Three-party verifiable key agreement method for centralized mobile positioning system
A technology for authenticated key negotiation and mobile positioning, which is applied in the field of three-party certifiable key negotiation for centralized mobile positioning systems, and can solve the problems of high algorithm complexity, inability to guarantee forward security, and inability to resist active attacks. Guaranteed safety, operability, and complete functionality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments:
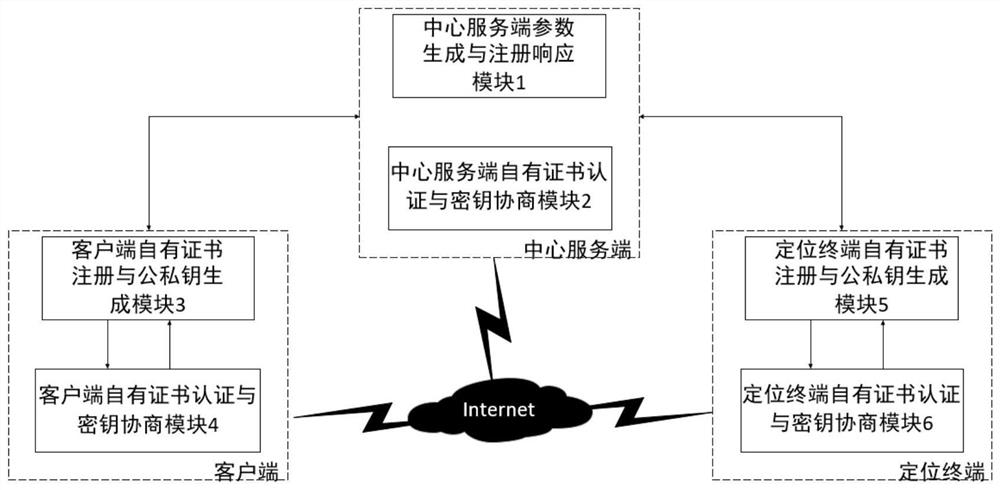
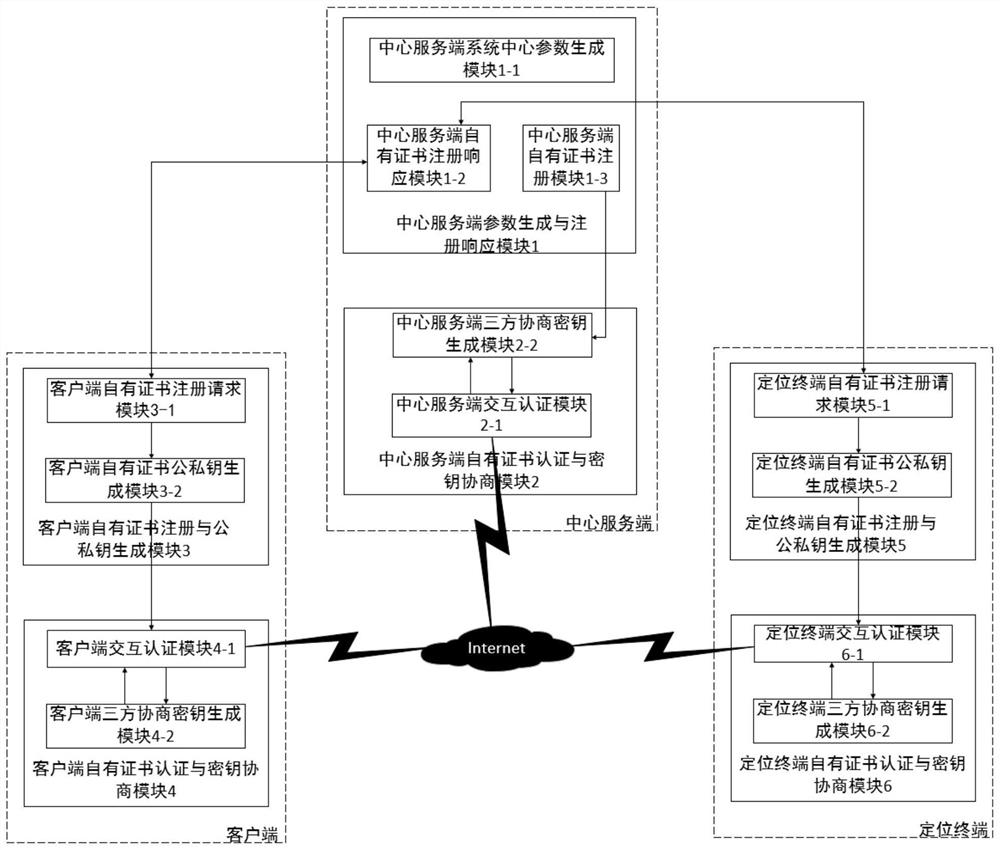
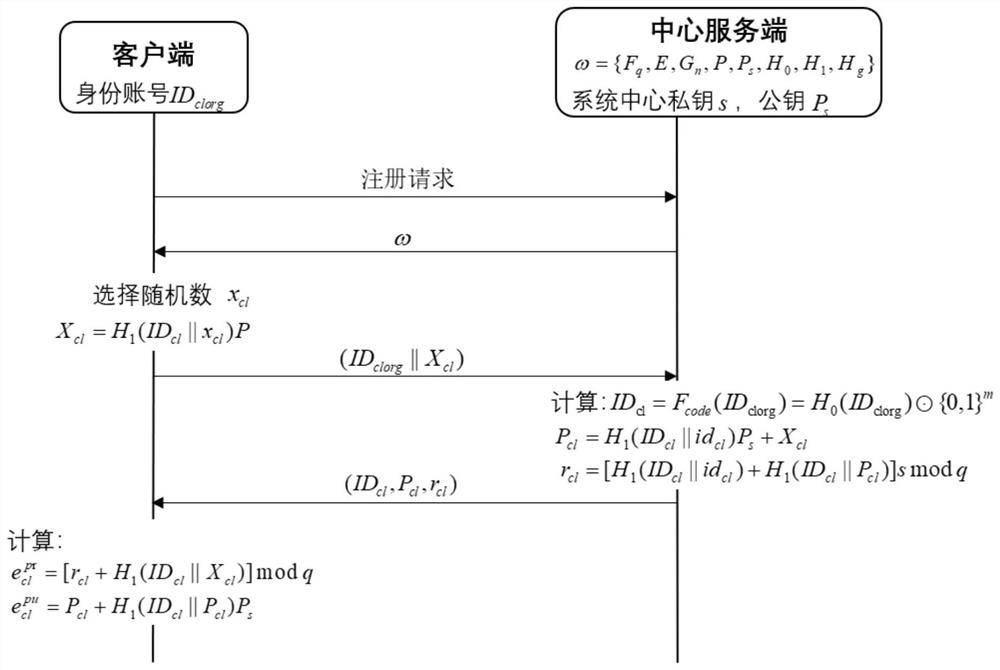
[0061] Based on the self-designed self-certified ECC three-party verifiable key negotiation algorithm, the present invention provides a method for interactive authentication and key negotiation applied to a centralized mobile positioning system. The present invention can be deployed as a separate authentication negotiation function module in existing In some three-party interaction systems, as the initial module of entity online security interaction, it generates session keys safely and reliably for multi-entity interaction; The key length is short and the computational complexity is low, and it can run stably in a lightweight computational unit; at the same time, the security of the long-term key can be guaranteed to the greatest extent without relying on a certificate authority and a key generation center; and the method of the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com