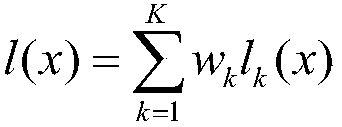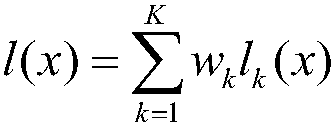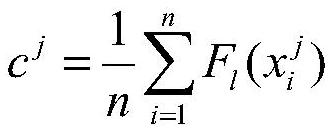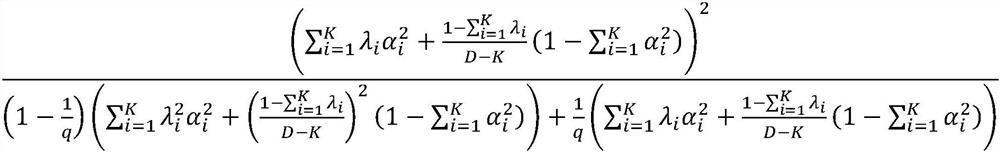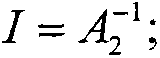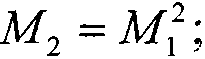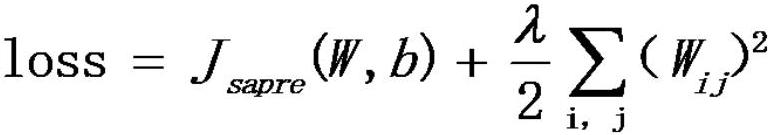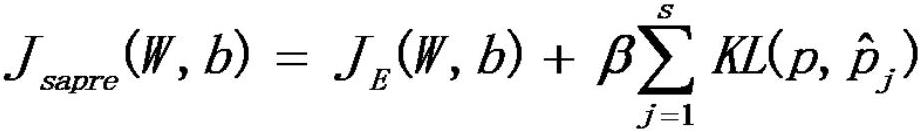Patents
Literature
39results about How to "Improve attack success rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
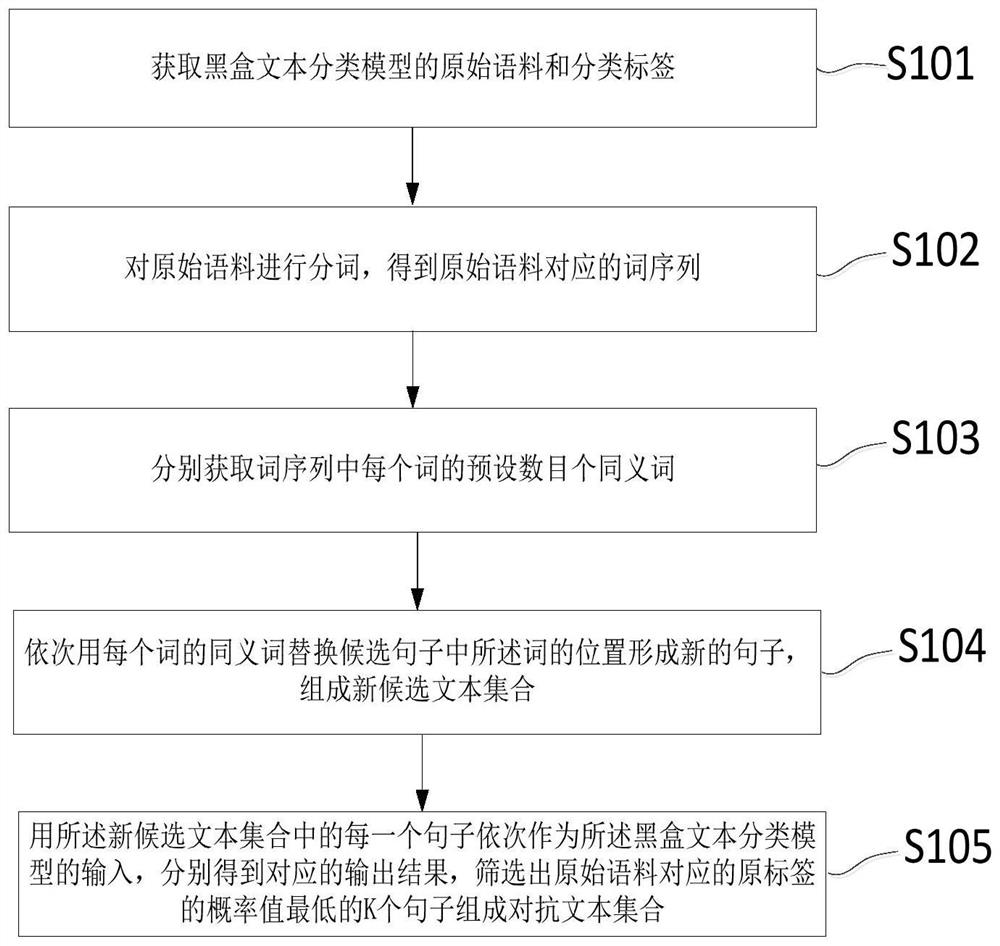
Method for generating adversarial image
InactiveCN108257116AImprove robustnessImprove accuracyImage enhancementImage analysisMomentumAlgorithm
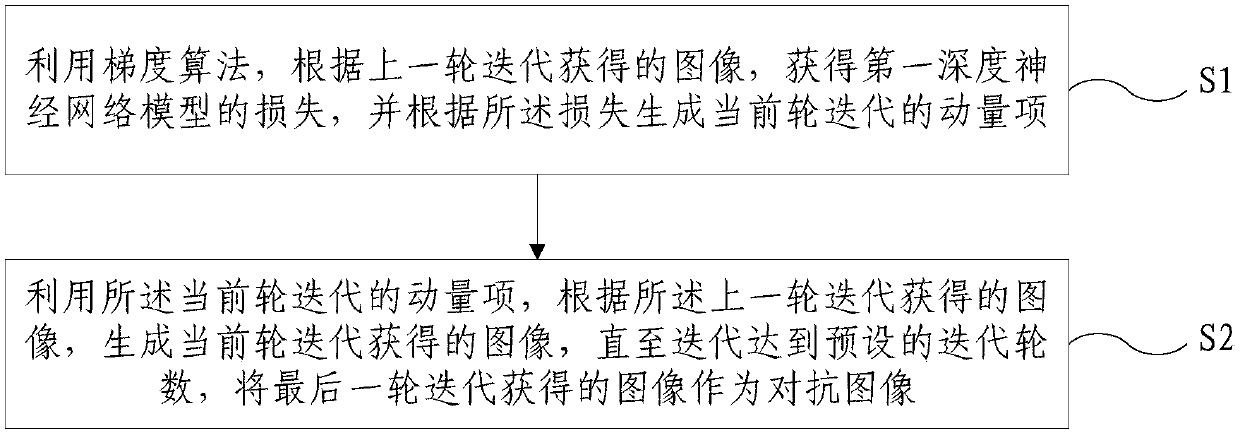
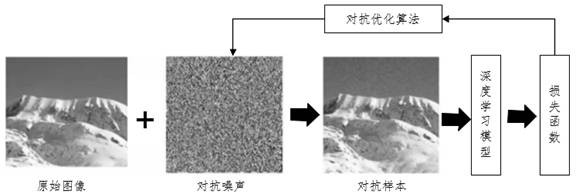
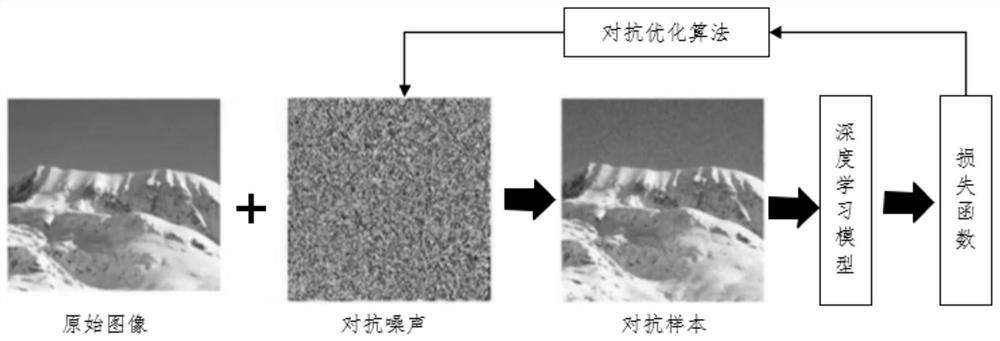
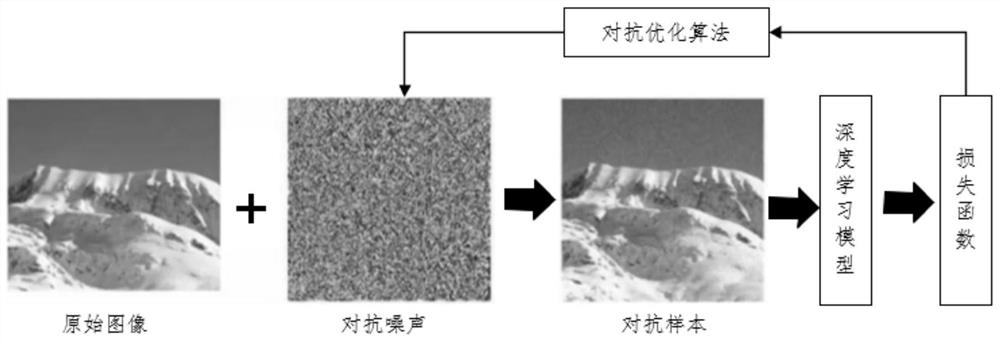
The invention provides a method for generating an adversarial image. The method comprises: on the basis of a gradient algorithm, a loss value of a first deep neural network model is obtained accordingto an image obtained by last-turn iteration, and a momentum of current-turn iteration is generated based on the loss value; and on the basis of the momentum of current-turn iteration, an image obtained by current-turn iteration is generated based on the image obtained by the last-turn iteration until iteration reaches a preset iteration turn number, and the image obtained by the last-turn iteration is used as an adversarial image. According to the method provided by the invention, iteration of an original image is carried out by using the momentum and the adversarial image being capable of attach the deep neural network model is obtained, so that coupling between a white-box attack success rate and a migration performance is reduced effectively. The high attack success rates of the whitebox model and the black box model are realized. The method can be used for adversarial training, thereby improving the correction rate of image classification by using the deep neural network model and also can be used for attacking the deep neural network model.
Owner:TSINGHUA UNIV
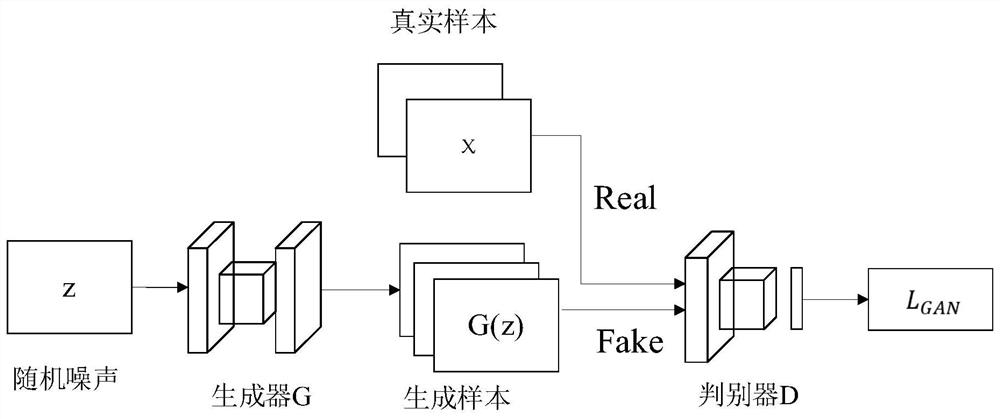
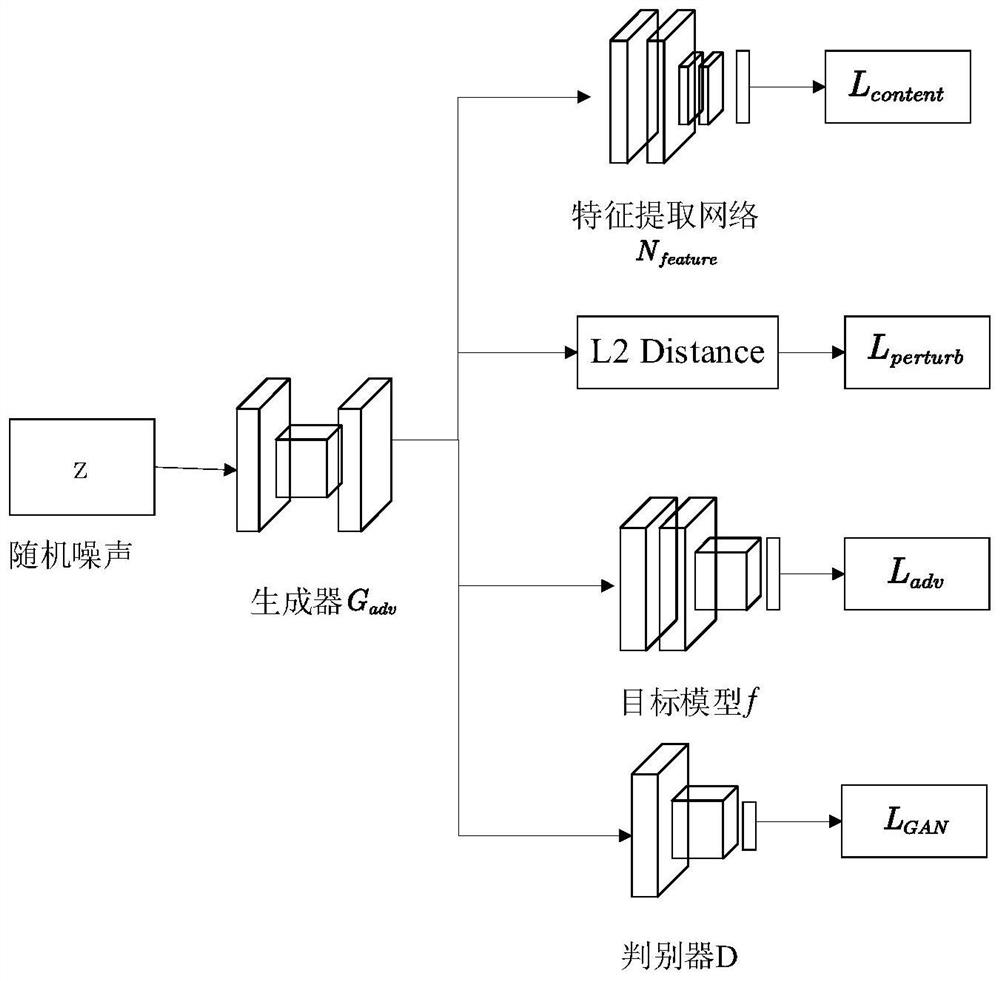
Adversarial sample generation method based on content-aware GAN
ActiveCN111881935AHigh speedImprove attack success rateInternal combustion piston enginesCharacter and pattern recognitionFeature extractionAlgorithm
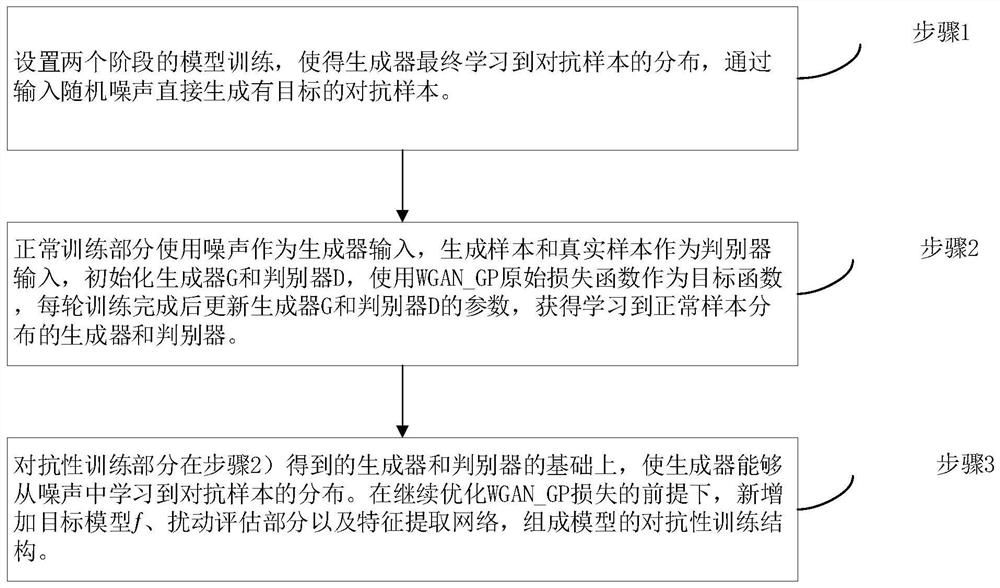
The invention discloses an adversarial sample generation method based on content awareness GAN, which changes a training process on the basis of WGAN_GP, directly generates an adversarial sample witha target by inputting random noise, adds a content feature extraction part, restrains the quality of the generated sample under the condition of not influencing an attack effect, and improves the accuracy of adversarial sample generation. Content characteristics of adversarial samples can be kept unchanged as much as possible. The system comprises a generator G, a discriminator D, a target model f, a disturbance evaluation part and a feature extraction network, wherein the generator is responsible for generating a sample from random noise, the generator is trained according to a loss functionof the discriminator D, the target model f, the disturbance evaluation part and the feature extraction network, and the generator directly generates an unlimited adversarial sample from the noise. Onthe basis of the generative adversarial network, the semantic information of the concerned sample and a mode of directly generating the adversarial sample instead of a superimposed disturbance mode, direct generation of the adversarial sample of the specified target is realized by using unsupervised GAN training, the sample generation speed is increased, and the quality of the generated sample isimproved; the change of the adversarial sample in the content feature region is reduced while the high attack success rate is maintained.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
