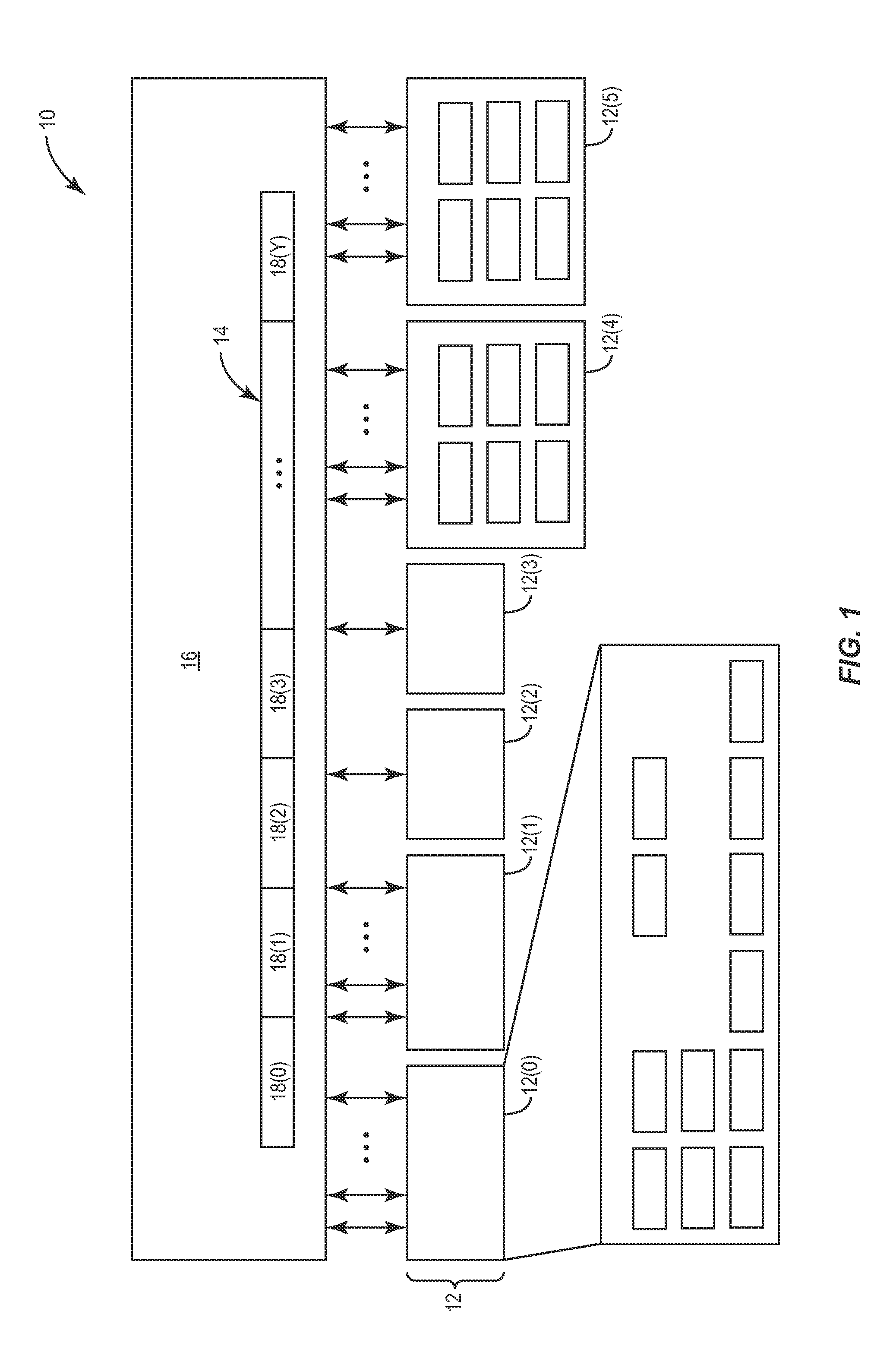
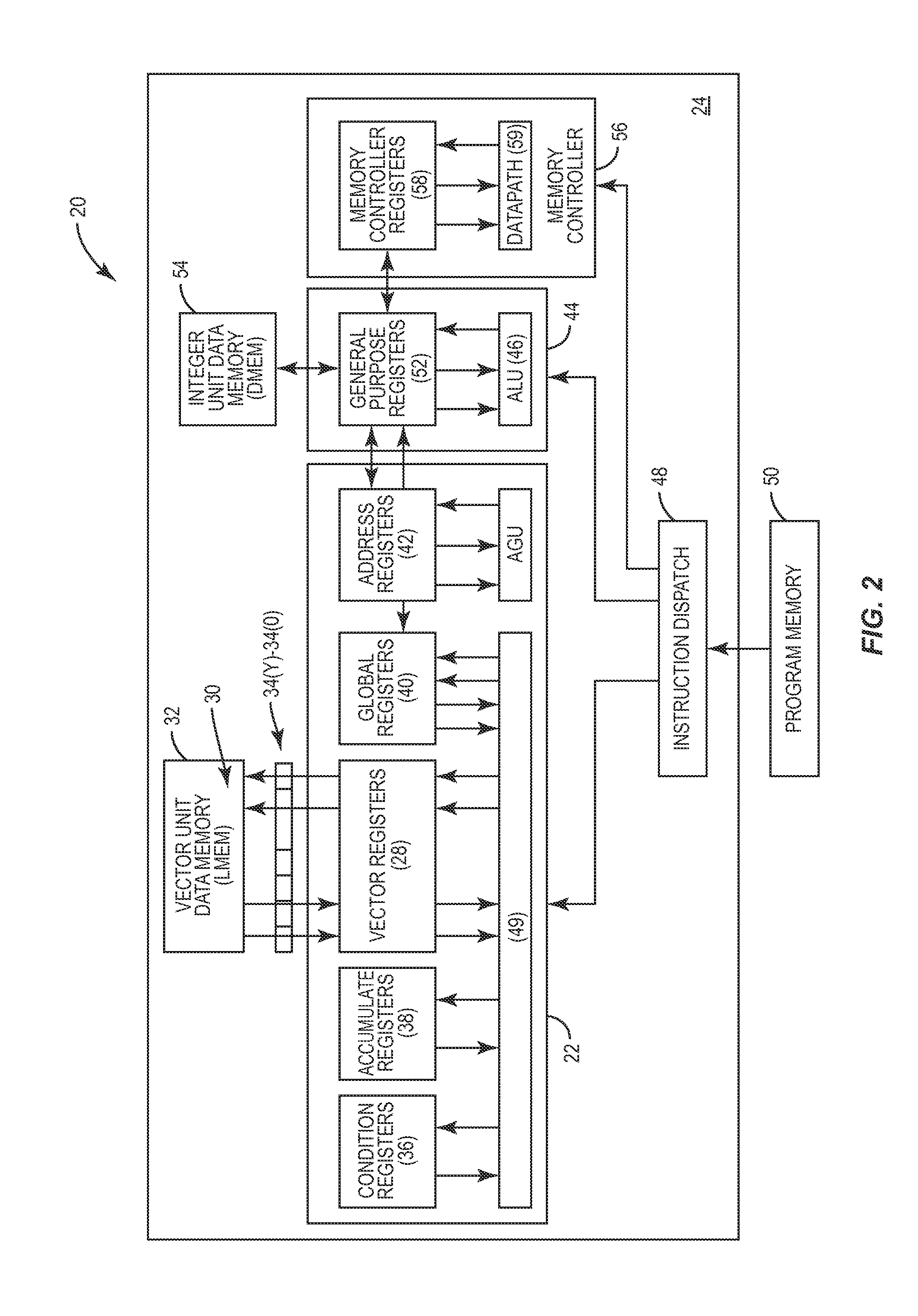
Vector processing engines having programmable data path configurations for providing multi-mode vector processing, and related vector processors, systems, and methods
ActiveUS20140281370A1Saving areaFast instruction executionGeneral purpose stored program computerEnergy efficient computingDatapathEuclidean vector
Embodiments disclosed herein include vector processing engines (VPEs) having programmable data path configurations for providing multi-mode vector processing. Related vector processors, systems, and methods are also disclosed. The VPEs include a vector processing stage(s) configured to process vector data according to a vector instruction executed in the vector processing stage. Each vector processing stage includes vector processing blocks each configured to process vector data based on the vector instruction being executed. The vector processing blocks are capable of providing different vector operations for different types of vector instructions based on data path configurations. Data paths of the vector processing blocks are programmable to be reprogrammable to process vector data differently according to the particular vector instruction being executed. In this manner, a VPE can be provided with its data paths configuration programmable to execute different types of functions based on data path configuration according to the vector instruction being executed.
Owner:QUALCOMM INC
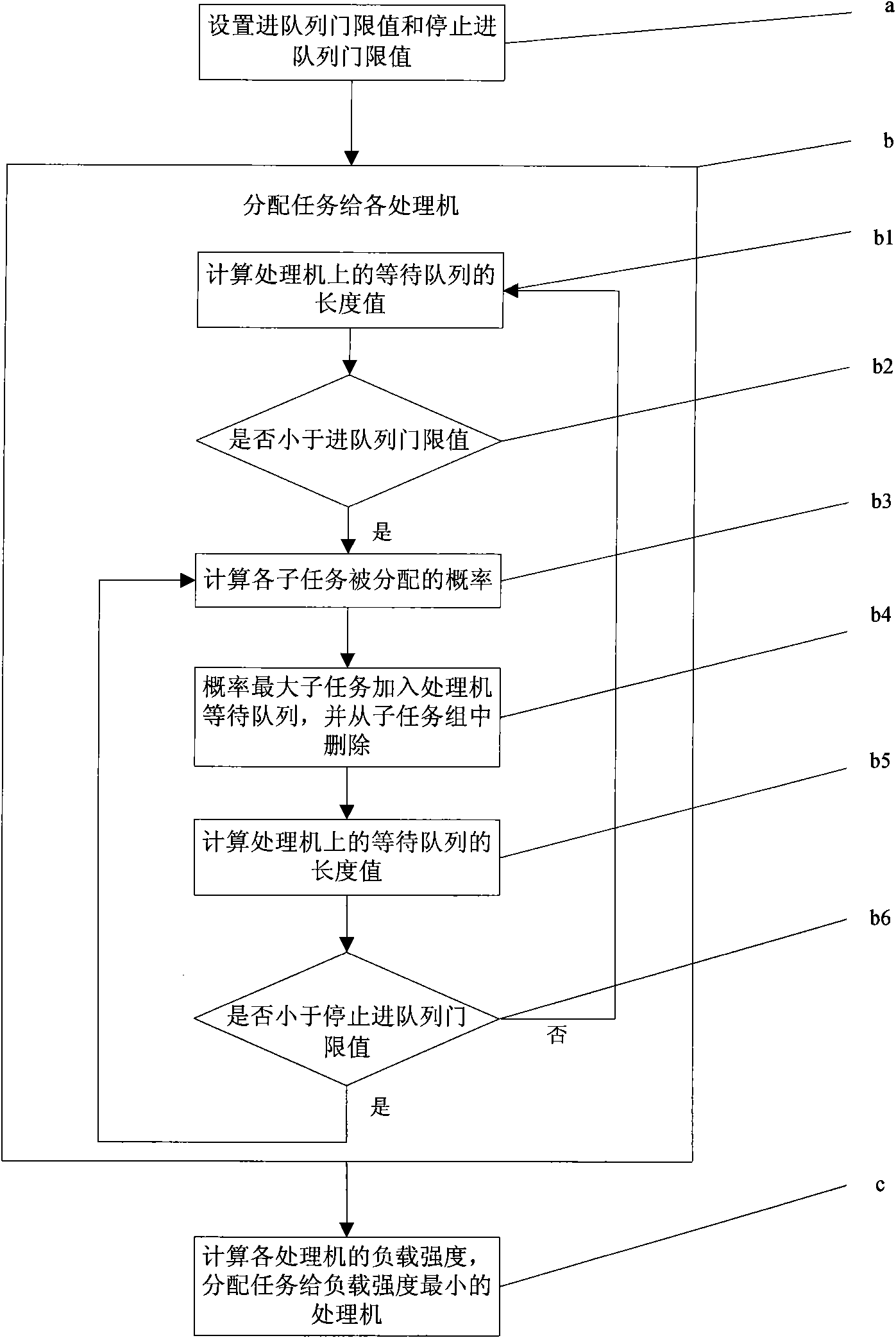
Dynamic task allocation method of heterogeneous computing system
InactiveCN101582043AFaster execution timeImprove execution timeResource allocationDistribution methodSymmetric multiprocessor system
The invention relates to a dynamic task allocation method of a heterogeneous computing system. The heterogeneous computing system completes the application task by cooperating with a group of heterogeneous processors together, decomposes the task into a group of parallel subtasks, and schedules the subtasks to all processors according to the execution sequence. The method realizes the dynamic allocation and the optimized allocation of the task in the heterogeneous computing system through the dynamic selection of the processors to a task to be processed. Compared with the prior art, the invention provides an optimizing scheduling method based on the heterogeneous computing system by considering the optimizing scheduling problem of the heterogeneous computing system from the dynamic angle and utilizing the swarm intelligence technique. The method can perform the dynamic task allocation according to the processing capacities of different processors in the heterogeneous computing system, and considers the possibly occurred competence problem. The invention dynamically considers the computing power of the processors and the loading condition of the processors so as to further quicken the execution time of the heterogeneous computing system.
Owner:EAST CHINA NORMAL UNIVERSITY
Saturation problem moving body attitude event-triggered control method with actuator
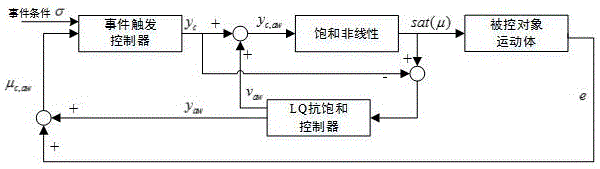
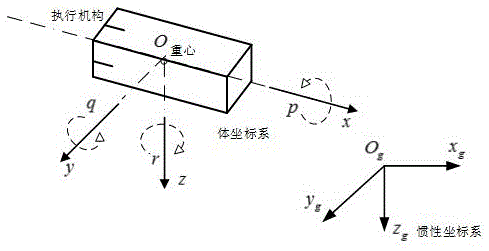
The invention provides a saturation problem moving body attitude event-triggered control method with an actuator. The steps are listed as follows: 1, expected tracking values are given: expected attitude angles phi<d>, theta<d> and psi<d>, and expected attitude angle speed p<d>, q<d>, r<d>; 2, attitude angle tracking error is calculated: attitude angle error phi<e>, theta<e> and psi<e>, and attitude angle speed error q<e>, p<e> and r<e>; 3, an event-triggered controller is designed: feedback gain K<c> is calculated; 4, event-triggered controller output quantity y<c> for eliminating the attitude angle is calculated; and event conditions are designed; 5, control quantity limit is given: saturation control quantity sat(mu) for eliminating the expected attitude angle and attitude angle speed error is calculated; 6, an LQ anti-saturation control compensator is designed: the feedback terms v<aw> and y<aw> of correction control quantity and state quantity are calculated; and 7, input and output mu<c,aw> and y<c,aw> of an event-triggered controller after correction of the LQ anti-saturation control compensator are calculated and applied to a moving body control model. According to the method, problems of actuating mechanism saturation and system data load can be solved, any expected attitude can be tracked and closed loop system asymptotical stability can be guaranteed.
Owner:北京天航华创科技股份有限公司
Unmanned vehicle water detection and tracking method based on SVM and SURF
InactiveCN106203261AImprove detection accuracyImprove execution timeScene recognitionSupport vector machine classifierBrightness perception
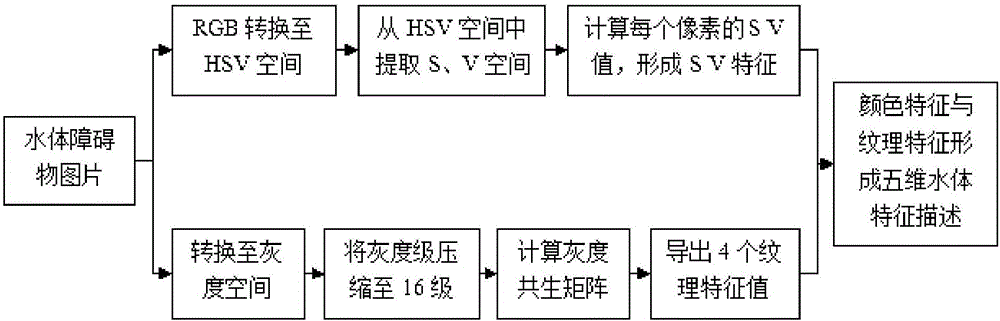
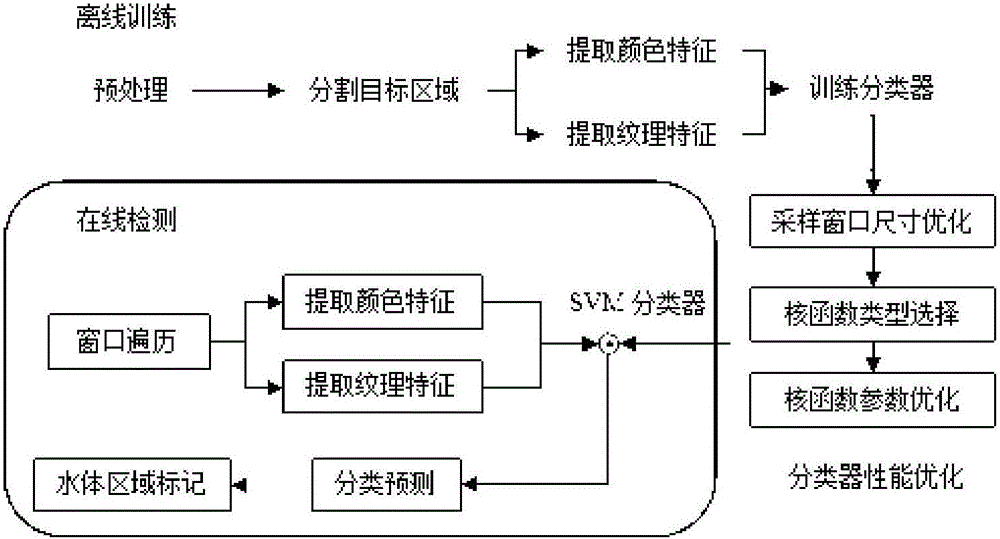
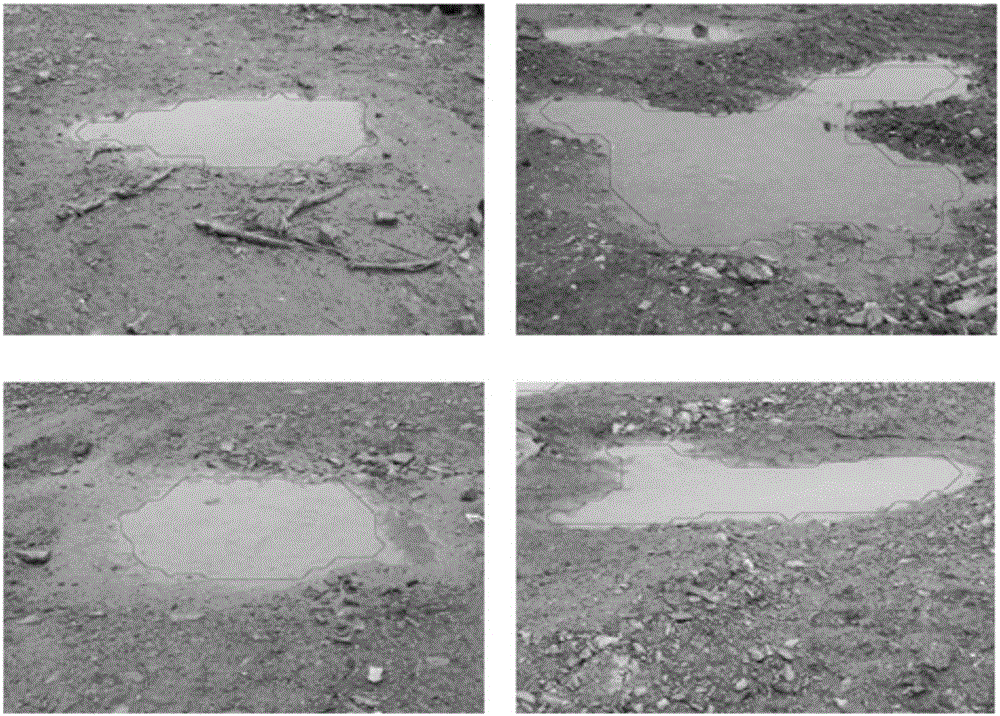
The invention discloses an unmanned vehicle water detection and tracking method based on the SVM and SURF. The method comprises the following steps of extracting color and texture features of a water obstacle; establishing a positive and negative sample bank of a water target and the ground surface, constructing a support vector machine classifier, and updating the search window position and scale based on an SURF algorithm; and detecting and tracking the water obstacle in a real-time video using a support vector machine algorithm. As the four texture features of the water are extracted and the water obstacle S / V is extracted as the color feature at the same time, the texture and color features are combined to constitute the water range features so the invention has higher detection accuracy as compared with a detection method using a brightness feature alone. In the invention, as the SVM algorithm is used for training the color and texture features to obtain the classifier, a kernel function RBF is used for transforming a non-linear problem into a linear problem in the high-dimensional space for solution, so the water detection accuracy is improved.
