Antagonistic attack and defense method and system based on PID controller
A defense system and adversarial technology, which is applied in the directions of instruments, machine learning, character and pattern recognition, etc., can solve the problems of decreased attack success rate, limited attack success rate, and limited transferability of confrontation samples, achieving high attack success rate, Improve the effect of robustness and strong migration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
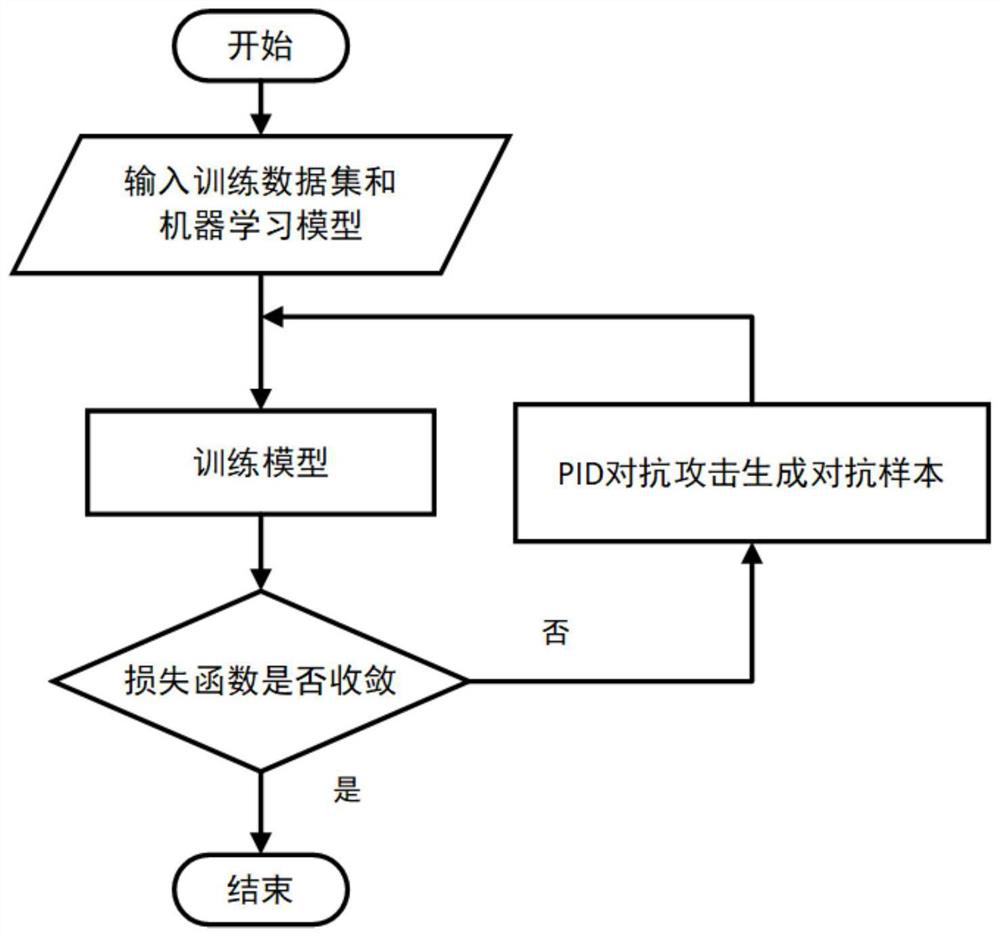
[0035] Such as figure 1 As shown, the present embodiment is based on the P (proportional), I (integral) and D (differential) controllers for adversarial attack and defensive attack, mainly related to the following technologies: 1) PID controller-based adversarial attack method: through the loss function The gradient relative to the input data is divided into current and past gradient information, corresponding to the P controller and I controller in the PID controller, and the D controller is calculated using the current and past gradient difference; 2) based on The defense method of the PID controller: using the adversarial samples generated by the adversarial attack method based on the PID controller to conduct adversarial training on the machine learning model becomes a defense method to improve the robustness of the model.
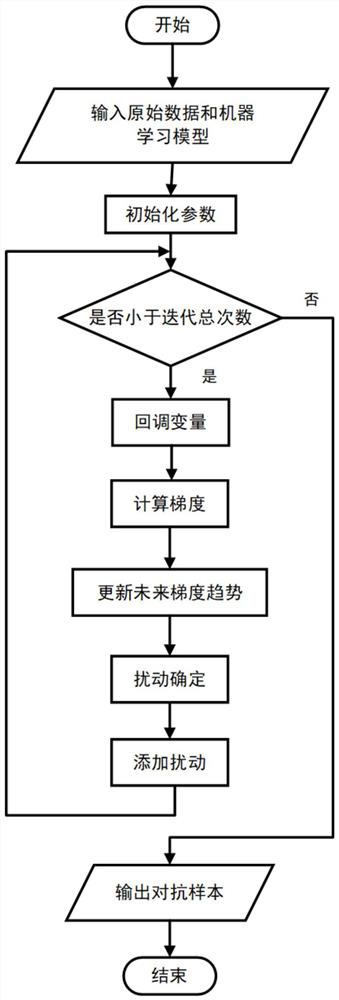
[0036] Such as figure 2 As shown, the present embodiment is based on the adversarial attack and defense method of the PID controller, and the specif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com