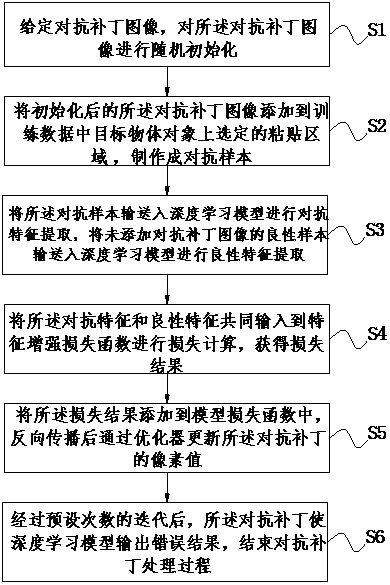
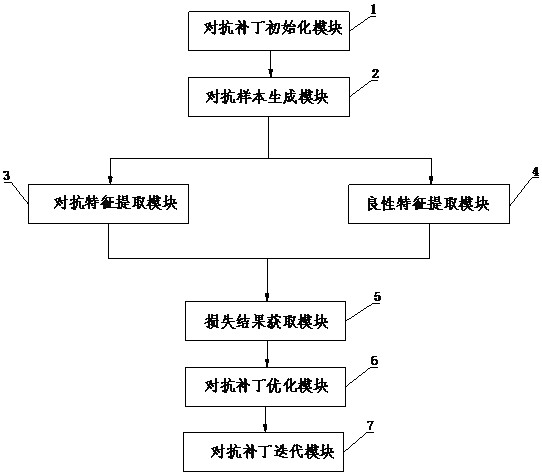
Small adversarial patch generation method and device
ActiveCN112241790ASmall sizeReduced legibilityCharacter and pattern recognitionNeural architecturesFeature extractionEngineering
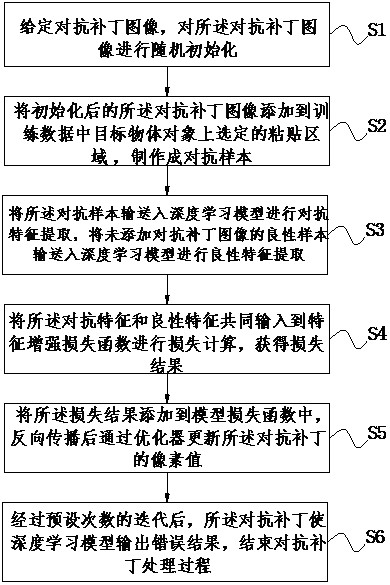
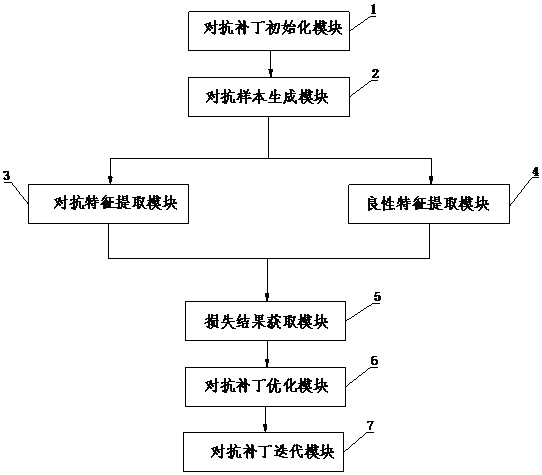
The invention discloses a small adversarial patch generation method and device, and the method comprises the steps: carrying out the random initialization of an adversarial patch image, adding the initialized adversarial patch image to a selected pasting region on a target object in training data, and manufacturing an adversarial sample; transmitting the adversarial samples into a deep learning model for adversarial feature extraction, and transmitting benign samples without adversarial patch images into the deep learning model for benign feature extraction; jointly inputting the adversarial features and the benign features into a feature enhancement loss function for loss calculation to obtain a loss result; adding a loss result into a model loss function, and updating a pixel value of the adversarial patch through an optimizer after back propagation; and after preset times of iteration, enabling the adversarial patch to enable the deep learning model to output an error result, and ending the adversarial patch processing process. According to the method, the size of the anti-patch in the physical world can be smaller, the manufacturing cost is reduced, the identifiability of the anti-patch is reduced, and a defense method based on detection is broken through more easily.
Owner:BEIJING REALAI TECH CO LTD
Adversarial sample generation method and device, electronic equipment and storage medium
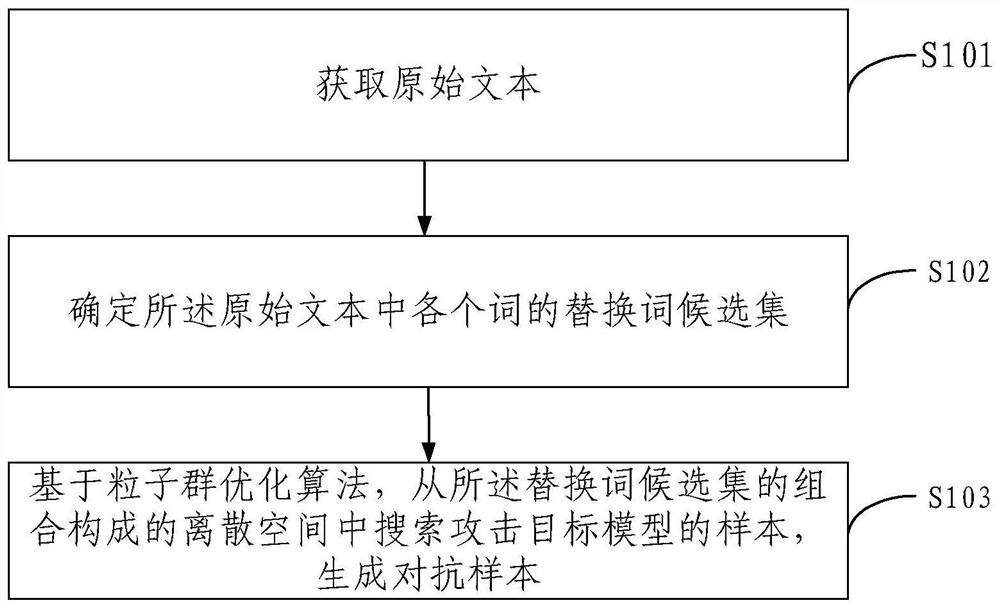
ActiveCN111652267AImprove search speedImprove attack success rateCharacter and pattern recognitionNatural language data processingTheoretical computer scienceEvolutionary computation
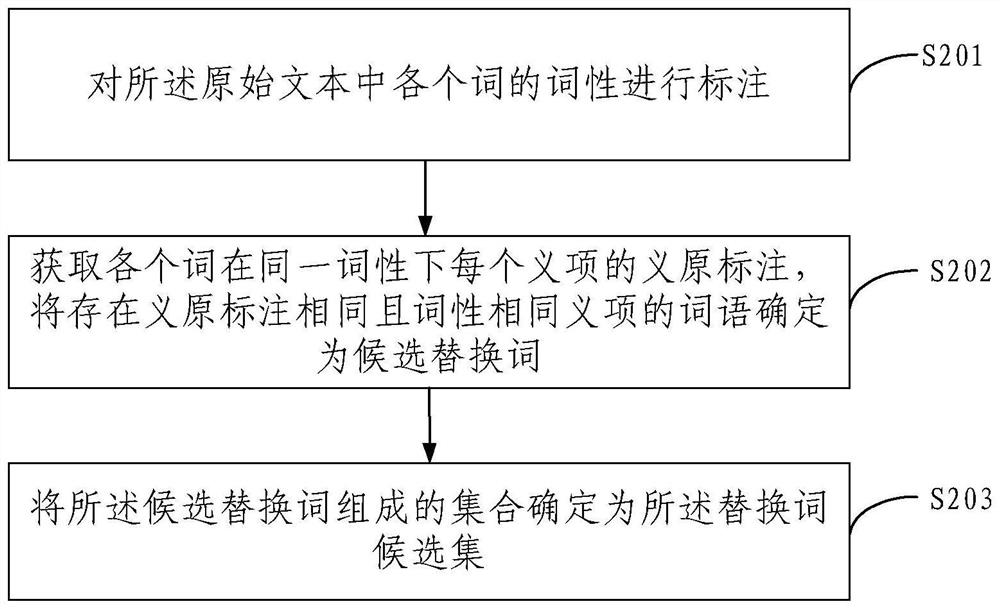
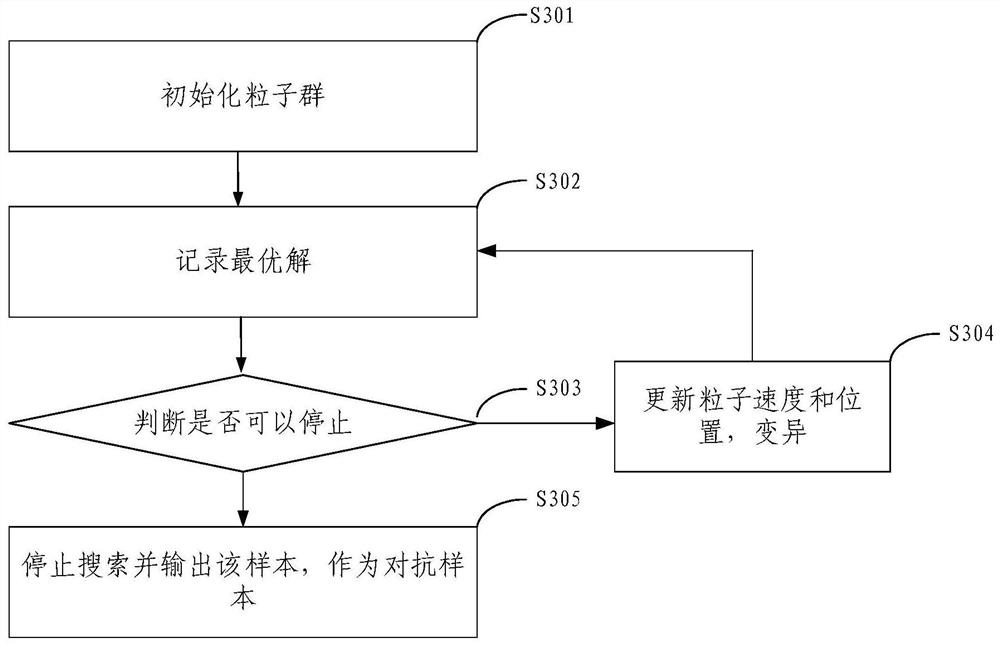
Embodiments of the invention provide an adversarial sample generation method and device, electronic equipment and a storage medium. The method comprises the steps of obtaining an original text; determining a replacement word candidate set of each word in the original text; and based on a particle swarm optimization algorithm, searching a sample of the attack target model from a discrete space formed by the combination of the replacement word candidate sets, and generating an adversarial sample. According to the embodiment of the invention, the particle swarm optimization algorithm is used forsearching the adversarial sample, and the particle swarm optimization is more efficient than the genetic algorithm as a meta-heuristic group evolution calculation method, so that the search speed canbe increased when the algorithm is used for searching the adversarial sample, and the attack success rate can also be increased. For different natural language processing models, the embodiment of theinvention can quickly and efficiently generate a large number of high-quality confrontation samples, successfully cheat the target model and further expose the vulnerability of the target model, andhas good practicability.
