Secret communication method based on key fusion transformation
A communication method and key technology, applied in the field of secret communication technology, can solve the problems of concealment and unpredictability of eavesdropping behavior, difficulty in locating eavesdroppers, key exposure, waste of entropy resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to facilitate those skilled in the art to understand the technical content of the present invention, the content of the present invention will be further explained below in conjunction with the accompanying drawings.
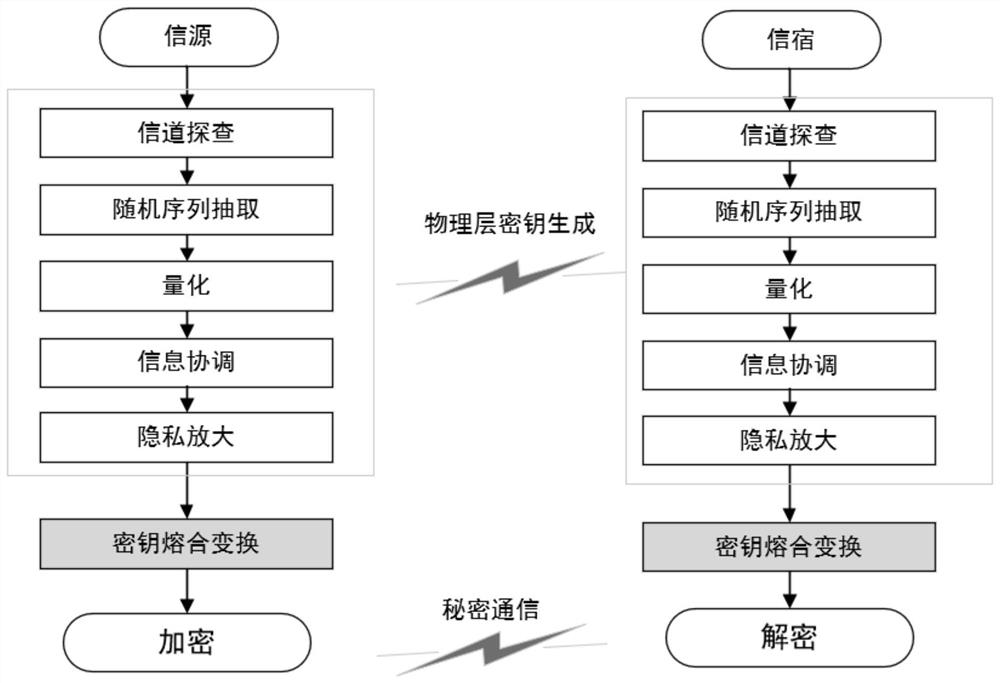
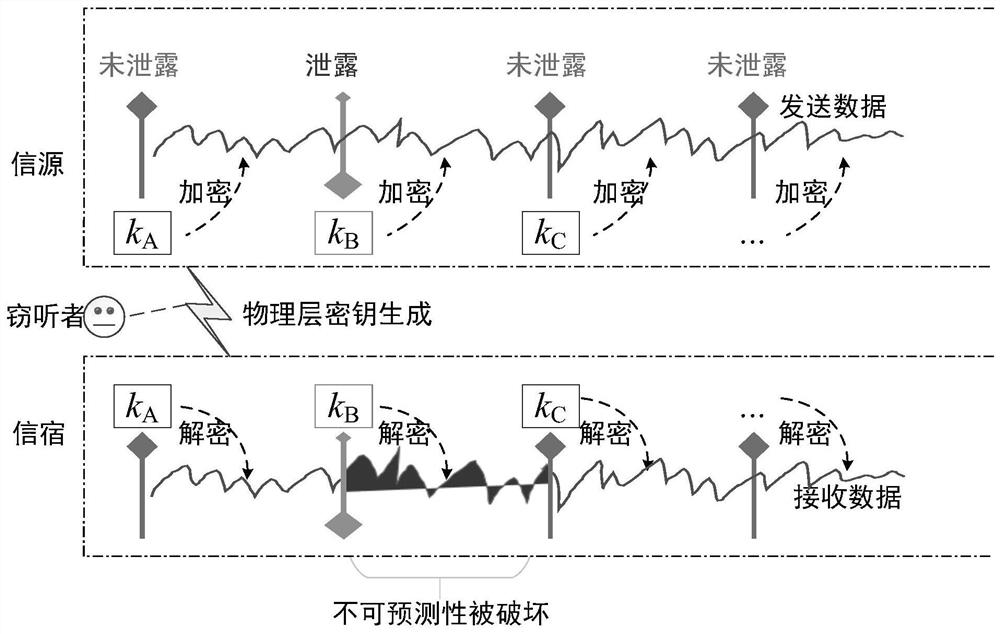
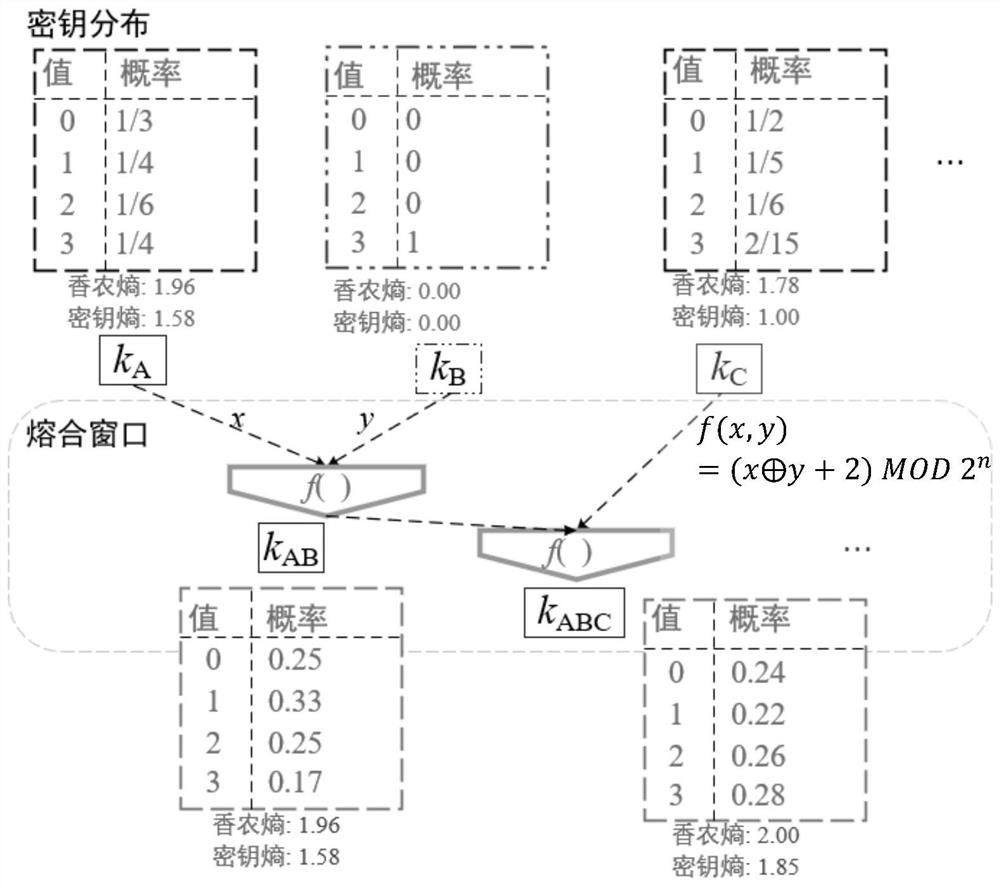
[0022] The secret communication method and data transmission system based on key fusion transformation proposed by the present invention include: a source, a channel, and a sink. The source and the sink generate a series of shared keys based on one or more key generation mechanisms. sequence; the source uses the fusion transformation to process the key sequence, and then uses the output result as a temporary key to encrypt and encode the message, and sends the ciphertext to the sink; the sink also uses the result of the fusion transformation as a temporary key to encrypt the message Decode to get plaintext. Since the key fusion transformation protects the randomness of a single key, the probability of secrecy interruption can be significantly red...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com