A remote office business authorization method, terminal and system
An authorized terminal, remote office technology, applied in transmission systems, office automation, digital transmission systems, etc., can solve the problems of multiple security risks, inconvenience of traceability, inflexibility, etc., to avoid security limitations, improve flexibility and security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
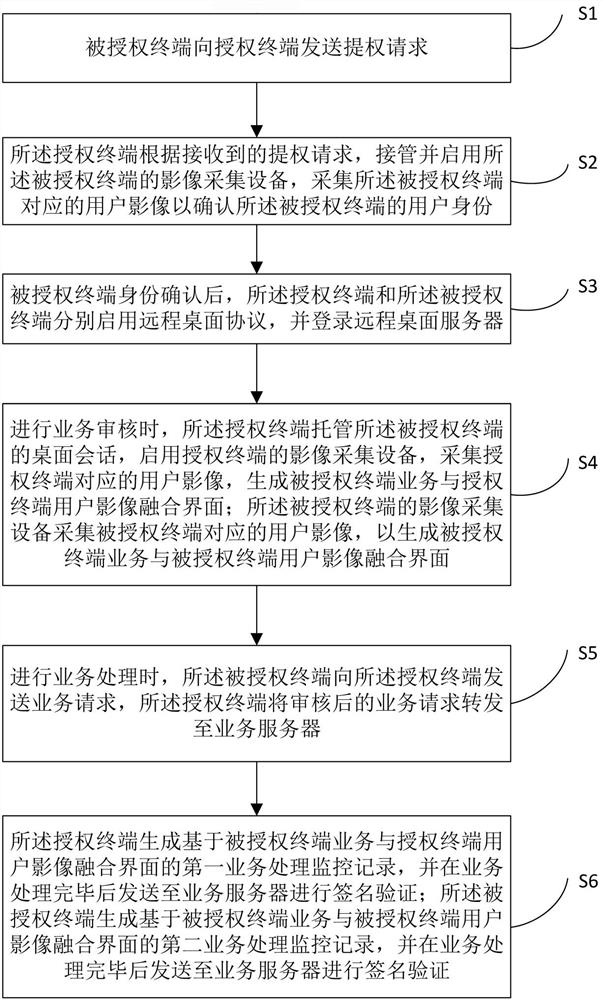
[0041] Such as figure 1 As shown, a remote office business authorization method includes the following steps:
[0042] S0, determine the authorized terminal, determine the authorized terminal, determine the service server;
[0043]It can be understood that the authorized terminal or the authorized terminal is not unique, the authorized terminal may be other authorized terminals as authorized terminal devices, and the authorized terminal may be other authorized terminals as authorized terminal devices Terminal; the authorized terminal and the authorized terminal may be a smart phone, a desktop computer, a portable notebook computer, a tablet device, a digital broadcast terminal, an intelligent control device or an intelligent wearable device, etc.
[0044] S1, when the authorized terminal needs to process business, the authorized terminal will send a privilege escalation request to the authorized terminal;
[0045] S2, the authorized terminal takes over and activates the imag...
Embodiment 2
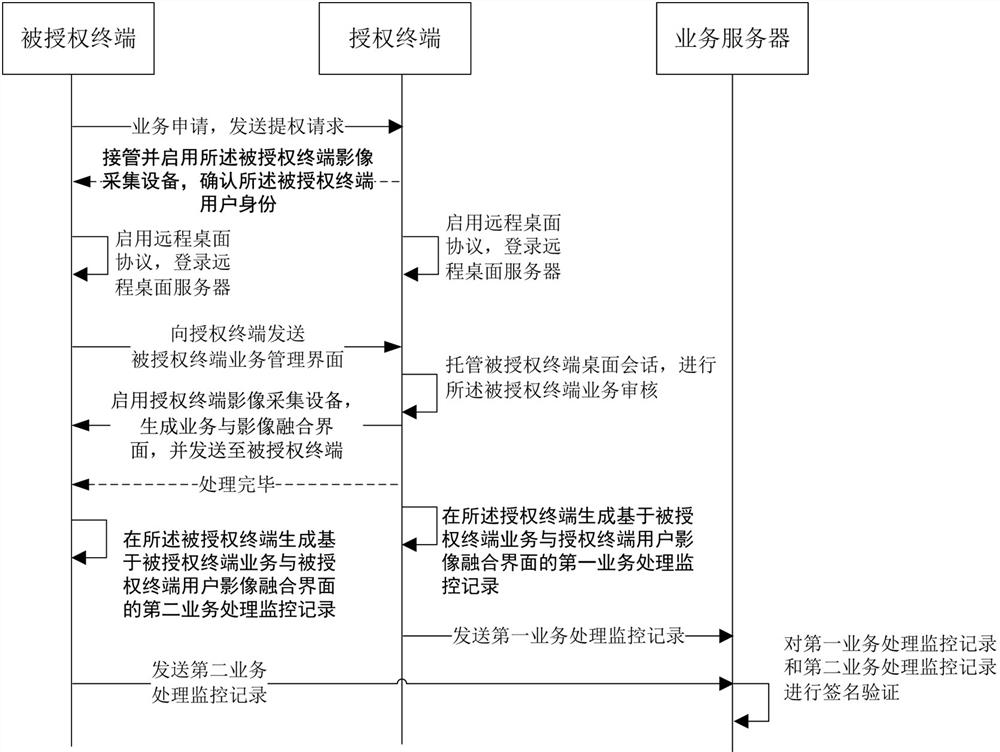
[0063] attached Figure 4 An authorization terminal is shown, and the authorization terminal includes a first user audit module, a second user audit module, a third user audit module, a business audit module, a business processing module, and a signature processing module; wherein,
[0064] The first user verification module is configured to receive a request for escalation of rights sent by an authorized terminal, take over and enable the image acquisition device of the authorized terminal according to the request for escalation of rights, collect images of users corresponding to the authorized terminal, and confirm that the The user identity of the authorized terminal;
[0065] The second user review module is used to enable the image collection device of the authorized terminal, collect the user image corresponding to the authorized terminal, generate the fusion interface of the authorized terminal business and the authorized terminal user image, and send it to the authoriz...
