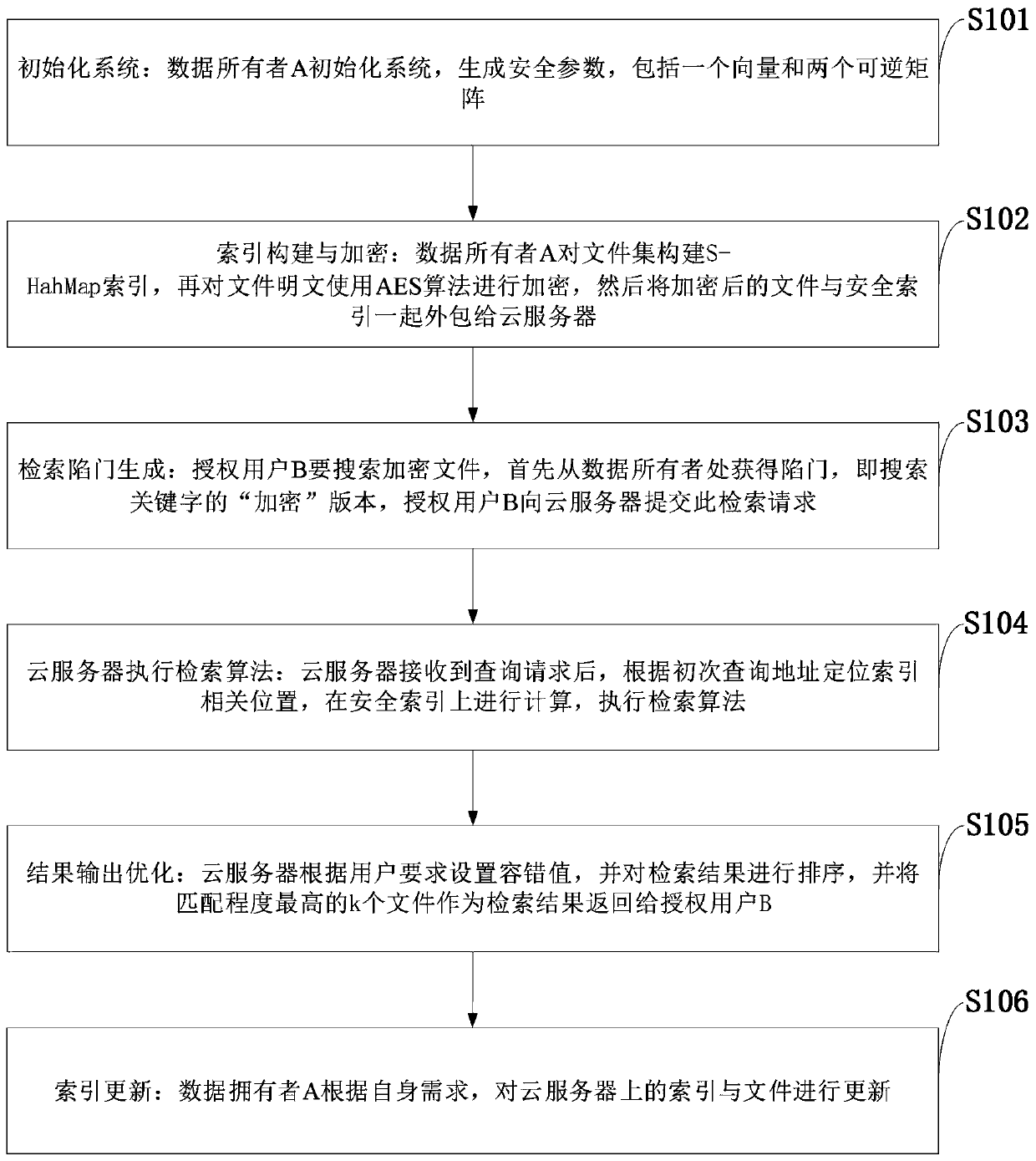
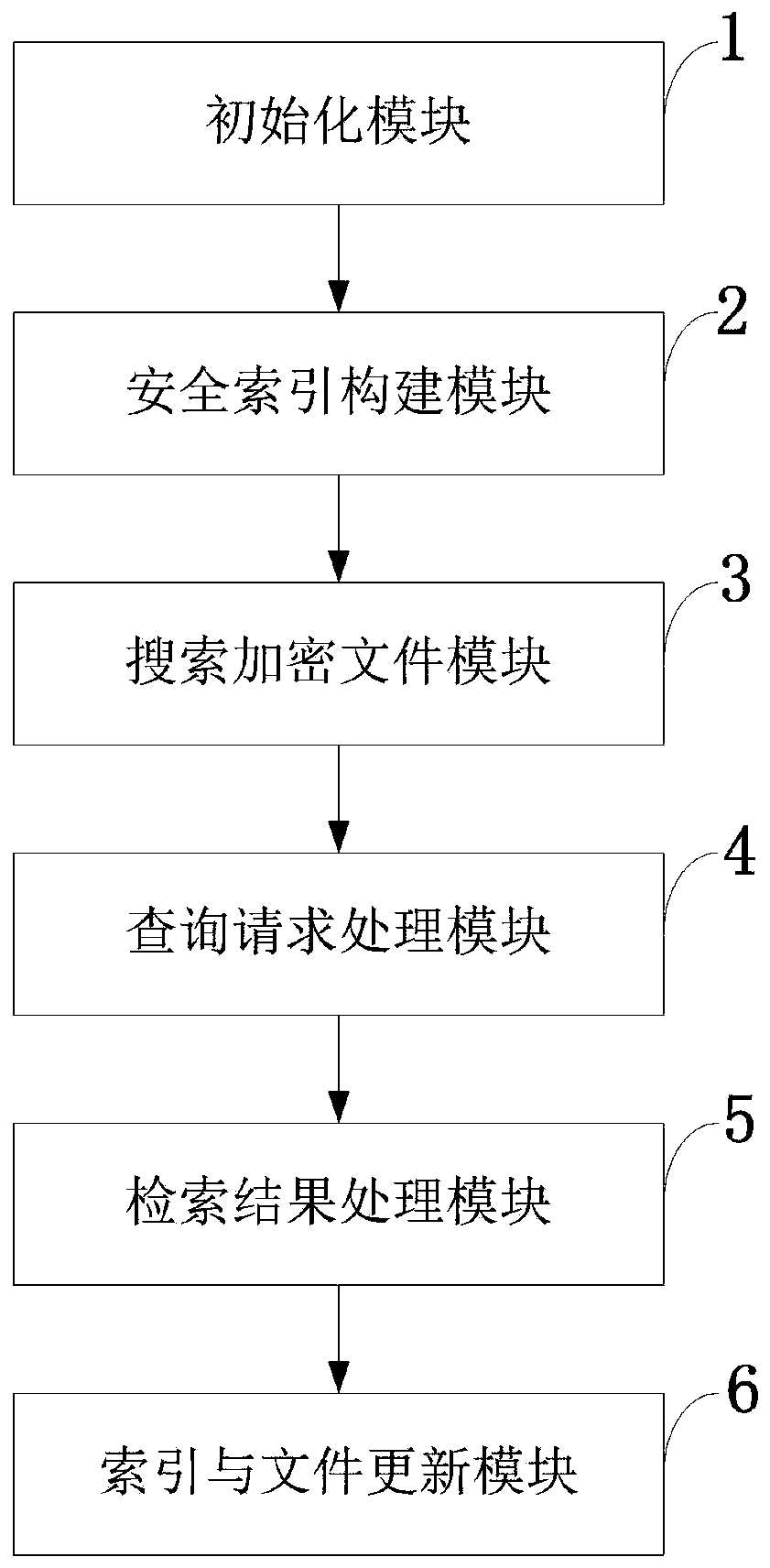
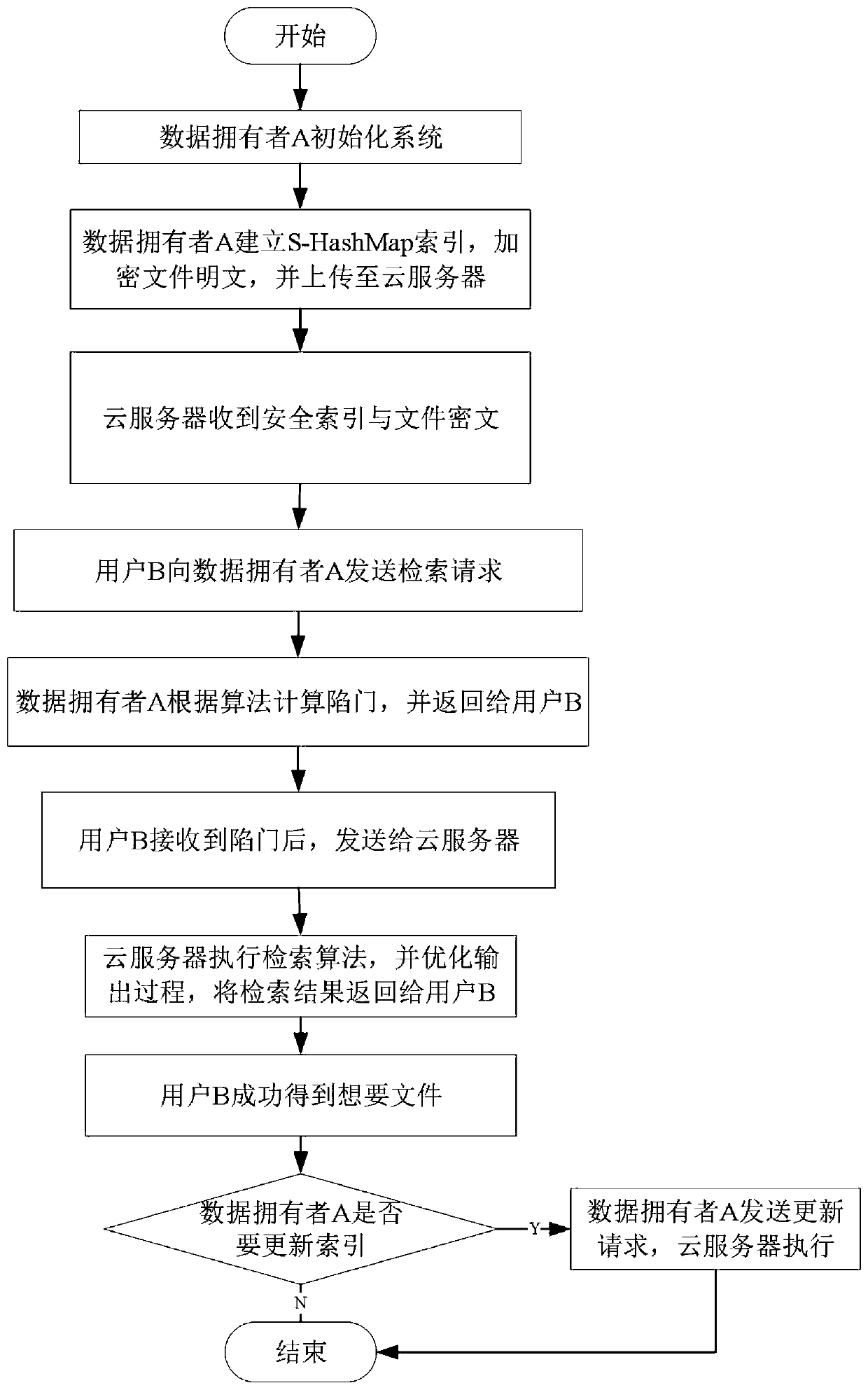
Searchable encryption method and system, storage medium, vehicle-mounted network and intelligent power grid
An encryption method and indexing technology, applied in transmission systems, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as difficulty in index update and deletion, difficulty in rapid update, complete and complex index structure, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
comparative approach 1
[0103] In the simulation of this invention, first test the generation time of the index, respectively extract keywords to 5, 10, 15, 20, and 25 files to construct the S-HashMap index, and compare it with other two schemes (comparison scheme 1: Privacy preserving multi -keyword ranked search over encrypted cloud data. Comparison scheme 2: Toward efficient multi-keyword fuzzy search over encrypted outsourced data with accuracy improvement.) for comparison, such as Image 6 As shown, the present invention has obvious advantages in index generation efficiency.
[0104] Figure 7 For the simulation of trapdoor generation time in this method, the present invention adopts an encryption algorithm similar to the comparison scheme, so the time consumption growth trend among multiple schemes is similar, but the time consumption of the present invention is still smaller than the other two comparison schemes. Figure 8 The simulation for which the time is retrieved in this method. In the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com