Block chain private transaction method, device and system based on trusted hardware
A blockchain and hardware technology, applied in the blockchain field, can solve problems such as low performance and complex transaction process, and achieve the effect of simple principle, privacy and security, and good performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] refer to Figure 2a As shown, it is a schematic diagram of the steps of the trusted hardware-based blockchain privacy transaction method provided by the embodiment of this specification. The method may include the following steps:
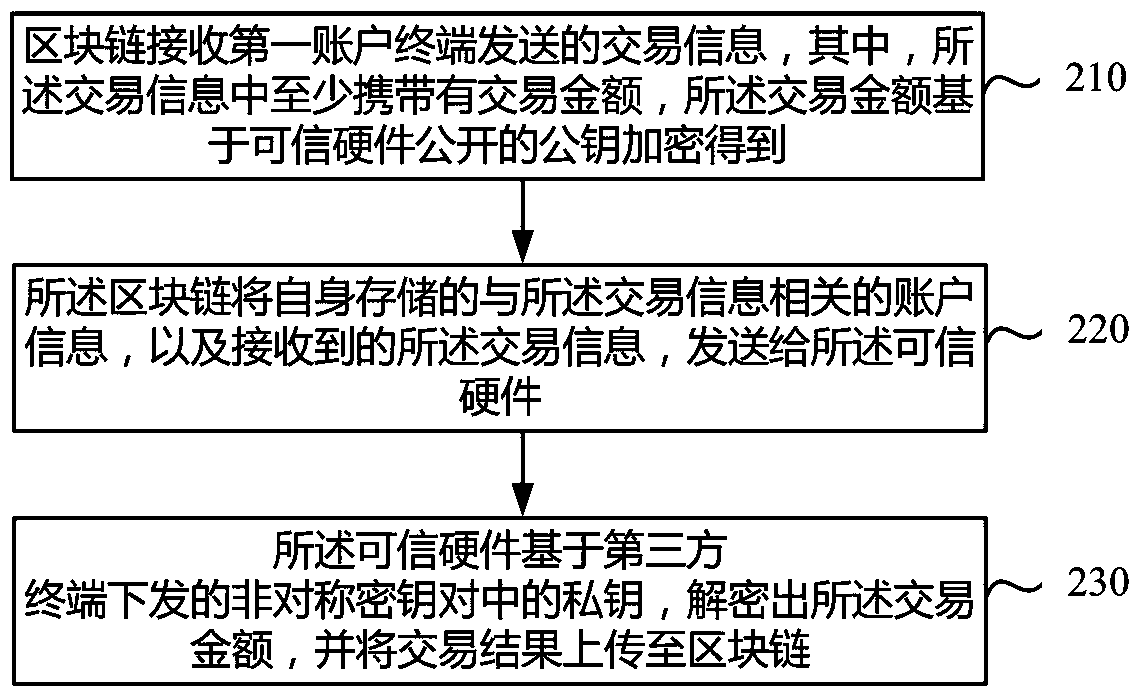
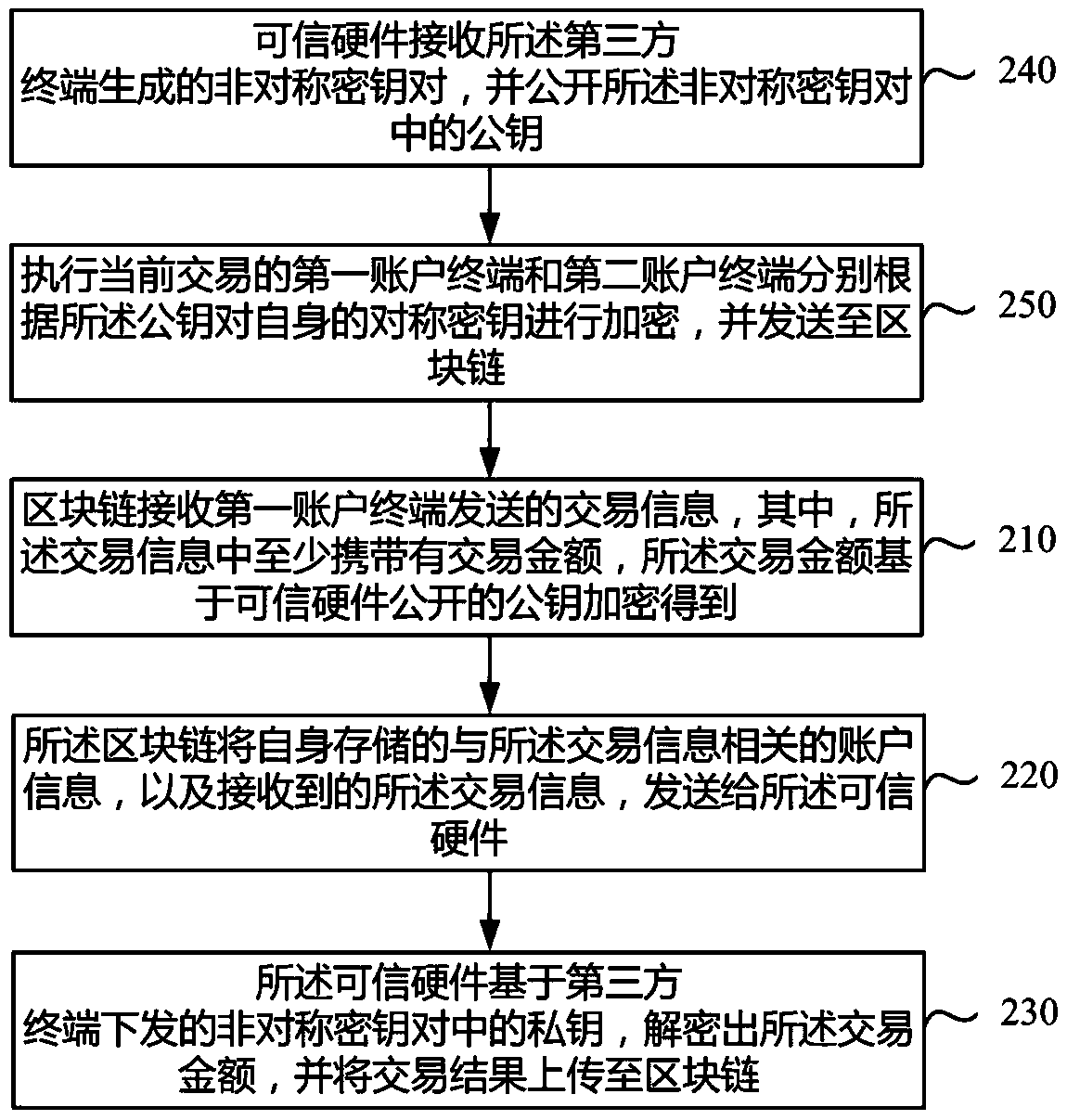
[0051] Step 210: The block chain receives the transaction information sent by the first account terminal, wherein the transaction information carries at least a transaction amount, and the transaction amount is encrypted based on a public key published by trusted hardware.
[0052] Step 220: The block chain sends the account information related to the transaction information stored in itself and the received transaction information to the trusted hardware.
[0053] Step 230: The trusted hardware decrypts the transaction amount based on the private key in the asymmetric key pair issued by the third-party terminal, and uploads the transaction result to the blockchain.
[0054] Optionally, the step 230 may be specifically performed as:
[005...