Embodiment 3
[0072] attached Figure 4 It also shows an authorized terminal, which includes a first user audit module, a second user audit module, a business processing module, a business audit module, and a signature processing module; wherein,
[0073] The first user verification module is used to receive the authorized terminal service and the image fusion interface of the authorized terminal user sent by the authorized terminal, and confirm the user identity of the authorized terminal;
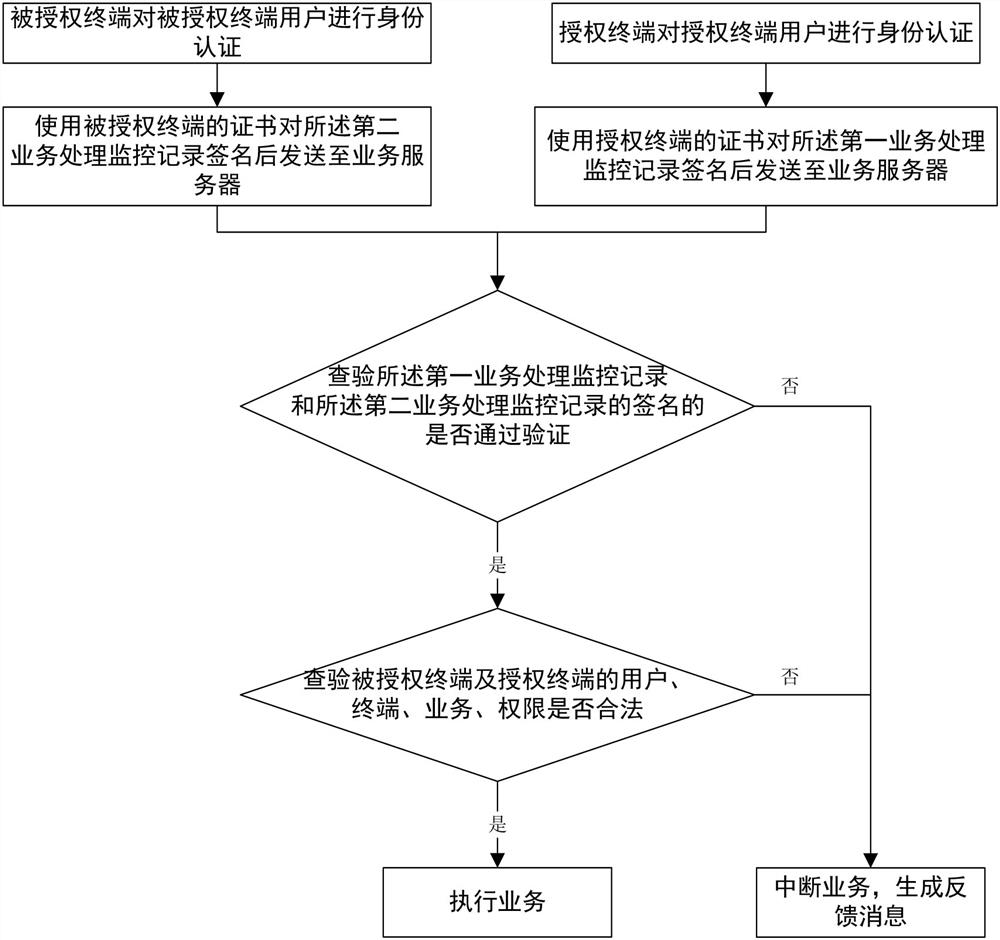
[0074] The second user verification module is used to authenticate the identity of the authorized terminal user before signing the second business processing monitoring record; specifically, the method adopted for the identity authentication of the authorized end user can be a biometric identification algorithm, UKey identification algorithm or PIN code verification algorithm, or a combination of at least two of the above authentication methods;
[0075] The business processing module is used to send ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com