Shield proximity existing tunnel safety evaluation method based on data mining and data fusion
A technology with existing tunnels and safety evaluation, applied in data processing applications, instruments, computing, etc., can solve problems such as less safety evaluation and early warning, and safety hazards not being identified and separated.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
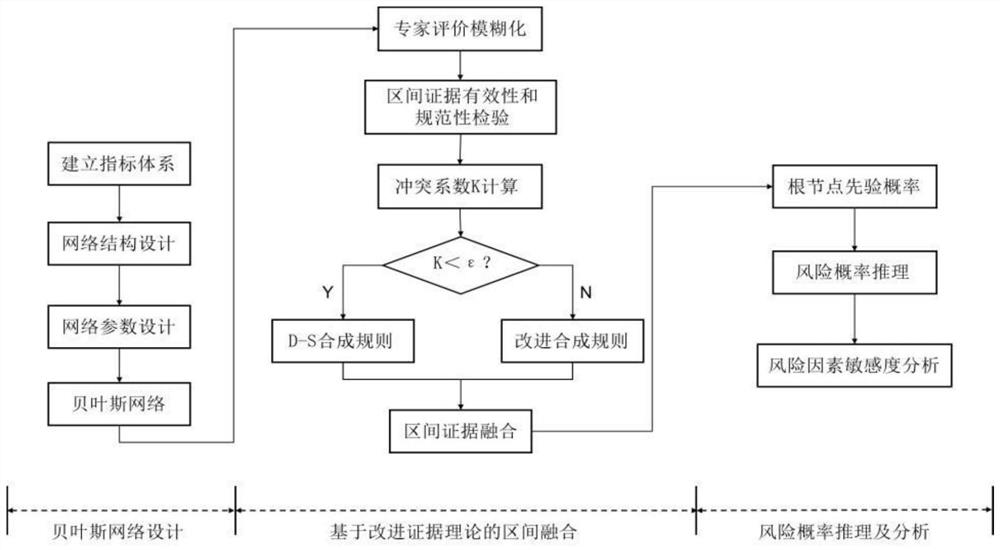
[0131] Such as figure 1 As shown, the present invention proposes a method based on fuzzy Bayesian and evidence theory based on data mining and data fusion shield approaching the existing tunnel safety evaluation method, which mainly includes the following steps:
[0132] 1. Bayesian network construction
[0133] (1) Node state division
[0134] Combined with the grade division of the security risk of the existing tunnel passing under the shield, each node in the Bayesian network is divided into five states of 1, 2, 3, 4, and 5, so that it can be compared with the security risk level status ( Ⅰ), Safer (II), General (Ⅲ), More Dangerous (IV), Dangerous (Ⅴ) for one-to-one correspondence to facilitate safety risk assessment and analysis.
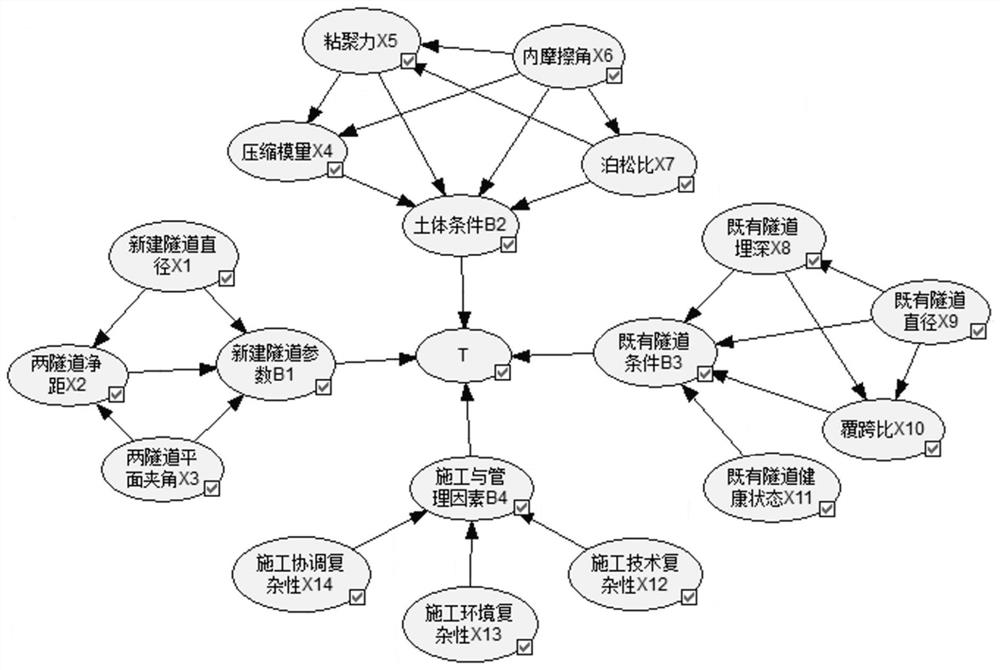
[0135] (2) Bayesian network design
[0136] According to the constructed evaluation index system, combined with the ideas and specific practices of Bayesian network design, and integrated prior knowledge such as fault tree and expert experien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com