Owner:TSINGHUA UNIV
Migratable adversarial sample attack method based on attention mechanism
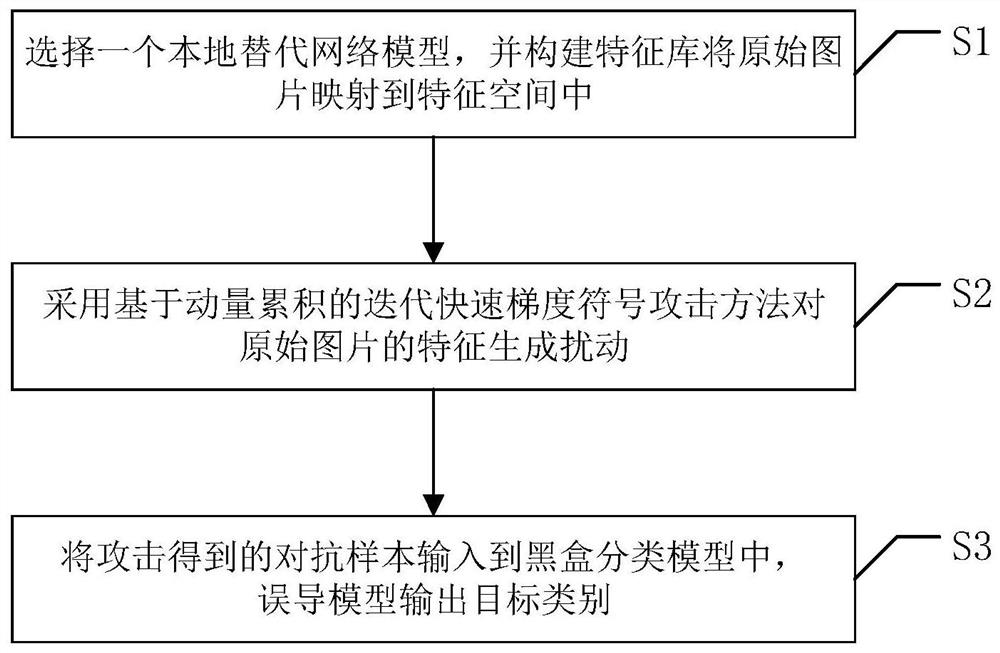
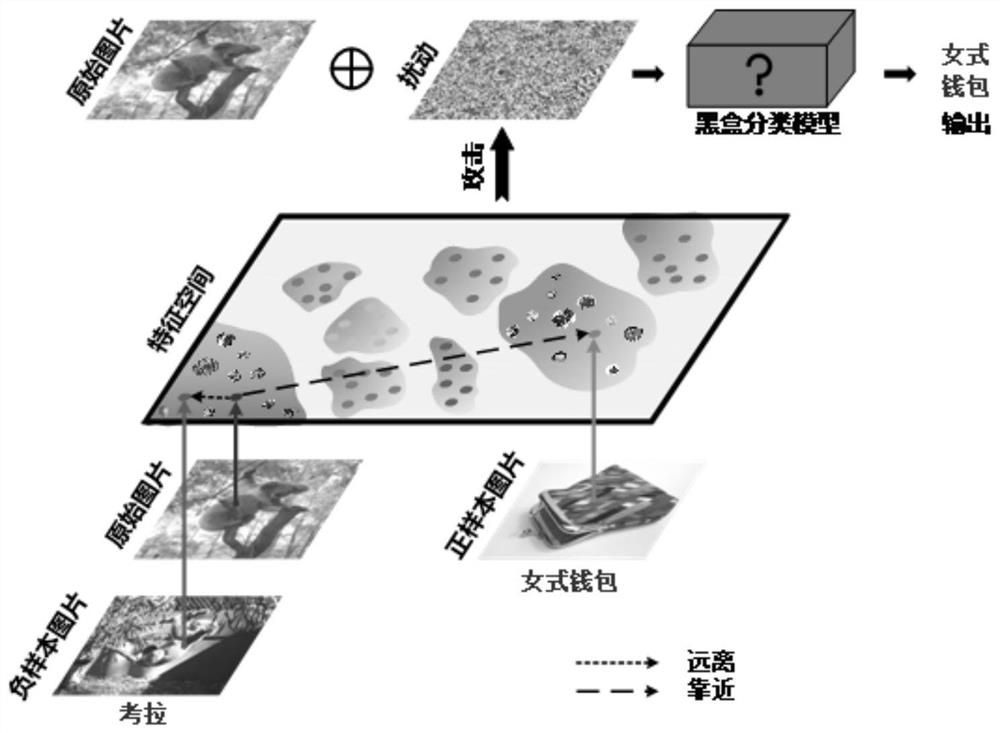
PendingCN111898645AImprove target attack success rateBalance target attack success rateCharacter and pattern recognitionNeural architecturesNetwork modelCharacteristic space
The invention discloses a migratable adversarial sample attack method based on an attention mechanism, and the method comprises the steps of selecting a local replacement network model, constructing afeature library, and enabling an original image to be mapped into a feature space; adopting an iterative fast gradient symbol attack method based on momentum accumulation to enable the characteristics of the original picture to be far away from the original category area and to be close to the target category area; and inputting an adversarial sample obtained by attacks into a black box classification model, and outputting a target category by a misleading model. According to the invention, a triple loss function is used to destroy an area which is rich in information and is mainly concernedby the model in an attacked model characteristic space; the problems of low white-box target attack success rate and low black-box target mobility of an existing attack method in a classification taskof a complex data set are solved, and misleading of a classification model is effectively realized under the condition of considering a white-box scene and a black-box scene.
Owner:GUIZHOU UNIV +1
Black box adversarial sample attack method for electric energy quality signal neural network classification model
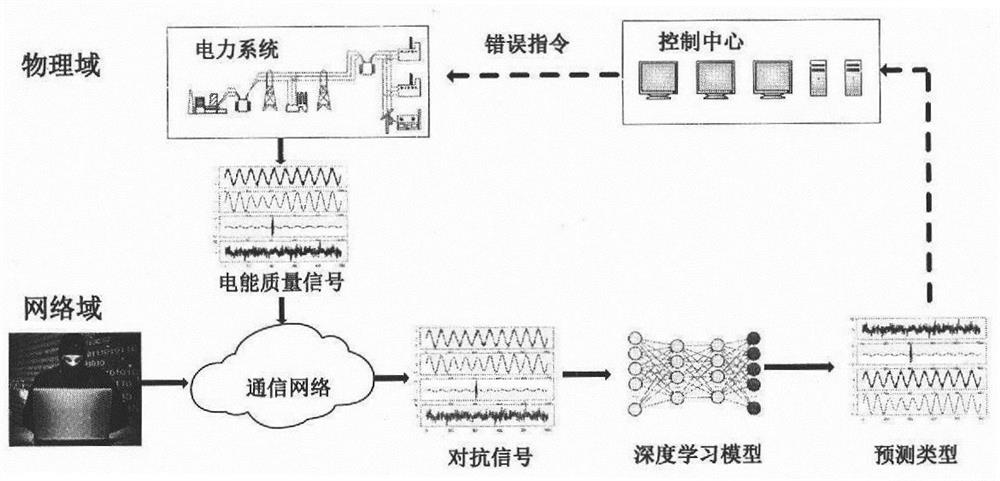
PendingCN112149609AImplement misclassificationIncrease success rateCharacter and pattern recognitionNeural architecturesEngineeringData mining
The invention relates to a black box adversarial sample attack method for a power quality signal neural network classification model, which is characterized by specifically comprising the following steps: a target model and a local substitution model of an attacker are subjected to training; the attacker generates general disturbance for the local training model; and the attacker attacks the target model by using the generated general disturbance. According to the method, the vulnerability of the neural network and the mobility of the adversarial sample are effectively utilized, the actual situation of attacks is met, and the attack success rate is high.
Owner:AIR FORCE UNIV PLA
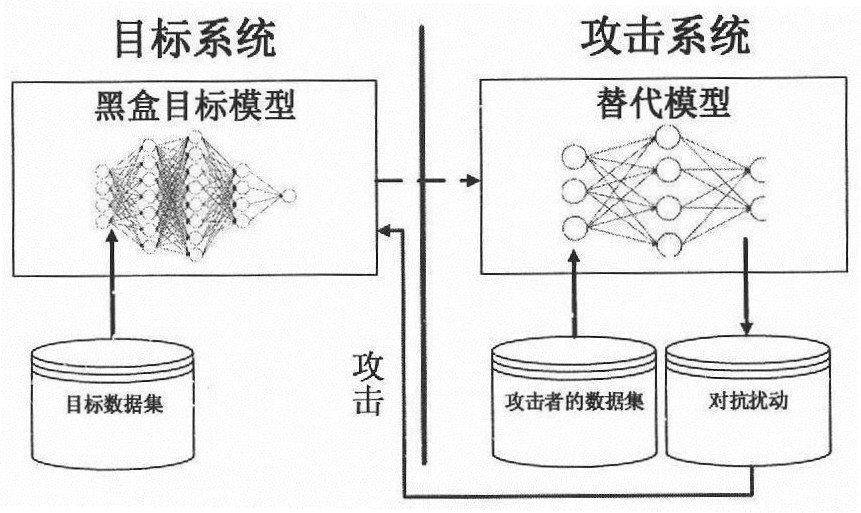
Method and system for testing robustness of artificial intelligence model
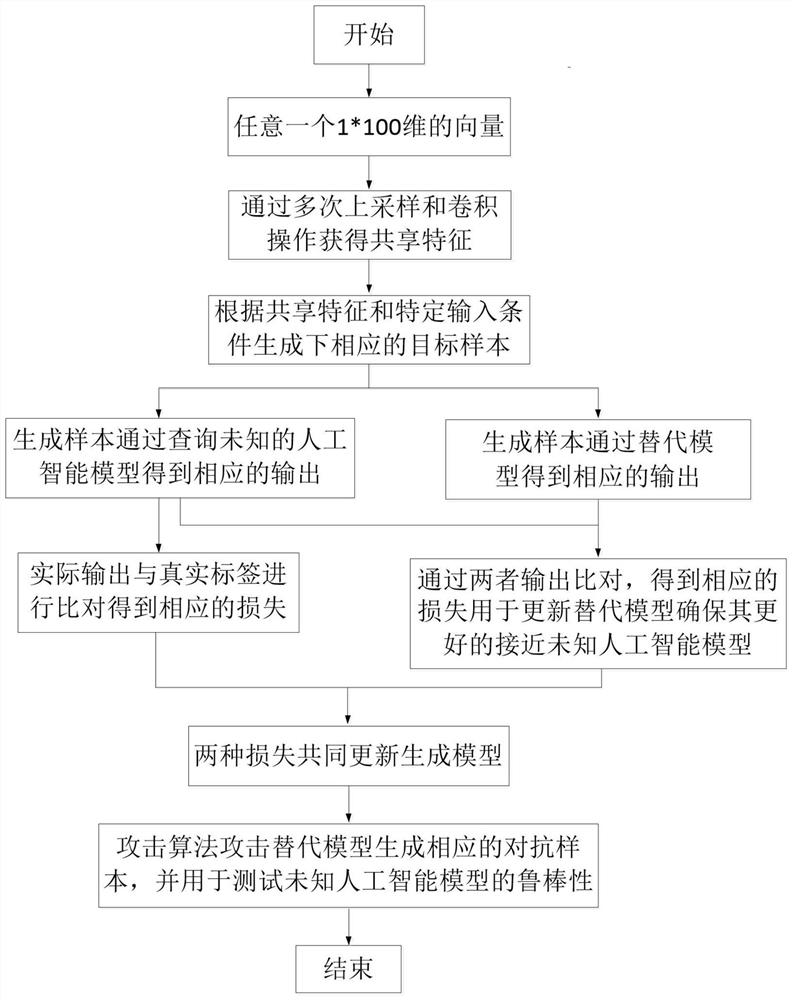
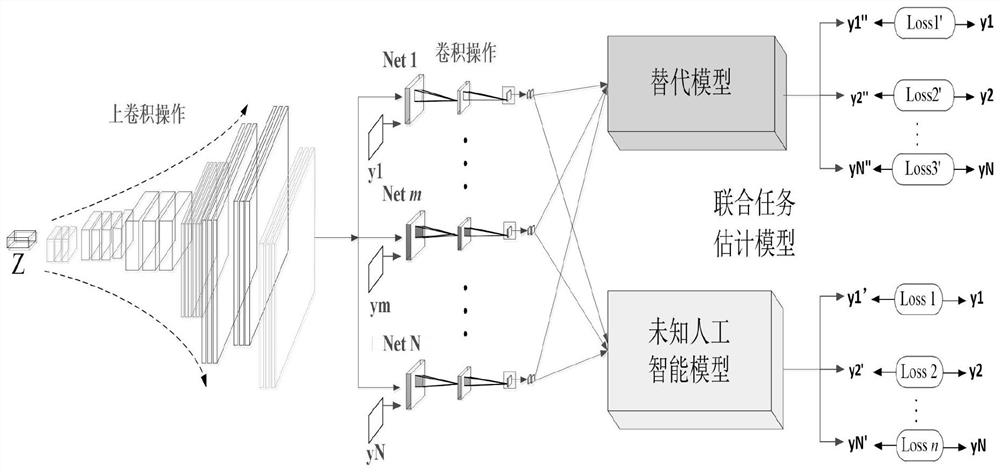
PendingCN112766315ASimple designEasy to implementCharacter and pattern recognitionNeural architecturesData setAlgorithm
The invention belongs to the technical field of artificial intelligence model robustness judgment, and discloses a method for effectively attacking an unknown model under the condition of not knowing an artificial intelligence model and a training data set. The method comprises the following steps: capturing shallow shared features of an original data set, and generating a corresponding target sample according to an input condition, wherein the artificial intelligence model to be tested is used for predicting the output of the target sample, and the output is compared with the formal label to obtain the corresponding loss, and the generated target sample is used for training the substitution model and obtaining corresponding output; comparing the output of the same sample under the condition of two different models to obtain comparison loss so as to ensure that the substitution model well learns all functions of the artificial intelligence model to be tested; employing some mature attack algorithms for attacking the substitution model to obtain corresponding adversarial samples, and employing the adversarial samples for attacking an unknown artificial intelligence model so as to judge the robustness of the artificial intelligence model.
Owner:HUNAN UNIV
Chosen plaintext side channel energy analysis method for ECC algorithm of P domain
ActiveCN103441846AEfficient analysisEasy to analyzeKey distribution for secure communicationUser identity/authority verificationPlaintextEnergy expenditure
The invention provides a chosen plaintext side channel energy analysis method for an ECC algorithm of a P domain, and relates to the filed of cryptographic algorithm implementation, side channel energy analysis and the like. To carry out side channel energy analysis on implementation of non-defense methods and defense methods of the ECC algorithm, the novel side channel energy analysis method of an elliptic curve on a prime field on the basis of chosen plaintext is provided, so that an energy consumption difference of multiply operation of a scalar in the ECC algorithm is produced, and secret key information is obtained. According to the technical scheme, the method includes the following steps: (1) energy tracks of two sets of kP operations are collected; (2) side channel energy analysis is carried out based on the energy tracks obtained in the step (1) to recognize hidden point add operations; (3) different portions in the point add operations are mapped to the energy tracks to carry out side channel energy analysis, and a secret key sequence of k is concluded. The method provides a theoretical basis for implementation of chosen plaintext side channel energy analysis for the ECC algorithm of the P domain.