Owner:DALIAN UNIV OF TECH
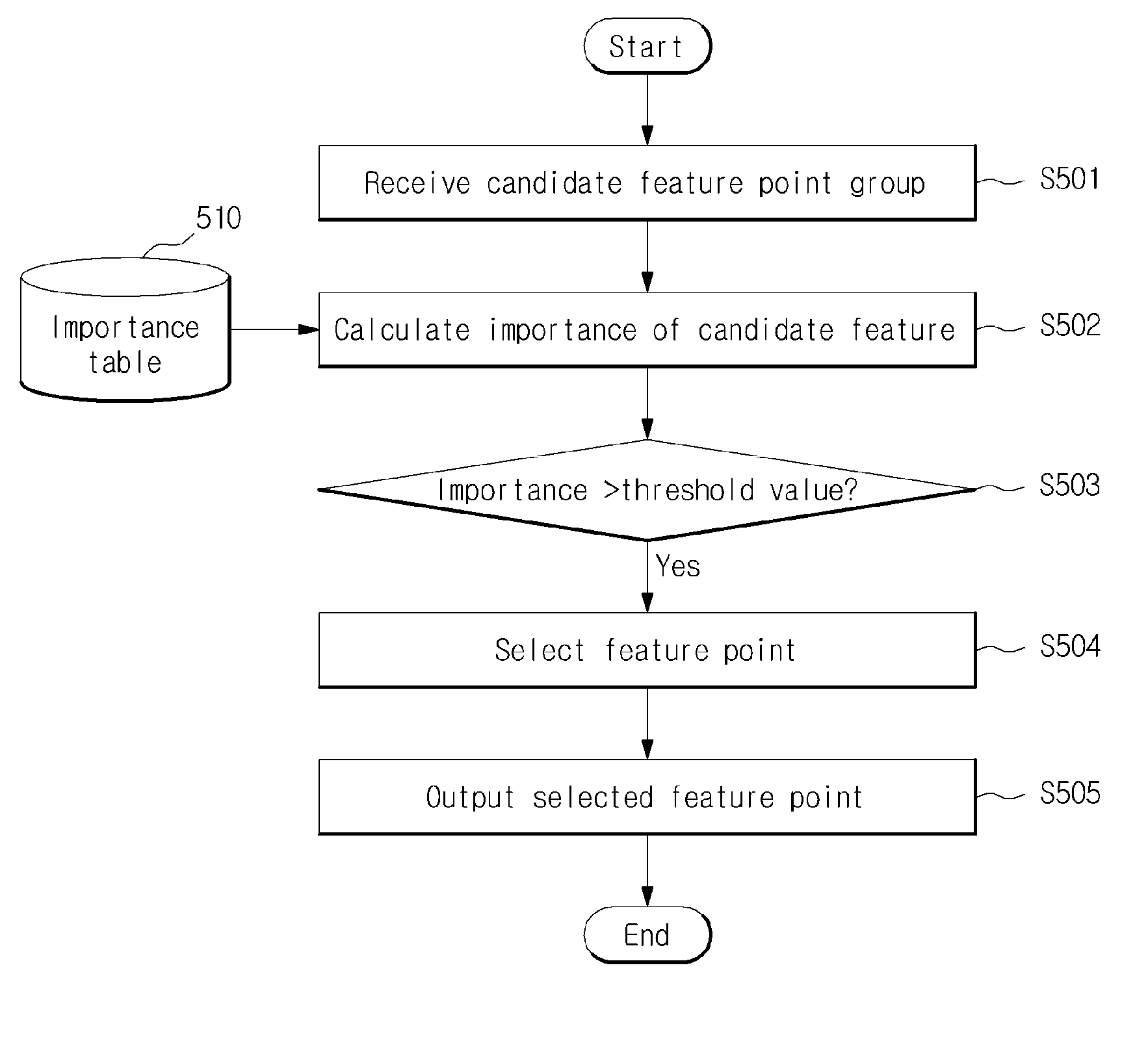
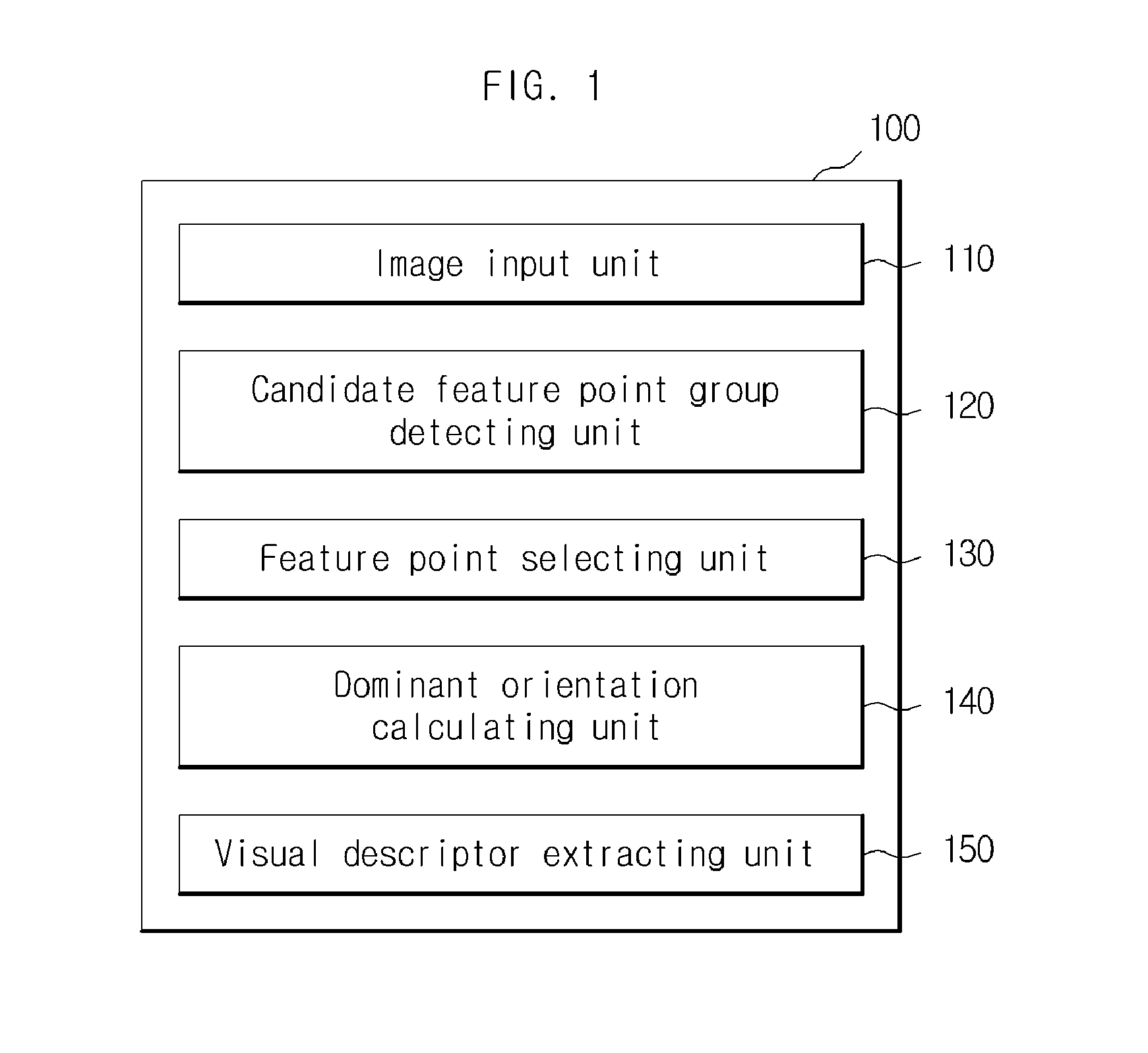
Method of extracting visual descriptor using feature selection and system for the same
ActiveUS20150117785A1Reduce computational complexityImprove efficiencyImage enhancementImage analysisScale spaceFeature selection
A method and system for extracting a visual descriptor using a feature selection are provided. The system includes an image input unit configured to receive an image, a candidate feature point group detecting unit configured to detect a point having a local maximum or minimum of local region filtering in scale-space images as being included in a candidate feature point group, a feature point selecting unit configured to calculate an importance for each candidate feature point, depending on its characteristics, select the candidate feature point as a feature point when its importance is greater than the predetermined threshold value, a dominant orientation calculating unit configured to calculate a dominant orientation of the selected feature point and a visual descriptor extracting unit configured to extract a patch for each feature point, according to its scale, location and dominant orientation, and extract a visual descriptor from the patch.
Owner:ELECTRONICS & TELECOMM RES INST
Fast artistic style study method supporting diverse images
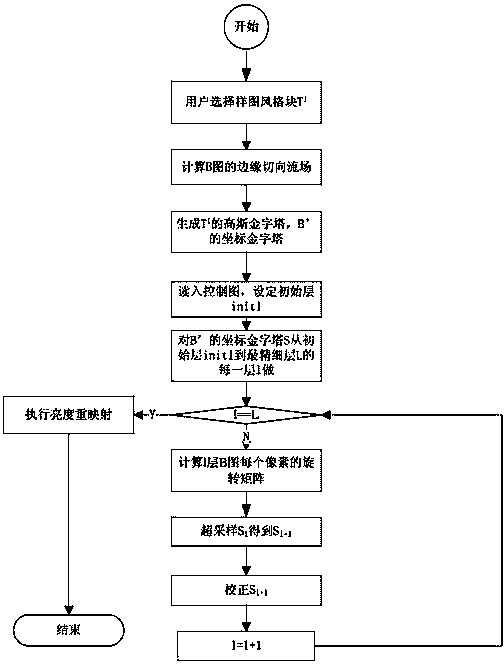
ActiveCN104346789AFast transferUnified streamlinedImage enhancementGeometric image transformationComputer graphics (images)Sample image
The invention provides an artistic style study method supporting diverse images. The input is one group or one artistic master image, a control image and a target image B, the output is an artistic master image B' with the similar style to the sample image, and the method comprises the steps that a user selects a sample pattern style block Ti (i=1, 2, to nexem) capable of best representing the style features from the artistic master image, and the nexem is the number of the sample image style blocks. The Ti is converted into a YIQ space, and a Y passage value is selected to be used as the feature; the edge tangential flow field of the image B (direction B) is calculated; the size of the image B (size B) is used for generating the Ti Gaussian pyramid T=(T0, to Tx, to T<L>) (wherein x is in a range of [0, L]) and generating the coordinate pyramid S=(S0, to Sx, to S<L>) (wherein x is in a range of [0, L], and L=log<2>(sizeB)) of the B', the Tx represent s the x-th layer image of the T Gaussian pyramid of the sample image style block, and the Sx represents the x-th layer image of the coordinate pyramid; the control image is read in ,and the initial layer sinitl is set; the coordinate pyramid of the B' is cyclically subjected to rotating matrix calculation, super sampling and correction steps from the rough layer Sinitl to each layer S1 in the finest layer, and the steps are stopped until the finest layer is reached; the brightness remapping is carried out, and the B' is obtained through calculation.
Owner:ZHEJIANG UNIV OF TECH
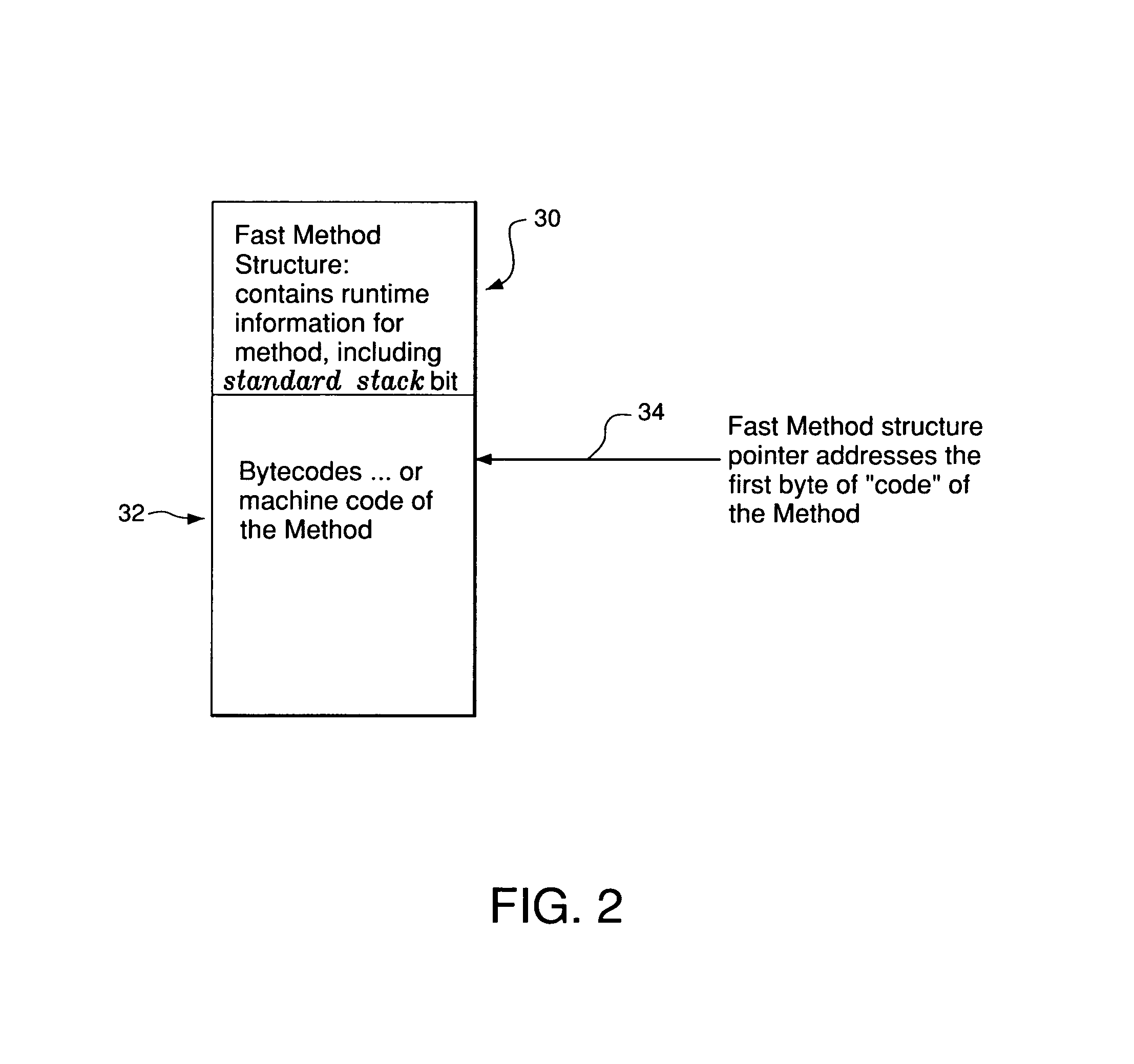
Inter-method control transfer for execution engines with memory constraints
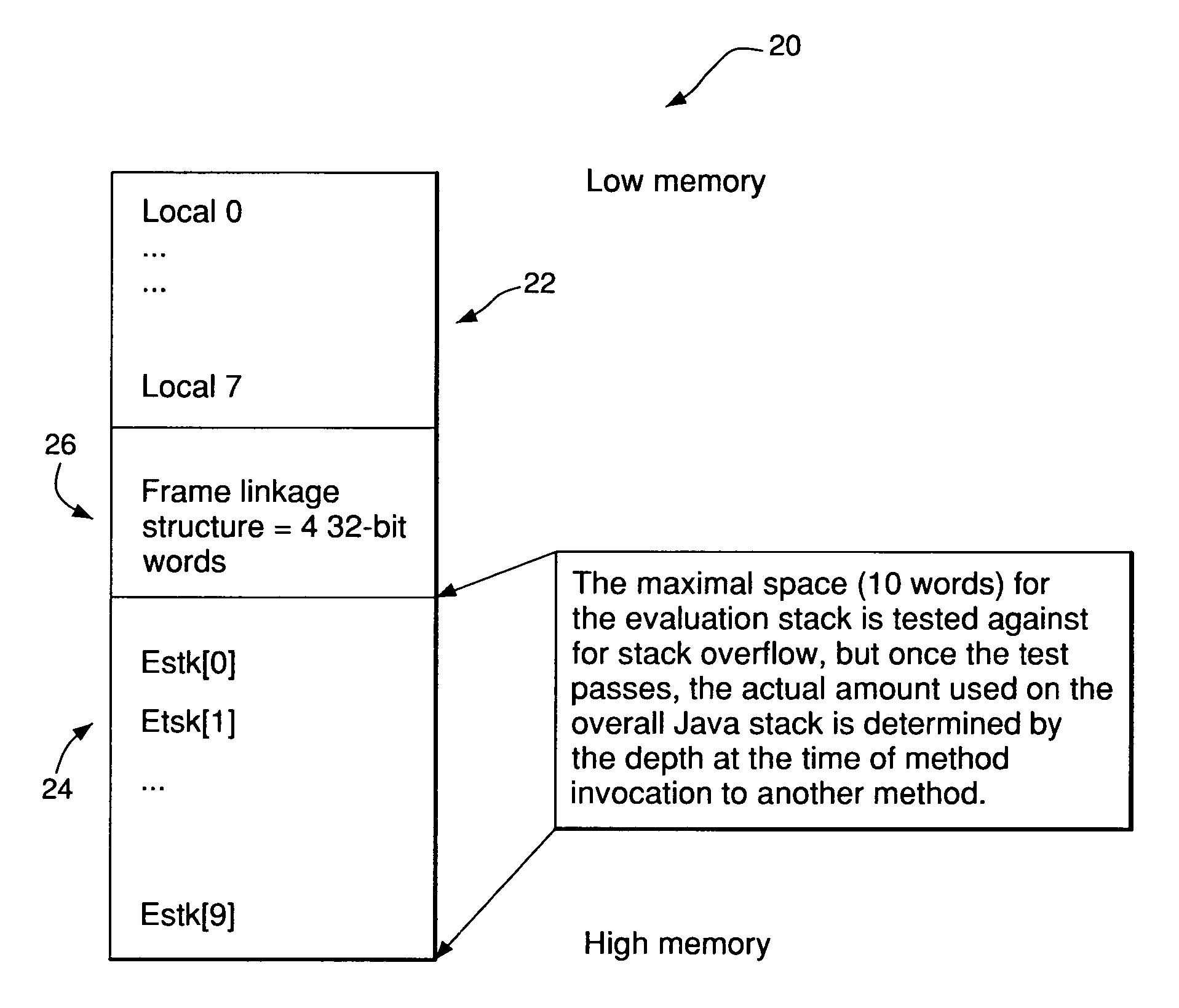
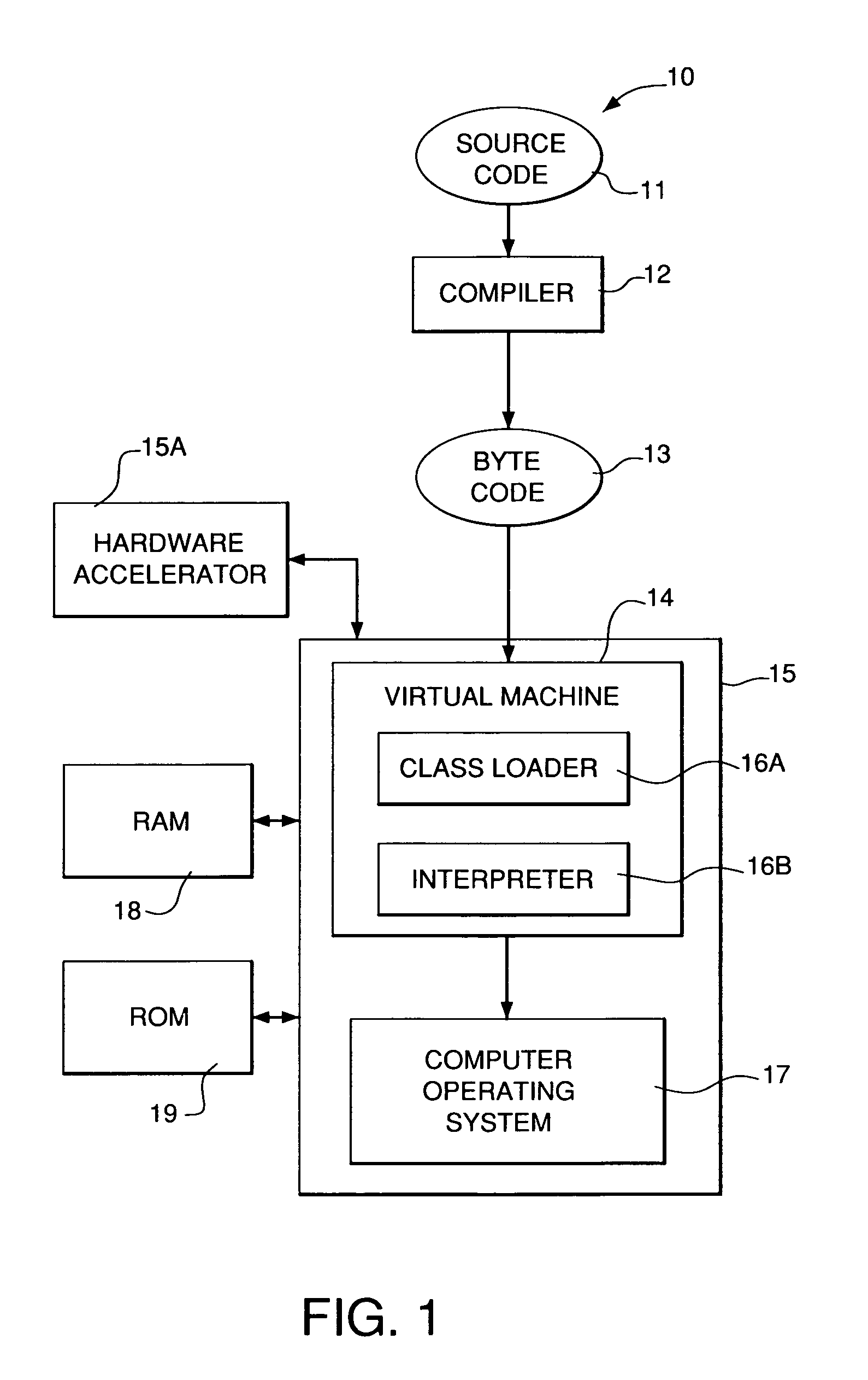
InactiveUS6976254B2Reduce execution engine overheadImprove execution timeMultiprogramming arrangementsComputer security arrangementsAccess structureFrame based
A bytecode execution system and method for increasing the execution speed of invoking and returning from Methods while minimizing the memory footprint required to support this. The system includes a virtual machine with a class loader and an interpreter or, alternatively, a hardware accelerator. Speed and memory enhancements are realized by establishing an activation stack frame template with a set of criteria. Each Method from subject code is examined to determine whether the Method conforms to the criteria of the stack frame template. If the Method conforms, an activation frame for that Method based on the activation stack frame template is created when the Method is invoked. Otherwise, an activation frame based on standard virtual machine criteria is created. An access structure is associated with each Method and a Method routing structure is created for each class.
