Data acquisition method in grade protection
A technology for data collection and data protection, applied in the field of information security, can solve the problems of time-consuming, labor-intensive, manpower and material resources, and achieve the effect of optimizing the detection path, reducing the workload, and improving the efficiency of data collection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
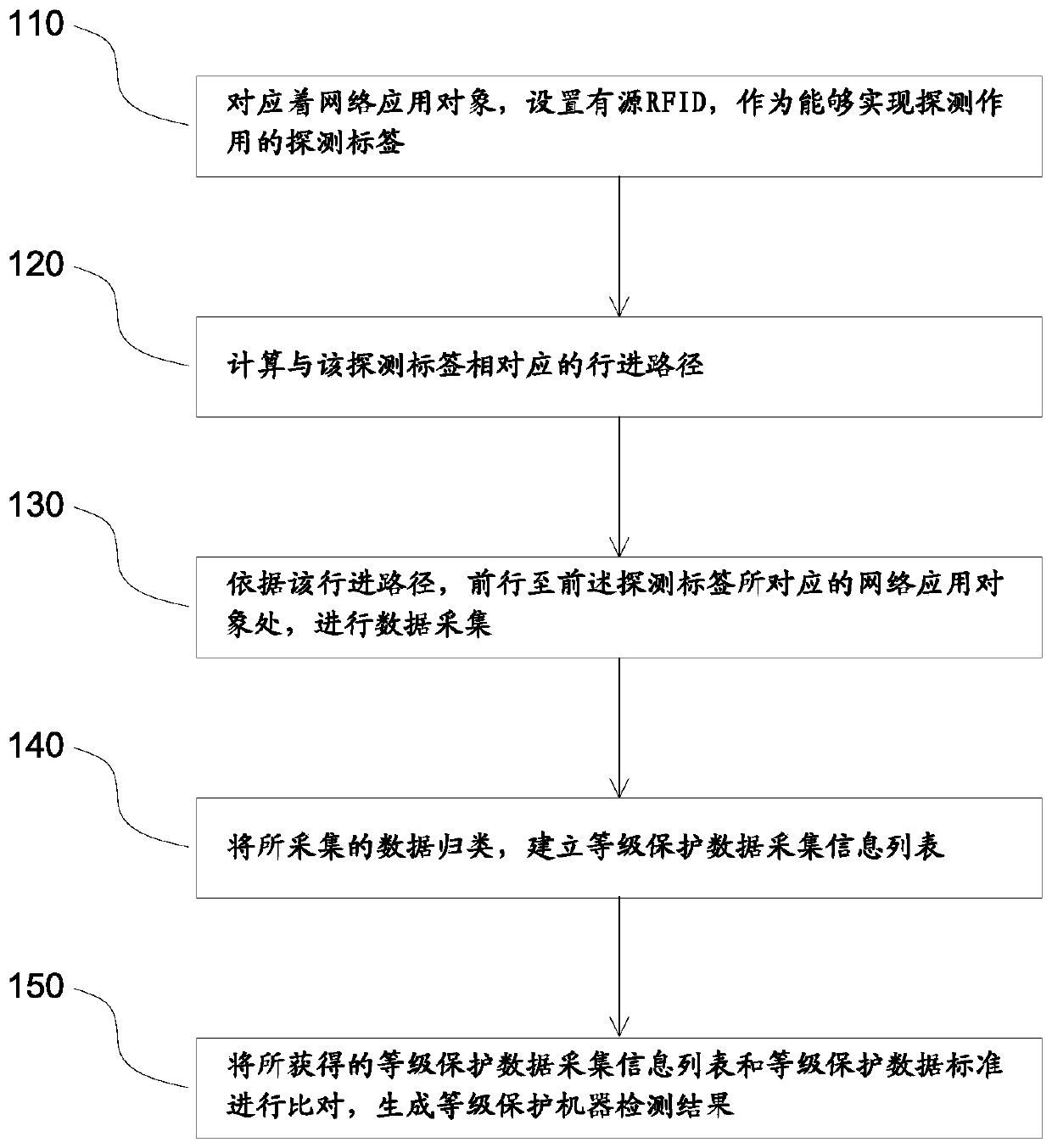
[0025] ginseng figure 1 As shown, an embodiment of the present invention is shown here, which specifically includes the following steps:
[0026] Step 110, corresponding to the network application object, setting an active RFID as a detection tag capable of realizing the detection function.
[0027] The detection tag needs a wireless data transmission source capable of emitting detectable electromagnetic signals, and the specifics are not limited, but it should be as low-cost and portable as possible. In actual operation, RFID is an excellent alternative.
[0028] Passive RFID can be deployed in a cost-effective manner. However, the effective detection distance corresponding to passive RFID is very short. Therefore, a more preferable solution is to use active RFID, through which the detection path can be extended in a large range.
[0029] The network application objects mentioned above refer to all the terminal devices capable of connecting to the network used by the unit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com