Owner:国家密码管理局商用密码检测中心
Intelligent confrontation sample generation method and system based on optimization algorithm and invariance
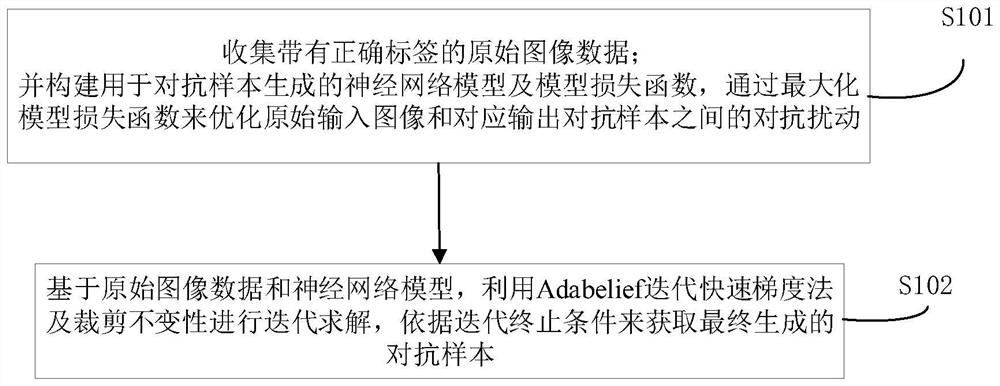
PendingCN114066912AImprove portabilityImprove the build processImage enhancementImage analysisNetwork modelEngineering
The invention belongs to the technical field of image recognition data processing, and particularly relates to an intelligent adversarial sample generation method and system based on an optimization algorithm and invariance. The method comprises the steps: collecting original image data with a correct label; constructing a neural network model for adversarial sample generation and a model loss function, and optimizing adversarial disturbance between an original input image and a corresponding output adversarial sample by maximizing the model loss function; based on original image data and a neural network model, an Adazief iterative quick gradient method and a cutting invariance method are used for iterative solution, and a finally generated adversarial sample is obtained according to an iteration termination condition. From the perspective that the generation process of the adversarial sample is similar to the neural network training process, the convergence process is optimized through the Adazief iteration quick gradient method, the over-fitting phenomenon in the adversarial attack is avoided by using the cutting invariance, the adversarial sample with better mobility can be generated, the robustness of the network model is improved, and the practical scene application is facilitated.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Adversarial sample and generation method thereof, medium, device and computing equipment
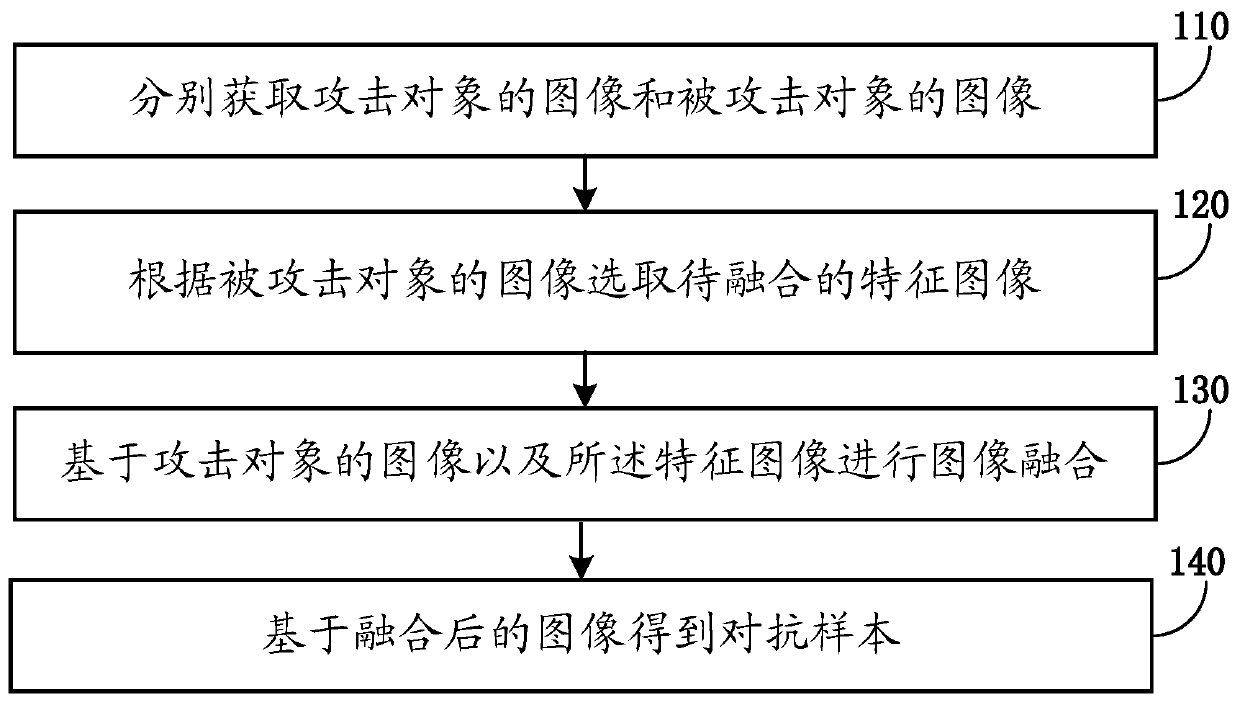
ActiveCN110705652AImprove attack success rateSave computing resourcesCharacter and pattern recognitionPattern recognitionEngineering
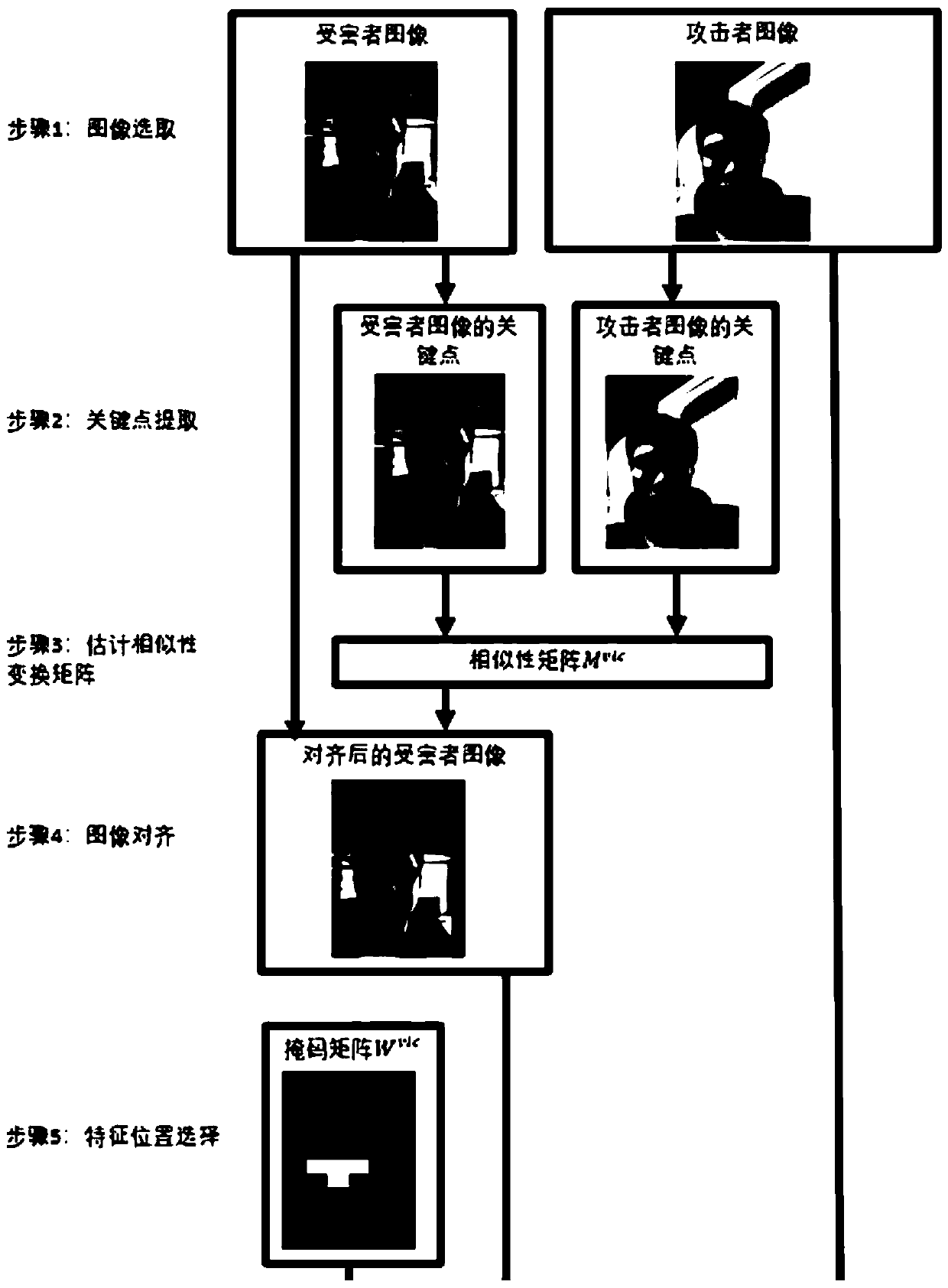
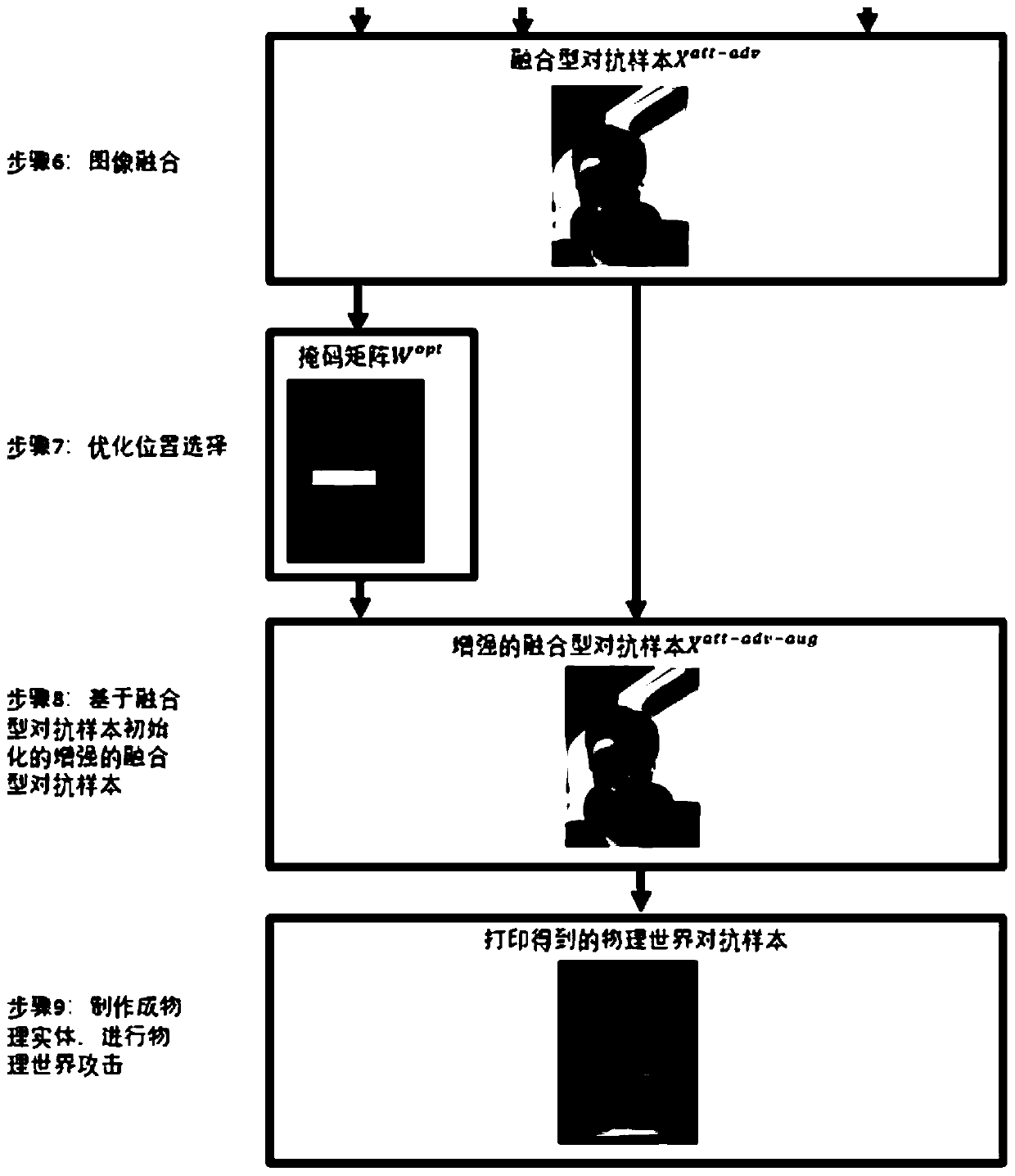
The embodiment of the invention provides an adversarial sample generation method. The method comprises the following steps: respectively acquiring an image of an attack object and an image of an attacked object; selecting a feature image to be fused according to the image of the attacked object; performing image fusion based on the image of the attack object and the feature image; and obtaining anadversarial sample based on the fused image. According to the method disclosed by the invention, the adversarial sample is generated; a model which is the same as or similar to the attacked model does not need to be acquired and / or operated; in addition, according to one method disclosed by the invention, an adversarial sample based on image fusion can be adopted as initialization, the attack success rate of an existing adversarial sample generation method based on optimization can be remarkably improved, and the embodiment of the invention provides an adversarial sample generation device, amedium and computing equipment.
Owner:BEIJING REALAI TECH CO LTD
Method for modular multiplication remainder input side channel attacks aiming at M-ary implementation of RSA
ActiveCN104811297ASmall amount of signal processing dataReduce distractionsEncryption apparatus with shift registers/memoriesLinear correlationMeasurement point
The invention discloses a method for modular multiplication remainder input side channel energy analysis attacks aiming at M-ary implementation of an RSA cryptographic algorithm. The core of the method is that when M-ary implementation is used by modular exponentiation, modular multiplication remainder input serves as an attack target to implement CPA (correlation power analysis) attacks. The method comprises the steps that (1) signals are acquired, and a sampling matrix is established; (2) the modular multiplication remainder input is selected to serve as the attack target; (3) a correlation model is determined; (4) cycle index values are guessed, and a median matrix is calculated; (5) a simulated energy consumption matrix is calculated; (6) linear correlation coefficients between corresponding measuring points in the step (1) and the matrix determined in the step (5) are calculated, correct modular multiplication remainder input values of all cycles are attacked, and all corresponding correct cycle indexes are found out, and are connected in series, so that a complete index is obtained. According to the method, a novel M-ary side channel attack method is provided, and the flexibility, the effectiveness and the success rate of RSA cryptographic algorithm analysis attacks are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
Voiceprint recognition confrontation sample generation method based on boundary attack
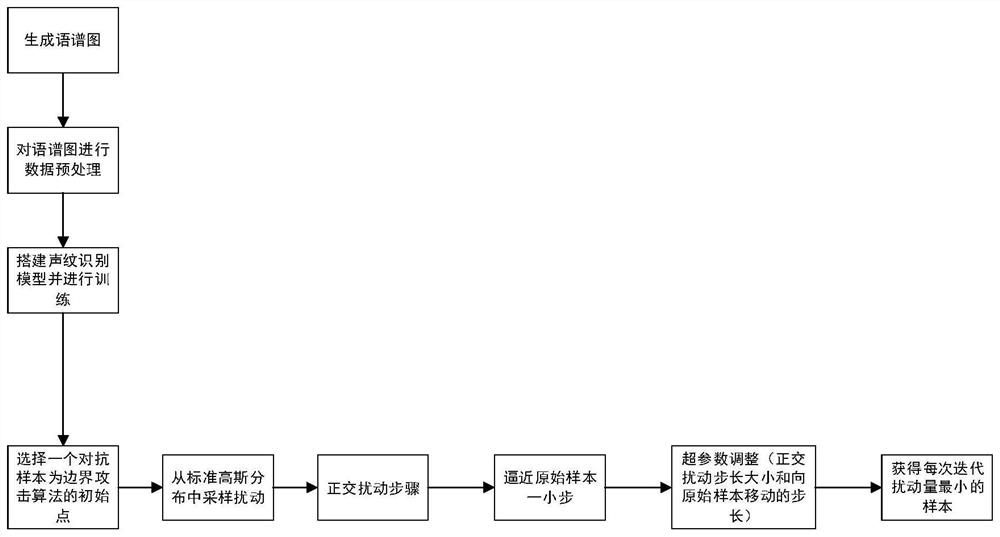
PendingCN113571067AImprove classification accuracyAccurately predict identity labelsSpeech analysisCryptographic attack countermeasuresAlgorithmSpeech sound
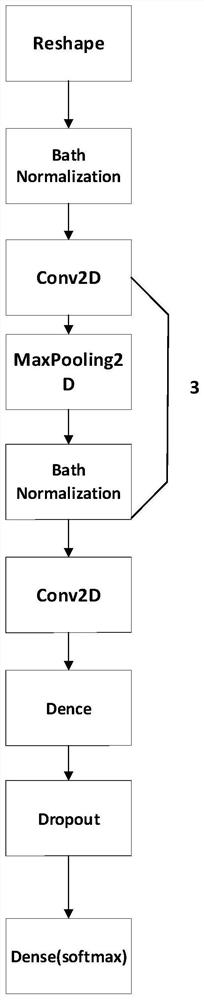
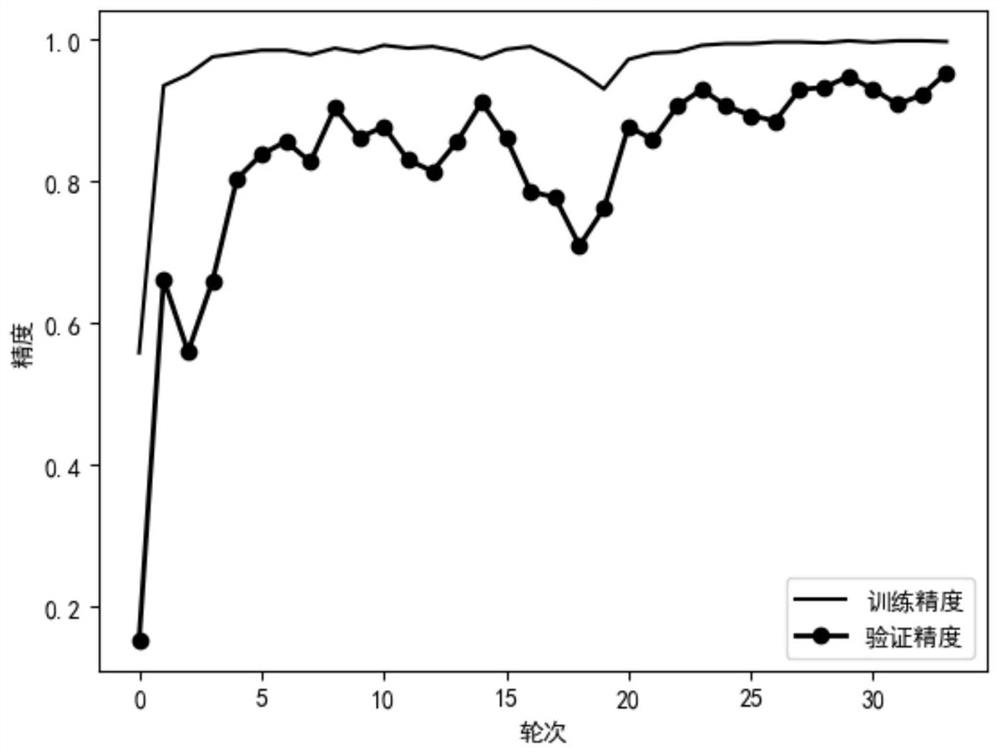
The invention discloses a voiceprint recognition confrontation sample generation method based on boundary attack. The method comprises the following steps: 1) performing data preprocessing on a used voice data set; 2) building a voiceprint recognition model; and 3) an algorithm for generating a confrontation sample through boundary attack, wherein the process comprises the following steps: selecting an initial point of a boundary attack algorithm, selecting a walking direction, and adjusting hyper-parameters. When the voiceprint identity is classified, traditional acoustic feature methods are not adopted, the voice is converted into the spectrogram for training, the advantage that the convolutional neural network extracts features on the image can be fully utilized, and the precision is greatly improved; and the method belongs to black box attacks, the structure and parameters of an original model do not need to be known, only classification labels of the model are needed, the application range is wider, and the practical significance is higher. The attack success rate is high, and generated confrontation samples cannot be perceived by naked eyes.
