Network camouflage method, device, equipment and computer readable storage medium
A network camouflage, host technology, applied in the field of network security, can solve the problem of honeypots or honeynet being seen through by attackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
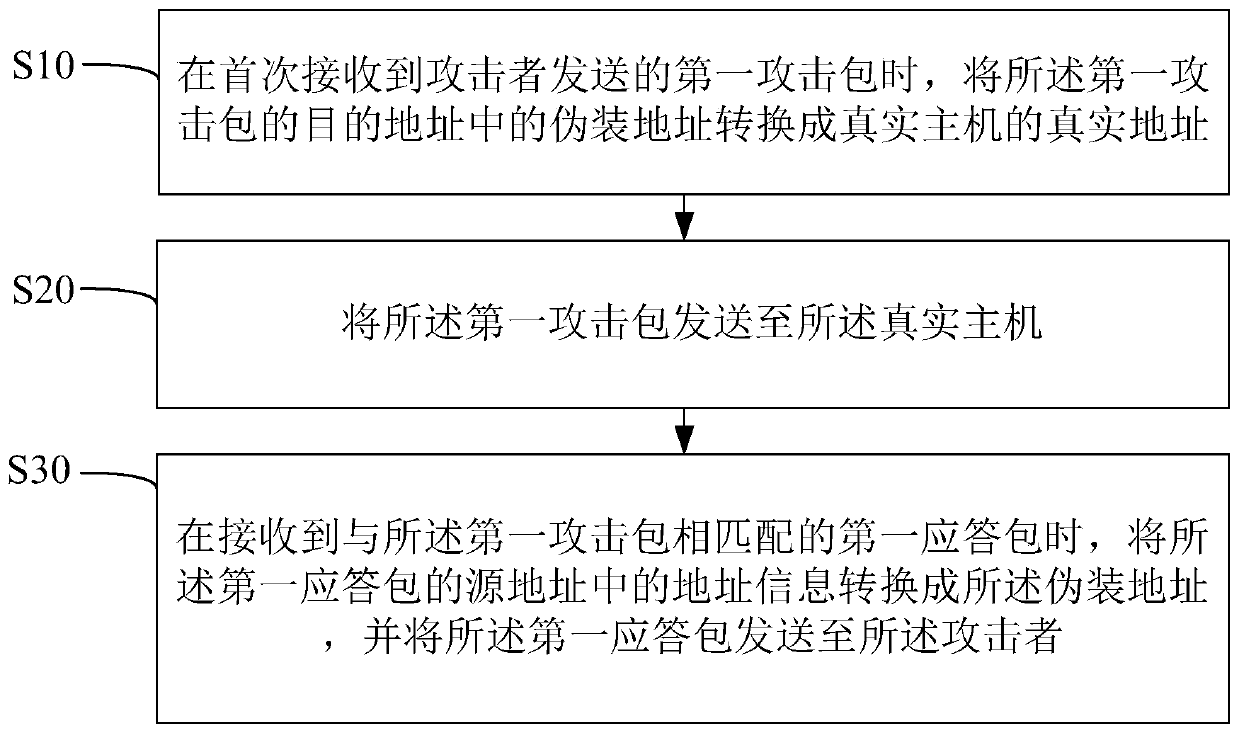
[0085] Based on the first embodiment, the second embodiment of the network camouflage method of the present invention is proposed. In this embodiment, after step S10, it also includes:
[0086] Step a, when receiving the second attack packet sent by the attacker, converting the fake address in the destination address of the second attack packet into the honeypot address of the honeypot;
[0087] Step b, sending the second attack packet to the honeypot;
[0088] Step c, after receiving a second response packet matching the second attack packet, converting the address information in the source address of the second response packet into the spoofed address, and sending the second response packets are sent to the attacker.
[0089] In one embodiment, after receiving the first attack packet sent by the attacker, if the second attack packet sent by the same attacker is subsequently received, it means that the real host successfully authenticates with the attacker through the first ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com