Internet analysis system
An analysis system and Internet technology, applied in the field of Internet analysis systems, can solve problems such as poor security performance, difficulty in detection, single detection means, etc., and achieve the effect of efficiently restricting operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
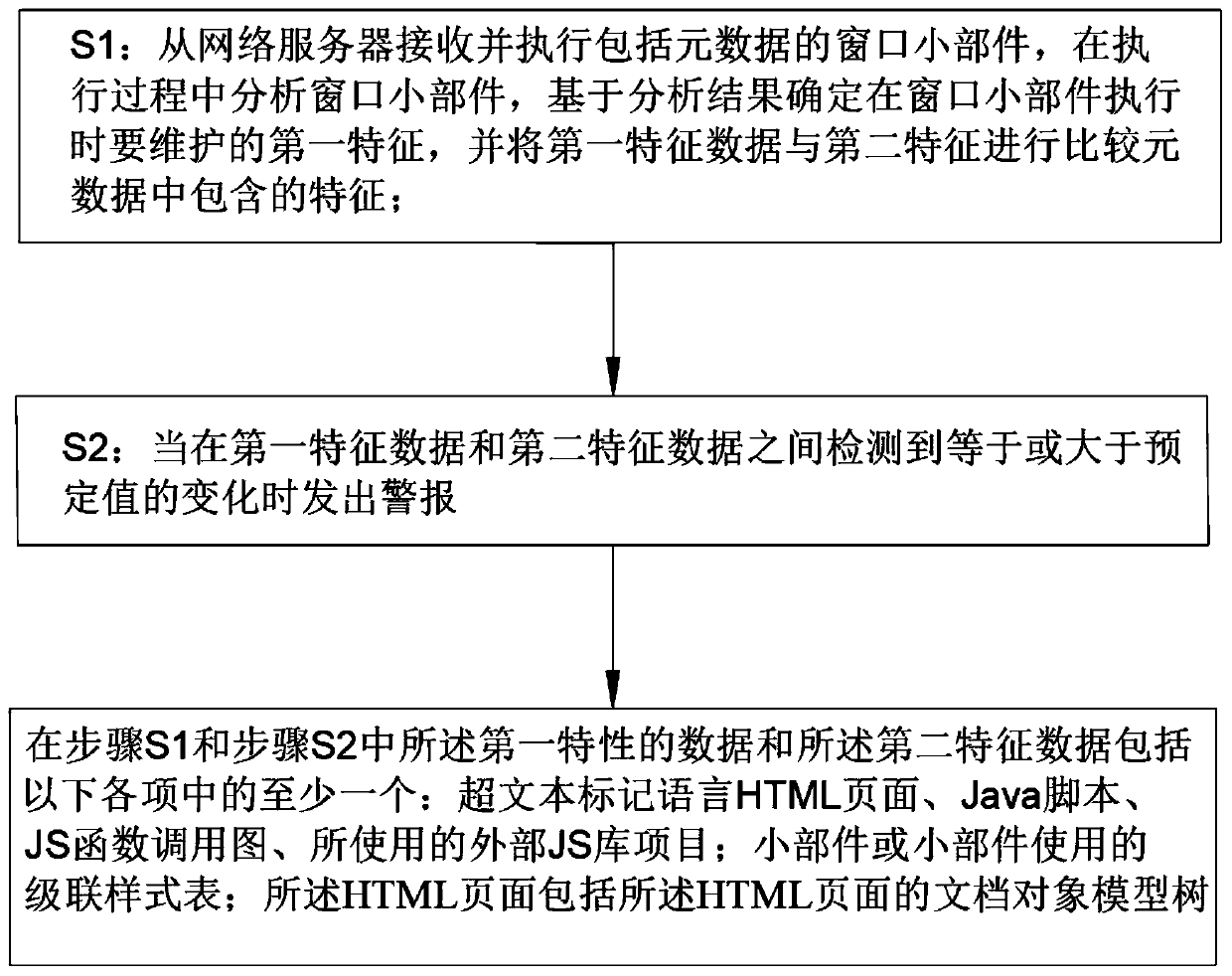
[0033] Embodiment 1: An Internet analysis system, comprising: a receiving module configured to receive a widget including metadata from a web server; an analysis module configured to execute the widget including metadata, in analyzing the widget during execution, determining a first characteristic to be maintained when the widget executes based on the analysis results, and comparing the first characteristic data with the second characteristic contained in the metadata; an alert module, which is constructed is configured to issue an alarm when a change equal to or greater than a predetermined value is detected between the first characteristic data and the second characteristic data. The data of the first characteristic and the data of the second characteristic include at least one of the following items: hypertext markup language HTML pages, Java scripts, JS function call graphs, external JS library items used; widgets or A cascading style sheet used by the widget; the HTML pag...