Owner:ZHEJIANG UNIV OF TECH
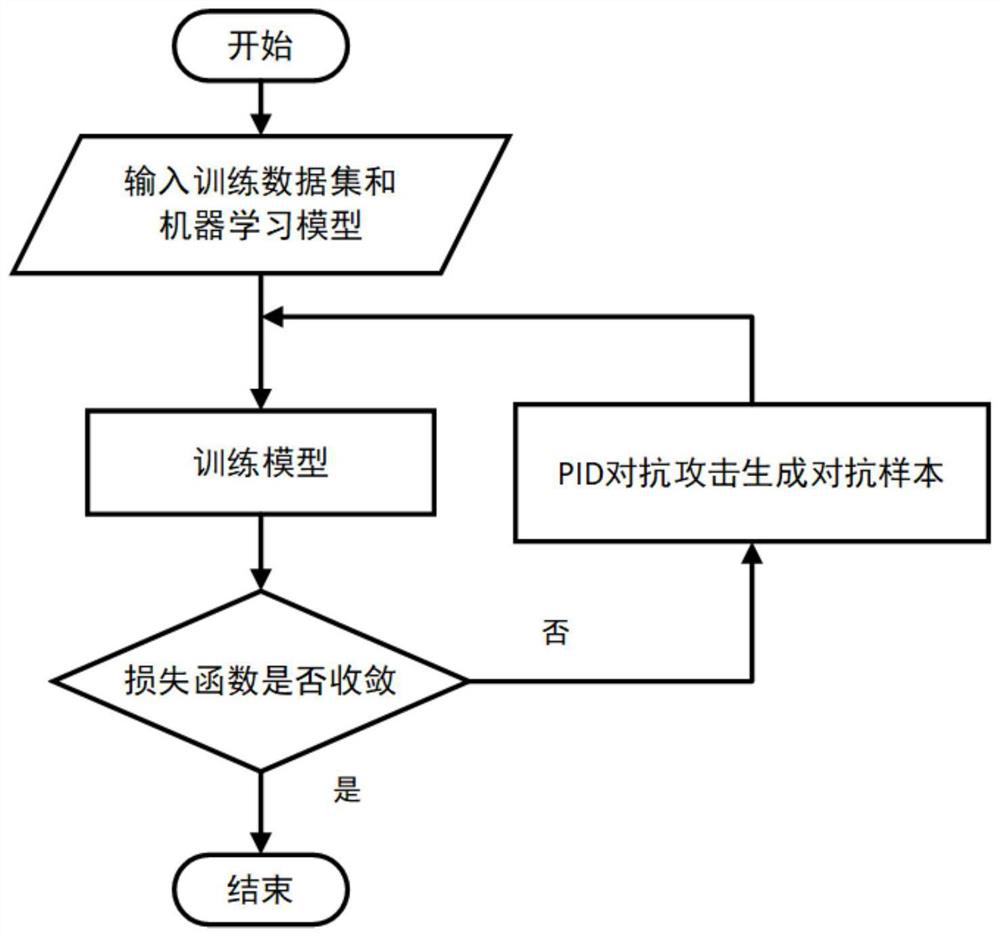
Antagonistic attack and defense method and system based on PID controller
InactiveCN112085050AIncrease success rateStrong disturbanceCharacter and pattern recognitionMachine learningData setAlgorithm
The invention relates to an antagonistic attack and defense method and system based on a PID controller. The method comprises the following steps: S1, inputting a training data set and a machine learning model f; s2, training a machine learning model f according to the input training data set; and S3, judging whether the loss function J is converged or not, if the loss function J is not converged,training the machine learning model f by adopting the adversarial sample xadv generated by the adversarial attack based on the PID controller and the original data x as a training data set until theloss function J is converged to obtain the trained machine learning model f, and if the loss function J is converged, directly outputting a result. According to the invention, a higher attack successrate can be realized under the same disturbance constraint limitation through a process of generating an adversarial sample by an adversarial attack, and the invention can be used for evaluating the performance of a machine learning model and the effectiveness of an adversarial defense method; adversarial training on the machine learning model by using adversarial samples generated by adversarialattacks can be used as a defense method to improve the robustness of the model.
Owner:SUN YAT SEN UNIV
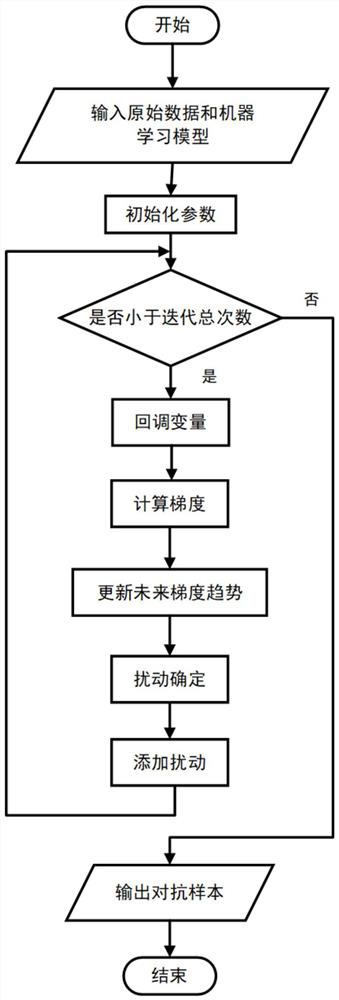
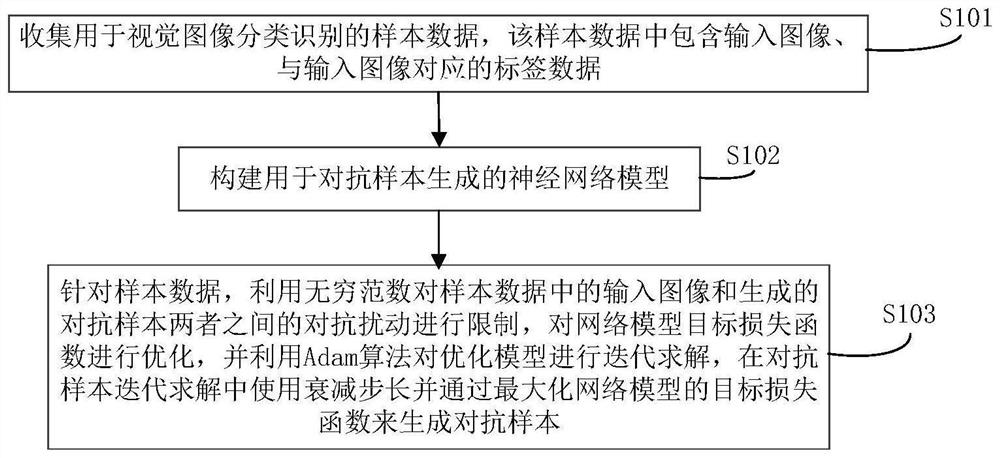
Adam algorithm-based adversarial sample generation method and system
PendingCN113591975AImprove migration abilityImprove build qualityCharacter and pattern recognitionNeural architecturesAlgorithmNetwork model
The invention belongs to the technical field of computer vision image recognition, and particularly relates to an adversarial sample generation method and system based on an Adam algorithm. Sample data used for vision image classification recognition are collected, and the sample data comprise an input image and label data corresponding to the input image; a neural network model used for adversarial sample generation is constructed; and, for sample data, adversarial disturbance between an input image in the sample data and a generated adversarial sample is limited by using an infinite norm, a neural network model loss function is optimized, an optimization model is iteratively solved by using an Adam algorithm, and the adversarial samples are generated by maximizing the target loss function of the model using the attenuation step size in the iterative solution of the adversarial samples. The migration of the adversarial samples between the models is increased by using the attenuation step length, so that the adversarial samples with relatively high quality are obtained, the robustness of the deep learning classification model is improved, and the quality and efficiency of visual image classification and recognition can be effectively guaranteed.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
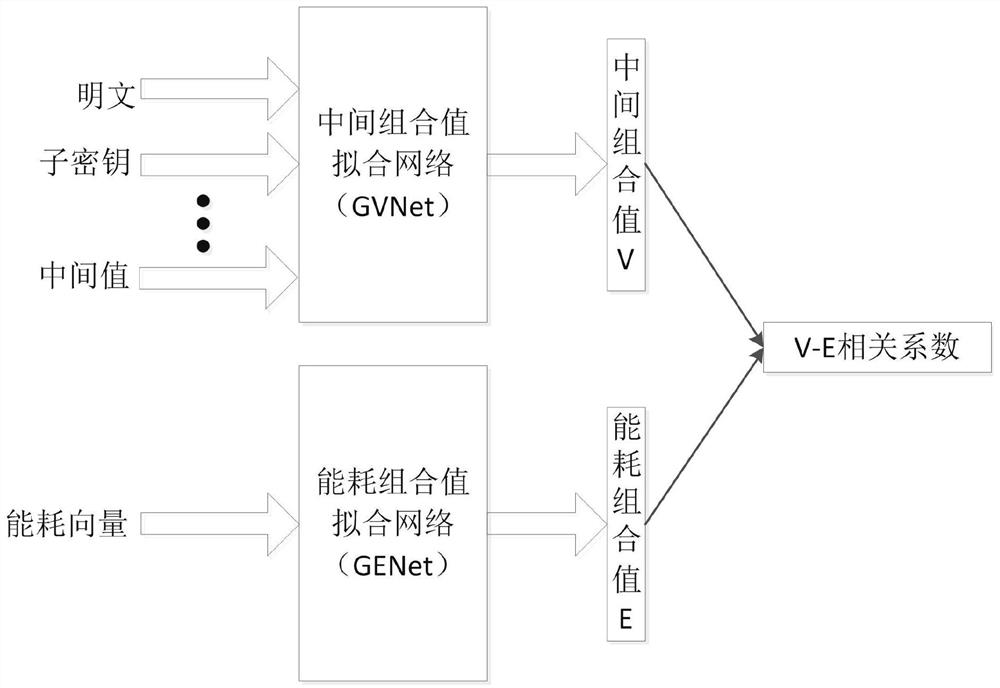
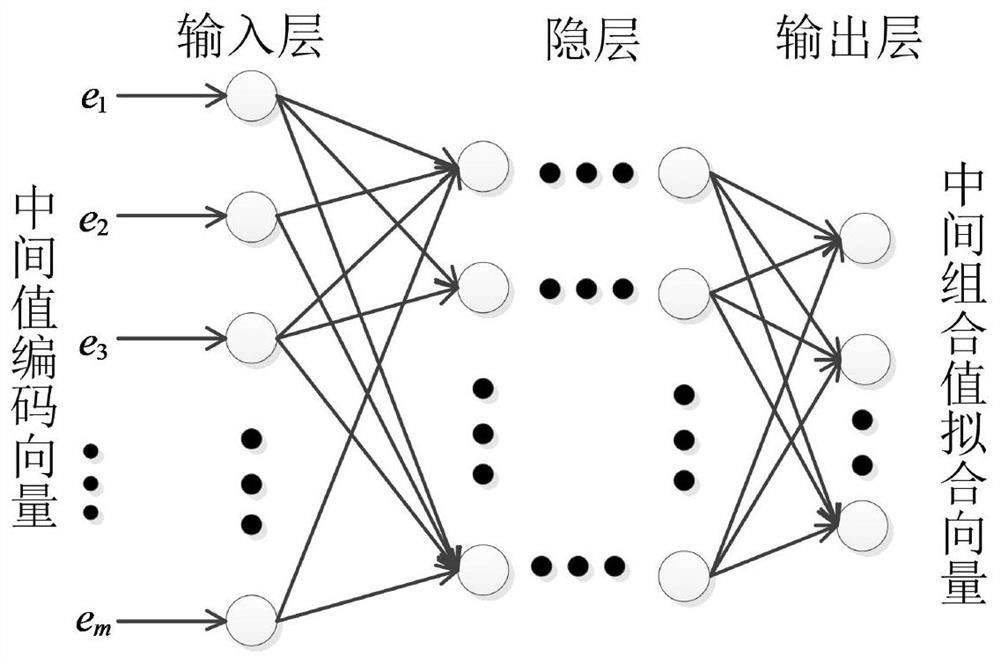
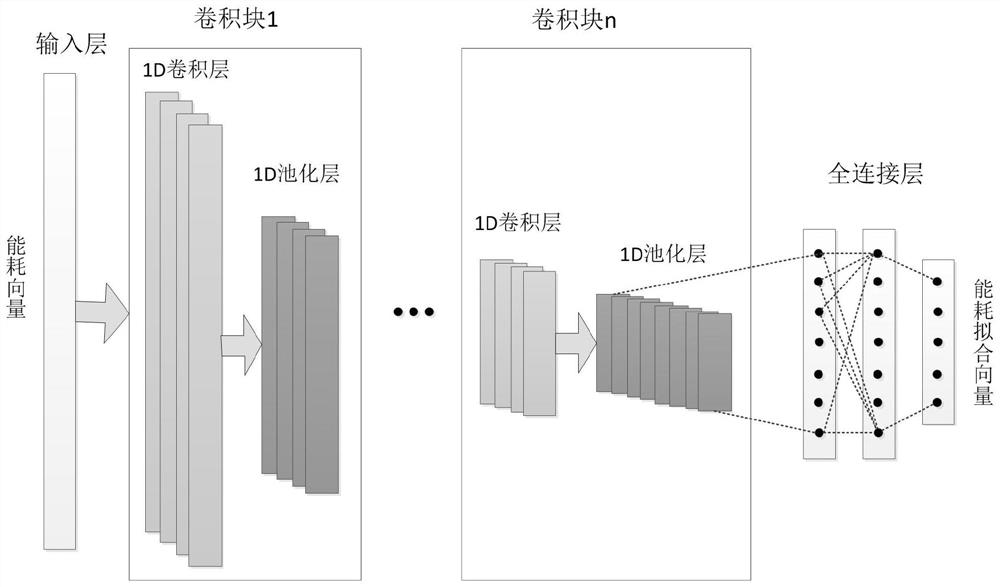
Learning side channel attack method for automatically discovering leakage model and encryption equipment
ActiveCN113158179ABig chanceLower success rateDigital data protectionPlatform integrity maintainanceData setAttack model
The invention belongs to the technical field of cryptographic algorithm analysis and detection, and discloses a learning side channel attack method for automatically discovering a leakage model and encryption equipment. A neural network of an attack model is trained, a combination form of an intermediate combination value of leakage key information and a corresponding energy consumption combination form are searched. The training target is to maximize the correlation between the intermediate combination value and the energy consumption combination value; in the attack stage, the attack model is used for identifying the correctness of guessed sub-keys; and the master key of the encryption equipment is recovered according to the sub-key obtained by the attack. In an attack stage, an attack data set of an unknown key is used, guess sub-keys are input into an attack model, and a vector distance between a corresponding guess middle combination value and an energy consumption combination value is calculated. The guessed sub-key with the minimum distance is selected as a correct sub-key, the sub-keys are obtained one by one by adopting a divide-and-conquer principle, and back calculation is performed on the master key to attack the master key of the encryption equipment.