Owner:MYRIAD GROUP
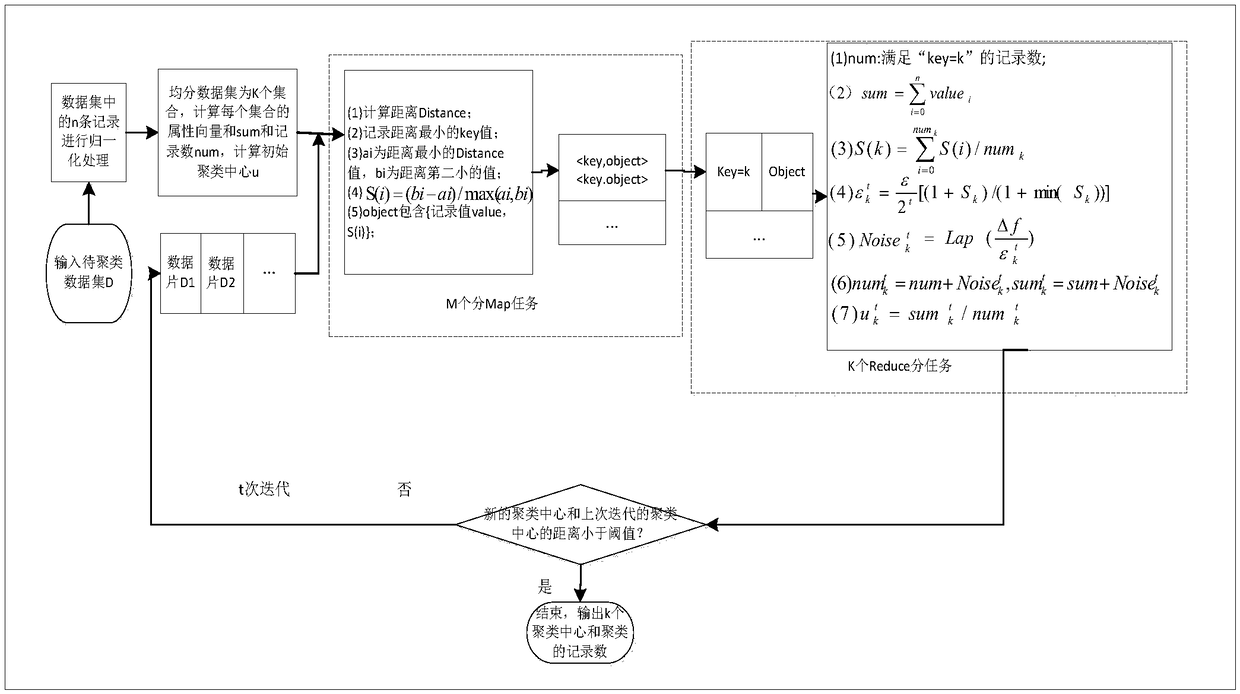
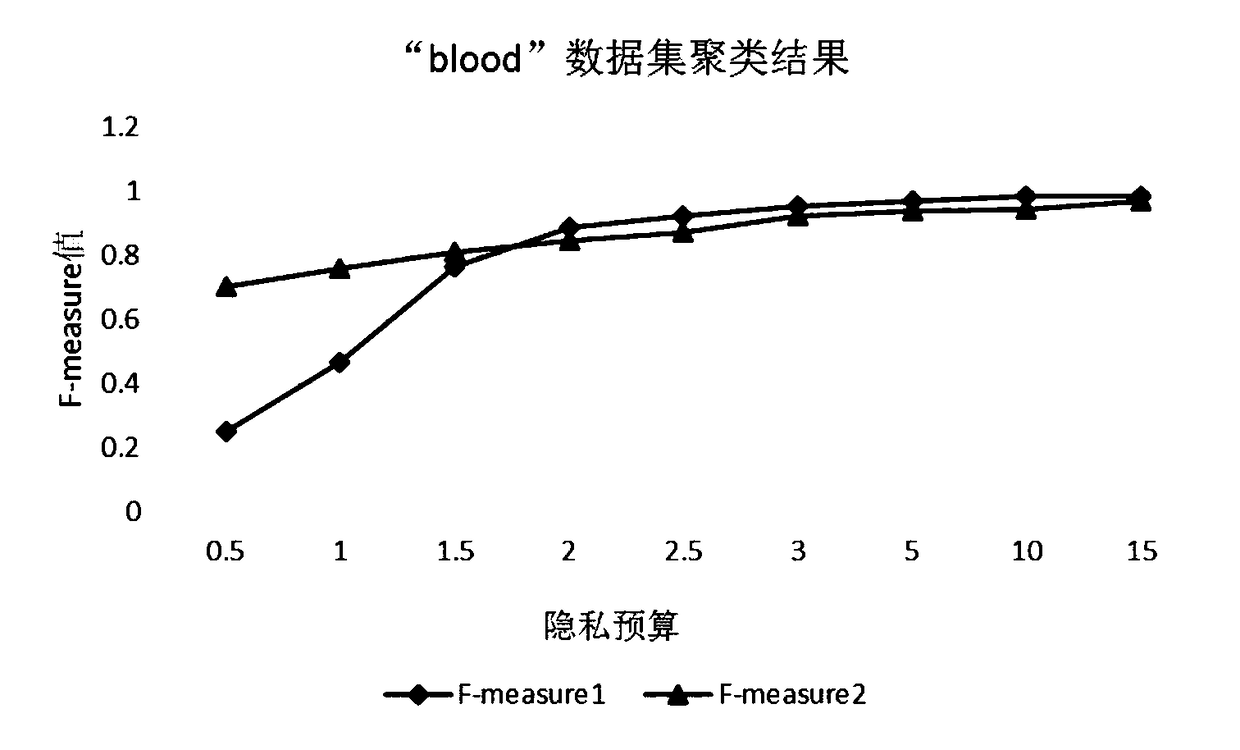
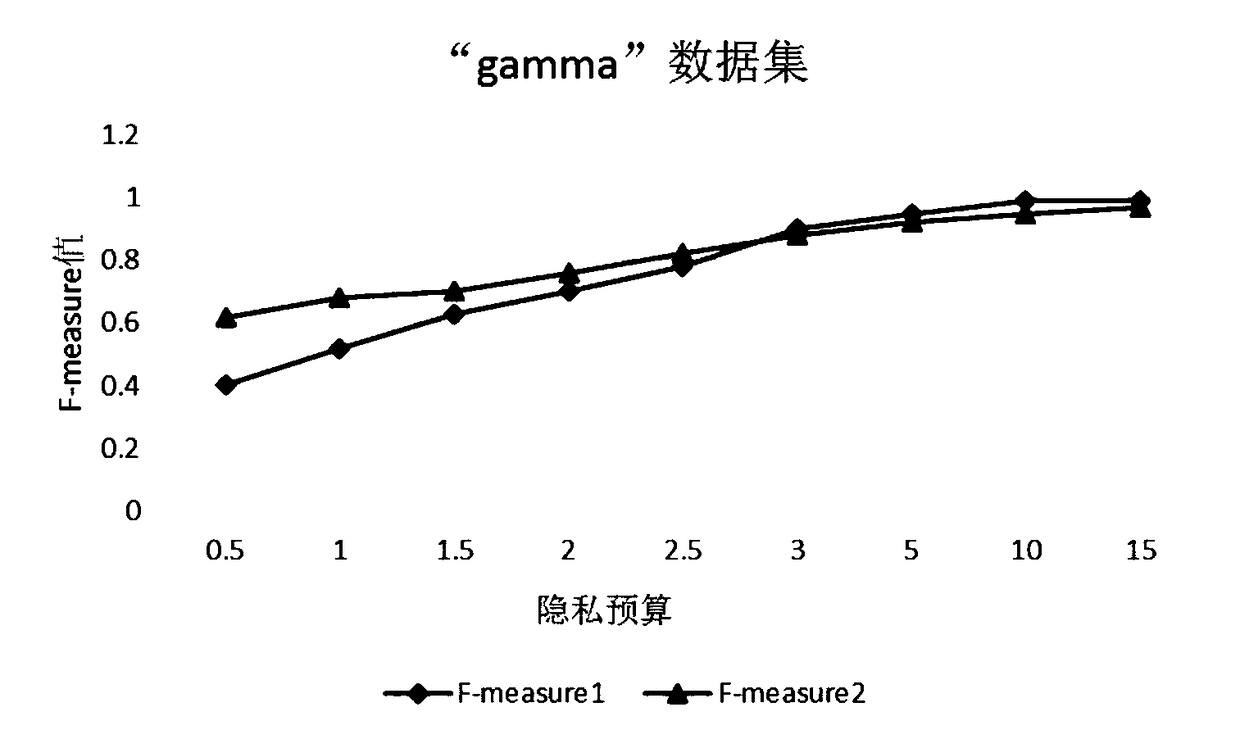
Difference privacy protection K-means cluster method based on profile coefficient
InactiveCN108549904AAlgorithm stability is goodReduce the number of iterationsCharacter and pattern recognitionSpecial data processing applicationsPrivacy protectionData set
The invention discloses a difference privacy protection K-means cluster method based on a profile coefficient; the method comprises the following steps: 1, normalizing all data in a data set D; 2, averagely dividing the data set D with N records into K sets; 3, solving an attribute vector sum (sum <o><k>) and a record number (num <0><k>) of all records in a set Ck; 4, calculating the distance between each record (ai) to the center (uk) of K clusters; 5, calculating the recording number (num) of the cluster and the attribute vector (sum) of all records; 6, calculating a profile coefficient Sk of the k clusters, and adding random noises (noise <t><k>) onto numk and sumk; 7, calculating a new cluster center; 8, calculating the distance between the new cluster center and the cluster center ofthe previous iteration, and finishing the algorithm if the distance is smaller than a threshold. An existing method in the big data cluster analysis under a distributed environment is severe in information leakage; the difference privacy protection K-means cluster method can solve said problems.
Owner:XIAN UNIV OF TECH
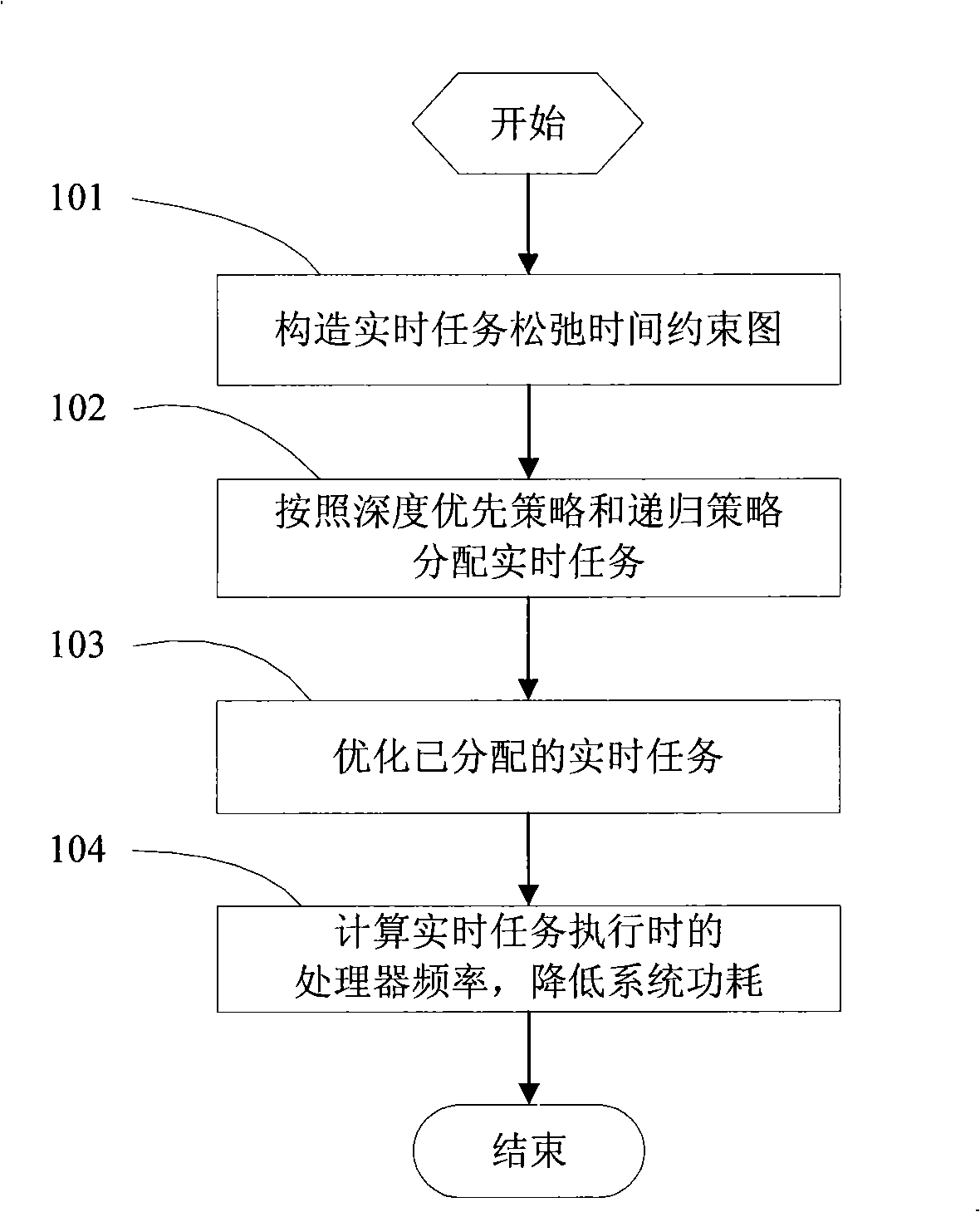
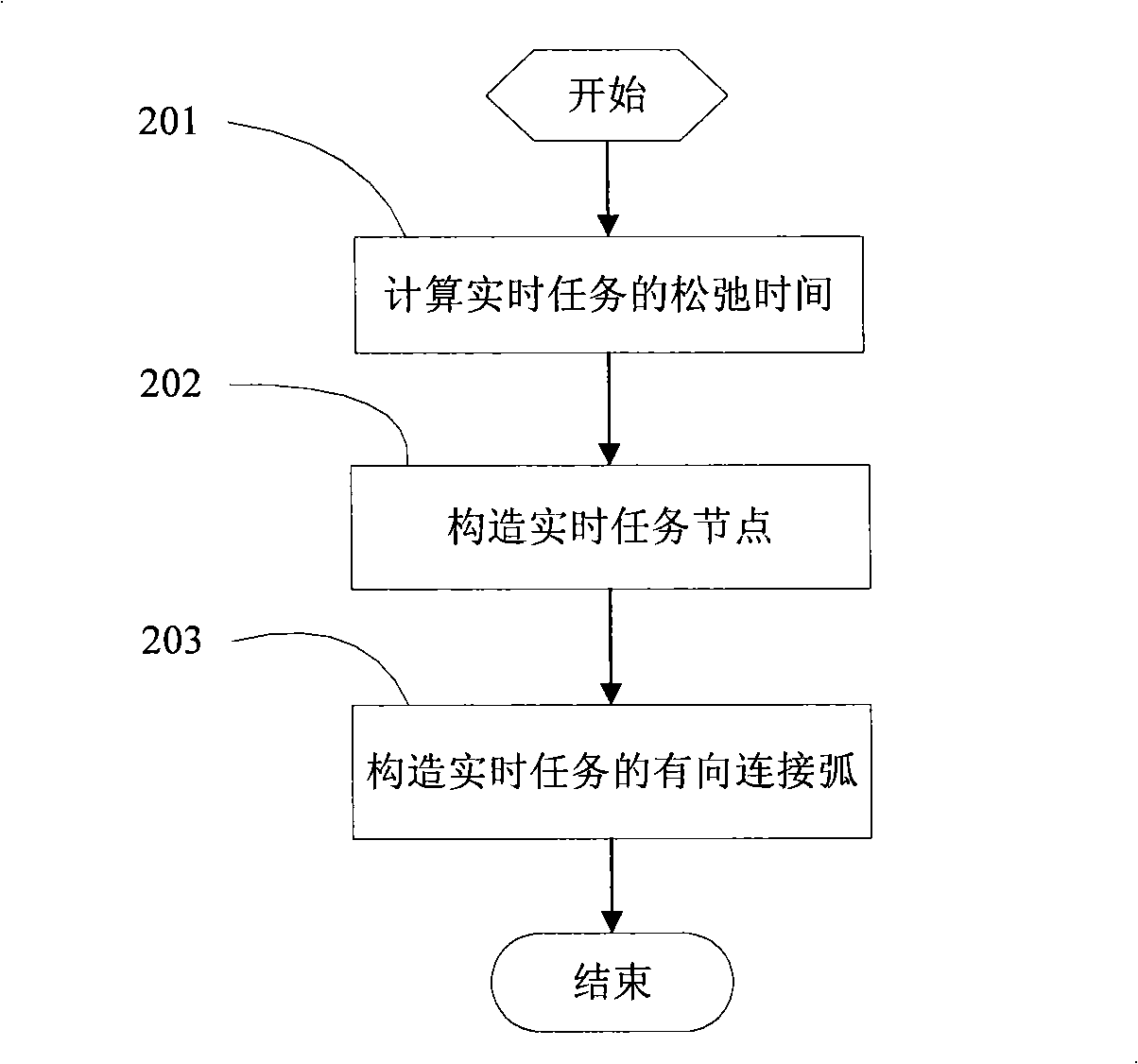
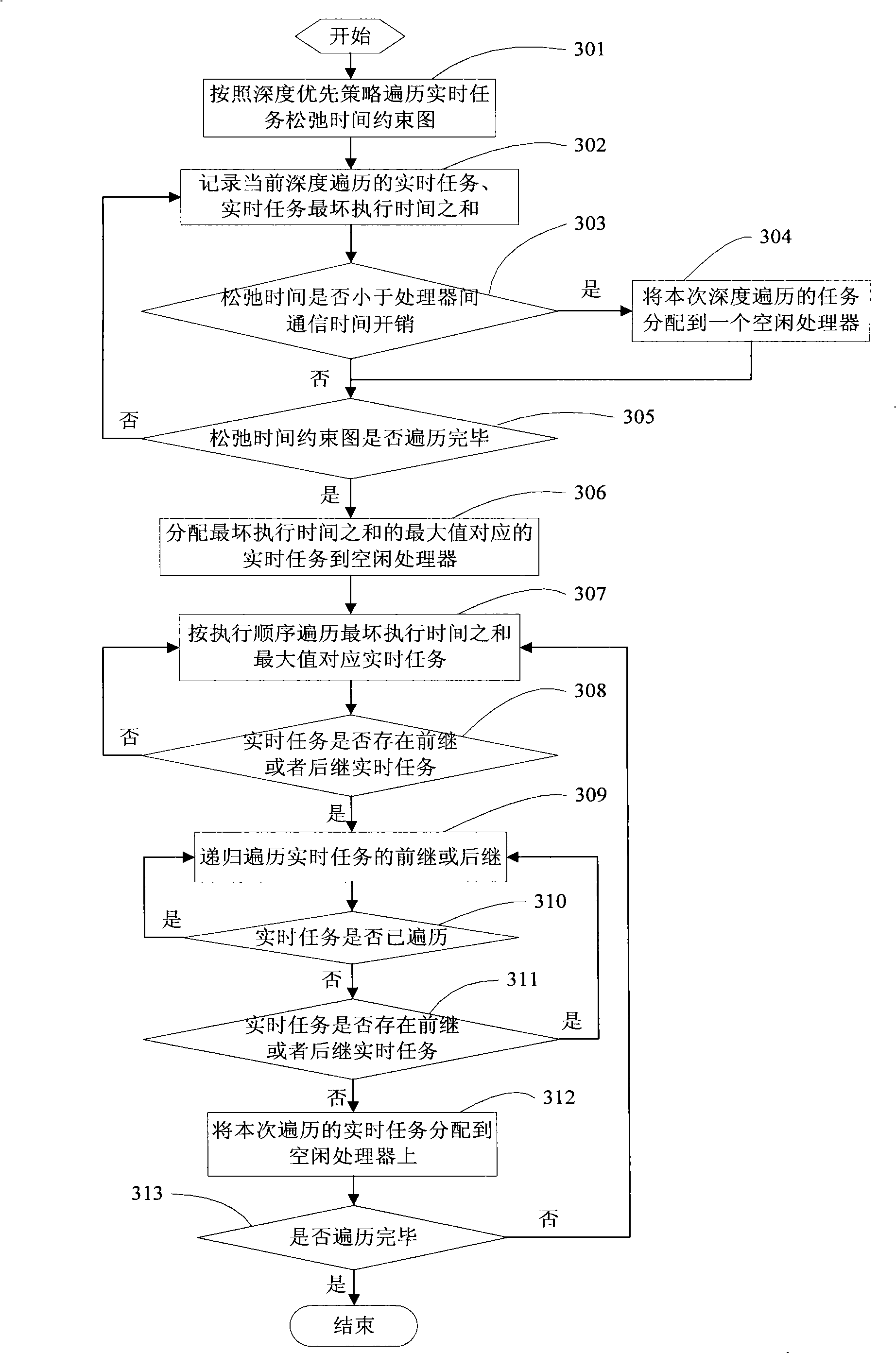
Method of optimization of multiprocessor real-time task execution power consumption
InactiveCN101303657AImprove execution timeReduce power consumptionEnergy efficient ICTResource allocationMulti processorRelease time
The invention discloses a method for optimizing the power consumption for implementing the real time tasks of multi-processors, which reduces the power consumption of a system by prolonging the implementing time of the real time tasks by utilizing the slack time of the real time tasks. First, the slack time restraining graph of the real time tasks is constructed by utilizing the restraining relation between the release time, the worst implementing time, the absolute deadline of the real time tasks and the tasks; second, the real time tasks in the slack time restraining graph of the real time tasks are distributed according to a depth-first strategy and a recursion strategy; then the distributed real time tasks are optimized by deleting the repeated real time tasks; finally the power consumption of the system is reduced by prolonging the implementing time of the real time tasks to the largest implementing time that can be prolonged through calculating the largest implementing time that can be implemented of the real time tasks according to an extent preference strategy.
