Secure cloud data deduplication method and system based on trusted hardware
A cloud data, trusted technology, applied in file systems, digital data authentication, digital data protection, etc., can solve problems such as damage to outsourced data, original data and privacy information leakage, data integrity damage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
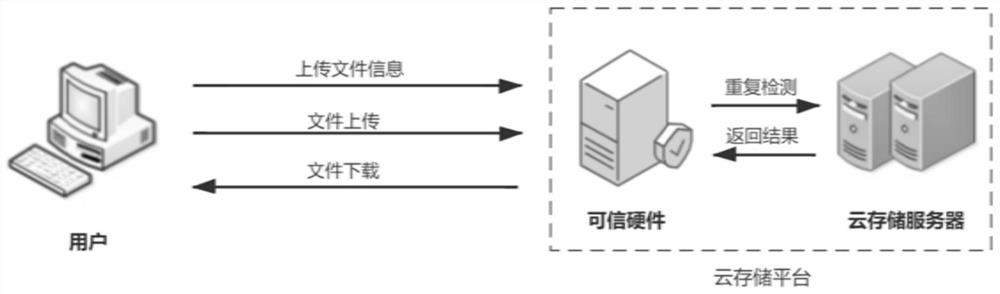
[0071] This solution only describes the file-level + block-level data deduplication process.
[0072] 1) System initialization phase
[0073] According to the SysSetup function proposed in Part 3, the cloud storage platform runs this function according to the input security parameter λ to generate the public parameter Pub:
[0074] 2) Data initialization stage
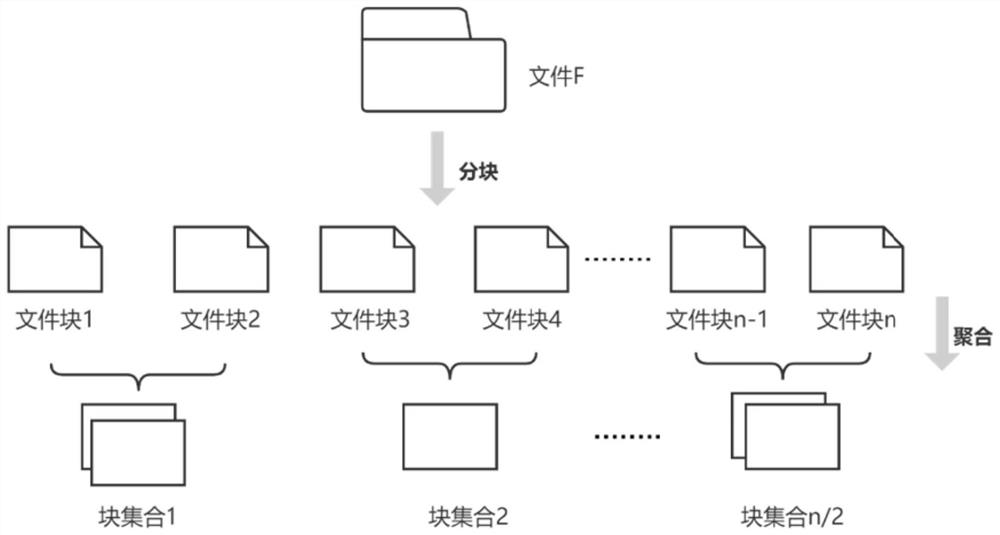
[0075] Client runs the KeyGen function proposed in Part 3 to generate the user's key pair (sk c ,pk c ). Then the Client runs the data encryption algorithm proposed in Part 3. If the file does not need to be divided into blocks according to the system parameters, the file ciphertext C is obtained, and if it needs to be divided into blocks, the ciphertext C={C 1 ,C 2 …C d ,i∈[0,d]}. Then the Client runs the tag generation algorithm proposed in Part 3 to get the tag set
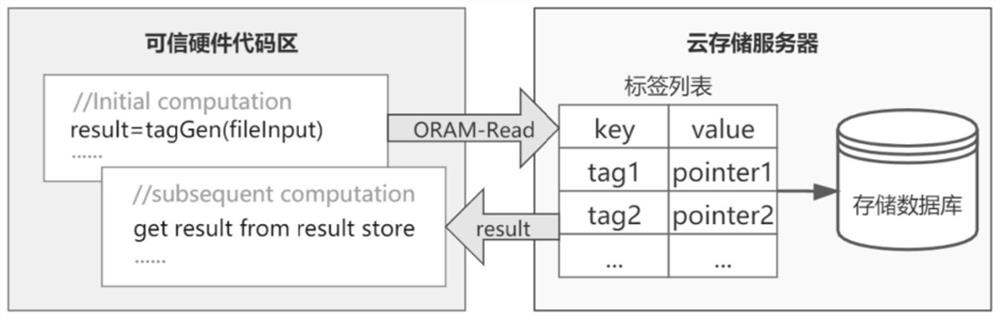
[0076] 3) Data deduplication stage
[0077] CEnclave and Client run the duplicate detection algorithm proposed in Part 3. If there is the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com