Owner:CHENGDU UNIV OF INFORMATION TECH
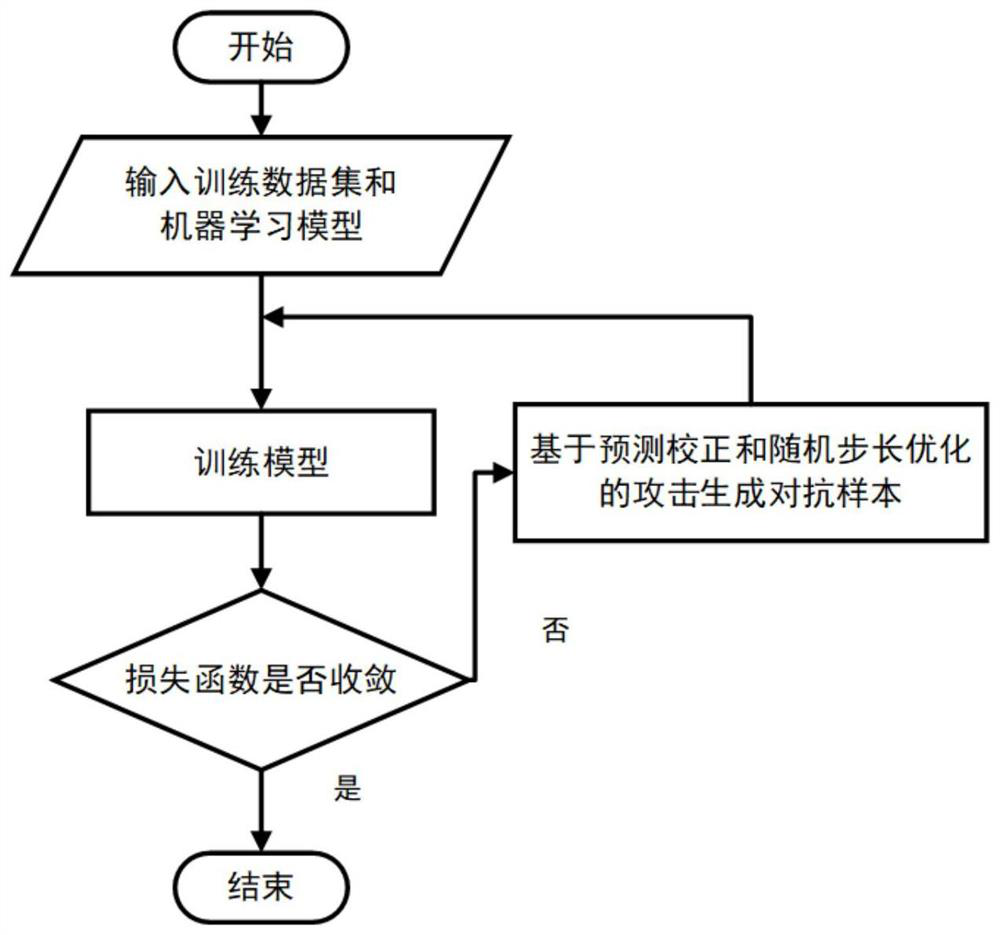
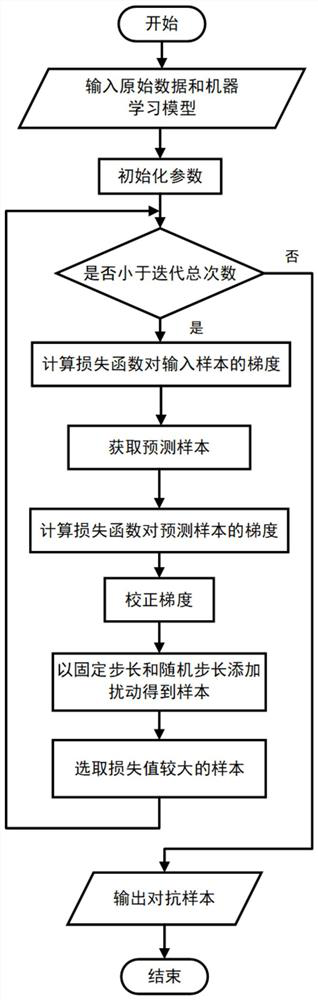
Adversarial attack and defense method and system based on prediction correction and stochastic step size optimization
The invention discloses an adversarial attack and defense method and system based on prediction correction and stochastic step size optimization. The method comprises the following steps: inputting a training data set and a machine learning model; training a machine learning model according to the input training data set; judging whether the loss function converges or not; if the loss function is not converged, generating an adversarial sample by adopting an adversarial attack based on prediction correction and stochastic step size optimization, and using the adversarial sample and the original data as a training data set to train a machine learning model until the loss function is converged, and obtaining a trained machine learning model; and if the loss function converges, directly outputting a result. The confrontation samples are generated through confrontation attacks, the higher attack success rate can be achieved under the same disturbance constraint limitation, and the method can be used for evaluating the performance of a machine learning model and the effectiveness of a confrontation defense method; the generated adversarial sample carries out adversarial training on the machine learning model, so that various adversarial attacks can be effectively resisted, and the robustness of the model is improved.
Owner:SUN YAT SEN UNIV
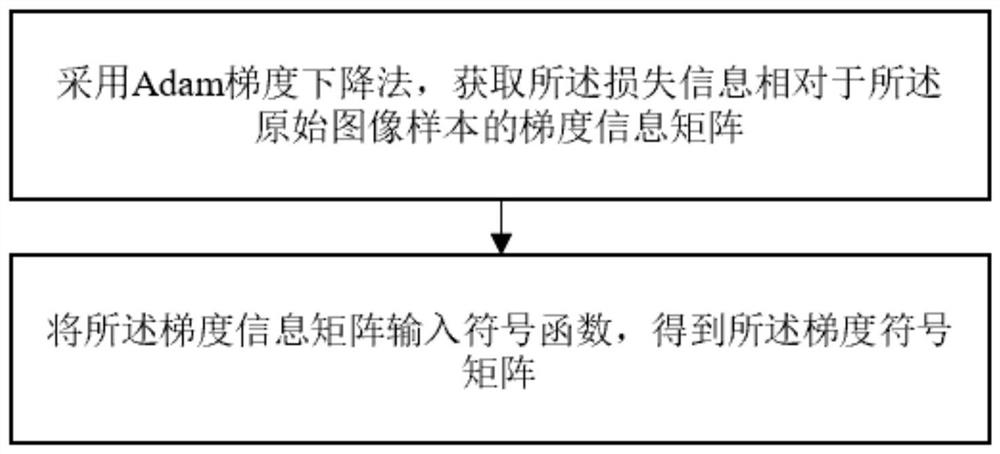
Gradient-based adversarial sample generation method and system
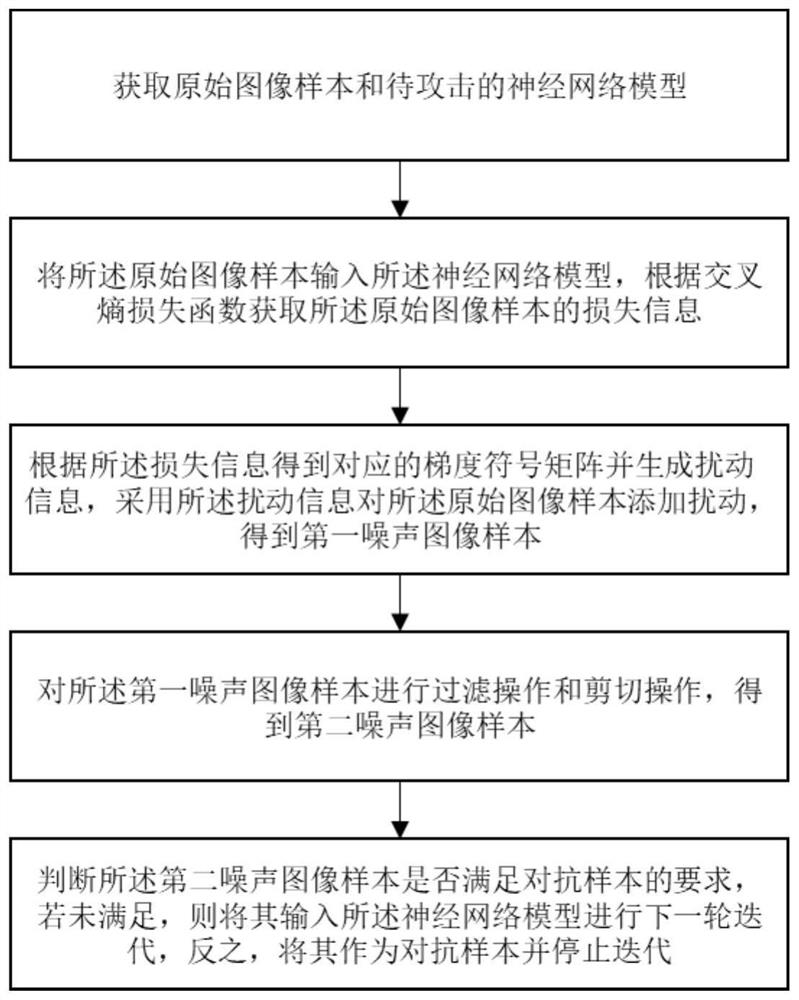
PendingCN114663665AReduce lossImprove attack success rateCharacter and pattern recognitionNeural architecturesComputer visionNetwork model
The invention discloses a gradient-based adversarial sample generation method and system. The method comprises the following steps: acquiring an original image sample and a neural network model to be attacked; inputting the original image sample into a neural network model, and obtaining loss information of the original image sample according to a cross entropy loss function; a corresponding gradient symbol matrix is obtained according to the loss information, disturbance information is generated, disturbance is added to the original image sample through the disturbance information, and a first noise image sample is obtained; performing filtering operation and cutting operation on the first noise image sample to obtain a second noise image sample; and judging whether the second noise image sample meets the requirements of the adversarial sample, if not, inputting the second noise image sample into the neural network model for next iteration, and otherwise, taking the second noise image sample as the adversarial sample and stopping iteration. According to the method, the adversarial sample with higher attack success rate and smaller noise visibility can be generated, so that the ability of the neural network model to resist adversarial attacks is enhanced.
