Dynamic verification code generation method
A dynamic verification code, currently generated technology, applied in the field of security verification, can solve problems such as easy to be cracked, unsatisfied security requirements, user end user authentication information leakage, etc., to avoid information security problems, suitable for promotion and use, to avoid easy cracked effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
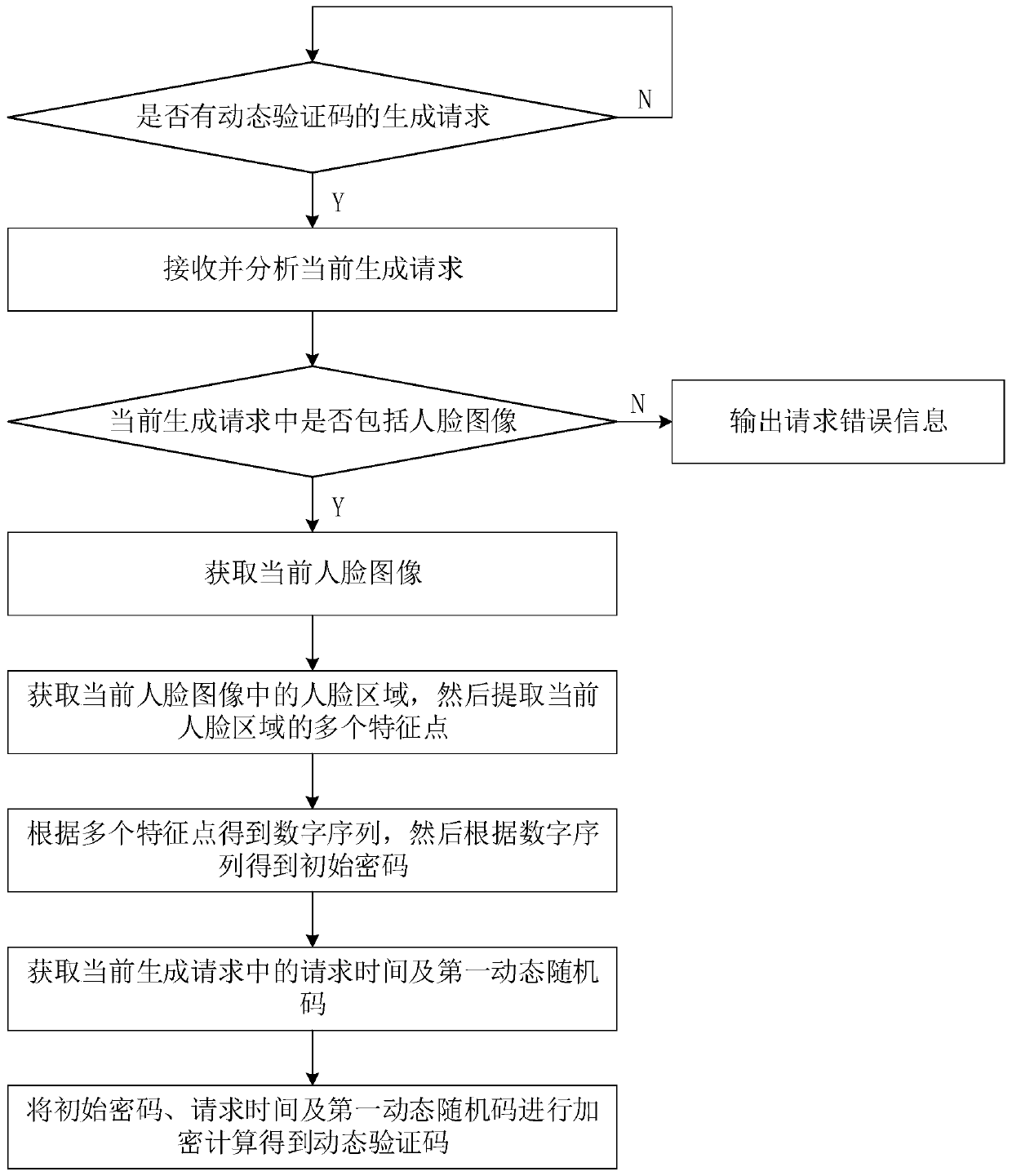
[0046] Such as figure 1 As shown, this embodiment provides a method for generating a dynamic verification code, including the following steps:
[0047] Detect in real time whether there is a request to generate a dynamic verification code, and if so, receive and analyze the current generation request;
[0048] Determine whether the current generation request includes a face image, if yes, obtain the current face image, if not, output a request error message;
[0049] Obtain the face area in the current face image, and then extract multiple feature points of the current face area;
[0050] Get the number sequence based on multiple feature points, and then get the initial password according to the number sequence;
[0051] The request time and the first dynamic random code in the current generated request are obtained, and then the initial password, the request time and the first dynamic random code are encrypted and calculated to obtain the dynamic verification code.
Embodiment 2
[0053] The technical solution provided in this embodiment is a further improvement made on the basis of the technical solution in embodiment 1. The difference between this embodiment and embodiment 1 is:
[0054] In this embodiment, after obtaining the dynamic verification code, the following steps are further included:
[0055] Generate a base layer based on the current dynamic verification code;
[0056] Obtain a second dynamic random code, and generate multiple interference layers according to the second dynamic random code;
[0057] Merge each interference layer separately with the base layer to form multiple composite frames;
[0058] The preset frame rate is obtained, so that multiple composite frames are dynamically displayed at the preset frame rate, and the final dynamic verification code is obtained; wherein, the preset frame rate can meet the requirement of visual persistence, and is convenient for human eyes to recognize the dynamic verification code.
[0059]As ...
Embodiment 3
[0062] The technical solution provided in this embodiment is a further improvement made on the basis of the technical solution in embodiment 2. The difference between this embodiment and embodiment 2 is:
[0063] In this embodiment, when generating the base layer, the specific steps are as follows:
[0064] Obtain the current dynamic verification code and basic background image;
[0065] Separate the multiple verification characters of the current dynamic verification code, and then combine the separated multiple verification characters with the basic background image to form a basic layer.
[0066] After the final dynamic verification code is generated, visually, the verification characters are still and clearly identifiable, and the random characters in the interference layer are constantly flashing. The random characters in the interference layer can interfere with the computer cracking program and increase the security of the dynamic verification code. At the same time, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com