Network traffic anomaly detection method based on small amount of annotation data
A network traffic and labeling data technology, applied in the field of network traffic anomaly detection based on a small amount of labeling data, can solve the problems of wasting labeling cost, not applying abnormal sample data information, difficult to cover, etc., to ensure stability and improve loss sensitivity. Learning ability, the effect of alleviating the overfitting problem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
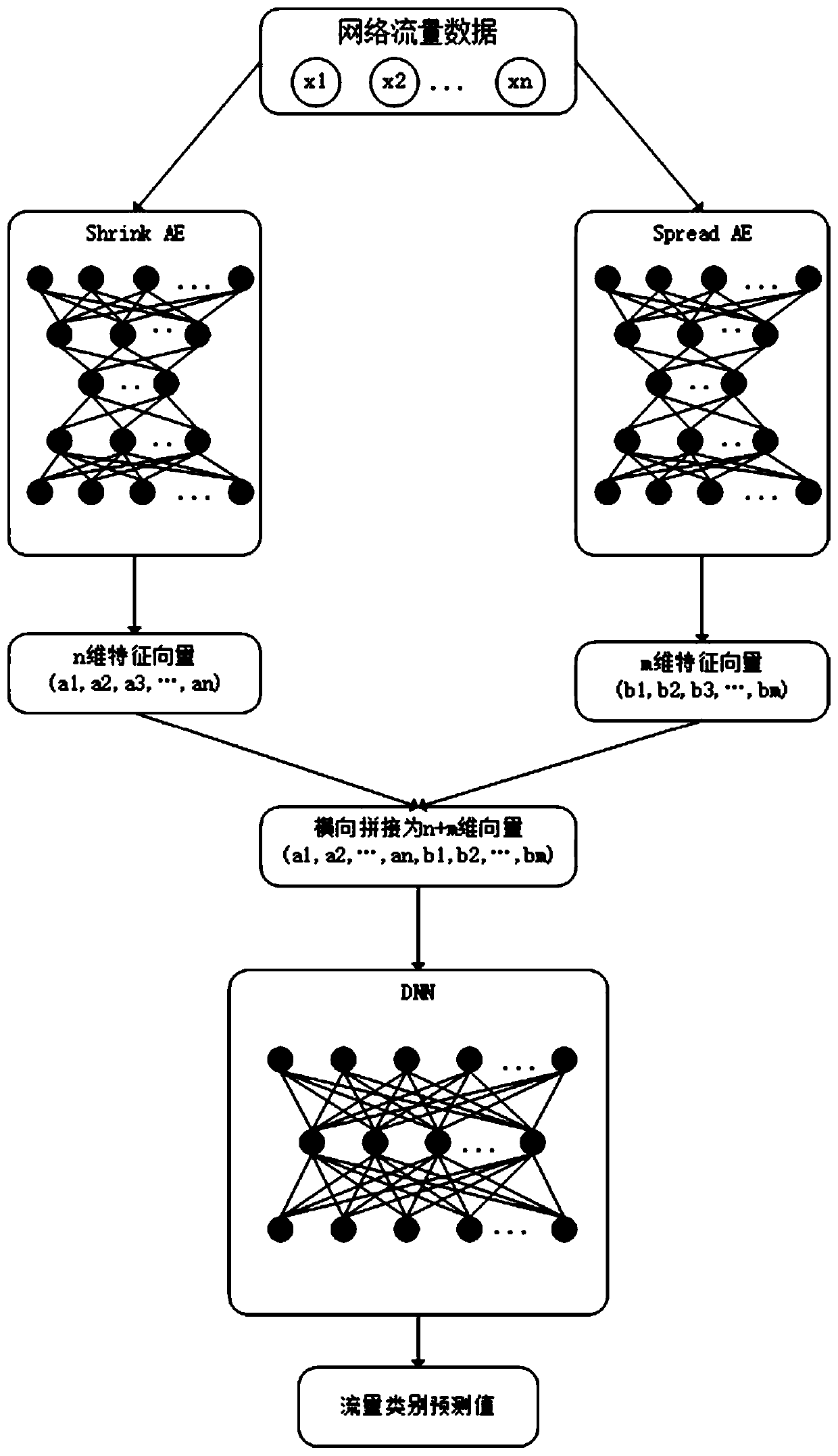
[0027] Such as figure 1 As shown, a method for detecting network traffic anomalies provided by the present invention includes the following steps:
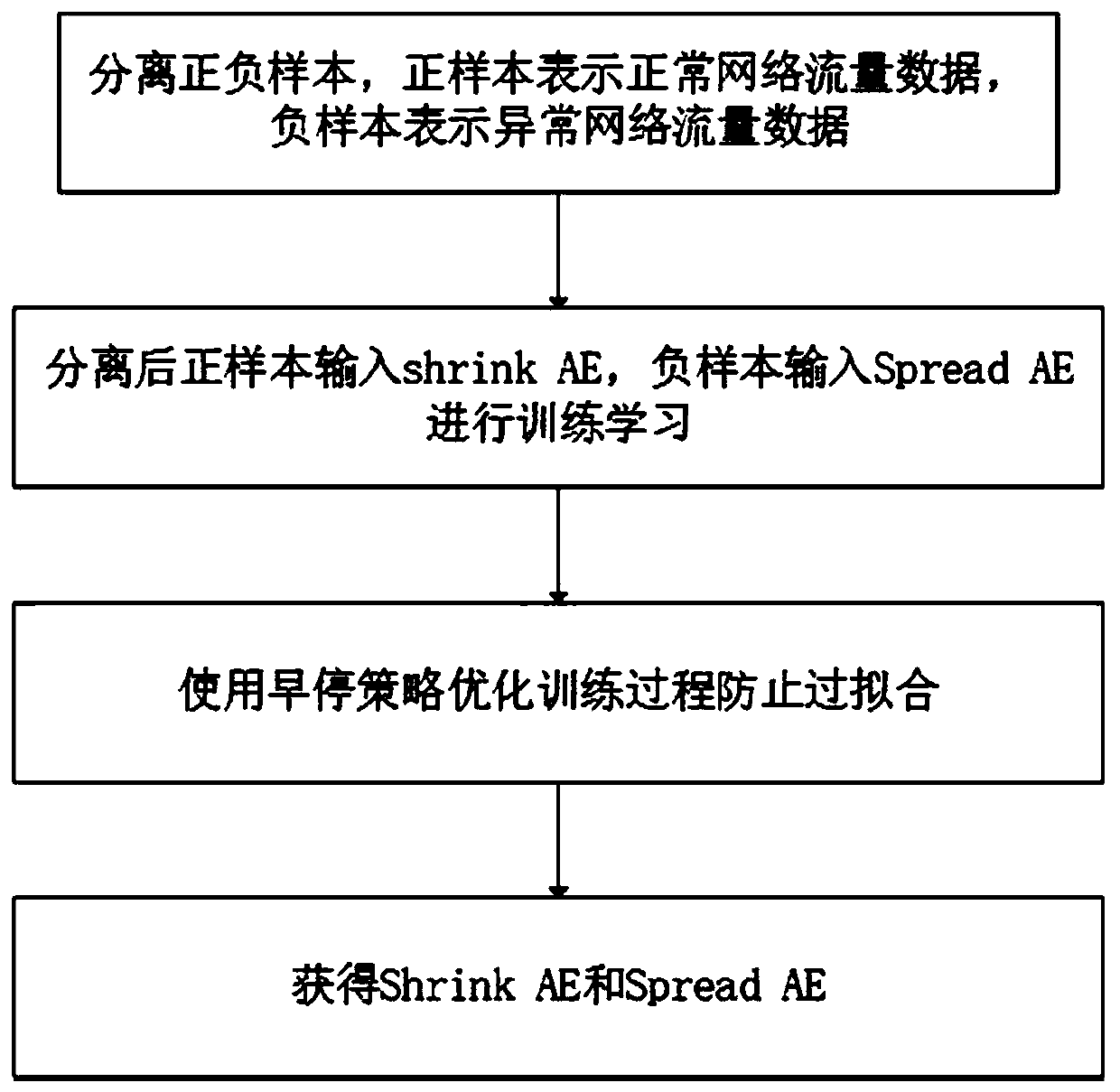
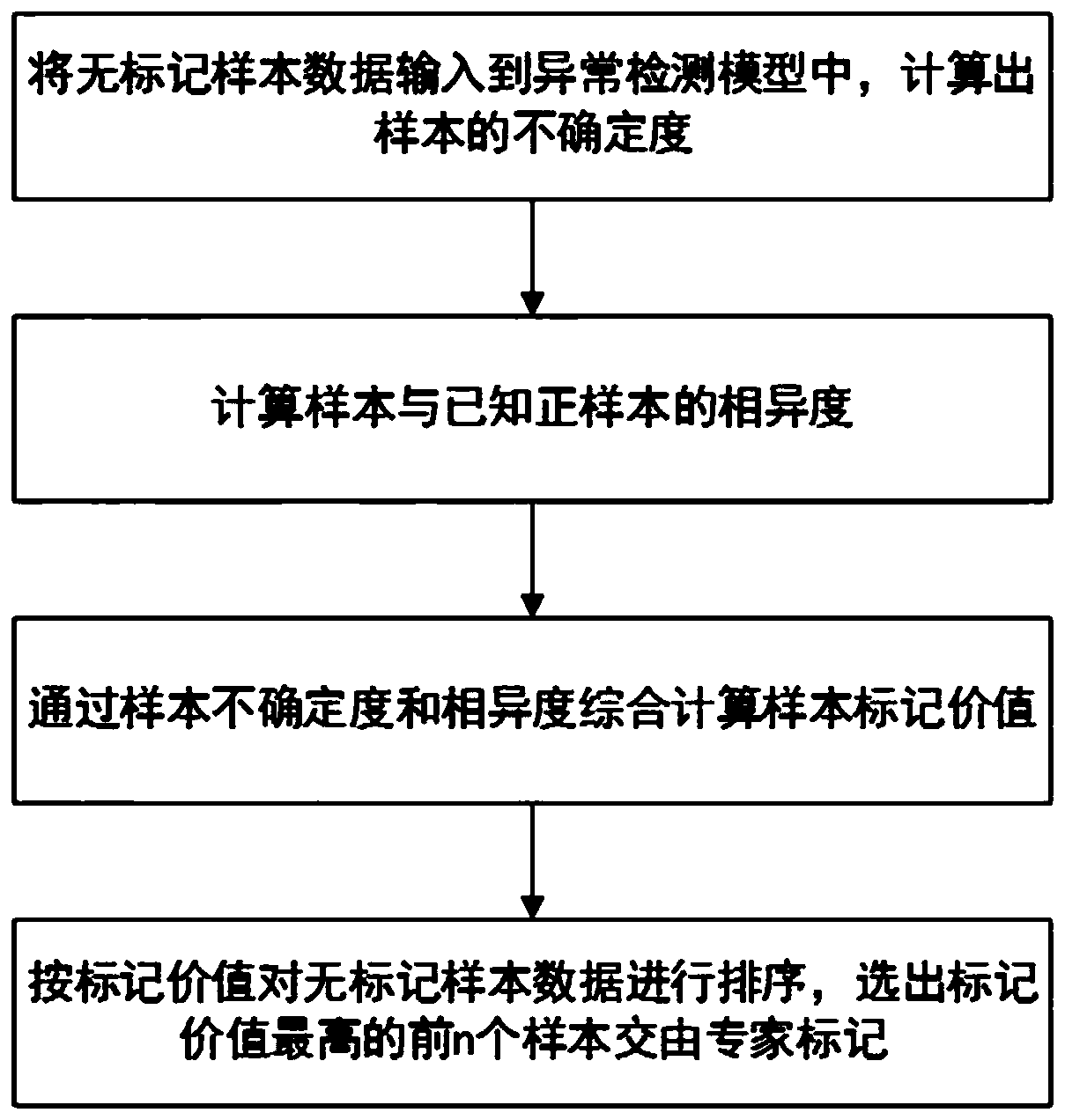
[0028] (1) Training autoencoder (Autoencoder, referred to as AE): download the intrusion detection public dataset NSL-KDD from the network, each piece of data in the dataset includes TCP connection duration, protocol type, target host network service type, access There are 41 characteristics related to network traffic such as the number of control files, and there are flag information to indicate whether this piece of data is normal traffic or abnormal traffic on the network. The normal traffic flag value is 1, which is called a positive sample, and the abnormal traffic flag value is -1. It is called a negative sample; if all non-numeric features are encoded as numerical features, each p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com