Malicious program identification method based on improved support vector machine
A technology of support vector machines and malicious programs, which is applied in the field of malicious program identification of support vector machines, and can solve problems such as high latency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further elaborated below through the accompanying drawings and specific steps.
[0031] The purpose of the present invention is to provide a kind of malicious program identification method based on the improved support vector machine for the malicious programs that exploit loopholes in the network traffic, effectively complete the identification of malicious programs, provide NTMI identification algorithm, and Sufficient experiments are carried out, which also prove the feasibility and effectiveness of the method.
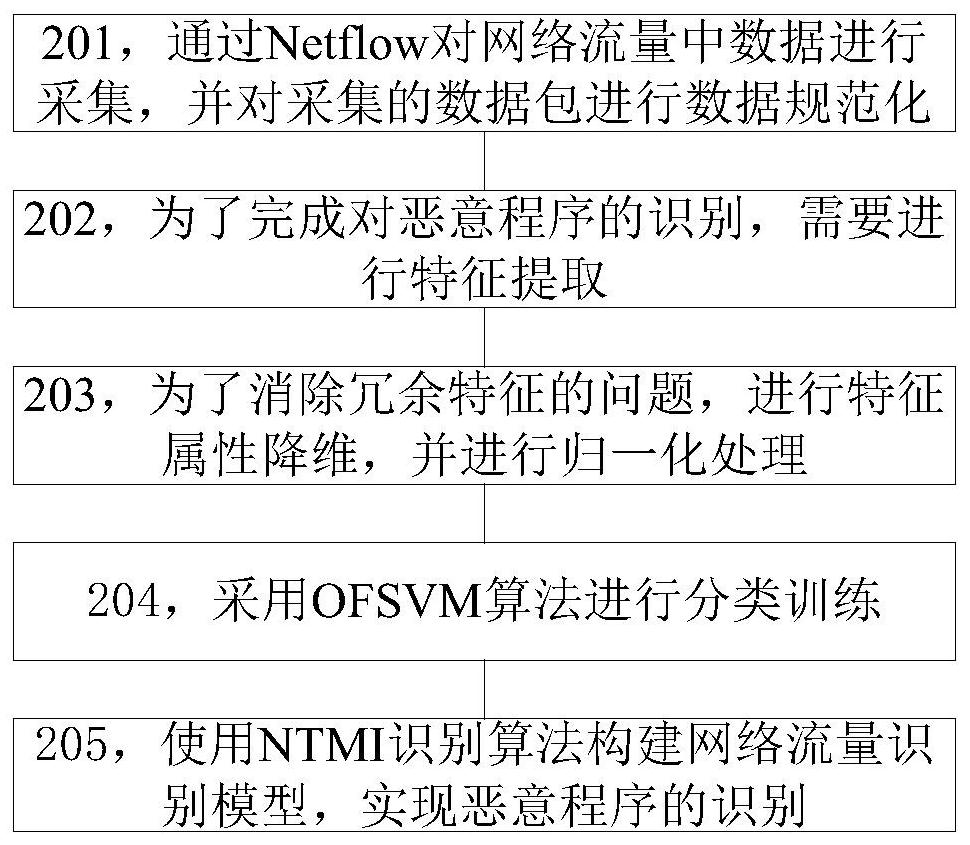
[0032] Such as figure 2 As shown, the malicious program identification method based on the improved support vector machine of the present invention includes:
[0033] Step 201 collects the data in the network flow by Netflow, and carries out data standardization to the collected data packets;
[0034] In step 202, in order to complete the identification of malicious programs, feature extraction is required;
[0035] In step 20...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com