Safety prevention and control method, device and system based on biological feature recognition
A biometric identification and biometric technology, applied in the field of information identification, can solve problems such as failure to detect whether the authorized person is in a voluntary/normal identification state on the device side, and potential safety hazards, so as to protect personal health, improve safety, and protect personal health. safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
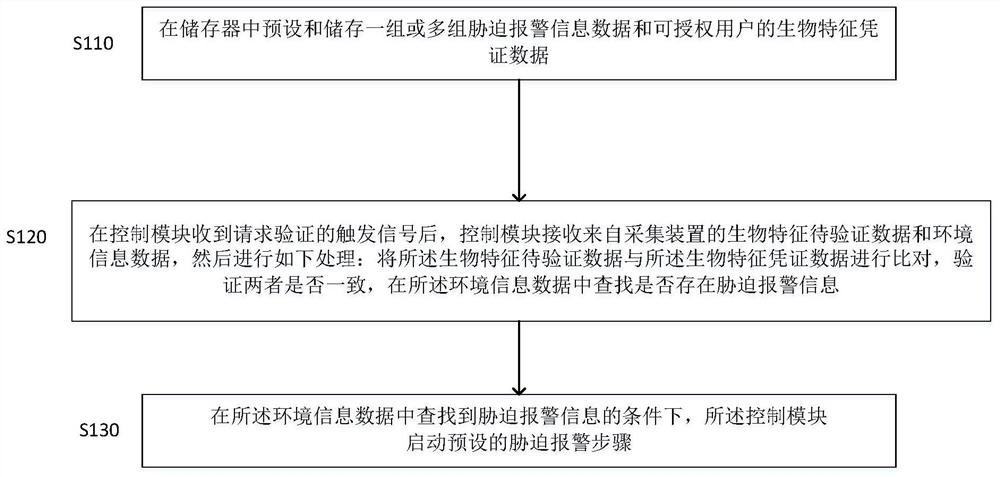
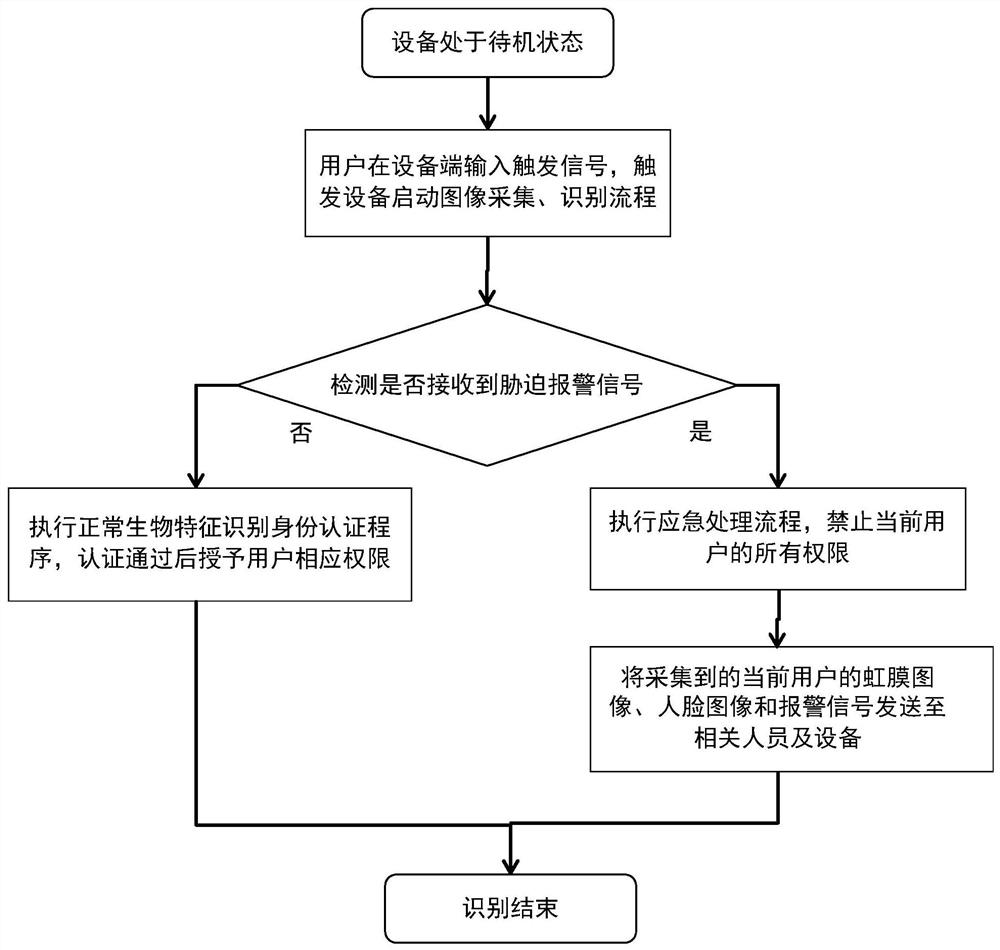
[0059] figure 2 It is a schematic flowchart of a security prevention and control method generally required by an embodiment of the present invention. Such as figure 2 As shown, the specific process of the method can be: when the device is in the standby state, the user inputs a trigger signal at the device end to enable the device to start the image acquisition and recognition process; the device end or the background server detects whether a duress alarm signal is received; When a threat alarm signal is received, the emergency treatment process is executed, that is, all permissions of the current user are prohibited; further, the collected iris image, face image and alarm signal of the current user are transmitted to relevant personnel or equipment for processing by relevant personnel; When no coercion alarm signal is detected, the normal biometric identity authentication procedure is executed, and the corresponding authority is granted to the user after the authentication...
