Correct link judgment method and device for service chain security deployment under mimicry defense, equipment and medium
A service chain and the correct technology are applied in the field of service deployment and mimic security defense to achieve the effect of increasing workload and protecting purity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
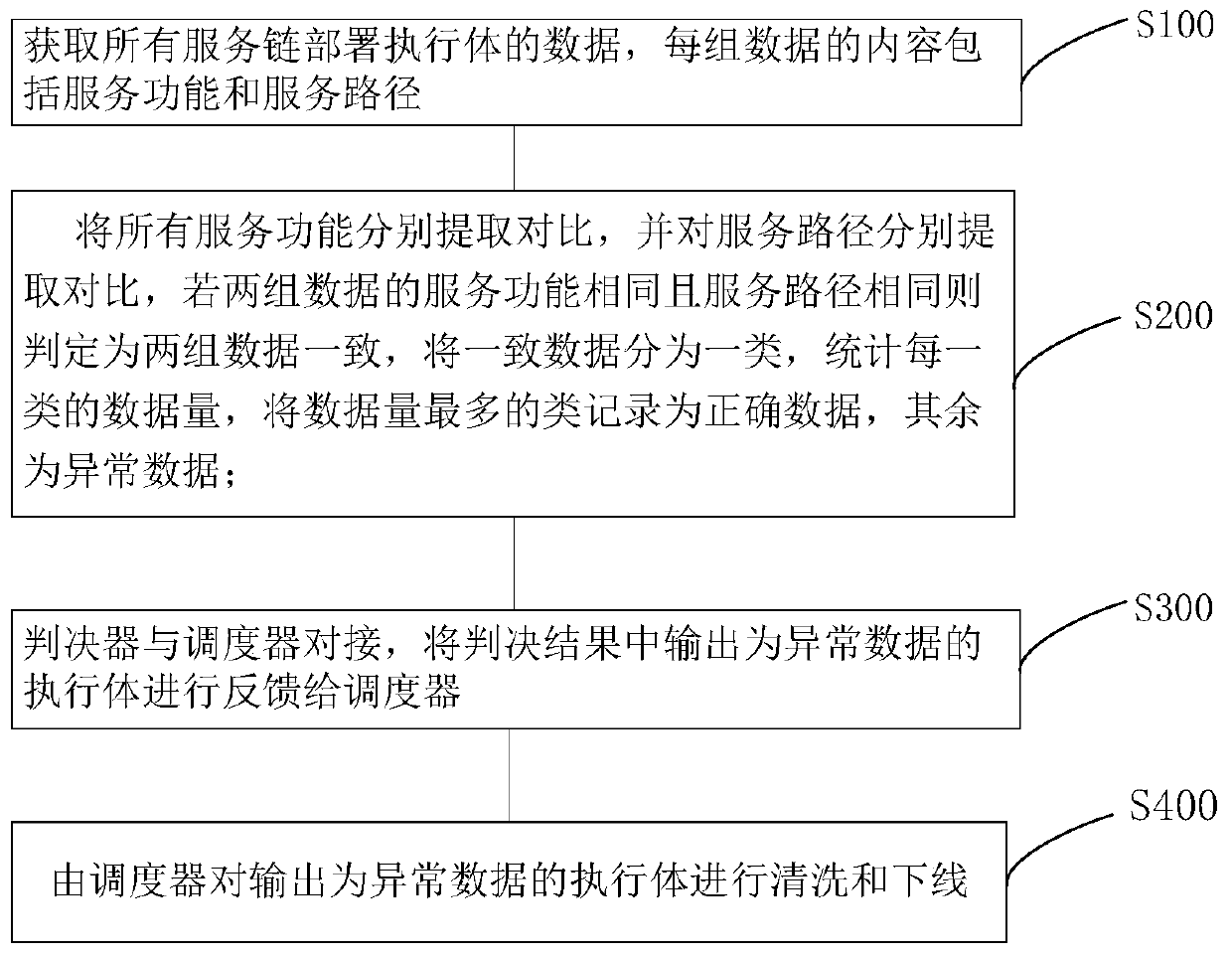
[0051] figure 1 It is a flow chart of a method for judging the correct link for secure deployment of service chains under mimic defense provided in Embodiment 1 of the present application, which is applied to the server side, and the method includes:
[0052] Step S100, the decider is acquiring the data of all service chain deployment executors, and the content of each set of data includes service functions and service paths;
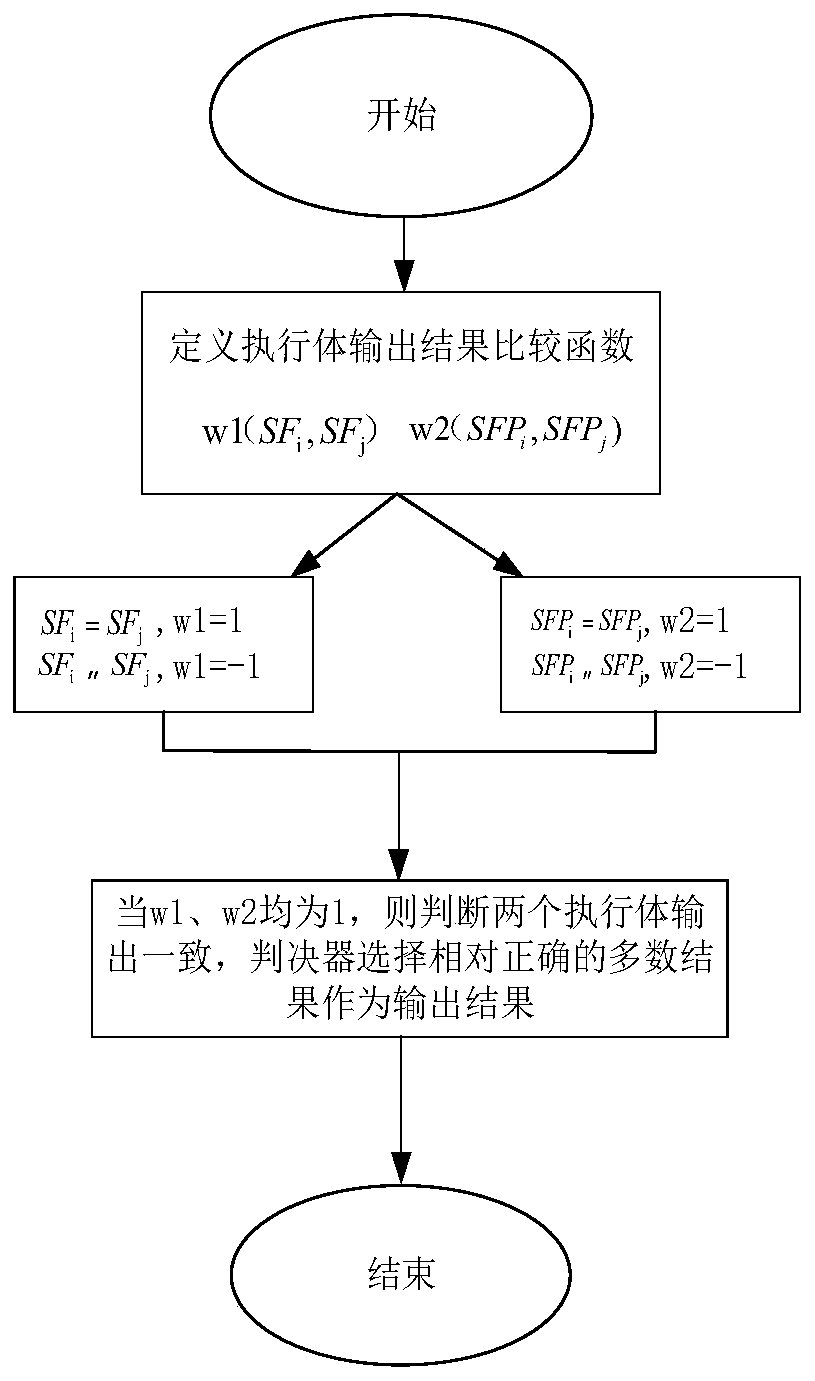
[0053] Specifically, use the set V to represent the output results of M execution bodies in all service chain deployment execution bodies:
[0054] V=(V 1 , V 2 ,...,V i ,...,V M )
[0055] The output of each executive body is described by a four-tuple, namely:
[0056] V i =(I i ,E i , SF i , SFP i )
[0057] V=(V 1 , V 2 ,...,V i ,...,V M )V i =(I i ,E i , SF i , SFP i ) among them, I i ,E i Respectively represent the source address and destination address of the service chain request business traffic in the output result of the...
Embodiment 2
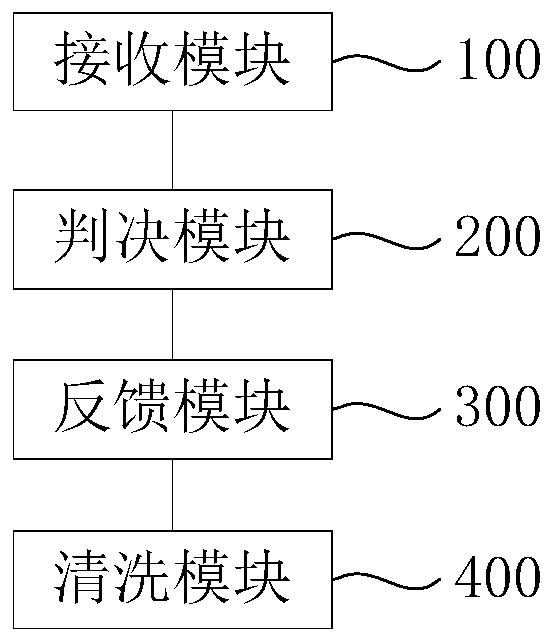
[0090] image 3 It is a schematic structural diagram of a device for judging the correct link for secure deployment of service chains under mimic defense provided in the second embodiment of this application. The correct link judging method has corresponding functional modules and beneficial effects for executing the method. Such as image 3 As shown, the device includes:
[0091] The receiving module 100 is used to obtain the data of all service chain deployment executives, and the content of each set of data includes service functions and service paths;
[0092] The judgment module 200 is used to extract and compare all service functions and service paths respectively. If the service functions and service paths of the two sets of data are the same, it is determined that the two sets of data are consistent, and the consistent data is classified into one category. Count the amount of data for each category, record the category with the largest amount of data as correct data...
Embodiment 3
[0096] Figure 4 It is a schematic structural diagram of a device provided by Embodiment 3 of the present invention. Figure 4 A block diagram of an exemplary device 1 suitable for implementing embodiments of the invention is shown. Figure 4 The displayed device is only an example, and should not limit the functions and scope of use of the embodiments of the present application.
[0097] Such as Figure 4 As shown, device 1 takes the form of a general-purpose computing device. The components of the device 1 may include, but are not limited to: one or more processors or processing units 2, a memory 3, and a bus 4 connecting different system components (including the memory 3 and the processing unit 2).
[0098] Bus 4 represents one or more of several types of bus structures, including a memory bus or memory controller, a peripheral bus, an accelerated graphics port, a processor, or a local bus using any of a variety of bus structures. These architectures include, by way of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com