Internet of Things identity authentication method and device and electric power Internet of Things identity authentication system
A technology of identity authentication and the Internet of Things, applied in user identity/authority verification, transmission systems, digital transmission systems, etc., can solve the problems of complex interconnection and interoperability of online identity verification, to ensure safe and efficient operation, ensure authenticity, and reduce complexity degree of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
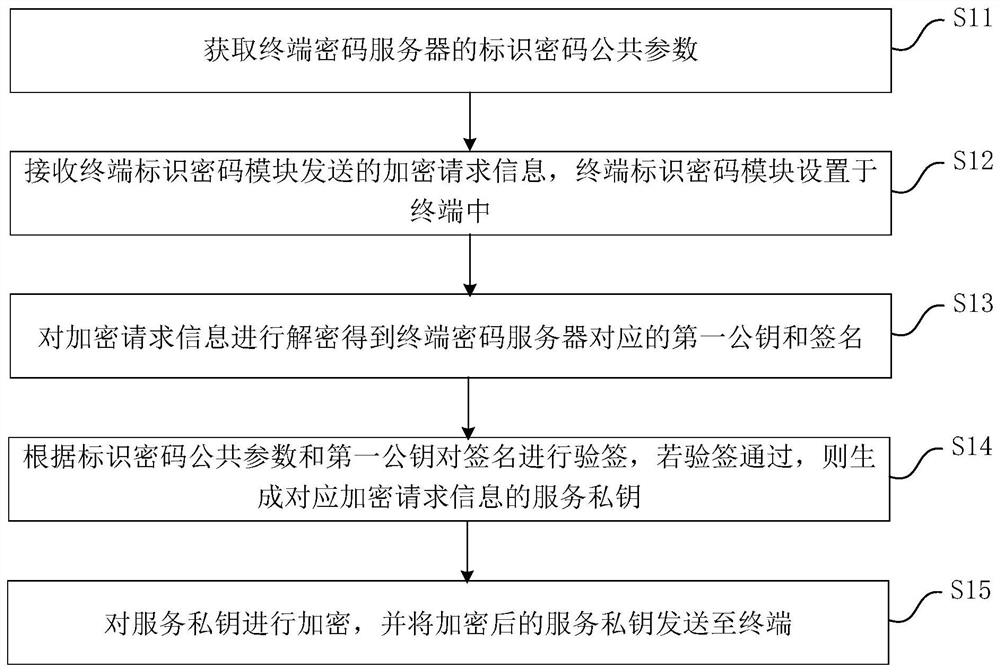
[0036] This embodiment provides an identity authentication method for the Internet of Things, which is applied to the service provider's password server in the power Internet of Things system to realize the interconnection between the service provider's password server and the Internet of Things terminal, such as figure 1 As shown, the IoT identity authentication method includes the following steps:
[0037] S11. Obtain public parameters of the identification password of the terminal password server.
[0038] Exemplarily, the terminal password server is a password server of an electric power Internet of Things terminal manufacturer. The identification password public parameter is a system parameter of the terminal password server, which can be generated according to the system parameter generation algorithm steup. The terminal password server can provide the identity TPID and the corresponding factory private key TO-RK for the electric power IoT terminal TPID .
[0039] S12...
Embodiment 2
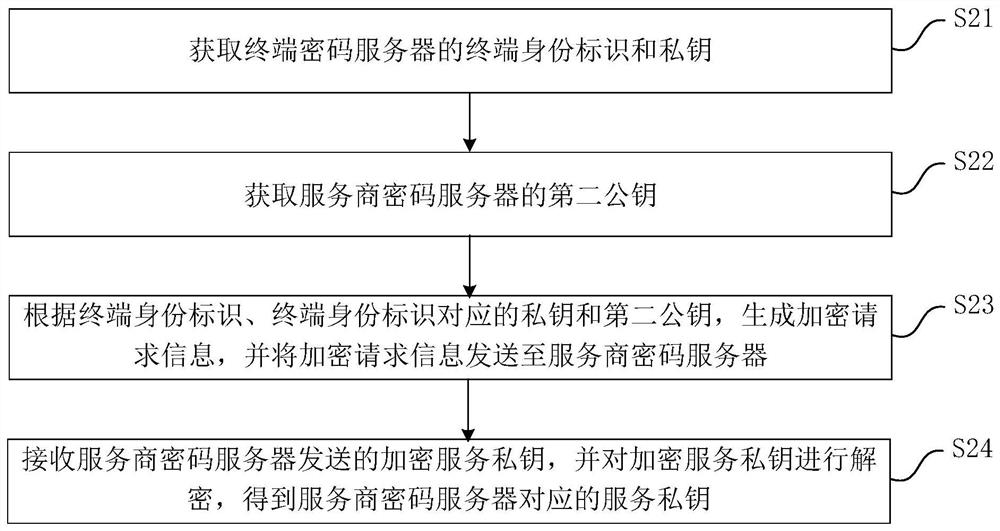
[0058] This embodiment provides an identity authentication method for the Internet of Things, which is applied to the Internet of Things terminal in the power Internet of Things system to realize the interconnection between the service provider's password server and the Internet of Things terminal, such as figure 2 As shown, the IoT identity authentication method includes the following steps:
[0059] S21. Obtain the terminal identity and private key of the terminal password server.
