Method for protecting privacy in federated learning prediction stage based on PSI technology
A federal, phased technology, applied in the field of information security, can solve problems such as no research
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
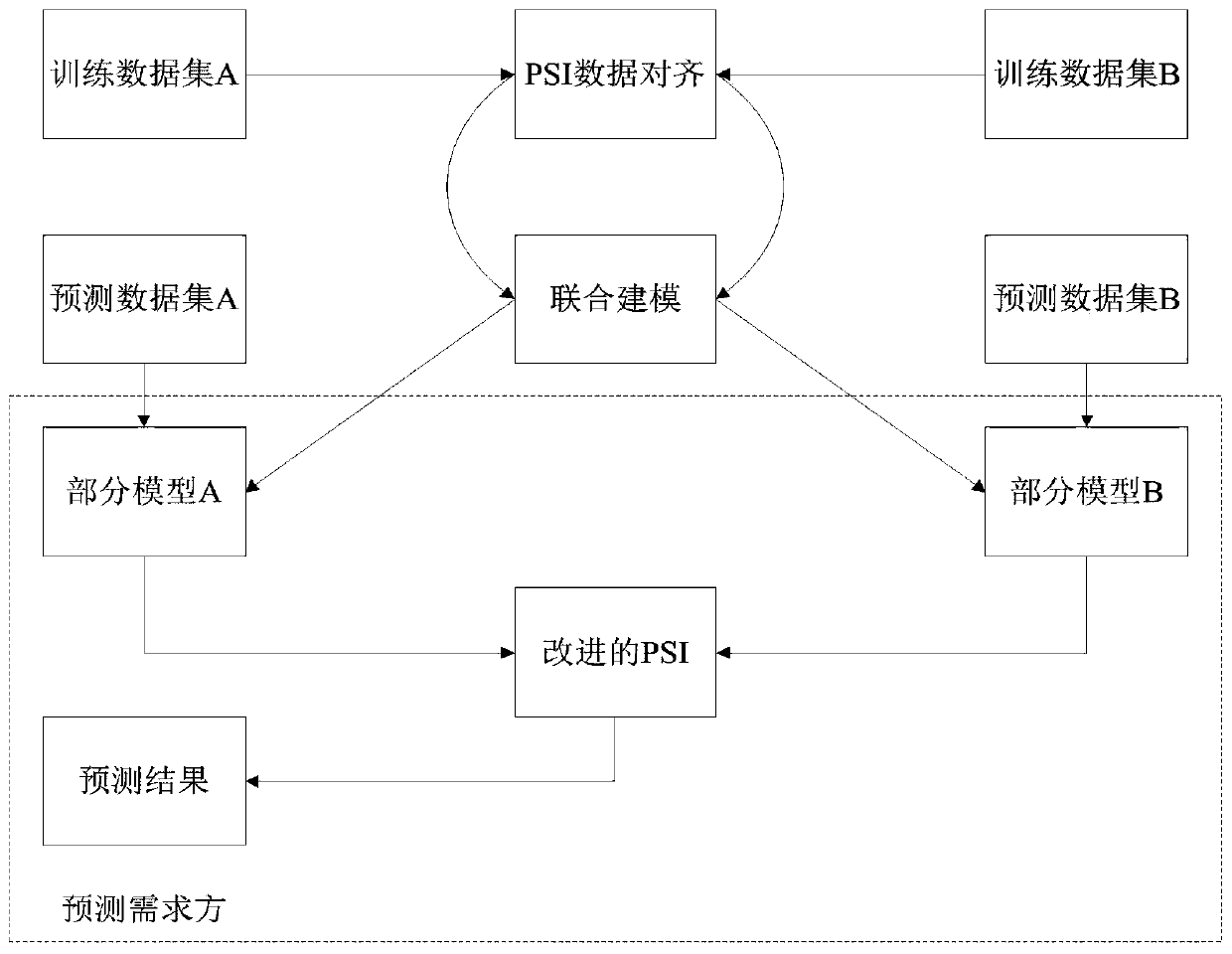
[0032] Let the machine learning algorithm used in the present invention be logistic regression, the data feature of Alice is Bob's data features are where d A and d B are the number of features owned by Alice and Bob respectively. The partial models obtained by Alice and Bob through federated learning are respectively with where θ -1 is the intercept. The prediction function of logistic regression is in For specific sample data, the first half Owned by Alice, second half owned by Bob. Then Alice performs the prediction according to the following steps:
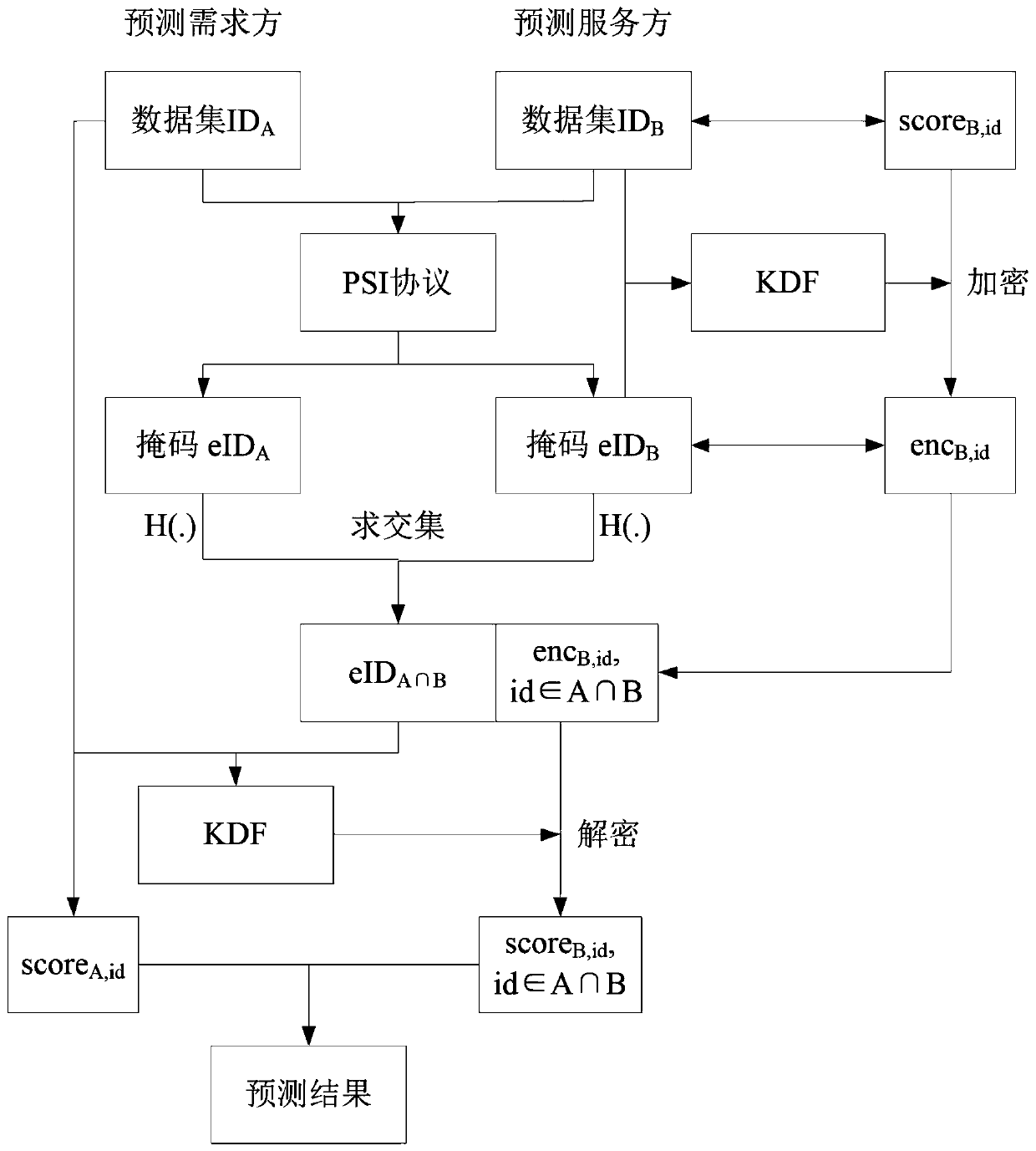
[0033] 1. For all id∈ID B , Bob calculates Form a new data set and record it as Predict B ={(id,score B,id )|id∈ID B};
[0034] 2. Alice and Bob execute the improved OT protocol-based PSI to obtain new data set eID respectively A ={eid A,id |id∈ID A} and eP B ={(eid B,id ,score B,id )|id∈ID B};
[0035] 3. For each (eid B,id ,score B,id )∈eP B , Bob uses the key derivation function KDF to g...
Embodiment 2
[0043] Same as the symbol used in Embodiment 1, the prediction is also made using logistic regression, the only difference is that the PSI based on the public key is used in this embodiment. For this reason, some other symbols need to be agreed upon. Assume that this implementation case is based on elliptic curves, and q is the order of elliptic curves. Represents the set {1,2,...,q-1}, H 1 and H 2 is a hash function, where H 1 Messages can be mapped to points on an elliptic curve. Specific steps are as follows:
[0044] 1. Precomputation, for all id∈ID B , Bob randomly chooses calculate s id =H 2 (a*H 1 (id)), and all s id ,id∈ID B send to Alice;
[0045] 2. For all id ∈ ID A , Alice randomly chooses calculate t id =b*H 1 (id), and t id ,id∈ID A send to Bob;
[0046] 3. Bob performs the following steps:
[0047] 3.1. For all id∈ID B , according to Alice's needs, Bob calculates
[0048] 3.2. For all id∈ID B , using the key derivation function to comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com