Owner:SHANGHAI UNIV
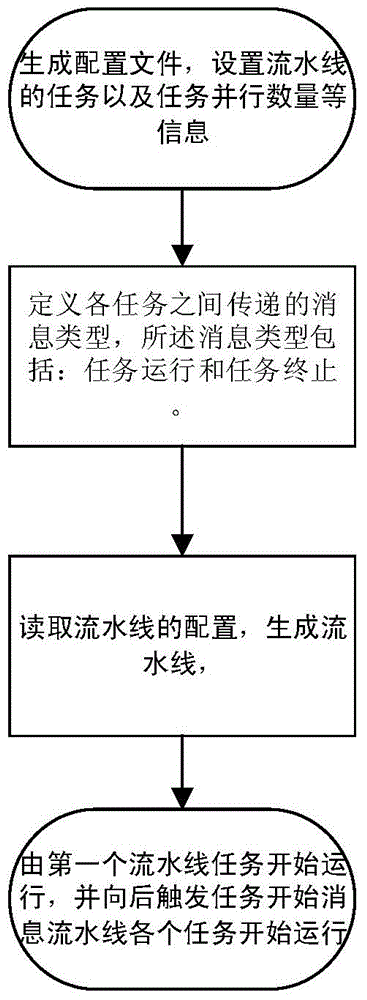
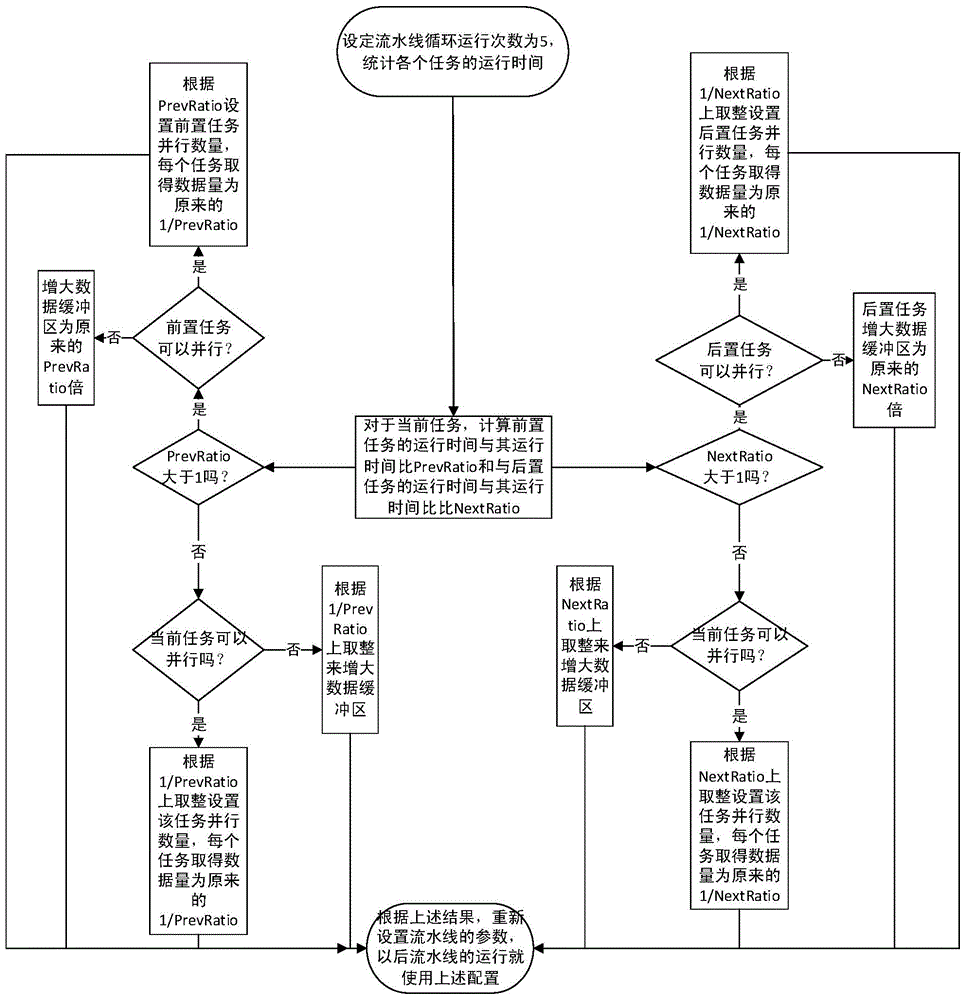
Flow line task self-adaptation parallelization method
InactiveCN104615413AImprove execution timeReduce waiting timeConcurrent instruction executionTask controlSoftware execution
The invention relates to a flow line task self-adaptation parallelization method which includes flow line initializing setting and task self-adaptation disintegration. The method has the advantages that the tasks long in execution time is disintegrated into small tasks according to the execution time of each task; a configuration file is used to configure each task of a flow line from starting to ending, each task can have many pre-tasks and subsequent tasks, and different tasks control task contents and task completing progress through messages; the method is achieved through a parallelization distribution processing algorithm, overall software execution speed is conveniently and effectively increased by self-adaptation task disintegration, and user waiting time is reduced.
Owner:SAINUO WEISHENG SCI & TECH BEIJING
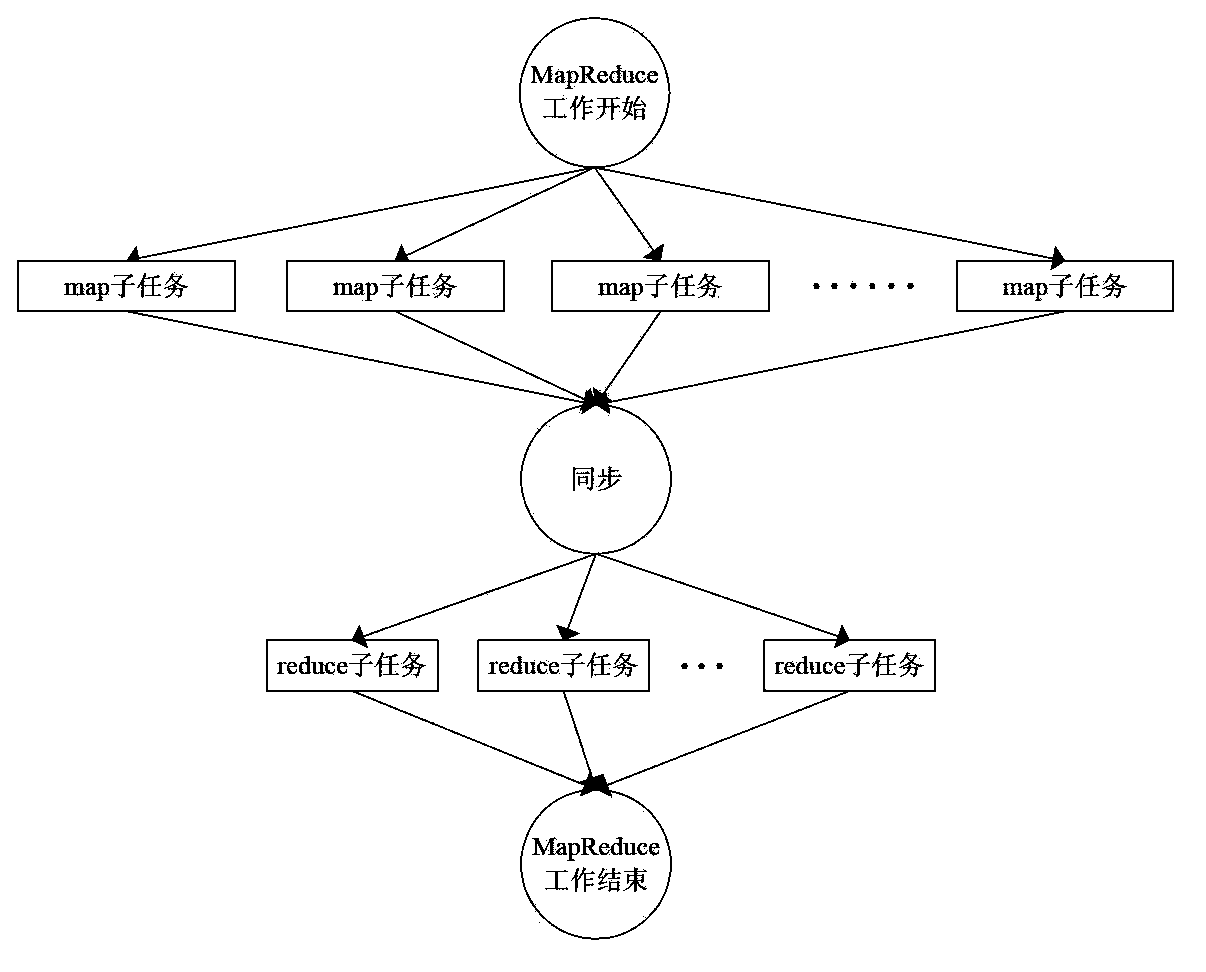
Non-accurate task parallel processing method based on MapReduce
ActiveCN103645952AImprove execution timeImprove execution efficiencyResource allocationConcurrent instruction executionParallel processingTask parallelism
A non-accurate task parallel processing method based on MapReduce comprises the steps that (1) M Map subtask executing nodes and a Check node are selected, and the Check node stores logic for judging whether a task to be executed with non-accuracy computing feature is completed; (2) the task is divided into N Map subtasks to be distributed to the M executing nodes for executing; (3) after each Map subtask is executed, task executing-finishing information and result information related to judging logic are sent to the Check node; (4) each time the Map subtask executing-finishing information is received, the information is accumulated into the previous result by the Check node until the accumulated result meets the requirement of judging logic; (5) Map subtasks in which the executing-finishing information is not received by the Check node are ended, a Map task executing process is finished, and a Reduce subtask is carried out synchronously; and (6) the Reduce task executing result is obtained, and whole task executing is finished.
Owner:NAT UNIV OF DEFENSE TECH
Protein rapid detection method based on matched microalgae protein characteristics sequence label and system thereof
The invention discloses a protein rapid detection method based on a matched microalgae protein characteristics sequence label and a system thereof; the method includes steps of collecting a microalgae sample, and acquiring its protein sequence set, converting it to a standard protein sequence set, performing splitting and configuration treatment, and converting the protein sequence set to a key / value pair list specific to a given sequence segment; after summarizing the key / value pair list, performing an intersection operation; when the result is not empty, confirming that one data of the data set contains the characteristic protein sequence. The system mainly includes a detection data input module, a key / value pair list module, a detection identification module, a characteristic value intersection operation module, and an output module. Through indexing the protein sequence, the method and the system judge the protein homology and similarity level; by comparing with the traditional method of comparing data one by one, the algorithmic identification accuracy is and efficiency are significantly improved, the indexing efficiency is greatly promoted; the method and system have good practicability, and the algorithmic time complexity is low, the performance is high; therefore, the method and the system are significant to study proteomics.
Owner:THE FIRST INST OF OCEANOGRAPHY SOA
Secure cloud data deduplication method and system based on trusted hardware
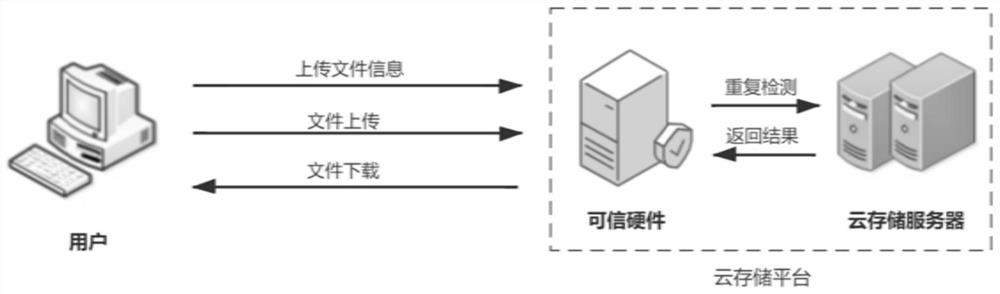
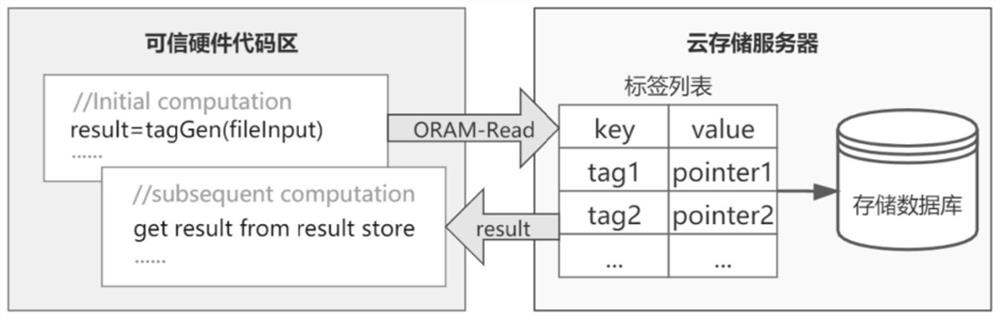
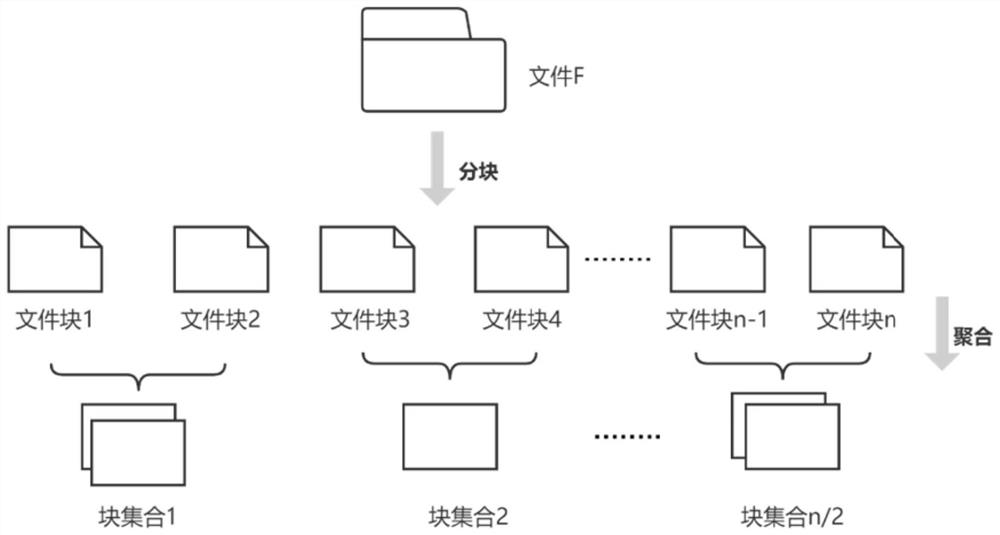
PendingCN113918528AGuaranteed safe transmissionSafe deduplication processDigital data protectionDigital data authenticationCloud storageEngineering
The invention discloses a secure cloud data deduplication method and system based on trusted hardware. Comprising the following steps: firstly, performing data encryption and label generation on an original file; sending the encrypted file and a corresponding label to a cloud storage platform; and enabling the cloud storage platform to store the to-be-encrypted file without the same copy after repeatedly detecting the label, and assigning the file permission. A secure trusted hardware area TH is configured in a cloud storage platform, all algorithms and operations related to user file privacy are realized in trusted hardware, and a code running in the trusted hardware is called CEnclave. Before a user communicates with a cloud storage platform, remote authentication needs to be carried out on the user and the TH to ensure secure transmission of data, and after the TH receives the data transmitted by the user, ORAM implicit reading is carried out on the TH and a cloud storage server CSS to realize a secure de-duplication process.