Embodiment 2
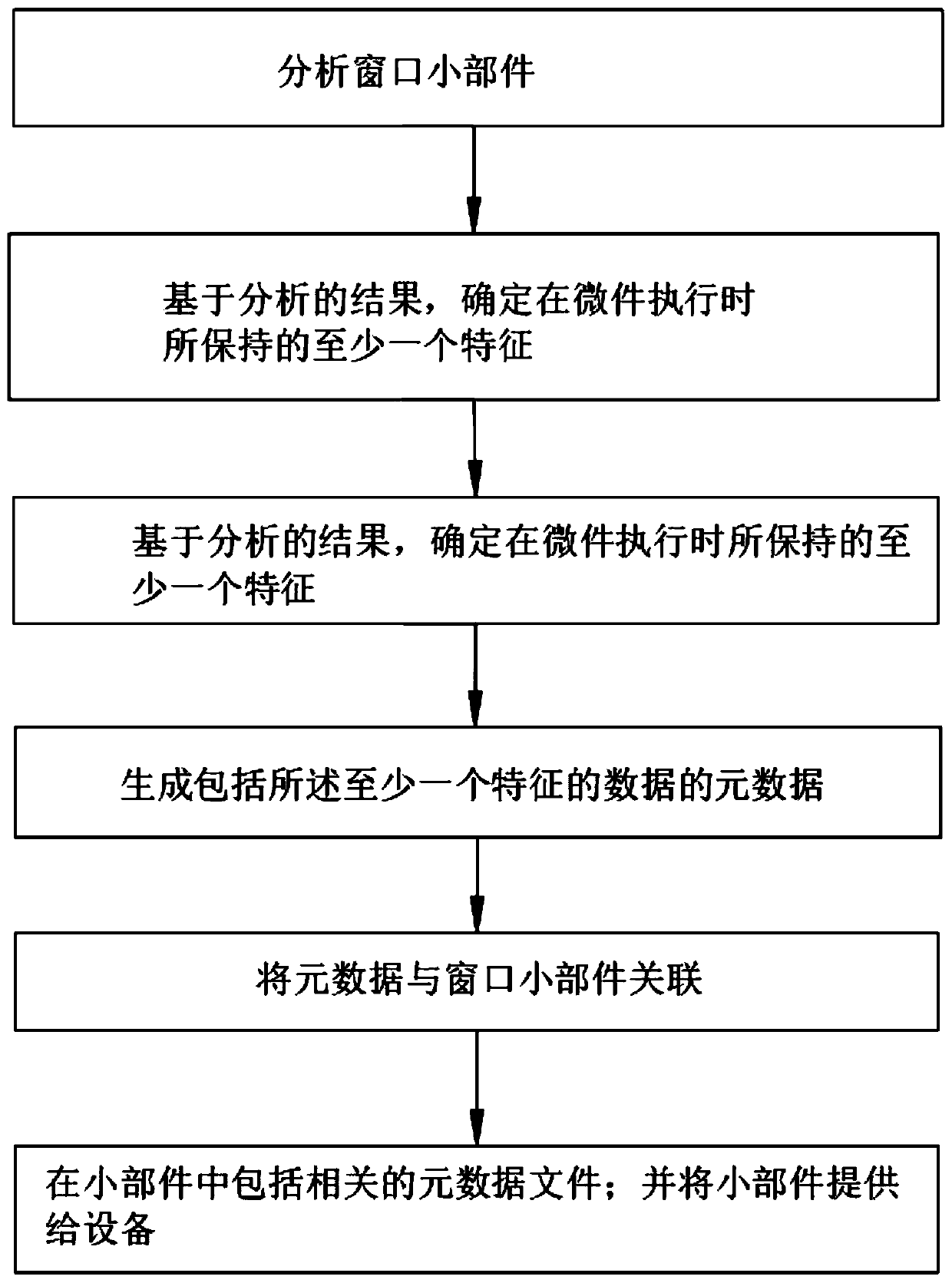
[0034]Embodiment 2: This embodiment should be understood as at least including all the features of any one of the foregoing embodiments, and further improvement on the basis thereof, specifically, an Internet analysis system, including: a receiving module, which is configured to The web server receives the widget including the metadata; an analysis module configured to execute the widget including the metadata, analyze the widget during execution, and determine based on the analysis results to maintain the widget when the widget executes The first feature of the first feature, and compare the first feature data with the second feature feature included in the metadata; an alarm module, which is configured to detect between the first feature data and the second feature data equal to or greater than a predetermined Alert when the value changes. Specifically, in the process of cross-searching, web pages often have orphan page implants. In this case, there are various small windows...
