Security detection method based on Ethernet IP industrial control protocol
A security detection and industrial control protocol technology, applied in electrical components, transmission systems, etc., can solve the problems of running system damage, lack of decoding and understanding, and inability to distinguish, avoiding spatial sparsity, in-depth processing, and saving memory usage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
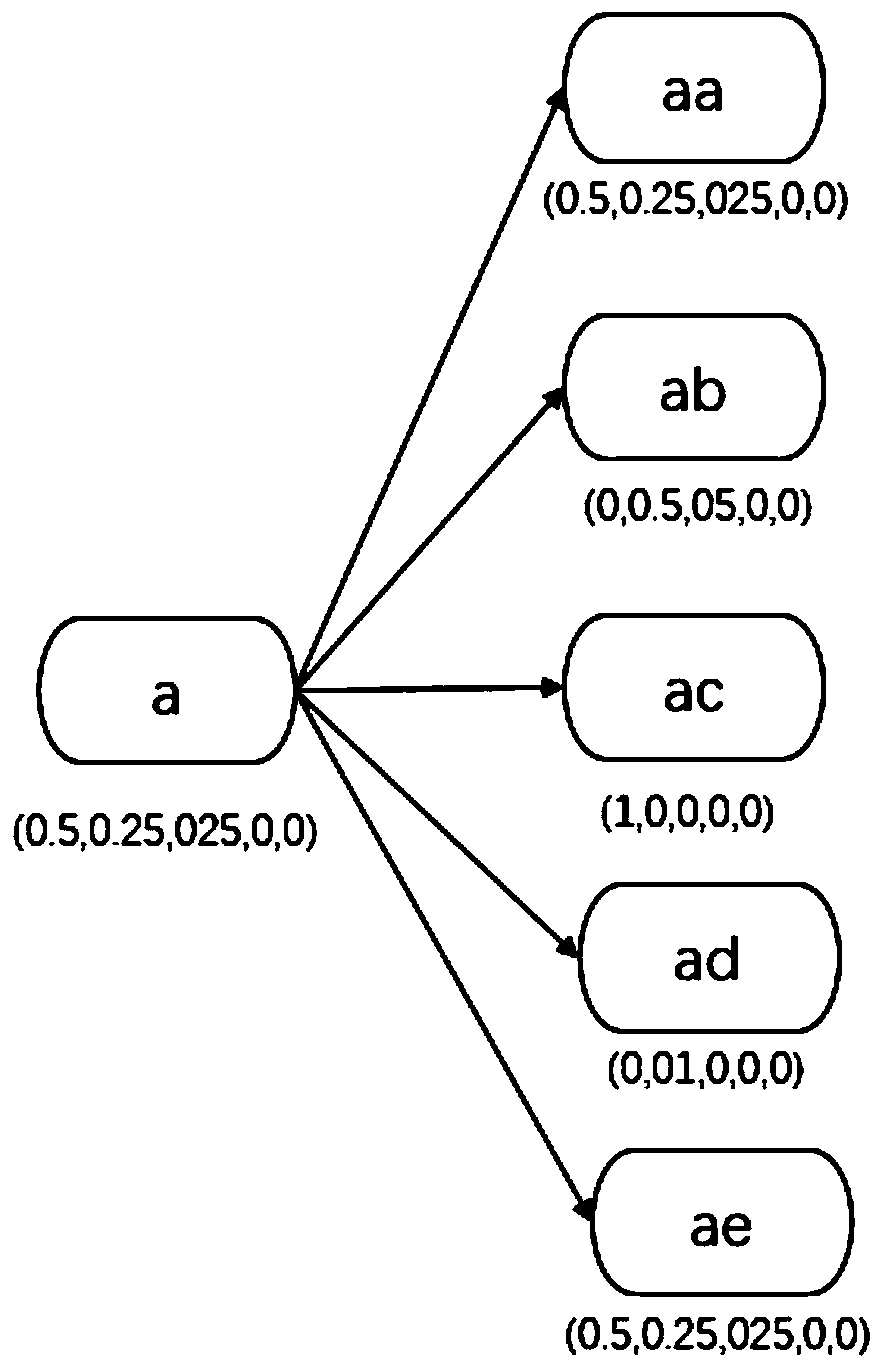
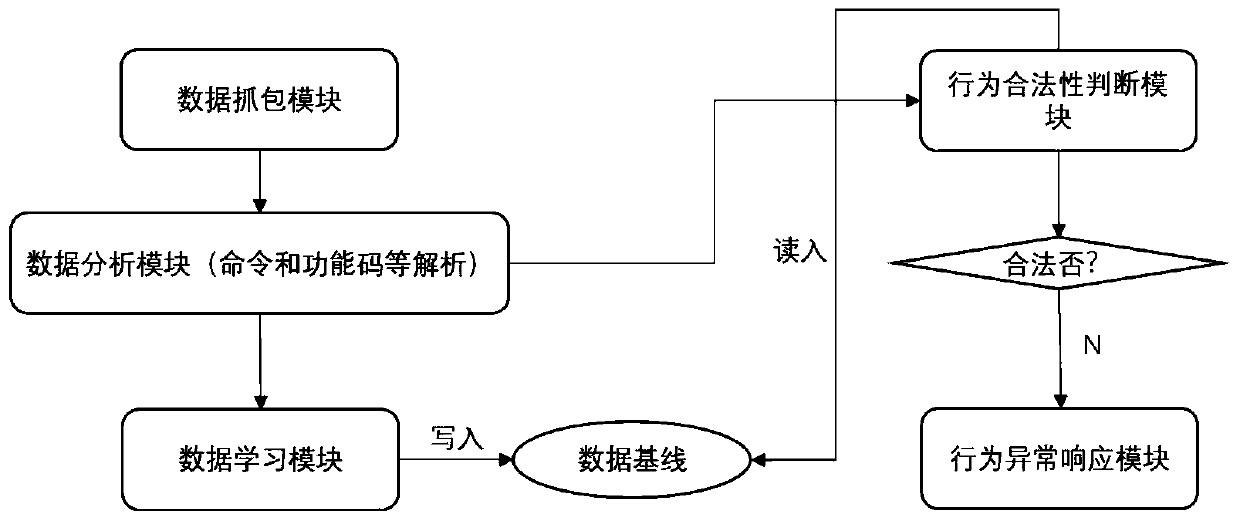
[0032] Embodiment 1: see figure 1 , figure 2 , a kind of security detection method based on Ethernet IP industrial control agreement, described method comprises the following steps: Step 1, set up network data capture module, module is mainly carried out for Ethernet network; Data link in the general Ethernet frame is carried out in the module The decoding is compatible with the VLAN format to meet the general requirements of the industrial control network; then, the module decodes the three layers of the network, namely the network layer, and parses out the IP address, etc., and then the module decodes the transport layer of the data packet, that is The source port and destination port can be analyzed. The communication port of the general Ethernet IP protocol is 44818. After analyzing the relevant information of the transport layer, the application layer information will be obtained. This application layer is the main content of the industrial control protocol; for In the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com