Owner:XI AN JIAOTONG UNIV
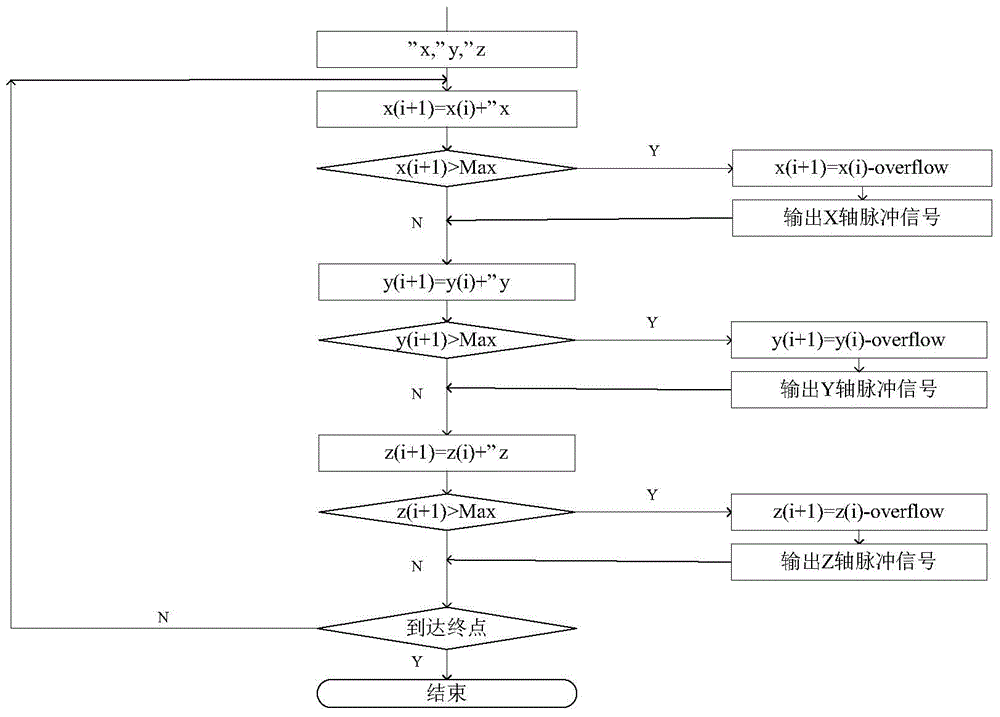
Optimized NURBS and DDA curve two level interpolation method
ActiveCN104636522AReduce communication delayReduce sizeSpecial data processing applicationsComputer science
The invention relates to an optimized NURBS and DDA curve two level interpolation method which is composed of a track generation phase, a conversion phase and a DDA interpolation phase. The track generation phase mainly executes NURBS interpolation algorithm, a position of a corresponding point of the next interpolation period is generated according to the track generation algorithm. The DDA interpolation phase mainly generates corresponding servo burst according to the position increment of each interpolation period to transmit to a servo system. The conversion phase mainly converts the position of each interpolation period in the NURBS interpolation phase into a position increment of the DDA phase. Each phase is connected through fifo. The optimized NURBS and DDA curve two level interpolation method has the advantages that the system communication delay is low, the efficiency is high, the portability is good, and the program is friendly to Cache.
Owner:中国科学院沈阳计算技术研究所有限公司
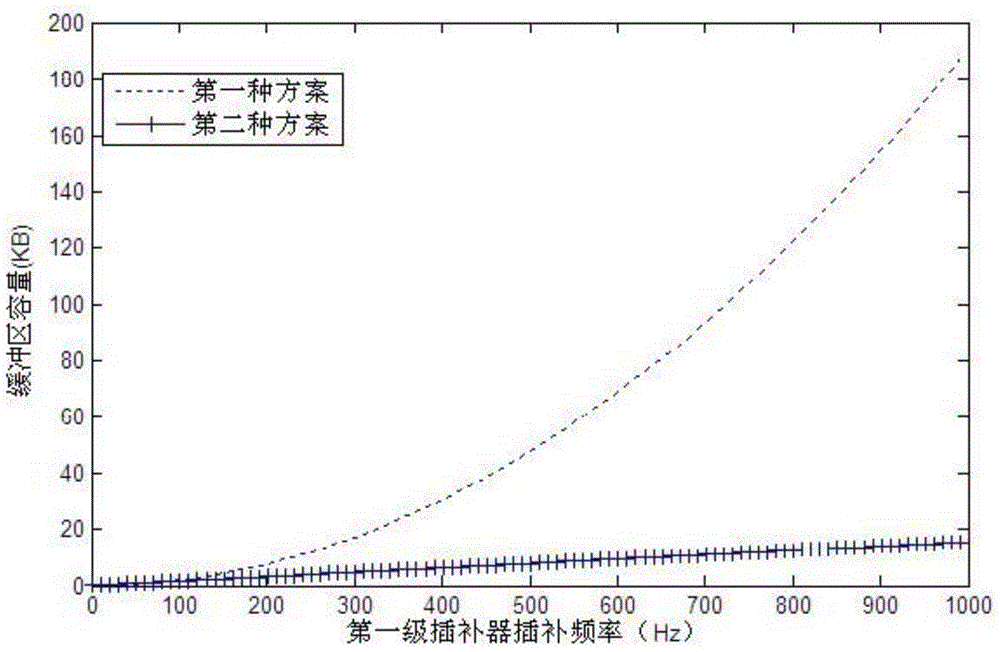
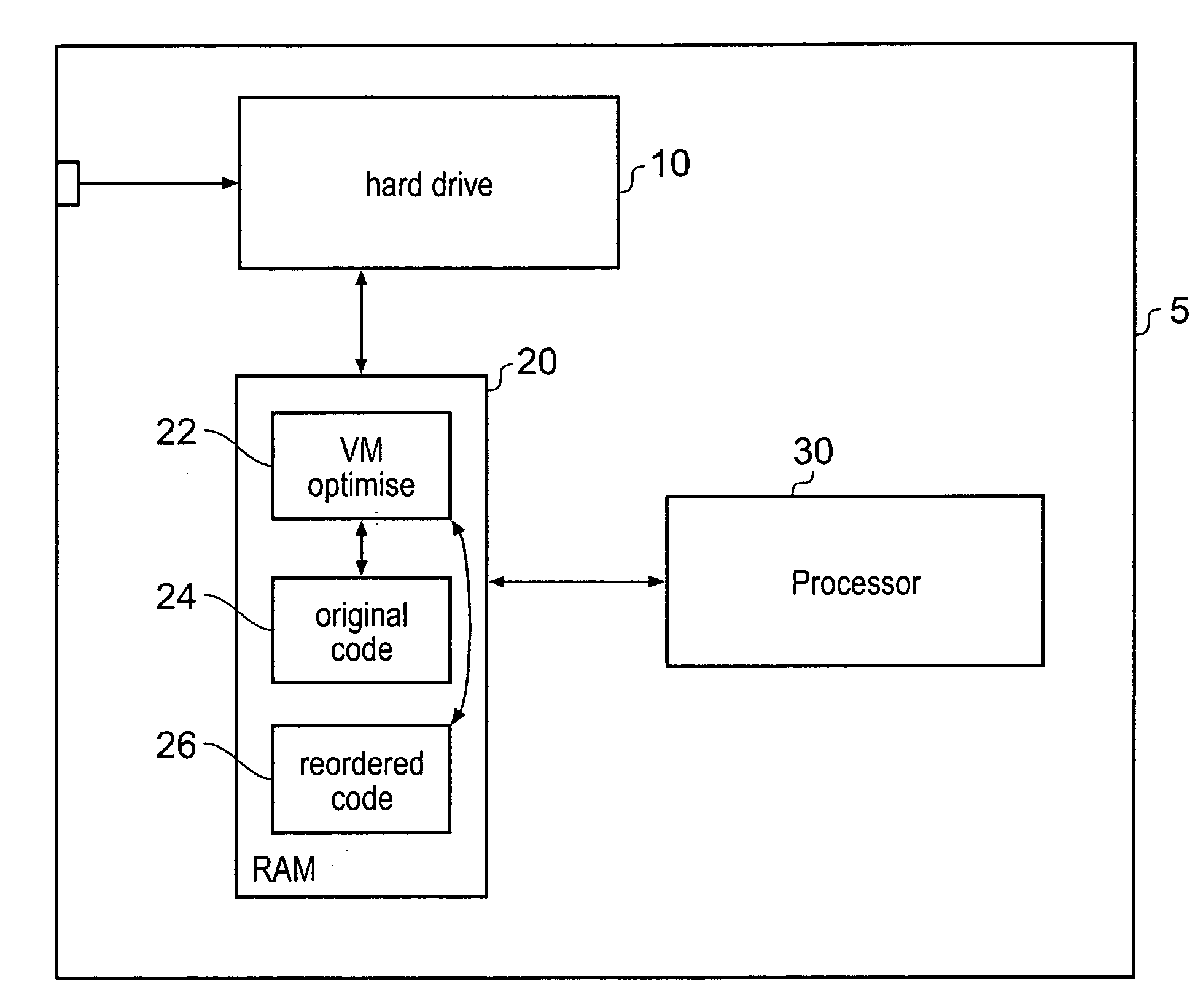
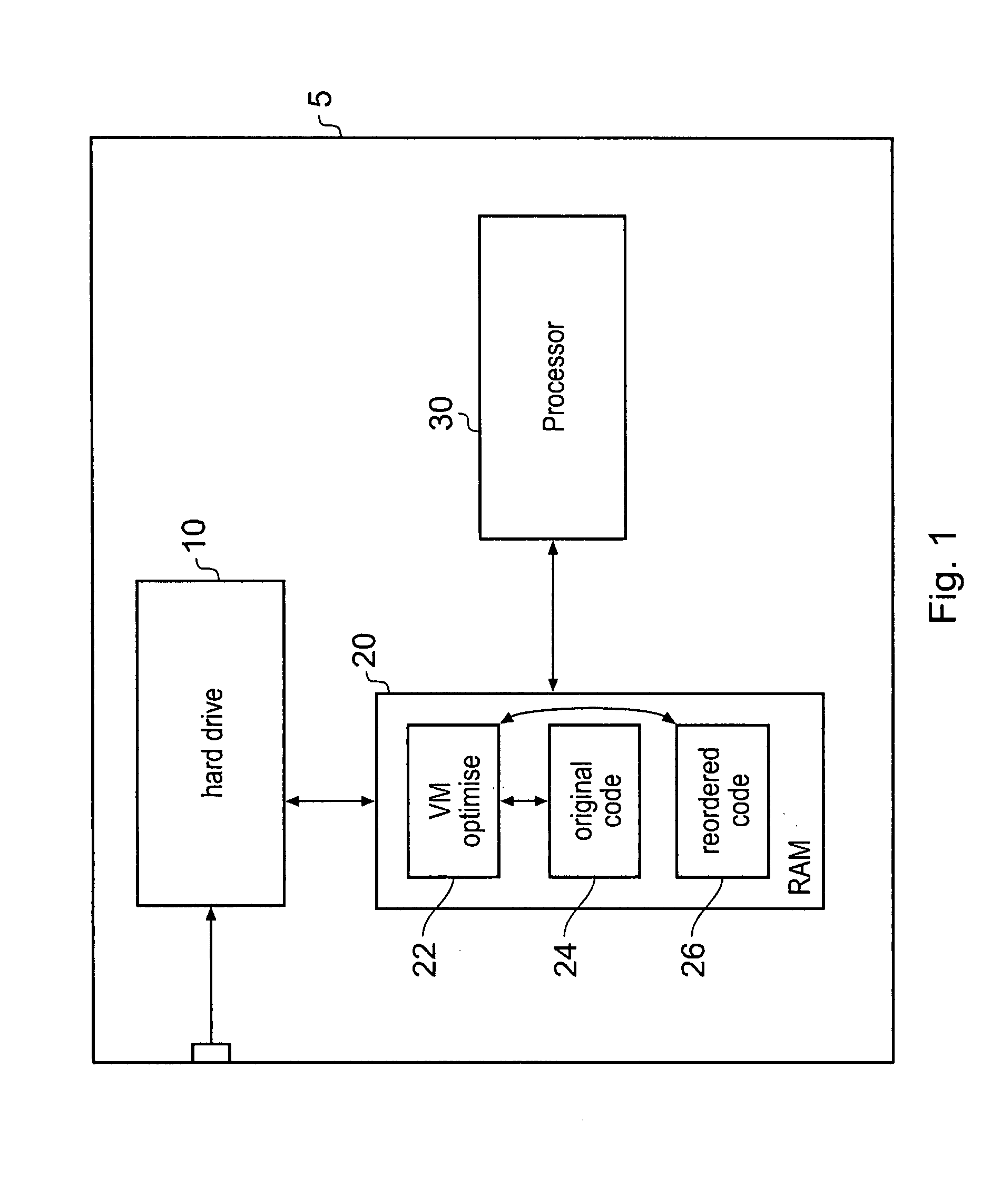
Reordering application code to improve processing performance
ActiveUS20080201698A1Improve performanceImprove execution timeSoftware engineeringDigital computer detailsData memoryApplication software
A method of reordering a sequence of code for processing by a target data processor in order to reduce an execution time for said code on said target data processor is disclosed. The method comprises the steps of: in response to a request to execute said sequence of code, loading said sequence of code into a volatile data store associated with said target data processor; analyzing said sequence of code in relation to properties of said target data processor; identifying interlocks within said sequence of code when executing on said target data processor, in which a portion of code would be stalled while waiting for an earlier portion to complete; reordering said sequence of code to remove at least some of said interlocks; and executing said reordered sequence of code; wherein said steps of analyzing, identifying, reordering and executing are performed by said target data processor.
Owner:ARM LTD
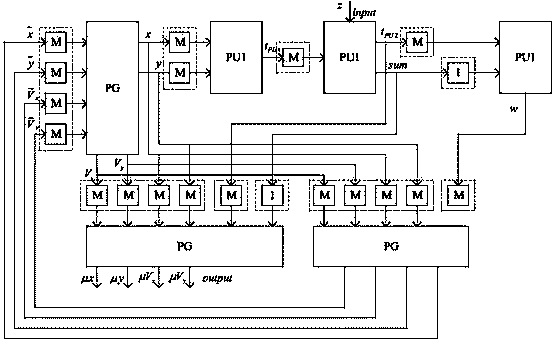
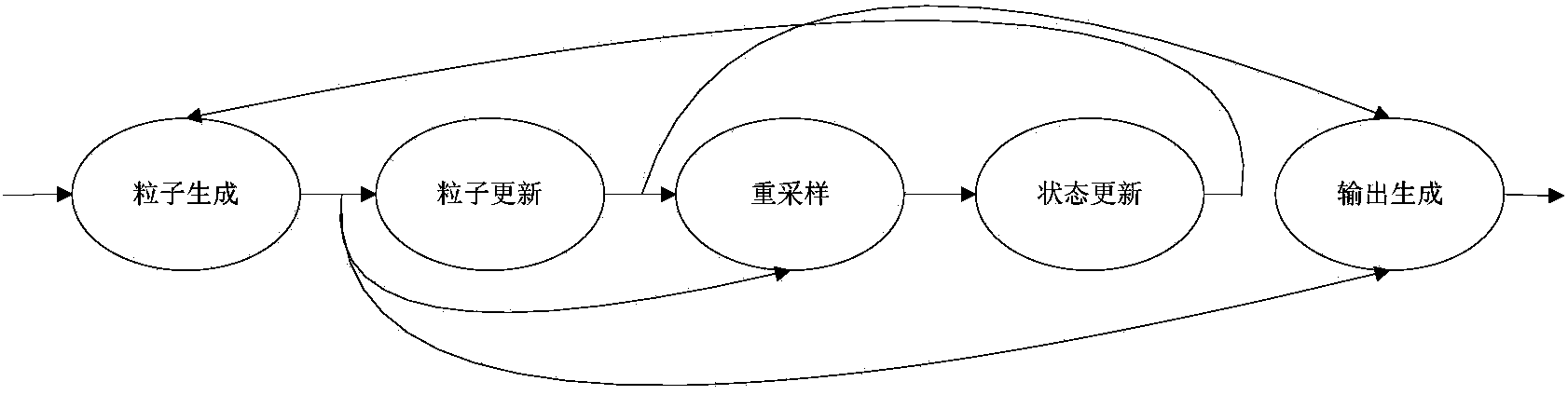
Sample importance resample particle filter hardware implementation method based on FPGA
ActiveCN104009733AImprove execution timeReduce Algorithmic ComplexityDigital technique networkHardware implementationsComputer science
The invention discloses a sample importance resample particle filter hardware implementation method based on an FPGA. The method includes the following steps that firstly, a particle generation module is used for receiving input vectors to generate particles and then outputting the particles to a particle renewing module and a resample module; secondly, the particle renewing module is used for conducting renewing, namely, weight calculation and weight normalization, on the particles generated in the first step and then outputting the particles to the resample module; thirdly, the resample module conducts resample and state renewing on the particles renewed in the second step or the particles generated in the first step and then feeding the particles back to the particle generation module in the first step; fourthly, an output generation module conducts data generation and output on the particles renewed in the second step or the particles generated in the first step.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
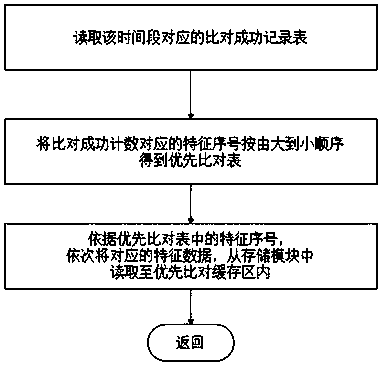
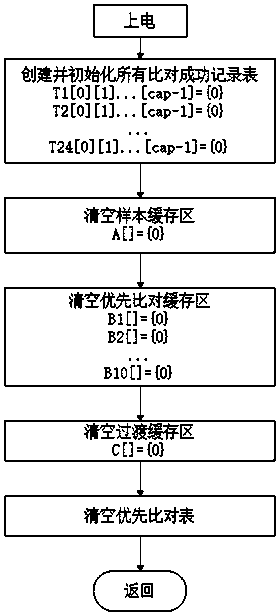
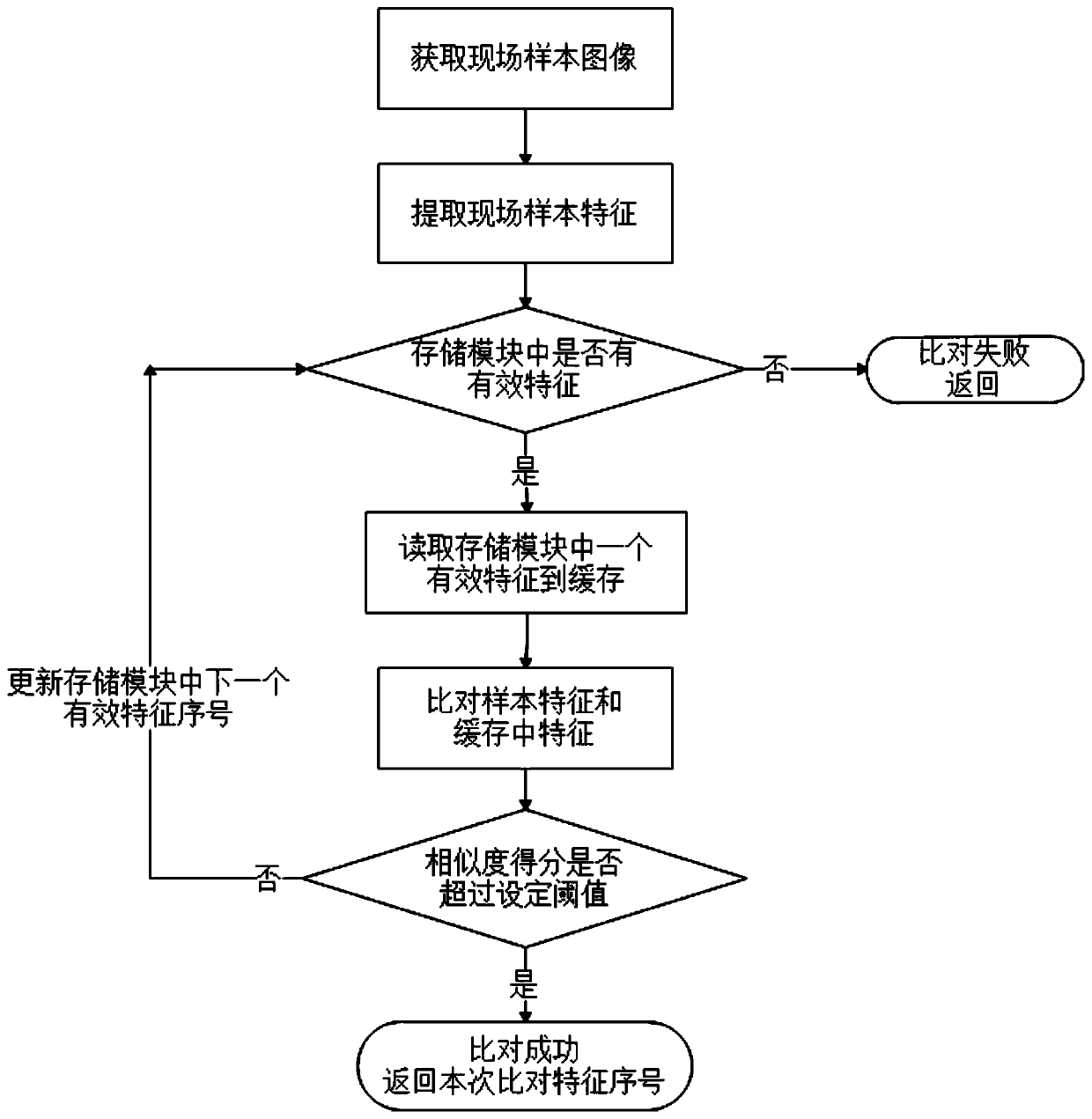
Electronic device and method for quickly feeding back comparison result in fingerprint identification system
InactiveCN110569748AShorten read timeReduced execution timeMatching and classificationFeature dataSerial code
The invention relates to an electronic device and method for quickly feeding back a comparison result in a fingerprint identification system, and the electronic device comprises a storage module, a comparison module, a clock module, a sample cache region, a transition cache region, a priority comparison cache region, a comparison success record table, and a priority comparison table. The method for quickly feeding back the comparison result in the fingerprint identification system specifically comprises the following steps: pre-reading; collecting field sample characteristic data; comparing. The method has the beneficial effects that by combining the previous time when comparison succeeds and the matching feature serial number, a plurality of groups of feature data with high comparison success frequency are loaded into the cache in advance, so that the reading time of a part of feature data is reduced, and the blind sequential reading of the feature data from the storage module is avoided; the whole process execution time is shortened; random comparison is avoided, and the execution time of comparison operation is shortened; the user experience is improved.