Embodiment 2
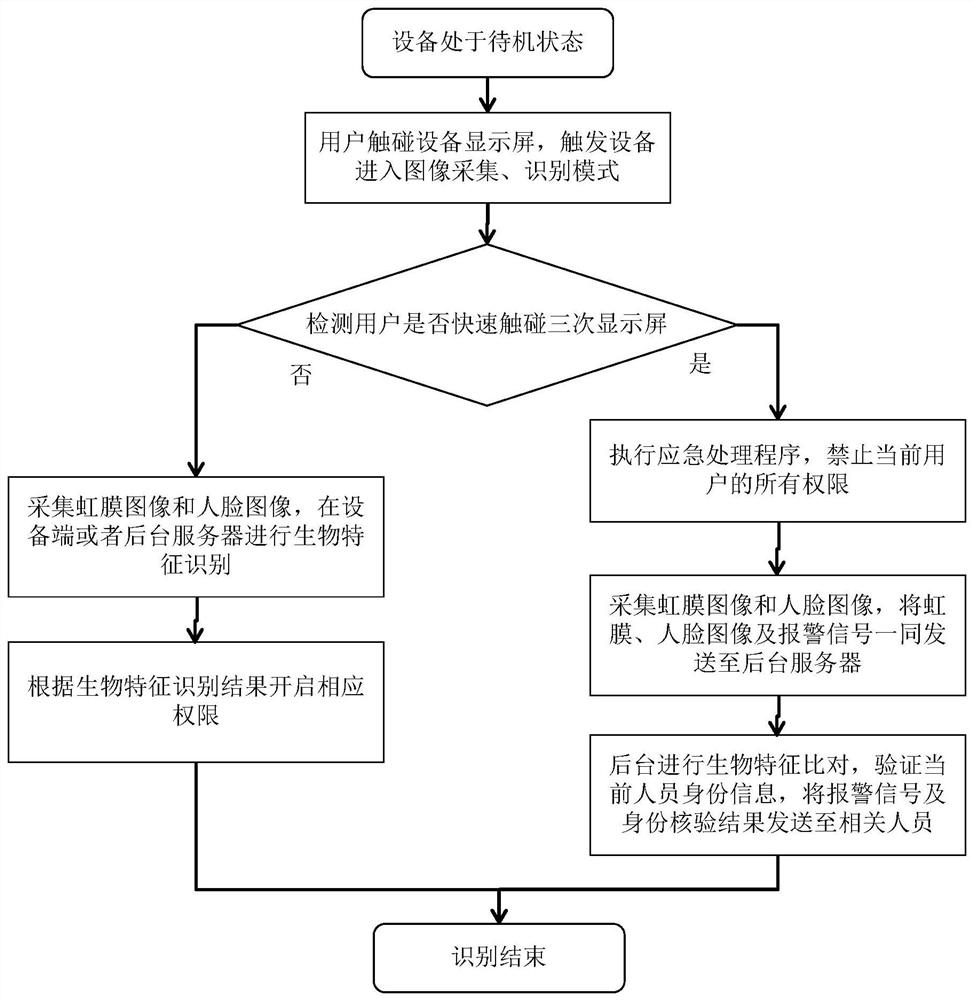
[0064] Figure 6 A schematic flowchart of a security prevention and control method with high security requirements according to an embodiment of the present invention. Such as Figure 6 As shown, the specific process of the method can be: when the device is in the standby state, the user inputs a trigger signal at the device end to enable the device to start the image acquisition and recognition process; the device end collects the current user's iris image and face image, and performs Compare and identify; when the identification result meets the conditions, enter the password input page; the user enters the duress password on this page. When the device determines that the user input is a duress password, it sends the iris image, face image and alarm signal to the background server; the background server performs biometric comparison, and then sends the alarm signal and identity verification results to the relevant responsible At the same time, in order to prevent the coerc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com