Stream cipher system generation method and apparatus, and terminal device
A technology of stream cipher and applied cipher, which is applied in the field of computer-readable storage medium and generation of stream cipher system, and can solve the problem of low security of stream cipher system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
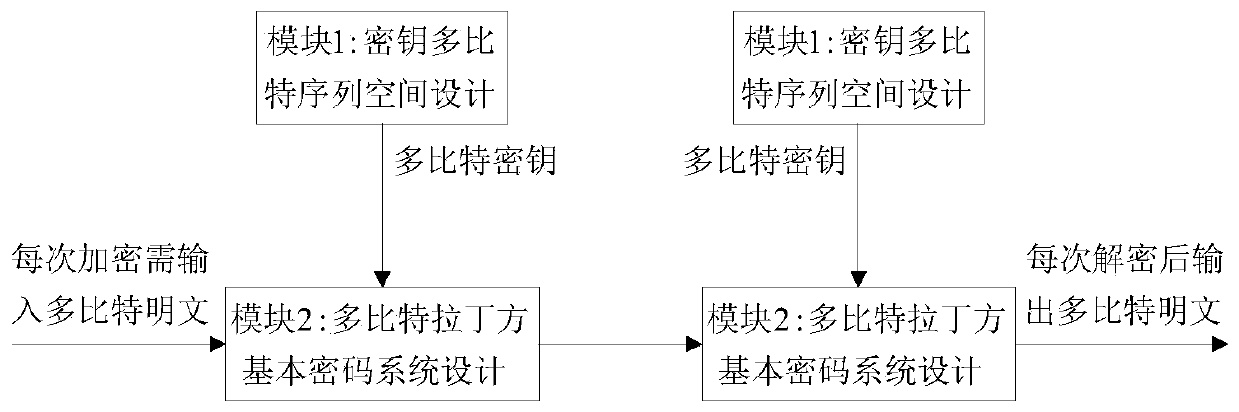
[0033] The applicant is aware, after an analysis of the prior art, that although the current figure 1 Some block cipher algorithm design methods are gradually integrated in the module 1 of , but the existing stream cipher algorithms are essentially based on the theoretical model of Shannon's perfect security system. That is, the prior art mainly has the following problems:
[0034](1) The application conditions of the theoretical model are limited: according to the existing cryptosystem theory, the theoretical basis of the existing stream cipher system is the perfect security system model proposed by Shannon. Moreover, the theoretical model requires that the number of keys should not be less than the number of plaintexts. Among them, the most perfect and most commonly used form of application is to design the number of basic keys equal to the number of basic plaintexts, and then use them evenly. In this way, in the design of computer security communication system, the theoret...
Embodiment 2
[0133] Corresponding to the generation method of the stream cipher system described in the above embodiments, Figure 4 A structural block diagram of the device for generating a stream cipher system provided by the embodiment of the present application is shown, and for convenience of description, only parts related to the embodiment of the present application are shown.