Owner:HANGZHOU ZHIAN TECH
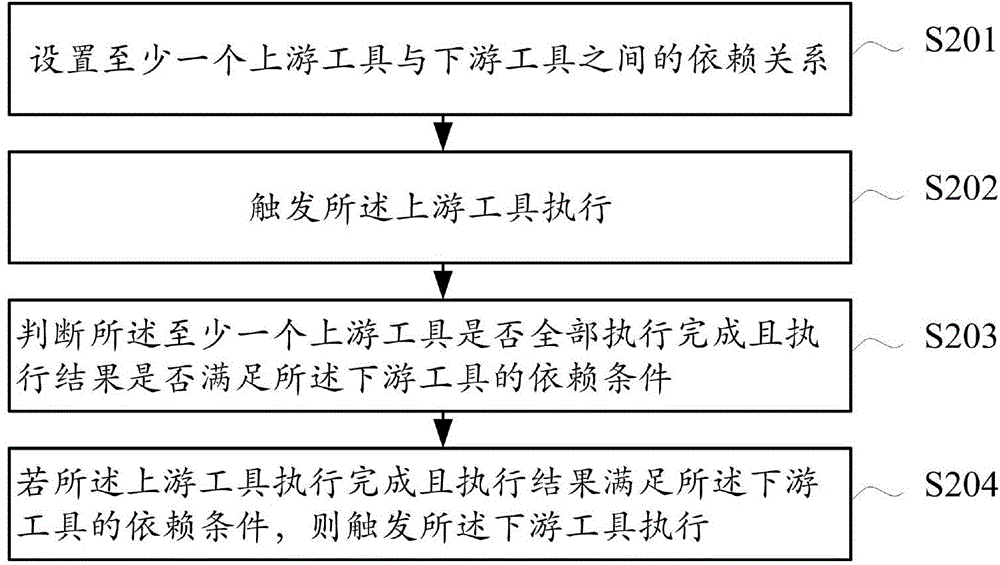
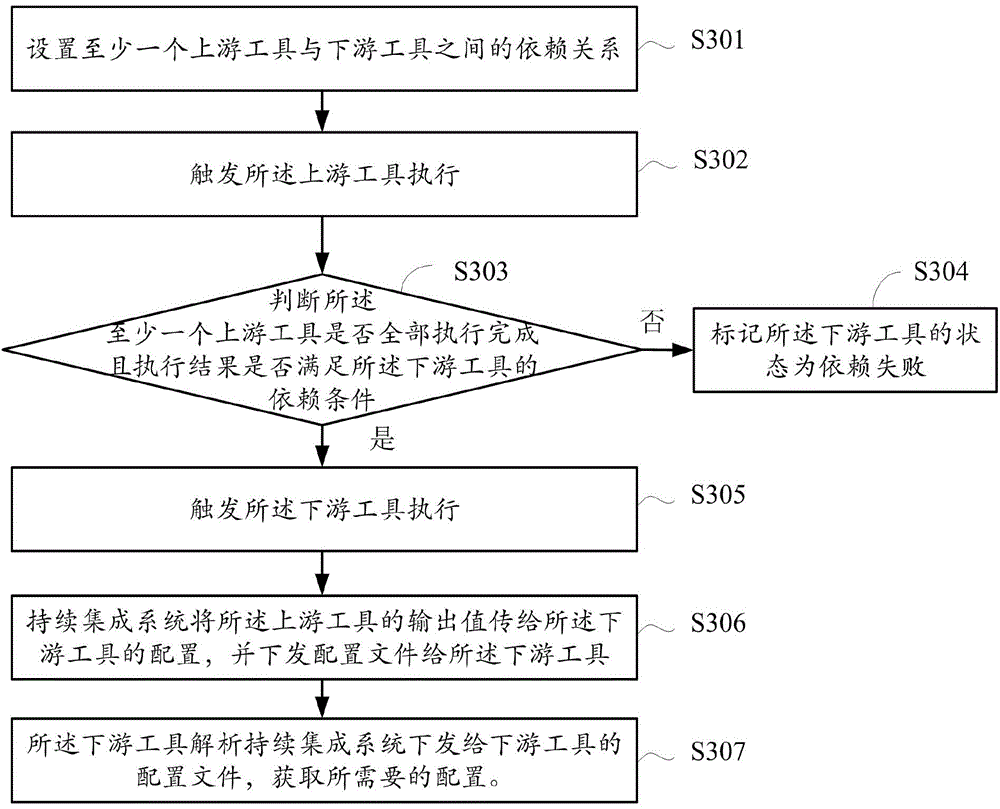
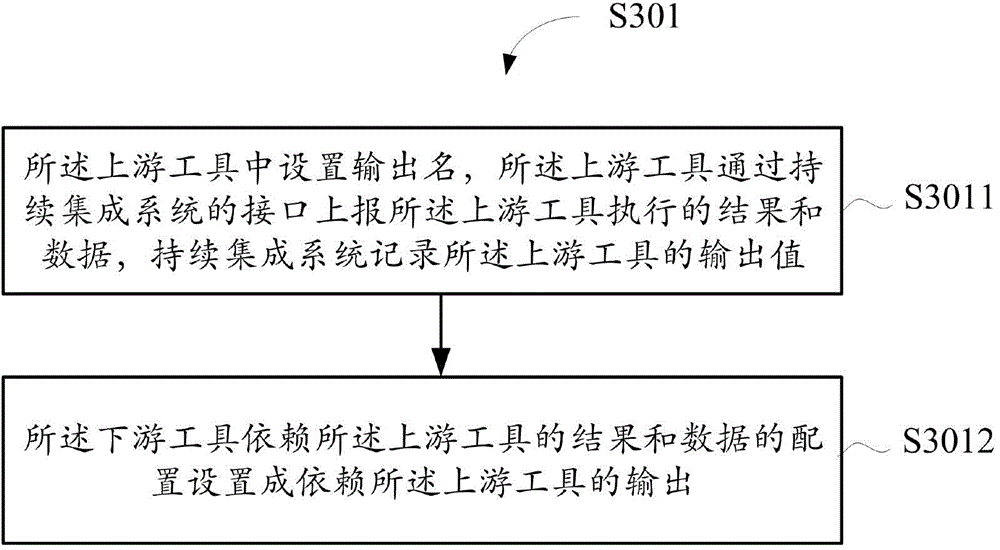
Data processing method and apparatus for continuous integration system
ActiveCN105335284AAvoid mistakesImprove execution timeSoftware testing/debuggingSpecific program execution arrangementsContinuous integrationParallel computing
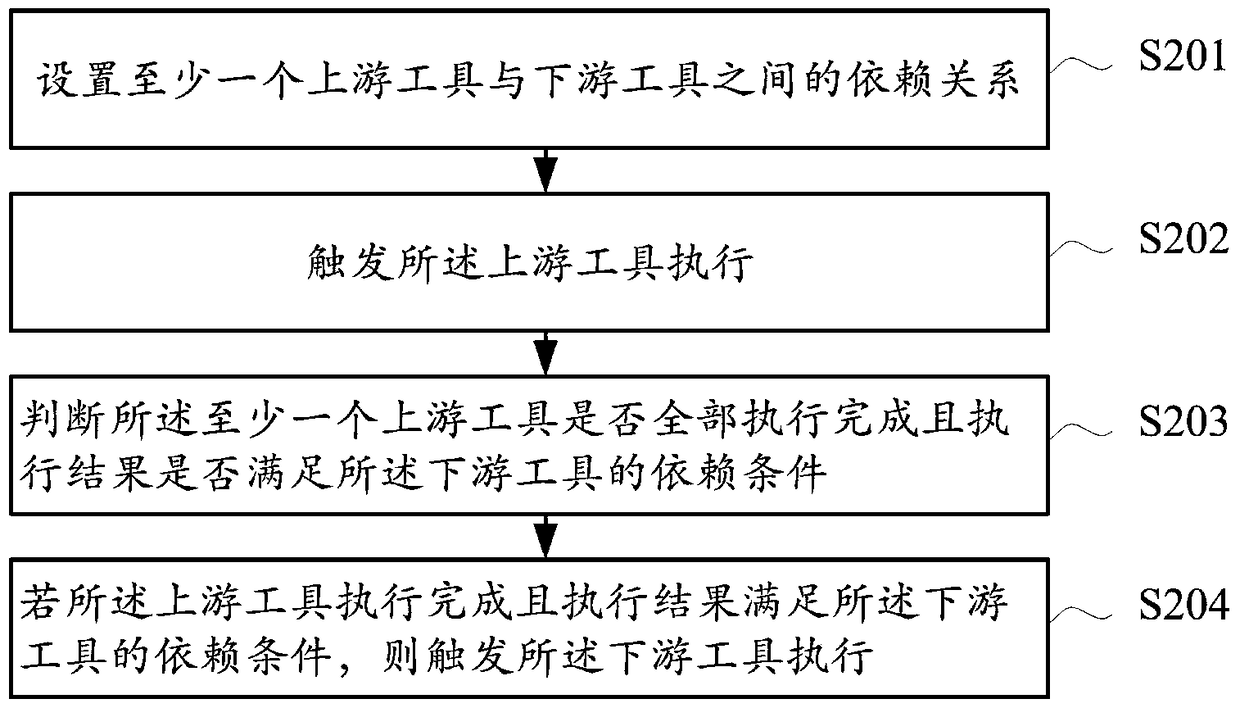
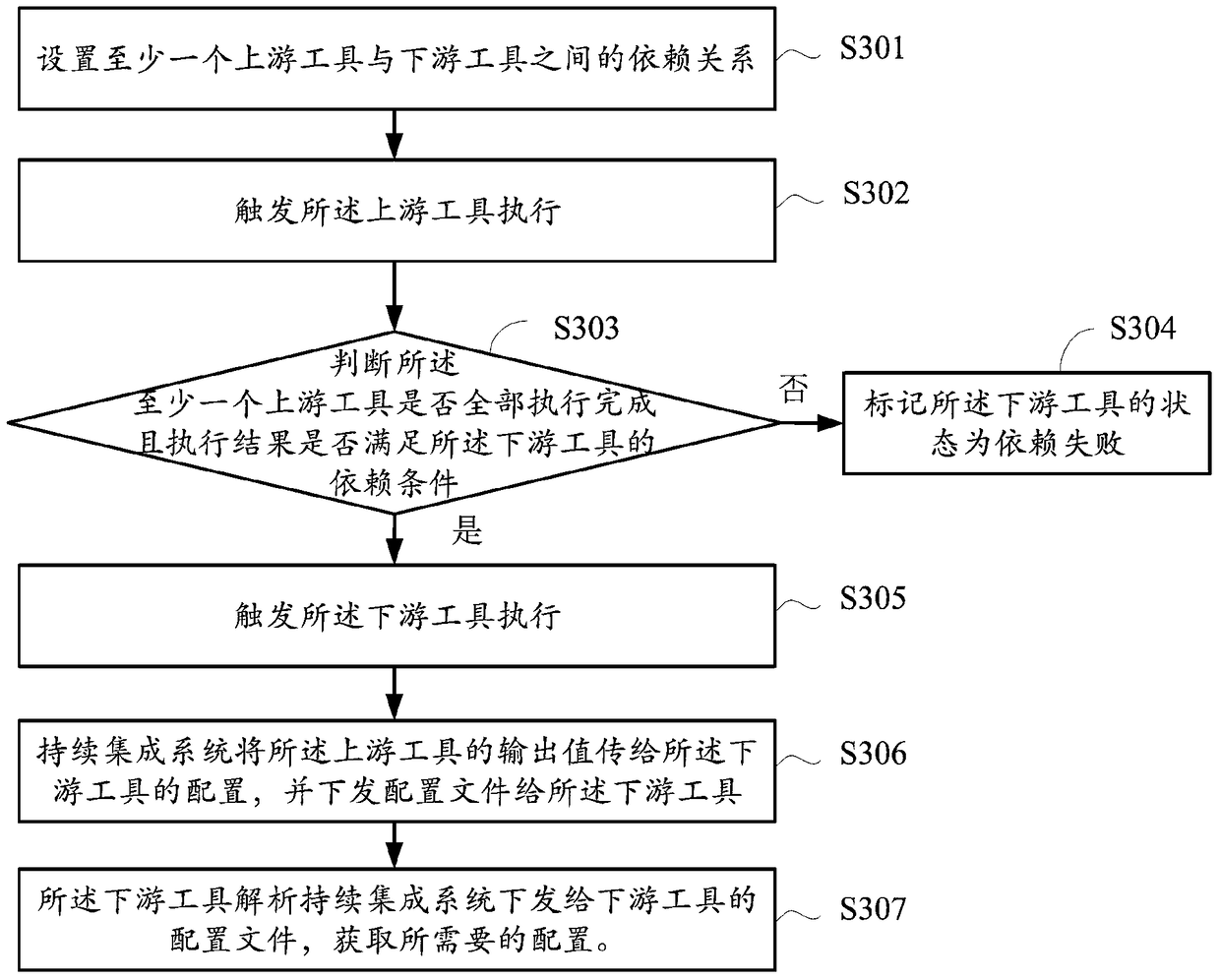
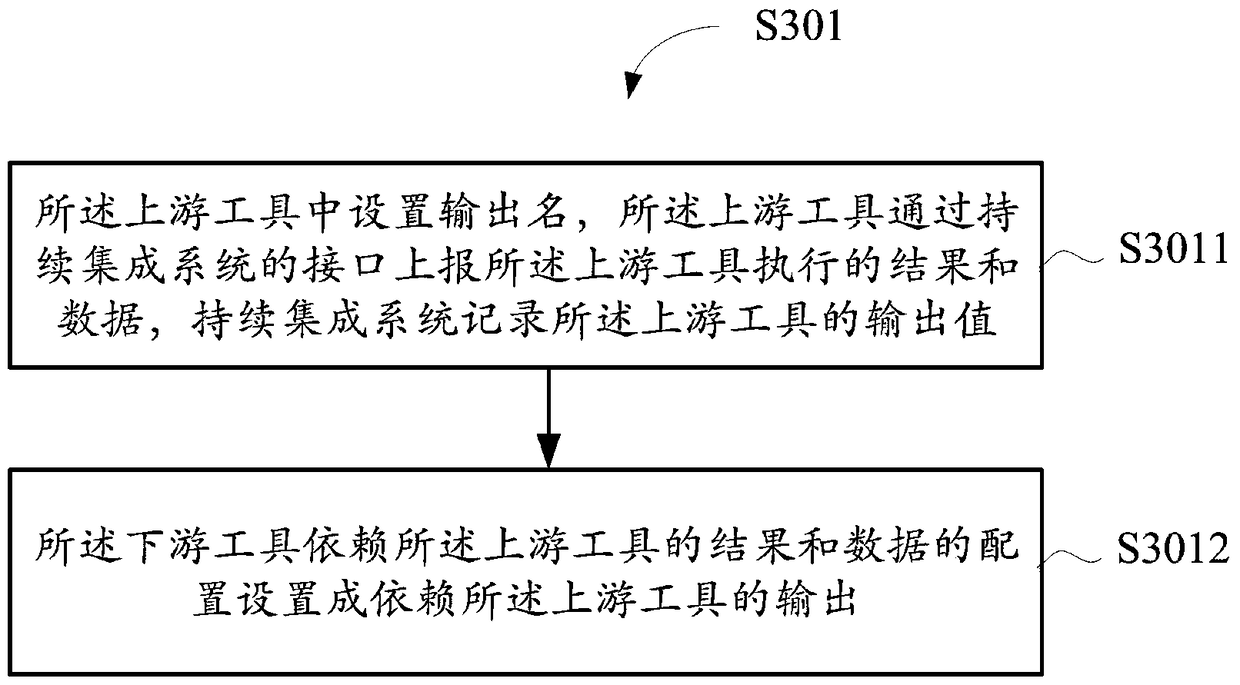
The invention relates to a data processing method and apparatus. The method comprises: setting a dependency relationship between at least one upstream tool and a downstream tool; triggering the execution of the upstream tool; judging whether the at least one upstream tool is fully executed or not and an execution result meets a dependency condition of the downstream tool or not; and if the upstream tools are all executed and the execution result meets the dependency condition of the downstream tool, triggering the execution of the downstream tool. In the prior art, a downstream tool is triggered without judging whether an execution result is successful or failed after an upstream tool is executed. According to the data processing method provided by an embodiment, the dependency condition of the downstream tool on the upstream tool can be set, so that unnecessary triggering of the downstream tool, unnecessary execution or running errors of the tool, prolonging of execution time and resource wastes are avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
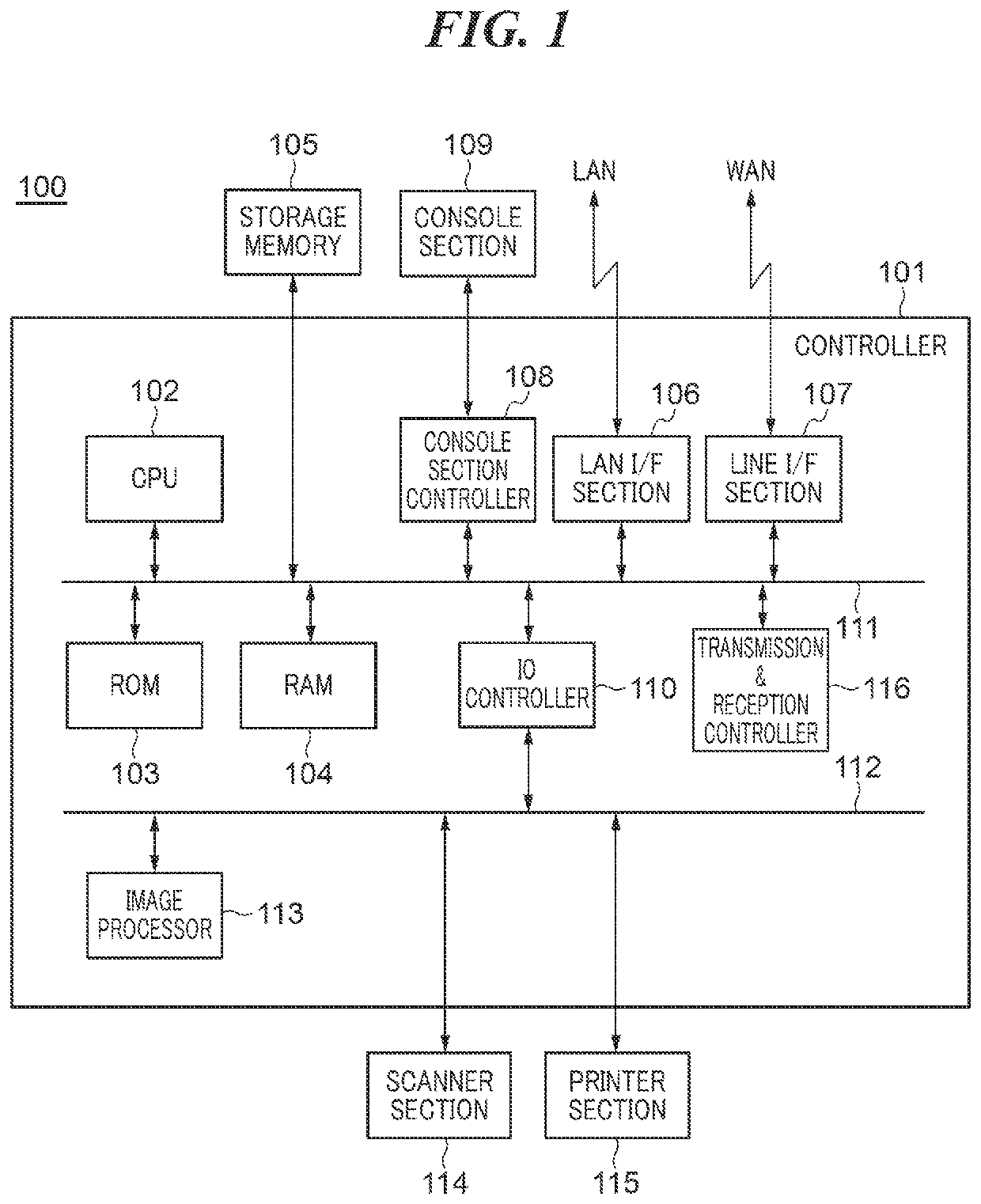
Multifunction peripheral capable of executing image processings in parallel, method of controlling same, and storage medium
ActiveUS20210281687A1Improve execution timePictoral communicationImaging processingComputer graphics (images)
In a multifunction peripheral, image data generated by a scanner section is transferred to an image processor via a data bus. If it is determined that an image processing and another image processing are not executed in parallel, the transfer rate of image data is set to a first transfer rate, whereas if it is determined that the image processing and the other image processing are executed in parallel, one of a plurality of different transfer rates lower than the first transfer rate is selected based on a result of determination of whether or not settings associated with the image processing are predetermined settings and a result of determination of whether or not settings associated with the other image processing are other predetermined settings, and the transfer rate of image data is set to the selected one.