Embodiment 2
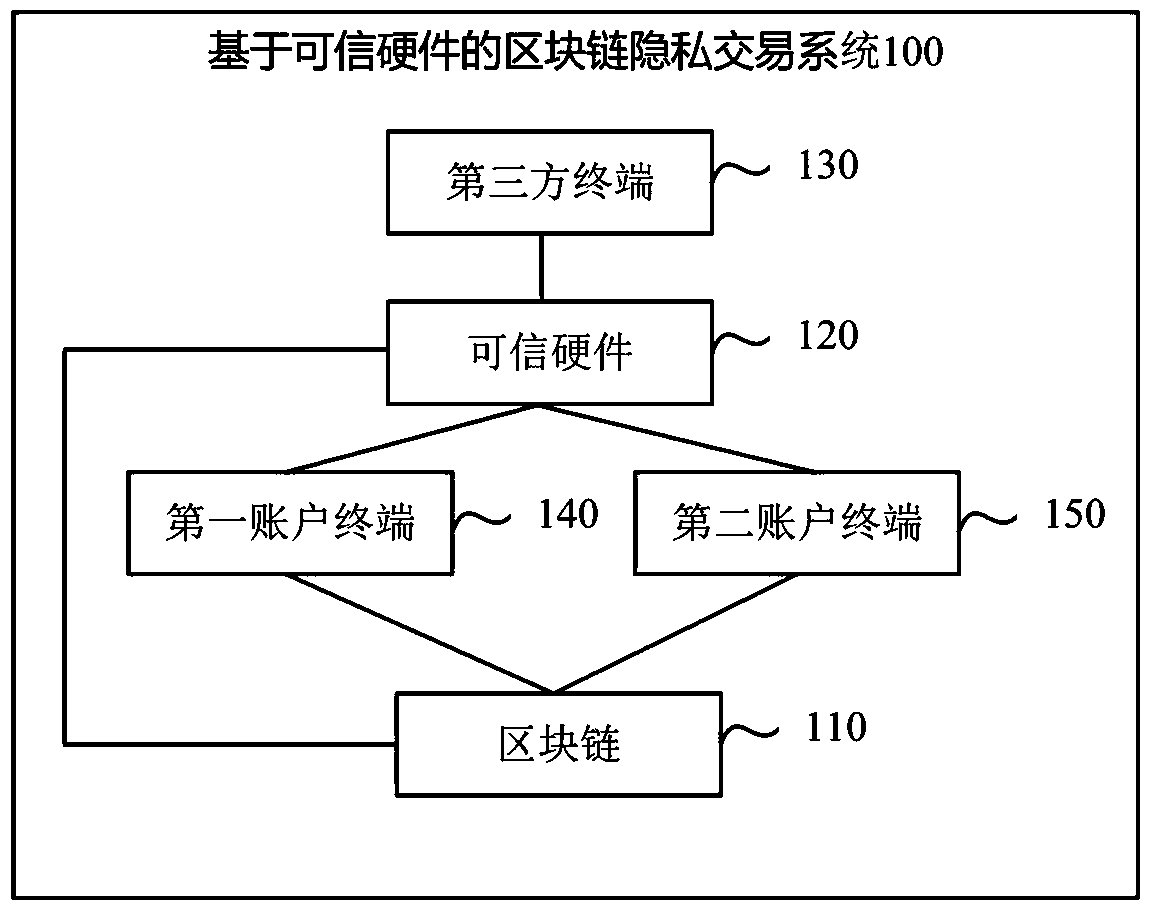
[0129] still refer to figure 1 As shown, the trusted hardware-based blockchain privacy transaction system provided by the embodiment of this specification, the privacy transaction system 100 may include: a blockchain 110, trusted hardware 120, a third-party terminal 130, and the first an account terminal 140 and a second account terminal 150;
[0130] Wherein, the block chain 110 receives the transaction information sent by the first account terminal 140, wherein the transaction information carries at least a transaction amount, and the transaction amount is encrypted based on the public key disclosed by the trusted hardware 120;
[0131] And, send the account information related to the transaction information stored by itself, and the received transaction information, to the trusted hardware 120;
[0132] The trusted hardware 120 decrypts the transaction amount based on the private key in the asymmetric key pair issued by the third-party terminal 130 , and uploads the transa...
Embodiment 3
[0149] Refer below Figure 8 The electronic equipment of the embodiment of this specification is introduced in detail. Please refer to Figure 8 , at the hardware level, the electronic device includes a processor, and optionally also includes an internal bus, a network interface, and a memory. Wherein, the memory may include a memory, such as a high-speed random-access memory (Random-Access Memory, RAM), and may also include a non-volatile memory (Non-Volatile Memory), such as at least one disk memory. Of course, the electronic device may also include hardware required by other services.
[0150] The processor, network interface, and memory can be interconnected by an internal bus, which can be an Industry Standard Architecture (ISA) bus, a Peripheral Component Interconnect (PCI) bus, or an extended industry standard Structure (Extended Industry Standard Architecture, EISA) bus, etc. The bus can be divided into address bus, data bus, control bus and so on. For convenience...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com