Owner:SOUTH CHINA UNIV OF TECH
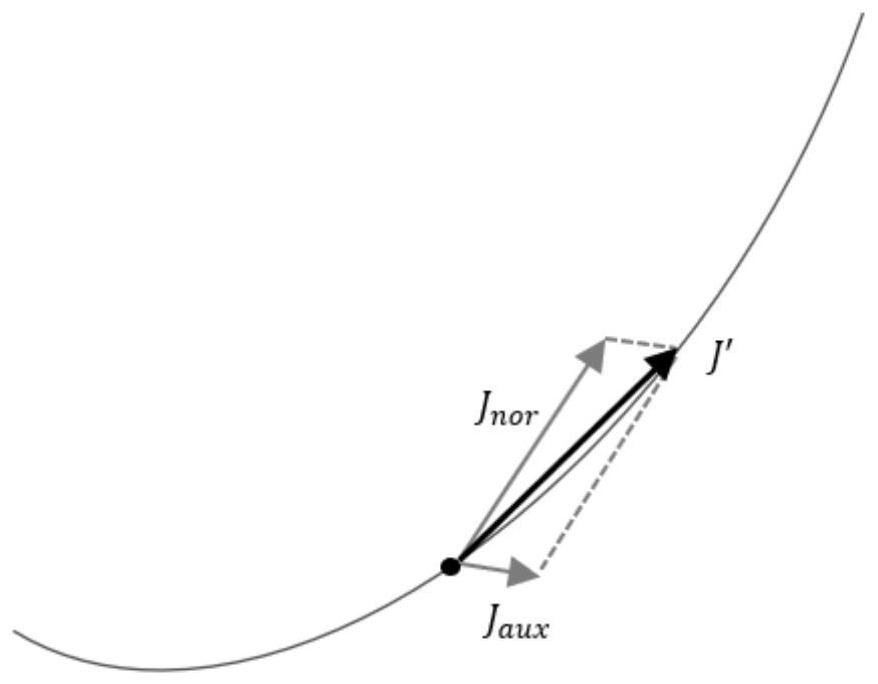
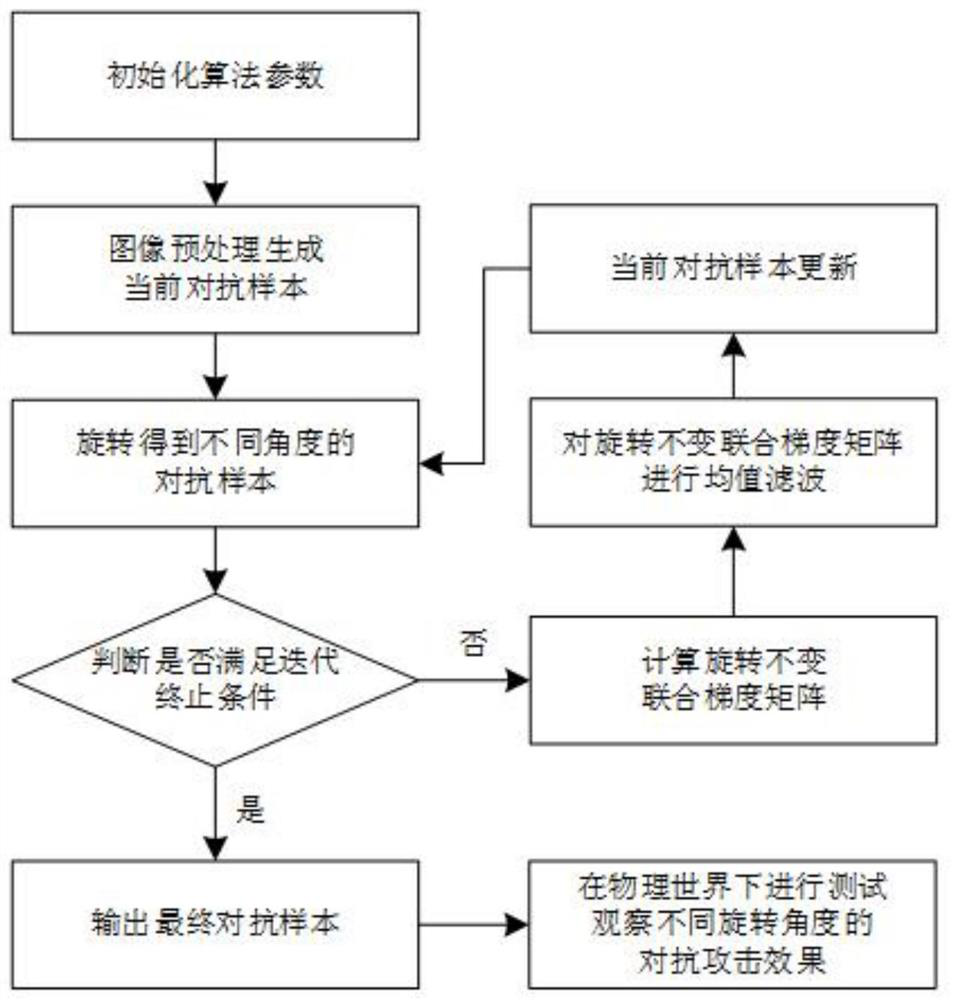
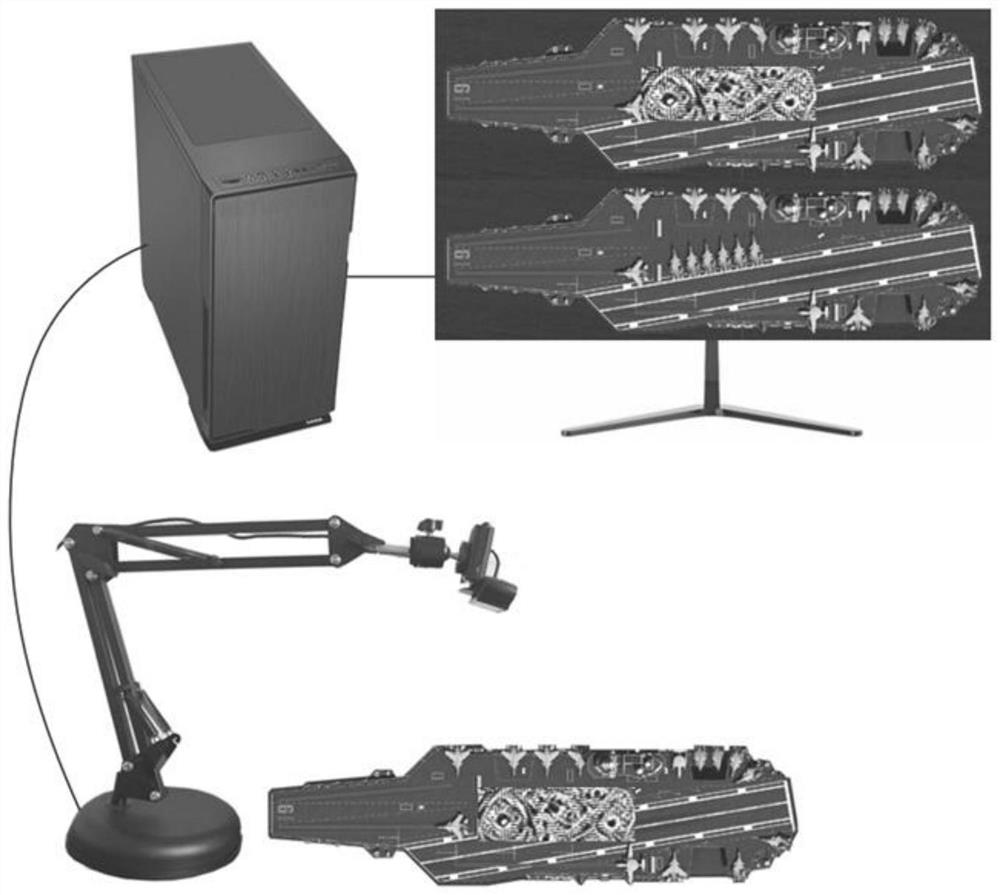
Image confrontation sample generation method with rotation robustness in physical world
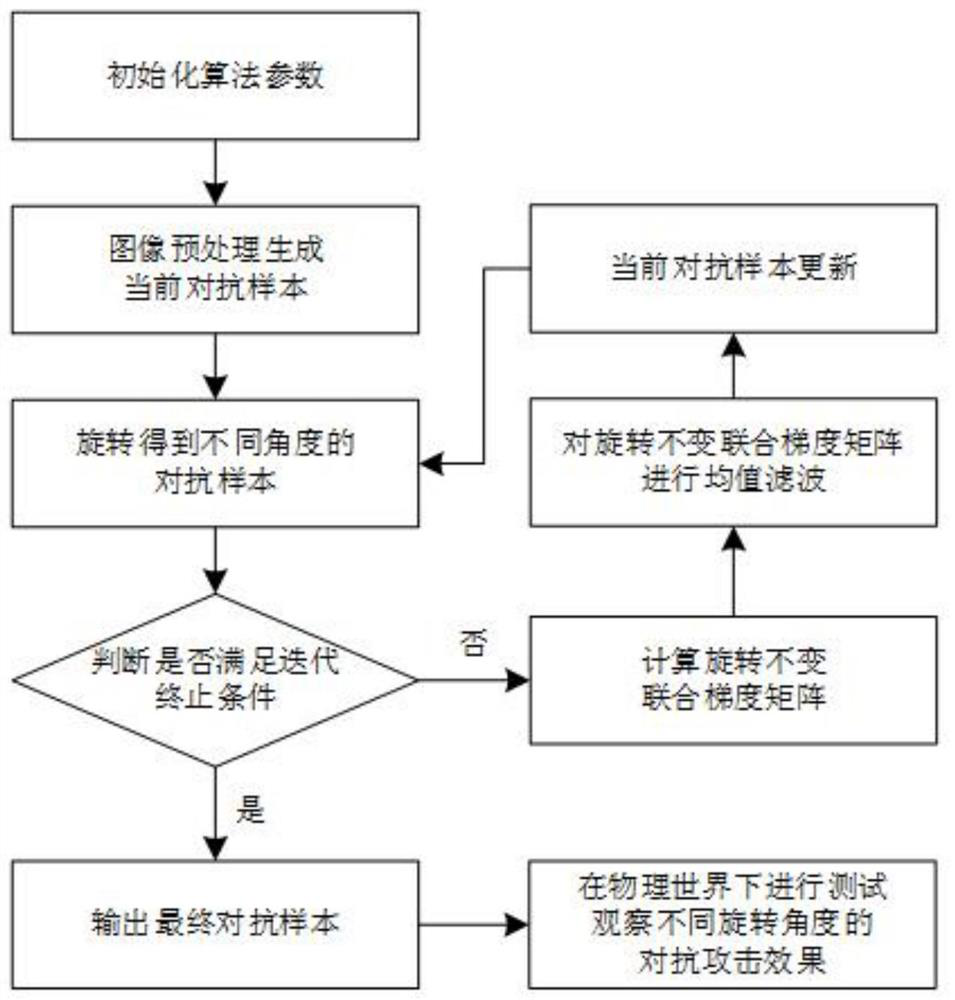
ActiveCN114332446AGuaranteed rotation robustnessGuarantees that the generated adversarial examples are rotation-robust in the physical worldCharacter and pattern recognitionNeural architecturesAlgorithmImage pair
The invention relates to an image confrontation sample generation method with rotation robustness in a physical world, and relates to the technical field of artificial intelligence security. The method mainly comprises the following steps: 1, initializing algorithm parameters and preprocessing an image to obtain a current confrontation sample; 2, rotating the current adversarial sample to obtain a rotated adversarial sample; 3, judging whether an iteration termination condition is met, if so, outputting a final confrontation sample and executing the step 7, otherwise, executing the step 4; 4, calculating a rotation invariant joint gradient matrix; 5, performing mean filtering on the rotation invariant joint gradient matrix; 6, updating the current confrontation sample, and returning to the step 23; and 7, testing by using the final confrontation sample in a real physical world, and observing confrontation attack effects at different rotation angles. The confrontation sample generated by the method has rotation robustness in the physical world, the problem that attack failure exists after the confrontation sample is rotated is solved, and the attack success rate is further improved.
Owner:BEIJING INST OF COMP TECH & APPL
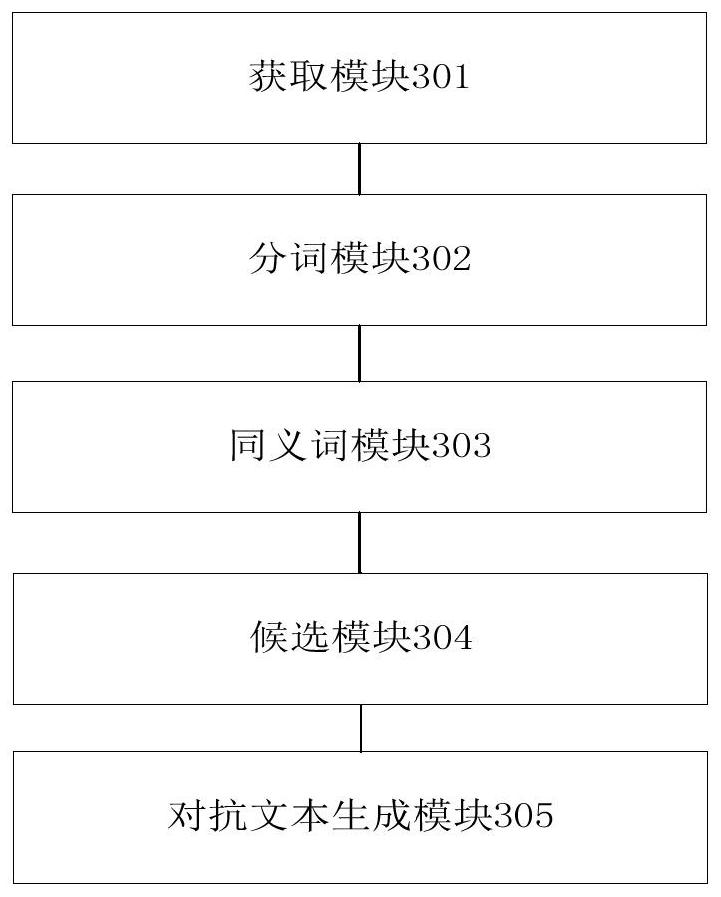
Adversarial text generation method and system for black box text classification model and medium
PendingCN113886559AFluency is easy to guaranteeImprove attack success rateNatural language data processingSpecial data processing applicationsAlgorithmText categorization
The invention relates to the technical field of adversarial text generation, in particular to an adversarial text generation method and a system for a black box text classification model and a medium. The method comprises the following steps: collecting an original corpus and a classification label of a black box text classification model; performing word segmentation on the original corpus to obtain a word sequence corresponding to the original corpus; respectively obtaining a preset number of synonyms of each word in the word sequence; sequentially replacing the positions of the words in the candidate sentences with synonyms of the words to form new sentences, and forming a new candidate text set; and taking each sentence in the new candidate text set as the input of the black box text classification model in sequence to obtain a corresponding output result, and screening out K sentences with the lowest probability value of the original tag corresponding to the original corpus to form a confrontation text set. The invention has better performance in the aspects of confrontation sample quality and effectiveness control and attack success rate, and the generated confrontation sample has smoothness and fluency.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
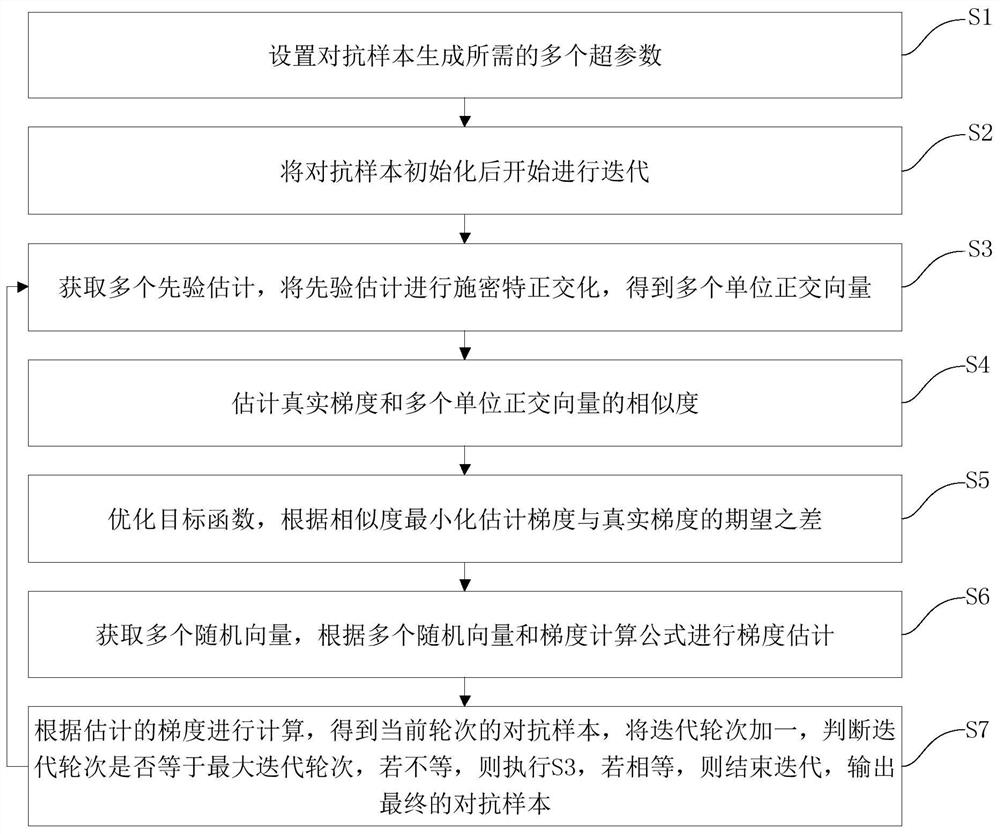
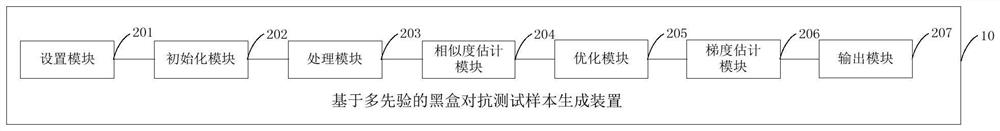
Multi-priori-based black box adversarial test sample generation method and device
ActiveCN112667496AImprove attack success rateReduce the number of samplesSoftware testing/debuggingMachine learningEngineeringTest sample
The invention discloses a multi-prior-based black box adversarial test sample generation method and device. The method comprises the steps of setting a plurality of hyper-parameters required for adversarial sample generation; initializing the adversarial sample and starting iteration; obtaining a plurality of different priors to obtain a group of orthogonal bases; estimating the similarity between the real gradient and each orthogonal vector; optimizing the objective function, and minimizing the expected difference between the estimated gradient and the real gradient; sampling a plurality of random vectors; estimating gradients according to a stochastic gradient estimation method. Therefore, the attack success rate of the neural network can be improved, or under the condition of the same attack success rate, the sampling frequency for estimating the gradient is reduced, and the generation of adversarial samples is accelerated.