Owner:CANON KK
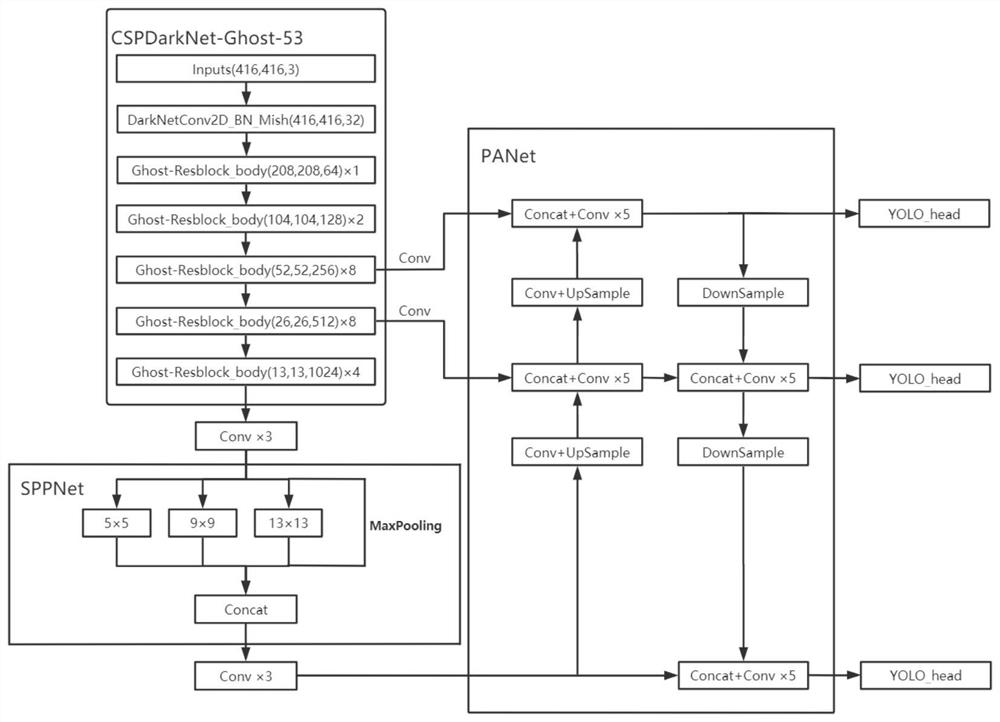
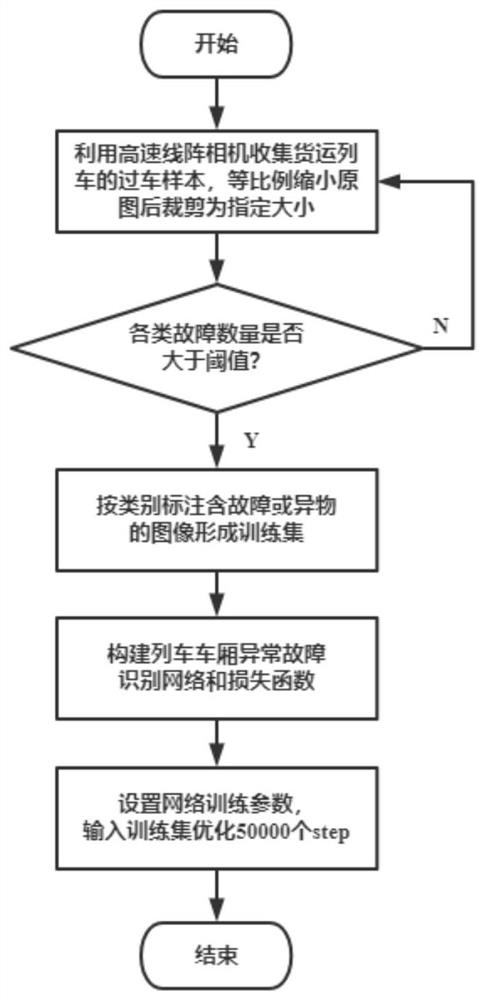
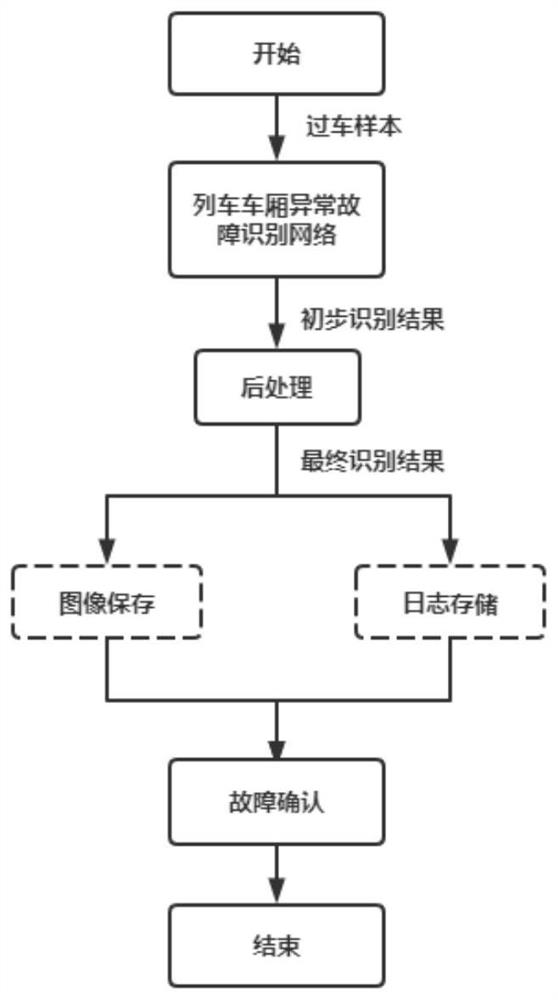
A station freight train carriage abnormity and fault automatic identification method
PendingCN112464846AImprove robustnessPrevent overfittingCharacter and pattern recognitionFreight trainsData set
The invention provides a station freight train carriage abnormity and fault automatic identification method. The method includes, firstly, using a high-speed linear array camera for shooting images ofthe left side, the right side and the top of each carriage to construct a carriage image data set under the condition that a freight train does not stop, and forming a carriage fault image training set after preprocessing operations such as cutting, screening and manual labeling; then constructing a train carriage abnormal fault identification network and a loss function, inputting carriage faultimages in the training set, and optimizing the identification network through a gradient descent algorithm; during testing, inputting a to-be-identified image into the optimized train compartment abnormal fault identification network to obtain a preliminary identification result; and carrying out confidence filtering, non-maximum suppression and other post-processing operations to obtain a finalidentification result. The invention has the advantages of being high in recognition rate, high in speed, high in real-time performance and the like, the functions of monitoring the running state of the train and automatically giving an alarm for abnormalities or faults are achieved, and the intelligent level of railway transportation is further improved.
Owner:WUHAN UNIV OF TECH
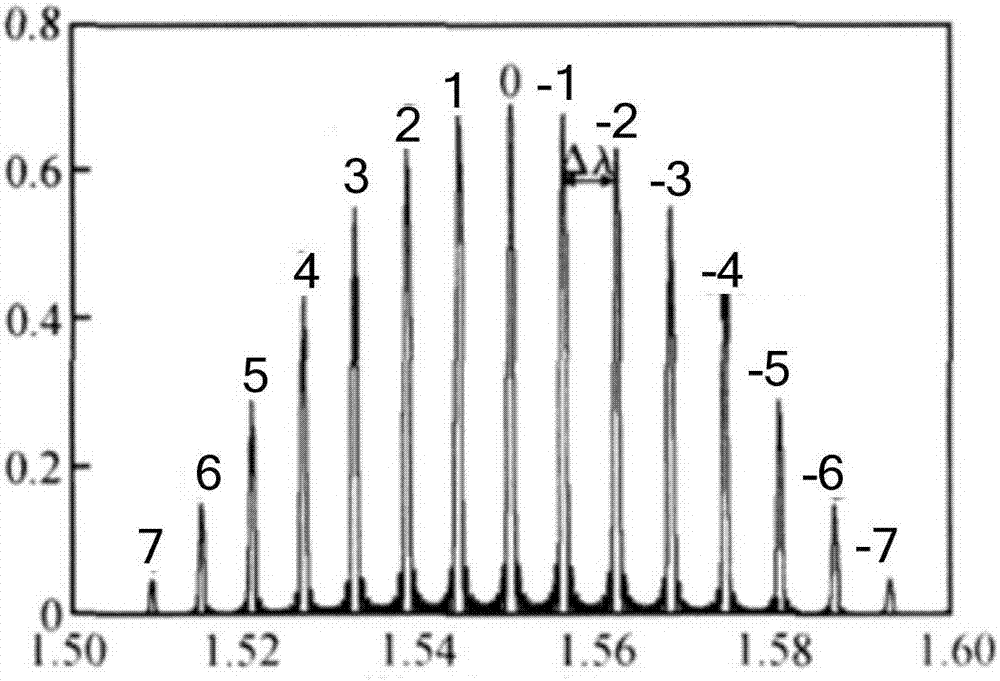
Laser machining method based on EBL and application method thereof
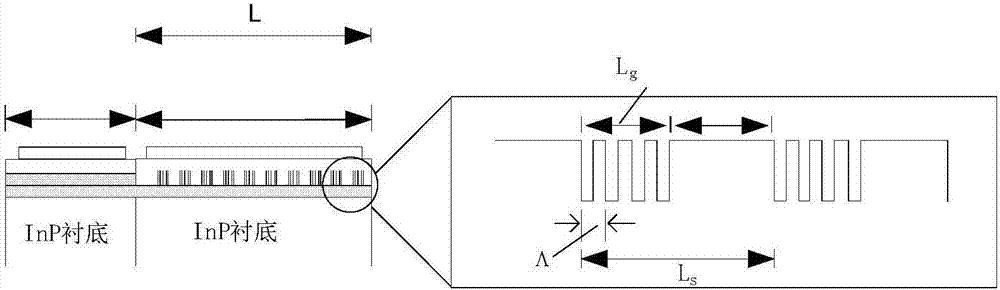
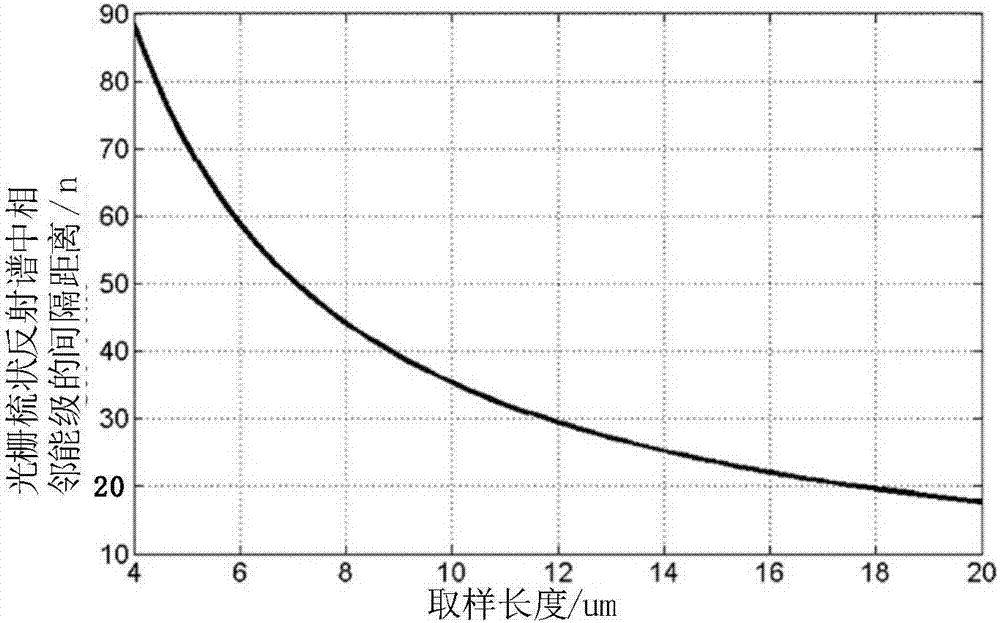
ActiveCN106941241AReduce the amount requiredImprove execution timeLaser optical resonator constructionSemiconductor laser arrangementsGratingLithographic artist
The invention relates to the technical field of lasers, and provides a laser machining method based on EBL and an application method thereof. The machining method includes: determining a related parameter of a first reflection peak corresponding to a grating region structure of a uniform grating laser; obtaining a related parameter interval of the grating region structure which is allowed to be fabricated by the laser; calculating a maximum coupling coefficient capable of being obtained by a uniform grating and a related parameter value of the correspondingly fabricated grating region structure according to the related parameter interval of the grating region structure which is allowed to be fabricated; calculating a minimum grating region length of a sampling grating according to the related parameter of the first reflection peak and the maximum coupling coefficient; and regarding the minimum grating region length of the sampling grating and the related parameter value of the grating region structure as input parameters for fabrication of the grating region of the laser. According to the method, the conventional uniform grating structure is replaced by the sampling grating containing the minimum grating region length, the total amount of lithography can be reduced, the complexity of the machining process is improved, and the production efficiency of laser chips is improved.
Owner:GUANGXUN SCI & TECH WUHAN +1
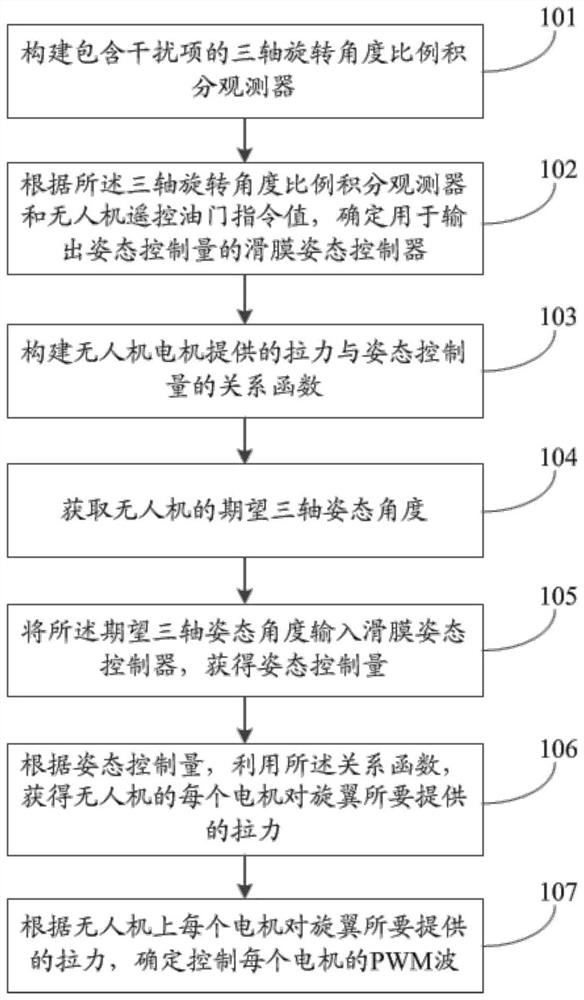
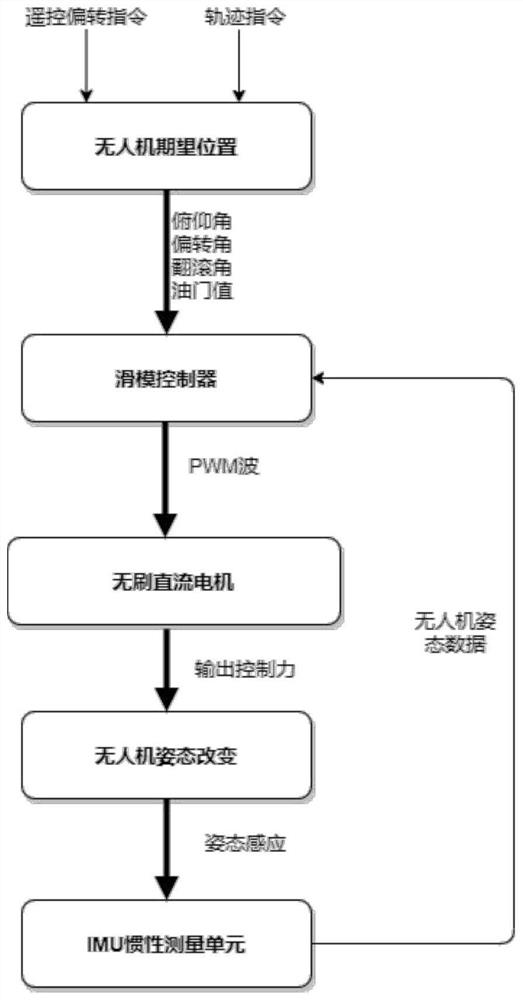
Anti-interference unmanned aerial vehicle control method and system
ActiveCN113485437AImprove anti-interference abilityImprove execution timePosition/course control in three dimensionsInterference resistanceAttitude control
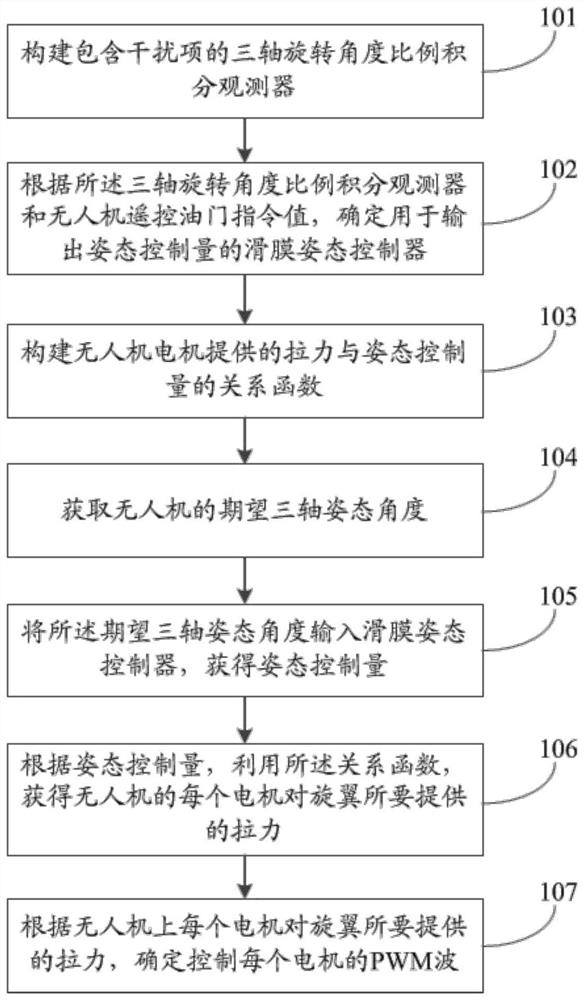
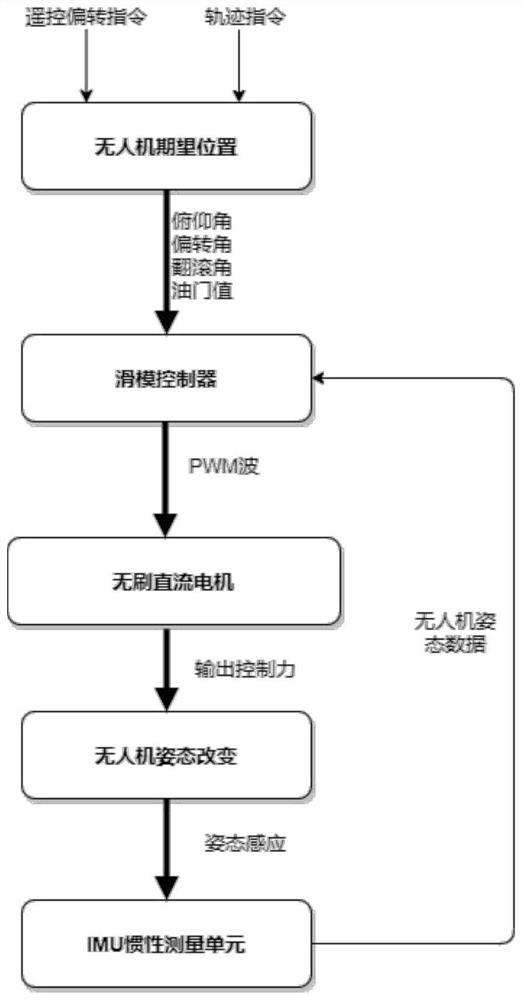
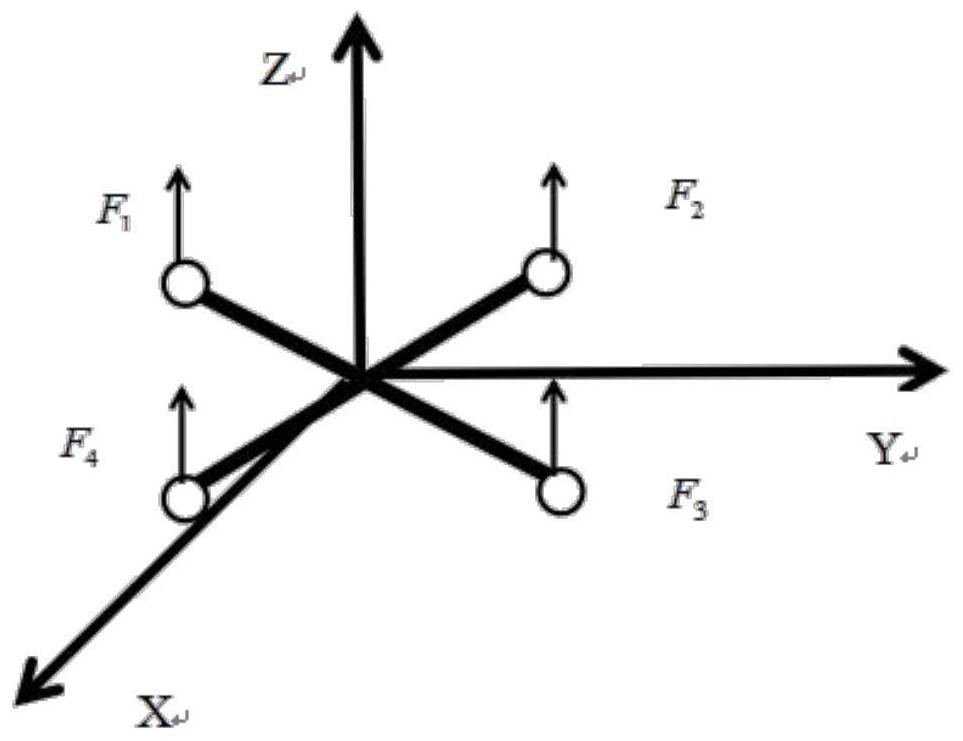
The invention relates to an anti-interference unmanned aerial vehicle control method and system. The method comprises the steps: constructing a three-axis rotation angle proportional-integral observer containing an interference term; according to the three-axis rotation angle proportional-integral observer and the unmanned aerial vehicle remote control accelerator instruction value, determining a sliding mode attitude controller used for outputting attitude control quantity; inputting the expected three-axis attitude angle into the sliding mode attitude controller to obtain an attitude control quantity; according to the attitude control quantity, utilizing a relation function to obtain a pulling force to be provided by each motor of an unmanned aerial vehicle to a rotor wing; and determining PWM waves for controlling each motor according to the pulling force to be provided by each motor of the unmanned aerial vehicle to the rotor wing. According to the invention, the interference term is introduced into the proportional integral observer to increase the anti-interference capability of the unmanned aerial vehicle, and the sliding mode attitude controller can increase the execution time rate of the unmanned aerial vehicle due to the exponential convergence characteristic of the sliding mode attitude controller, so that the stability of the system is improved.
