Method for discovering intranet attacker based on windows login information
A technology for login information and attackers, applied in the field of network security, which can solve problems such as low efficiency, high labor cost, and large business volume.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] A method for discovering attackers in an intranet based on windows login information, in which each server is installed with a windows operating system in the internal network, select a server to be set as an agent server; install an agent client in each server within the protection range program.
[0037] Wherein, the Agent server maintains the login information whitelist list, and sends the login information whitelist list to the agent client program in each server within the protection range. The Agent server maintains the login information whitelist list, specifically stores the whitelist list, and modifies the whitelist list correspondingly if there is a modification. The agent server sends the login information whitelist to the agent client program in each server within the protection range, and the agent client program in the server obtains the login information corresponding to the server.
[0038] The agent client program of each server within the protection r...
Embodiment 2
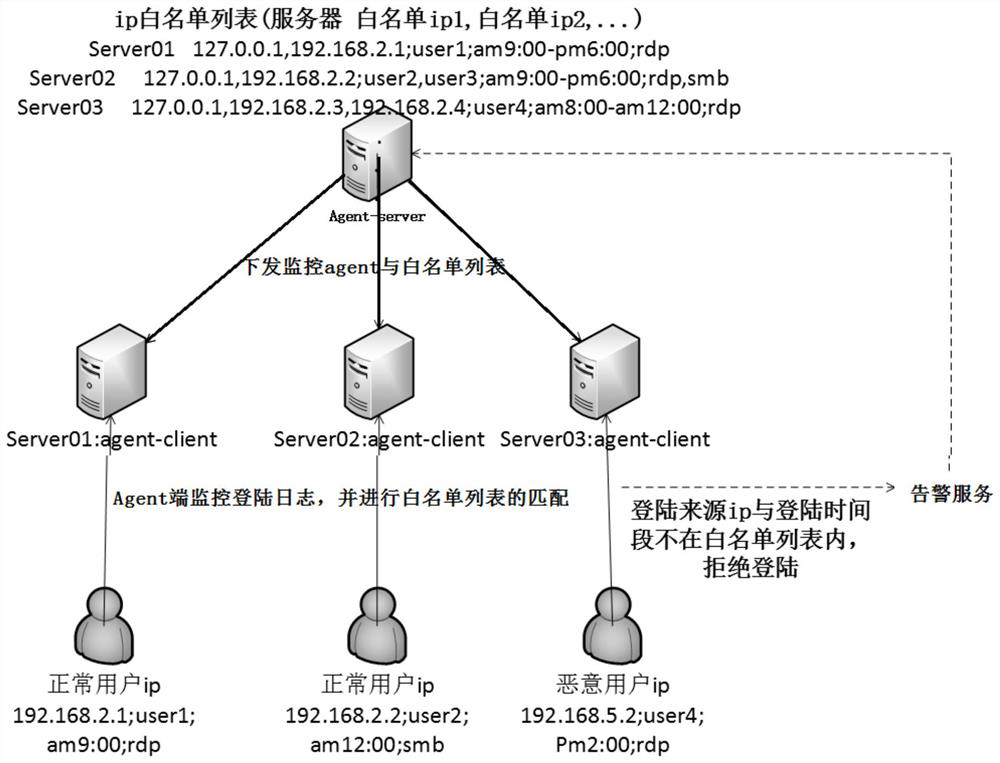
[0057] A method for discovering intranet attackers based on windows login information of the present invention is described in conjunction with specific examples, such as figure 1 As shown in , it is specifically described by taking one agent server and three servers within the protection range as an example.
[0058] In the internal network, the server Agent-server, server server01, server server02 and server server03 are all installed with windows operating system.
[0059] In the internal network, select the server Agent-server and set it as the agent server. The servers within the protection scope are server server01, server server02 and server server03, and lightweight agent client programs are installed in server server01, server server02 and server server03 respectively.
[0060] Agent server Agent-server is responsible for maintaining the white list of login information. The white list includes the IP addresses of server server01, server02 and server03, and the allowe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com