[0060] Exemplarily, the terminal password server is a password server of an electric power Internet of Things terminal manufacturer. The terminal identity is the identity TPID provided by the terminal password server for the electric power Internet of Things terminal. The private key is the factory private key TO-RK built into the power Internet of Things terminal by the terminal password server TPID . Wherein, the terminal identity is the first public key of the electric power Internet of Th...
Embodiment 3
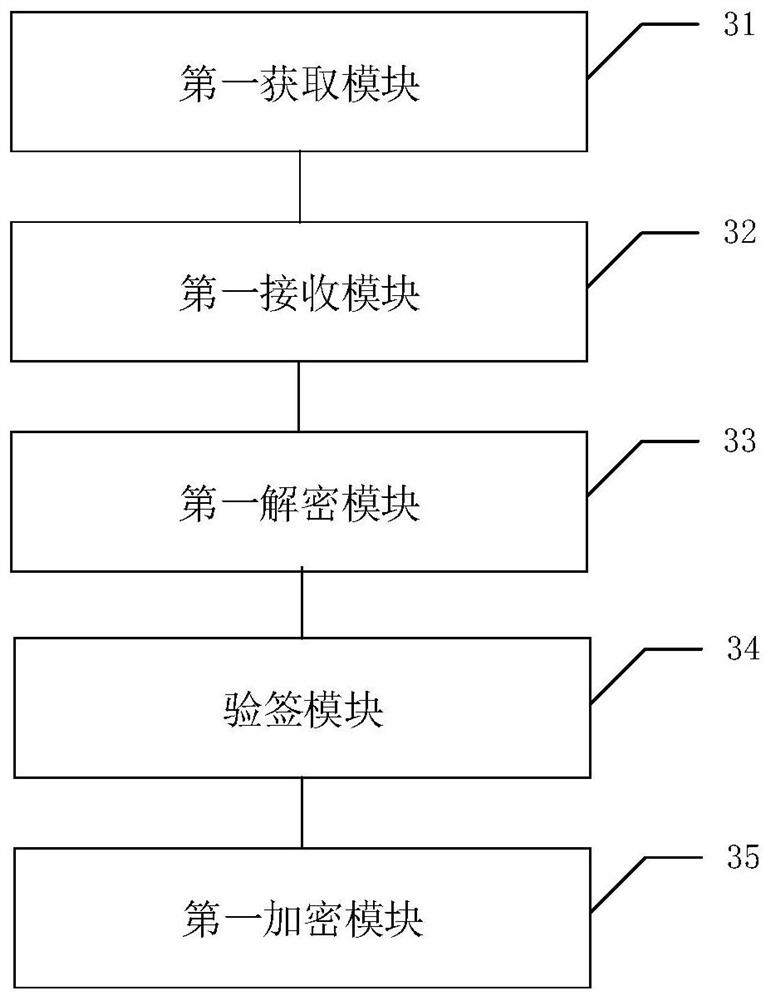
[0077] This embodiment provides an identity authentication device for the Internet of Things, which is applied to the service provider's password server in the electric power Internet of Things system, so as to realize the interconnection between the service provider's password server and the Internet of Things terminal, such as image 3 As shown, the IoT identity authentication device includes:
[0078] The first acquiring module 31 is configured to acquire the identification password public parameter of the terminal password server. For details, refer to the relevant description of step S11 corresponding to the above method embodiment, and details are not repeated here.
[0079] The first receiving module 32 is configured to receive the encryption request information sent by the terminal identification and encryption module, and the terminal identification and encryption module is set in the terminal. For details, refer to the relevant description of step S12 corresponding ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com