Embodiment 3
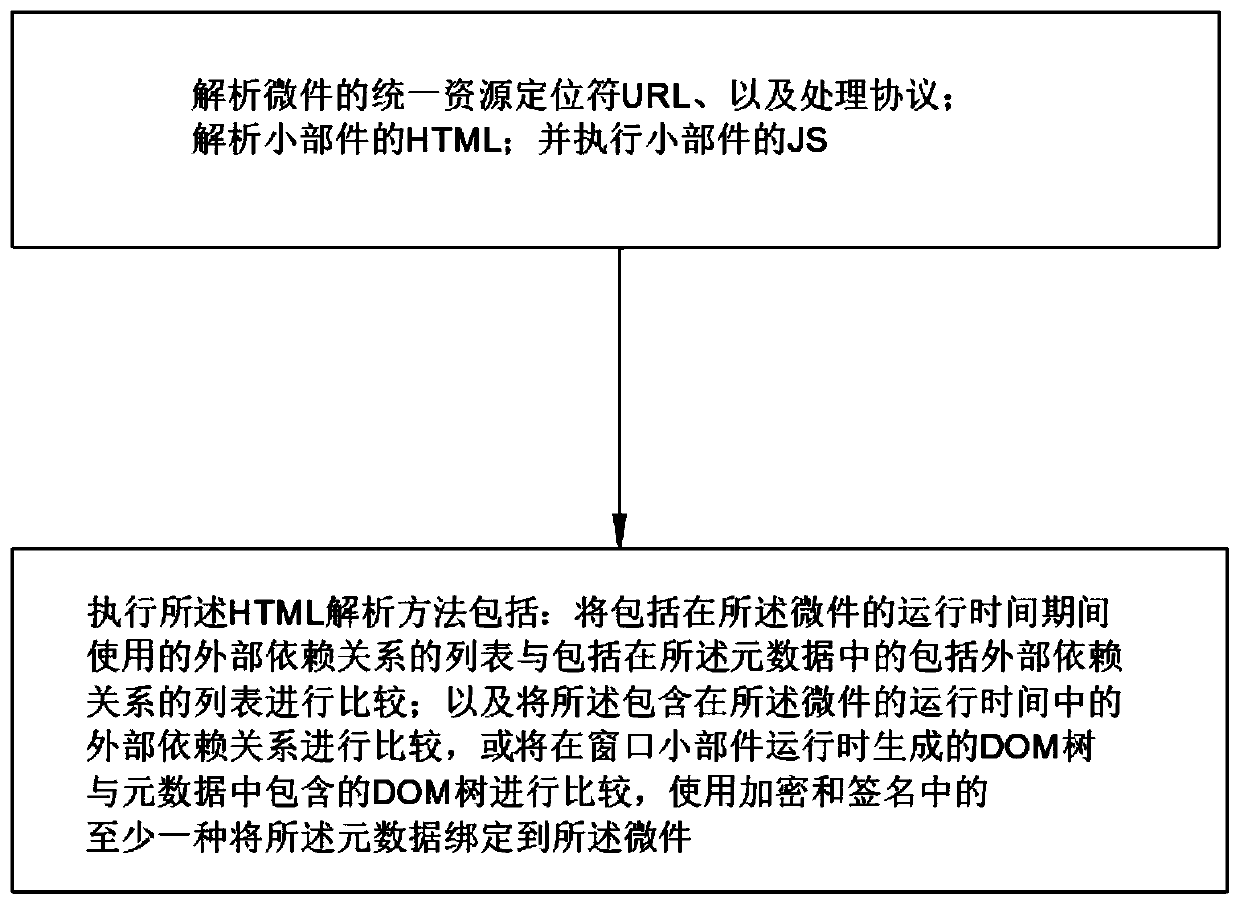
[0046] Embodiment 3: This embodiment should be understood as at least including all the features of any one of the foregoing embodiments, and further improvements are made on the basis thereof. Specifically, the system of this embodiment includes a product that executes a Web program, including: hardware A storage device having stored therein computer executable program code that, when executed by a computer hardware system including a security system configured to test a web service, causes the computer hardware system to perform the following operations: performing static analysis on the web service; performing the static analysis on the web service by the security system; during the static analysis, locating seed instructions in the program code of the web service, wherein the identity of the requester is determined by the web service; during the static analysis, determining whether the value in the seed instruction selects between a plurality of paths for branching in the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com