Owner:HEFEI UNIV OF TECH
A data processing method and device for continuous integration system
ActiveCN105335284BAvoid mistakesImprove execution timeSoftware testing/debuggingContinuous integrationParallel computing
The invention relates to a data processing method and apparatus. The method comprises: setting a dependency relationship between at least one upstream tool and a downstream tool; triggering the execution of the upstream tool; judging whether the at least one upstream tool is fully executed or not and an execution result meets a dependency condition of the downstream tool or not; and if the upstream tools are all executed and the execution result meets the dependency condition of the downstream tool, triggering the execution of the downstream tool. In the prior art, a downstream tool is triggered without judging whether an execution result is successful or failed after an upstream tool is executed. According to the data processing method provided by an embodiment, the dependency condition of the downstream tool on the upstream tool can be set, so that unnecessary triggering of the downstream tool, unnecessary execution or running errors of the tool, prolonging of execution time and resource wastes are avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Image forming apparatus
ActiveCN103941560AReduce consumptionReduce power consumptionElectrographic process apparatusImage formationEngineering
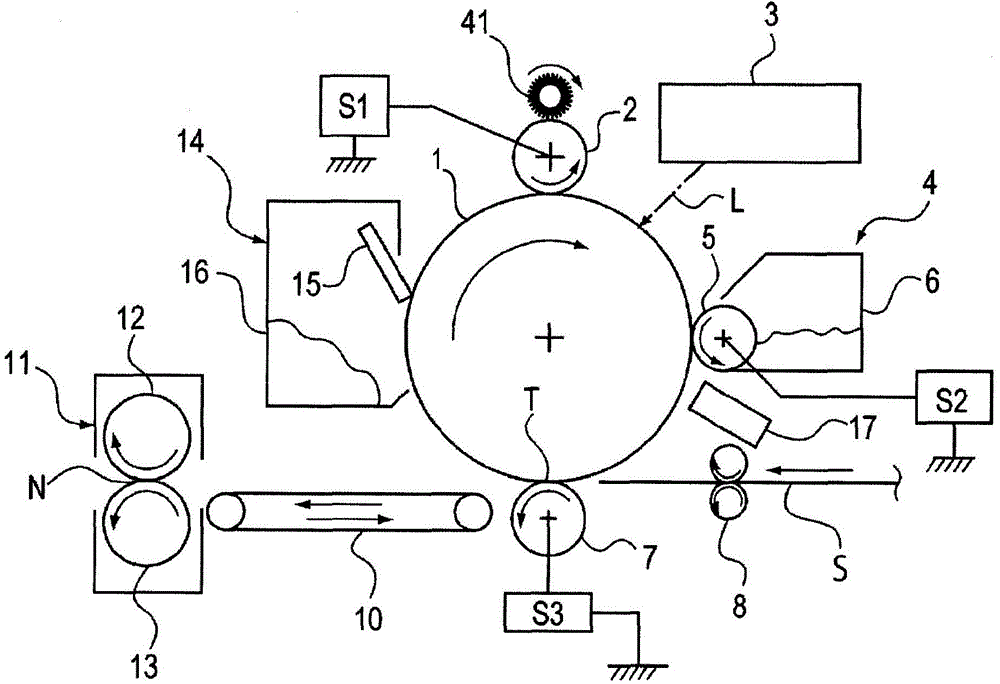
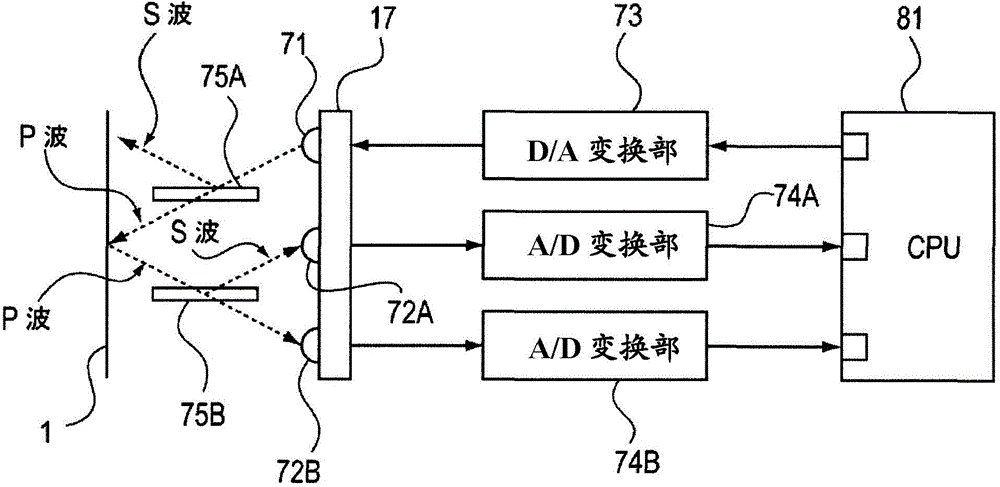
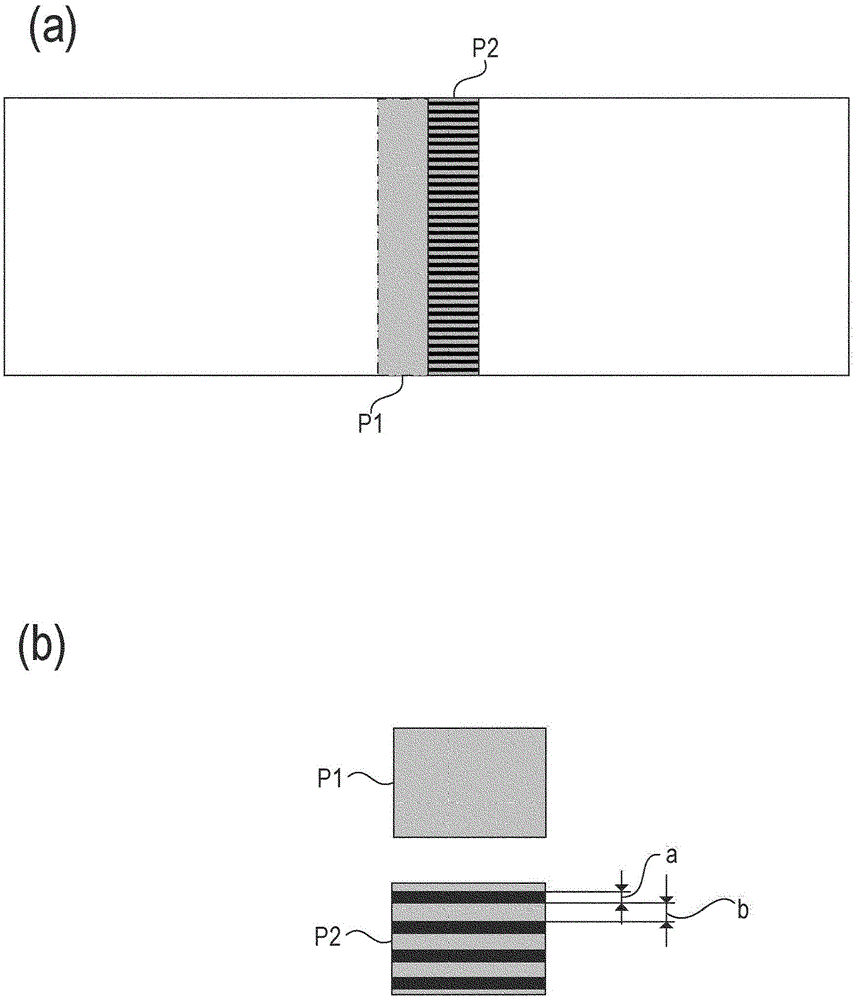
The present invention aims to precisely detect an image flow generation level and reliably recover image flow. An image forming apparatus is provided with an image forming part forming a color toner image on a photoreceptor drum; an intensity sensor detecting the intensity of the color toner image of the photoreceptor drum; and a control part for determining the surface state of the photoreceptor drum according to the detecting result of the intensity sensor, wherein the image forming part forms a first pattern image and a second pattern image different from the first pattern image on the surface of the photoreceptor drum, and the control unit determines the intensity of the first pattern image and the second pattern image formed on the surface of the photoreceptor drum and determines the surface state of the photoreceptor drum according to the detecting results of the intensity sensor.
Owner:COPYER
A method and system for performing changes to software
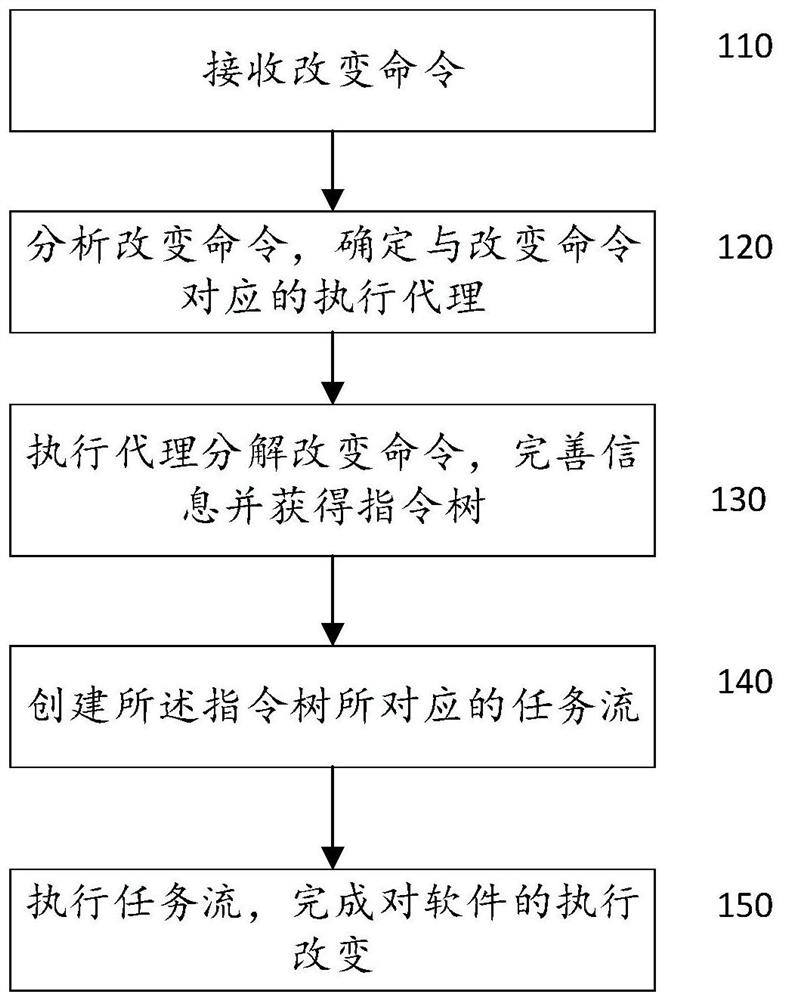
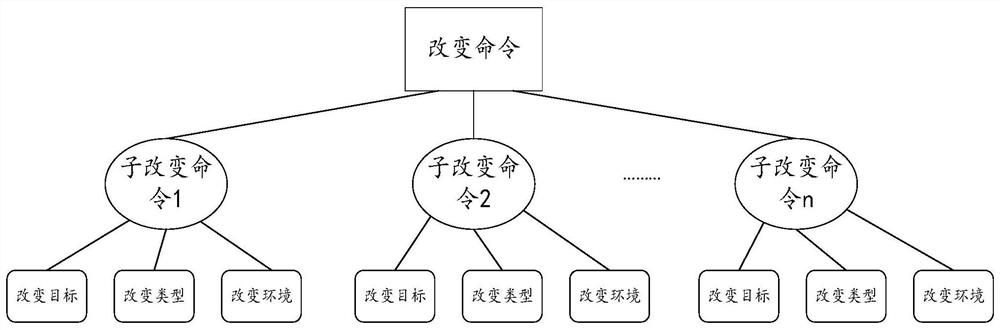
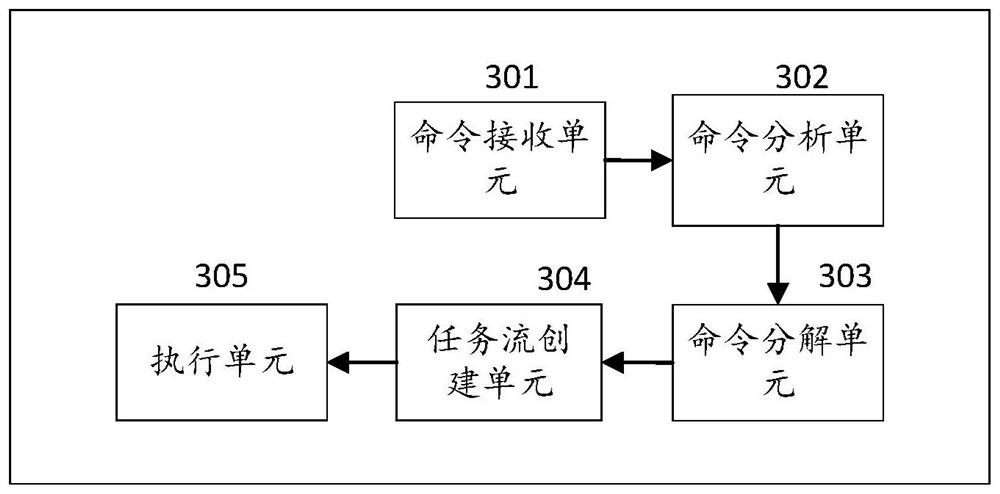
ActiveCN109375947BImprove execution timeImprove securityVersion controlSoftware engineeringEngineering
The present application discloses a method and system for implementing changes in software. The method for implementing changes in software specifically includes the following steps: receiving a change command; analyzing the change command to determine an execution agent corresponding to the change command; executing the agent to decompose the change command, Complete the information and obtain the instruction tree; create the task flow corresponding to the instruction tree; execute the task flow to complete the execution change of the software. The method and system for performing changes to software provided by the present application can automatically and quickly execute change commands without manual changes, and improve the execution time and safety of change commands.
Owner:杭州炎魂网络科技有限公司
Process mining technology oriented to composite services
InactiveCN104636391AImprove execution timeImprove execution efficiencySpecial data processing applicationsComposite servicesBusiness Personnel
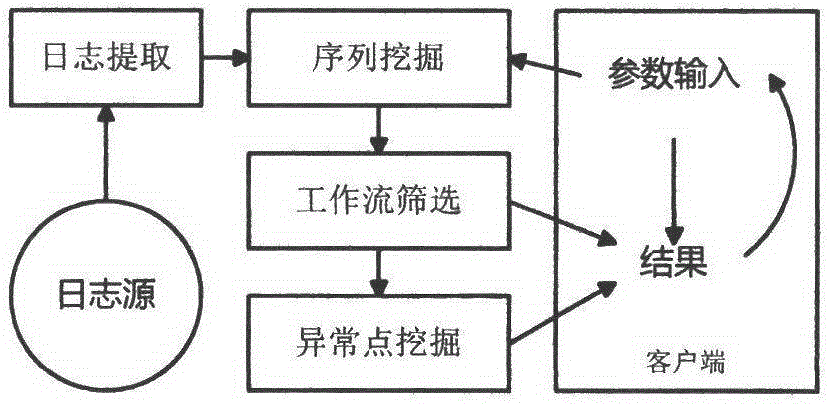
Business personnel are helped to find frequent processes in a business log by means of a sequence mining method, and a process may be further improved in the aspects of execution time and efficiency by improving frequent execution actions; besides, according to abnormal actions occurring at low frequency, an abnormal point mining method is designed to help the business personnel to find the processes. A log mining system framework graph is shown in the figure.
Owner:SHANGHAI XINYOU NETWORK TECH
A control method and system for an anti-jamming unmanned aerial vehicle
ActiveCN113485437BImprove anti-interference abilityImprove execution timePosition/course control in three dimensionsInterference resistanceAttitude control
The invention relates to an anti-interference UAV control method and system, constructing a three-axis rotation angle proportional-integral observer including interference items; The synovial membrane attitude controller that outputs the attitude control amount; input the desired three-axis attitude angle into the synovial membrane attitude controller to obtain the attitude control amount; according to the attitude control amount, use the relationship function to obtain the required value of each motor for the rotor of the UAV. The pulling force; according to the pulling force provided by each motor on the drone to the rotor, determine the PWM wave to control each motor. The present invention introduces interference items into the proportional integral observer to increase the anti-interference ability of the UAV, and the sliding film attitude controller can increase the speed of the execution time of the UAV due to its exponential convergence characteristics, thereby increasing the stability of the system.
Owner:HEFEI UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com