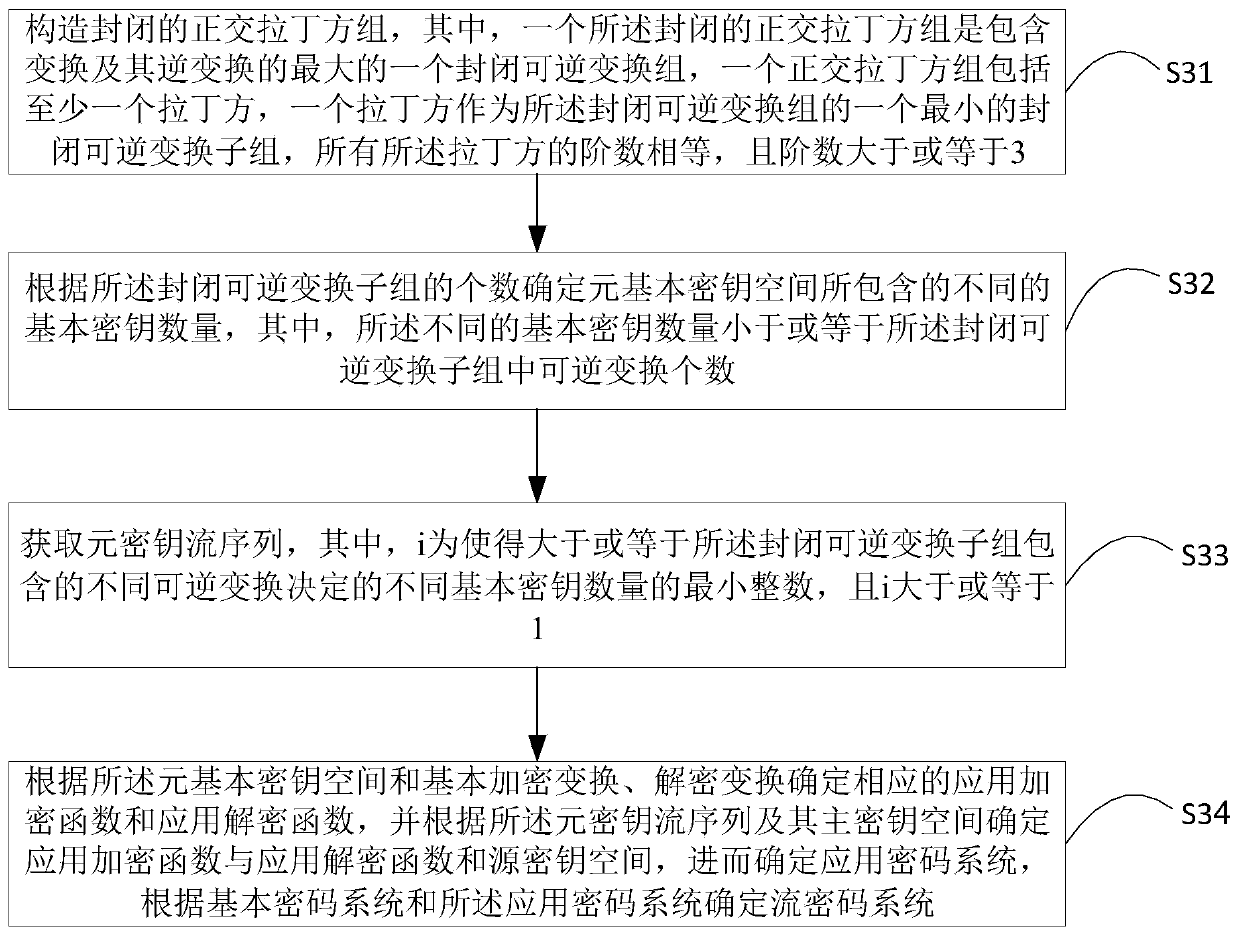
[0134] refer to Figure 4 , the generating device 4 of the stream cipher system includes: a closed orthogonal Latin square group construction unit 41, a basic key number determination unit 42, a key stream sequence acquisition unit 43, and a stream cipher system determination unit 44, wherein:
[0135]A closed orthogonal Latin square group construction unit 41 is used to construct a closed orthogonal Latin square group, wherein one closed orthogonal Latin square group is the largest closed reversible transformation group including transformation and its inverse transformation, An orthogonal Latin square gro...
Embodiment 3
[0164] Figure 5 It is a schematic structural diagram of a terminal device provided in Embodiment 3 of the present application. Such as Figure 5 As shown, the terminal device 5 of this embodiment includes: at least one processor 50 ( Figure 5 Only one processor is shown in ), a memory 51 and a computer program 52 stored in the memory 51 and operable on the at least one processor 50. When the processor 50 executes the computer program 52, the above-mentioned Steps in any of the various method embodiments:
[0165] Construct a closed orthogonal Latin square group, wherein, a closed orthogonal Latin square group is the largest closed reversible transformation group containing transformation and its inverse transformation, an orthogonal Latin square group includes at least one Latin square, a The Latin square is used as a minimum closed reversible transformation subgroup of the closed reversible transformation group, and the orders of all the Latin squares are equal, and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com