Domain name traffic feature extraction method, device and equipment and readable storage medium
A technology of traffic features and extraction methods, applied in the field of network security, can solve the problems of less intuitive high-level features, low recognition accuracy, and omissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
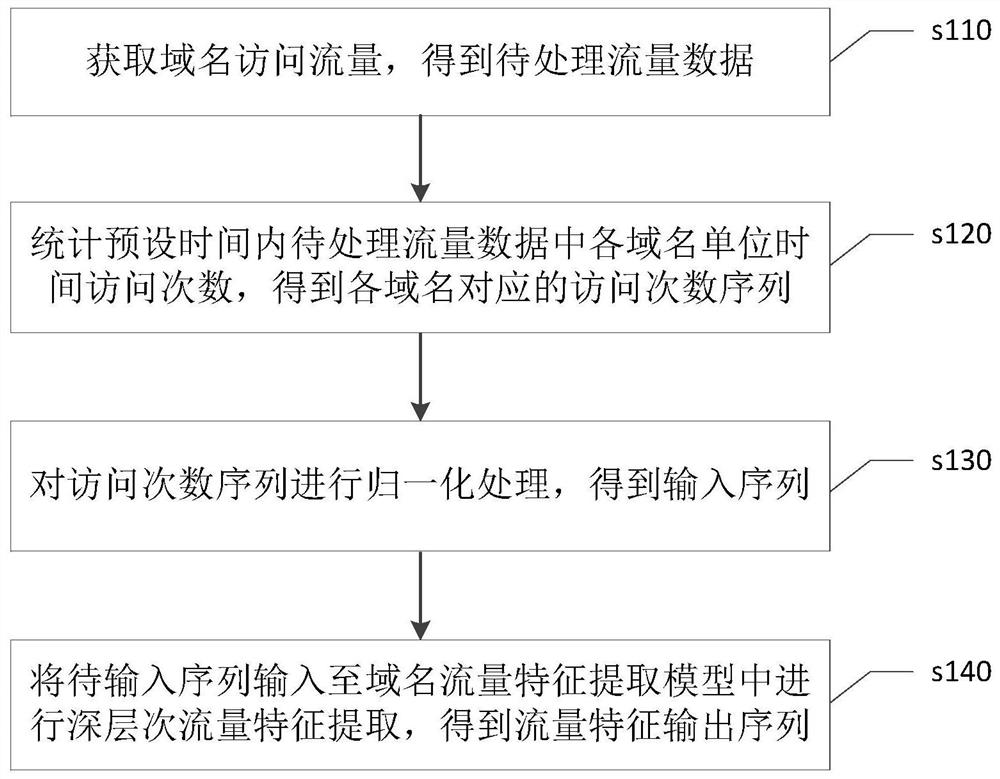
[0086] Please refer to figure 1 , figure 1 The flow chart of the email account breach detection method provided by this embodiment; the method may include:
[0087] Step s110: Obtain domain name access traffic, and obtain traffic data to be processed.
[0088] The access traffic of a domain name refers to the change of the number of visits of a domain name over time. For example, counting the number of visits of a domain name every hour, the change of the number of visits over time within a period of time (one day or one week) is the domain name. flow.
[0089] The following table 1 shows the access traffic of a domain name A within one day. In this embodiment, only the following domain name access traffic is taken as an example. The access traffic at other statistical intervals can refer to the introduction of this embodiment. Let me repeat.
[0090]
[0091] Table 1
[0092] In this embodiment, the application scenarios are not limited, and the feature vectors propos...
Embodiment 2
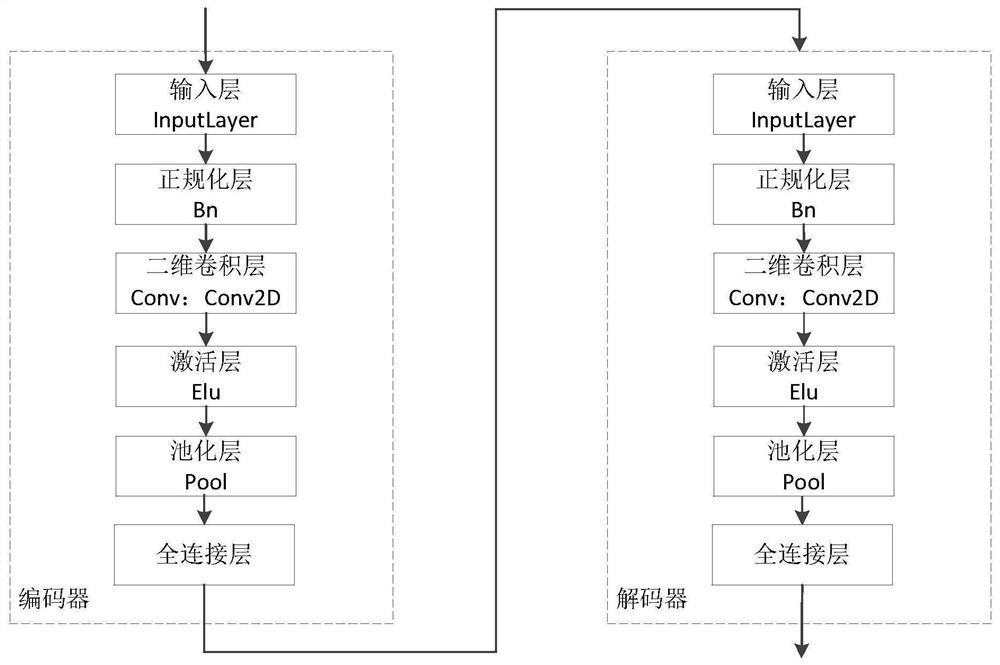
[0121] In the first embodiment, there is no limitation on the subsequent processing means after step s140, wherein, in order to accurately distinguish the domain name types and avoid the threat of illegal domain names to network security, preferably, after step s140, the flow characteristic output sequence can be further Perform feature cluster analysis to obtain domain name classification results, such as legal domain names and illegal domain names.
[0122] The traffic feature output sequence obtained in step s140 can be directly used as the traffic feature of the domain name for domain name analysis, for example, feature analysis of a single domain name, or combined analysis of multiple sequence-to-sequence model output features; it can also be combined with other pre-extracted The combination of domain name features, wherein, preferably, the statistical features of the traffic and the output sequence of the traffic features can be combined, and the obtained result can be us...
Embodiment 3
[0127] In order to deepen the understanding of the domain name traffic feature extraction method provided by the present invention, this embodiment takes the local area network traffic feature extraction as an example for introduction, and other implementation modes can refer to the introduction of this embodiment.
[0128] It mainly includes the following steps:
[0129] Step s201: Collect domain name access traffic and other relevant information.
[0130] The DNS traffic and HTTP traffic corresponding to multiple LANs can be aggregated in the cloud. The aggregated traffic may come from various applications in various industries. The larger the aggregated data volume, the more accurate the overall situation of the domain name being accessed. The information that needs to be recorded is which domain name was accessed by which host in the local area network at what time, what is the corresponding URL, what is the IP address resolved by the domain name, and what is the TTL value...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com