Owner:TSINGHUA UNIV
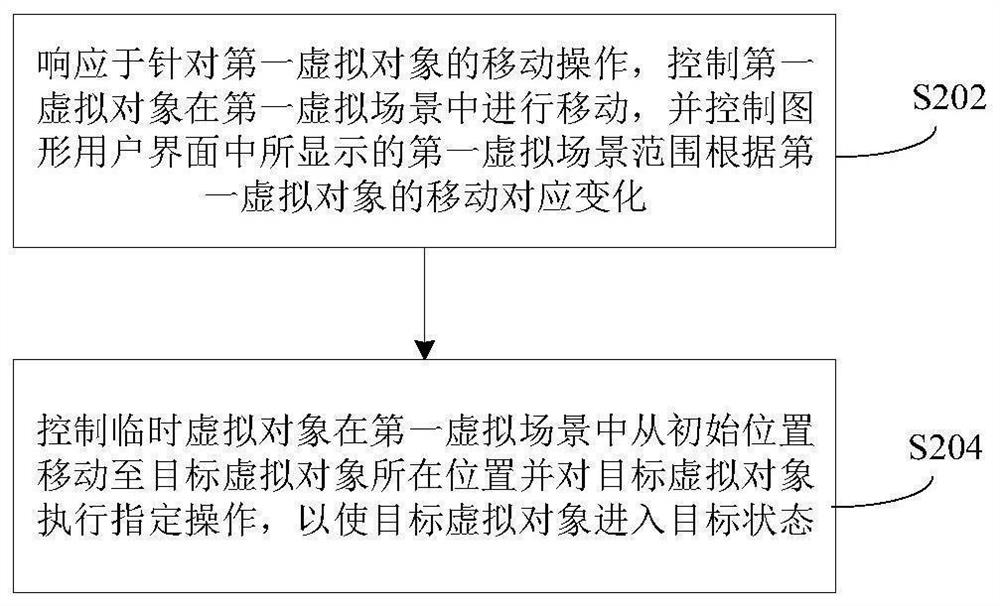
Target attack method and device in game and electronic equipment
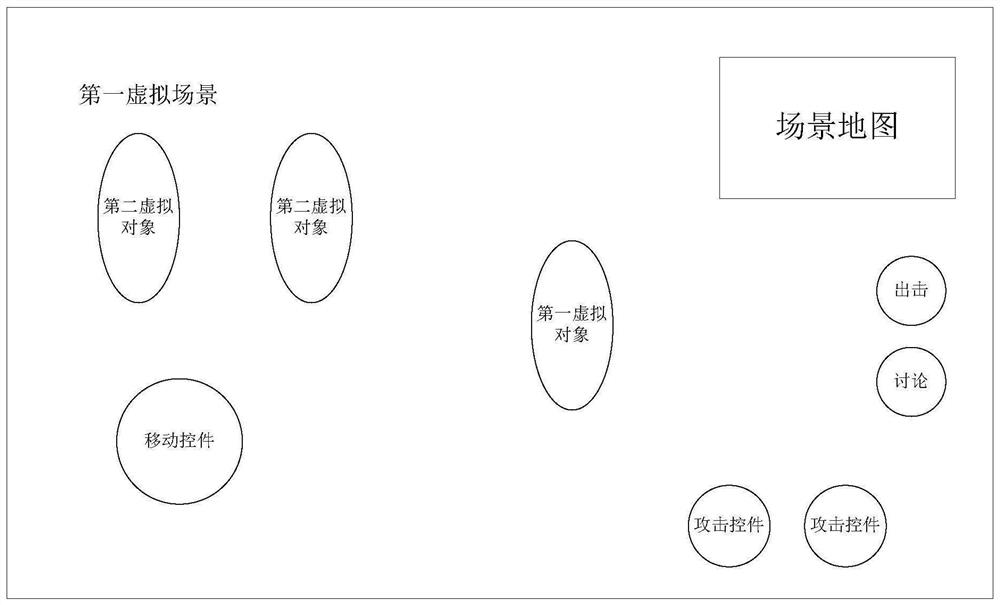
PendingCN113101639AReduce the risk of exposing the target's identitySimple and fast operationVideo gamesGraphical user interfaceAttack
The invention provides a target attack method and device in a game and electronic equipment. The method comprises the following steps: in response to a movement operation for a first virtual object, controlling the first virtual object to move in a first virtual scene, and controlling a first virtual scene range displayed in a graphical user interface to correspondingly change according to the movement of the first virtual object; and controlling the temporary virtual object to move from the initial position to the position of the target virtual object in the first virtual scene, and executing a specified operation on the target virtual object, so that the target virtual object enters a target state. The method is simple and convenient to operate, can help the virtual object reduce the risk of exposing the target identity, and improves the attack success rate.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
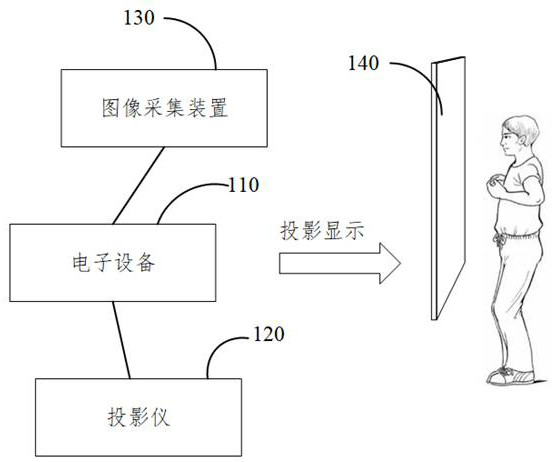
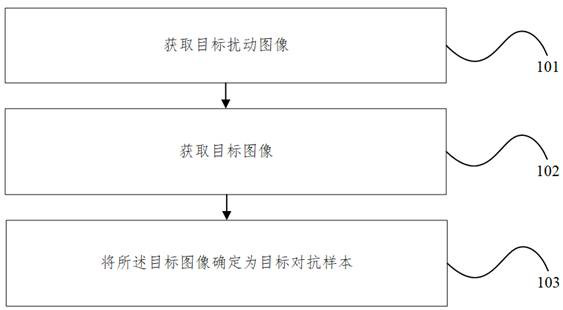
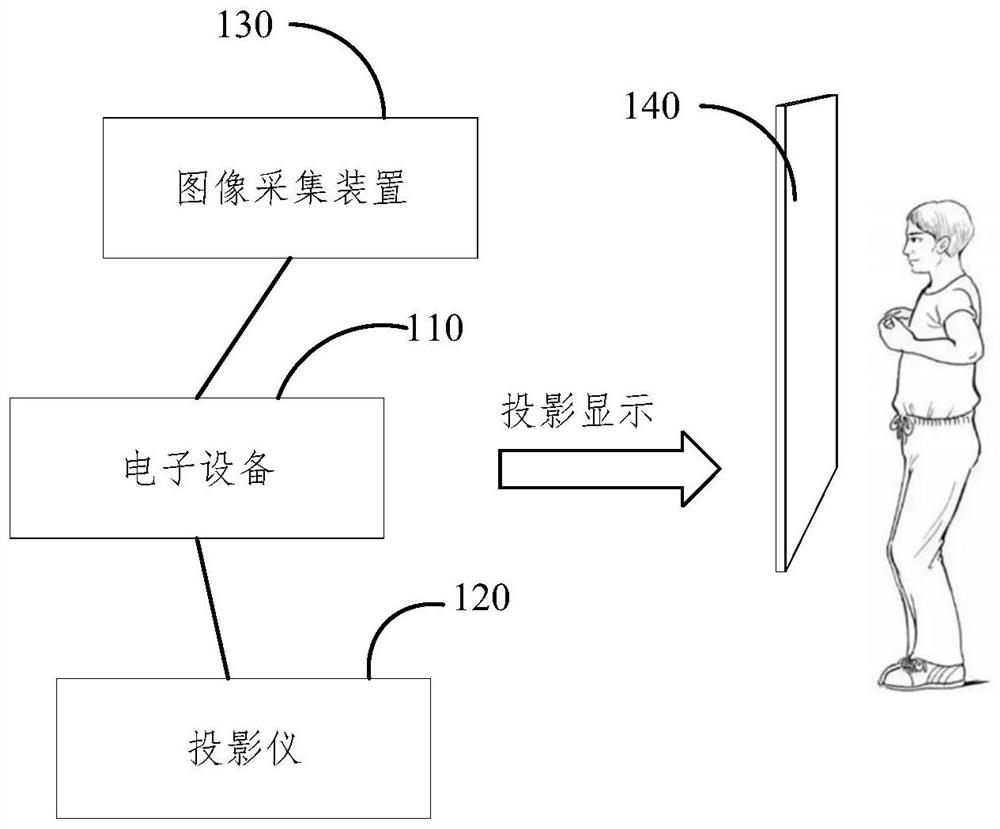
Physical world confrontation sample generation method and device, electronic equipment and storage medium
PendingCN114005168AImprove attack success rateImplement global perturbation attackCharacter and pattern recognitionComputer graphics (images)Algorithm
The invention relates to a physical world confrontation sample generation method and device, electronic equipment and a storage medium, and is applied to the technical field of artificial intelligence. The method comprises the steps: obtaining a target disturbance image which is an image projected to a holographic film and generated based on an adversarial attack algorithm, and obtaining a target image, wherein the target image comprises a target disturbance image and a first face image of the first user, and determining the target image as a target confrontation sample. The anti-disturbance image of the digital world displayed in the electronic equipment can be converted into the real physical world in a holographic imaging mode, the anti-disturbance image does not need to be printed, so that unknown loss introduced in the printing process is avoided, the attack success rate of the physical world anti-disturbance sample is improved, and the global disturbance attack can be realized in the physical world.
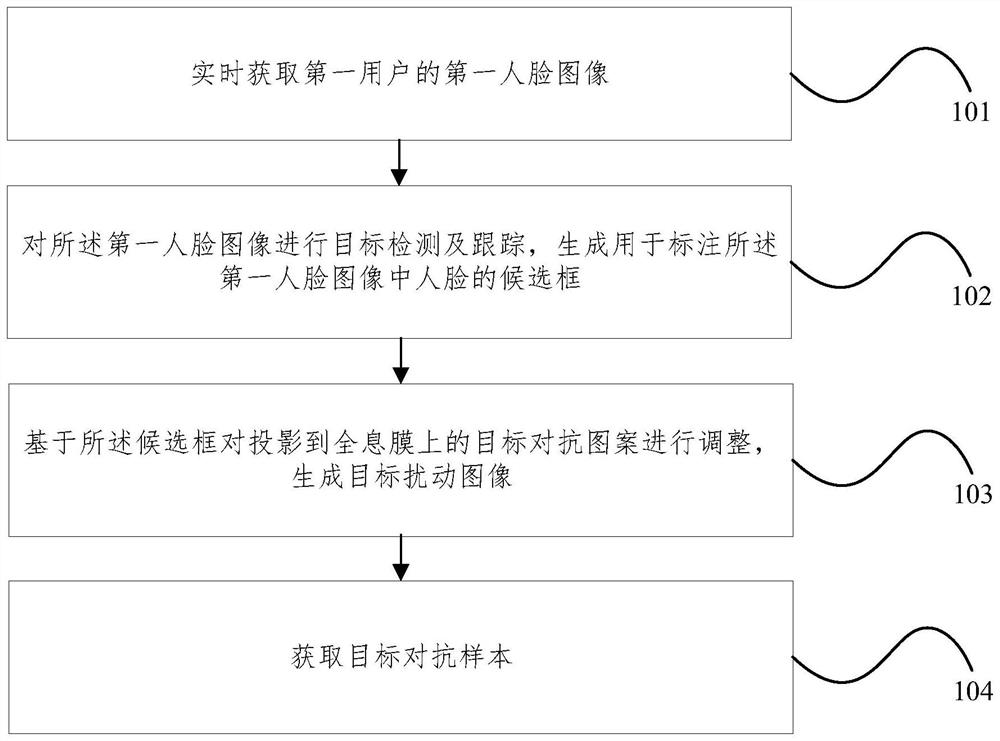
Owner:BEIJING REALAI TECH CO LTD
Convolutional neural network-based side channel attack method and system
PendingCN114285545AImprove attack success rateShorten training timeKey distribution for secure communicationNeural architecturesSide channel attackKey recovery
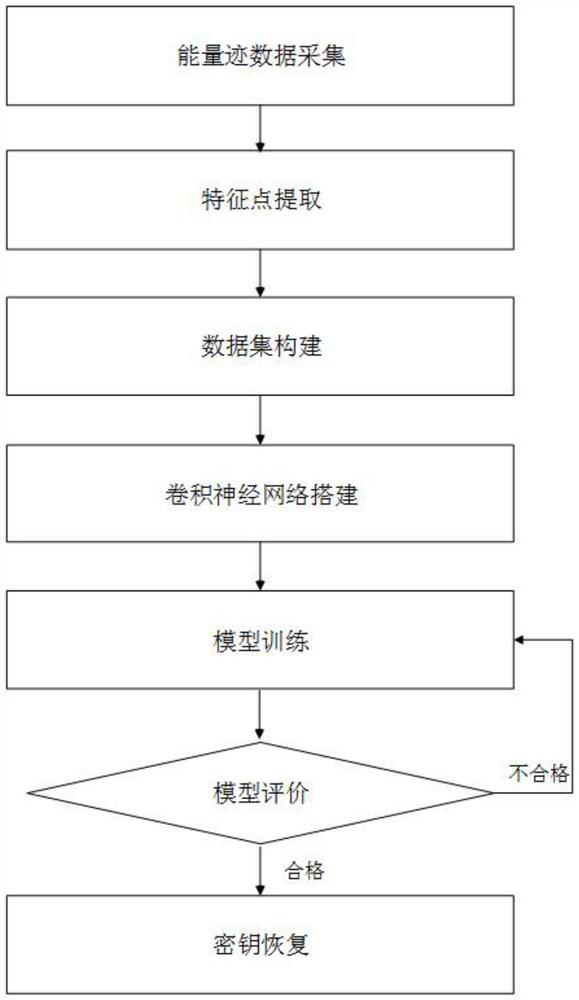
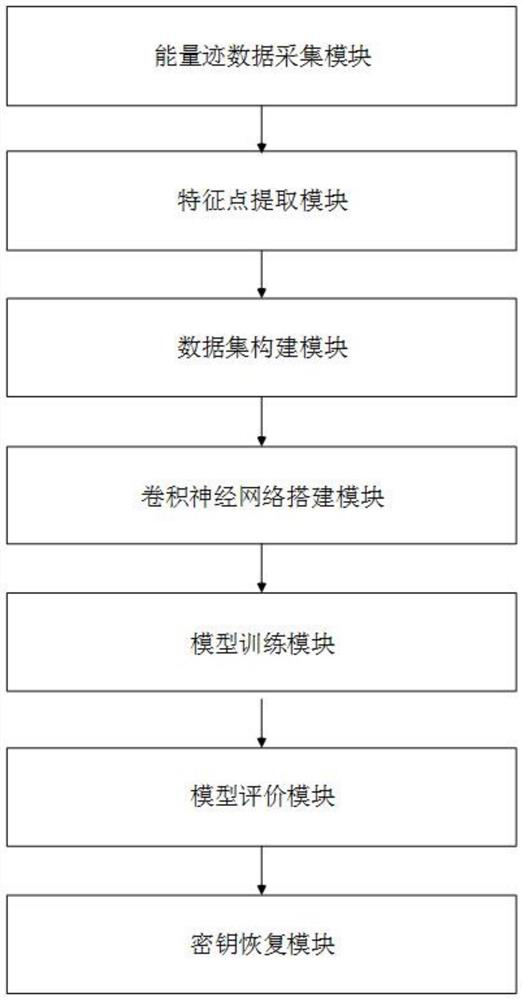
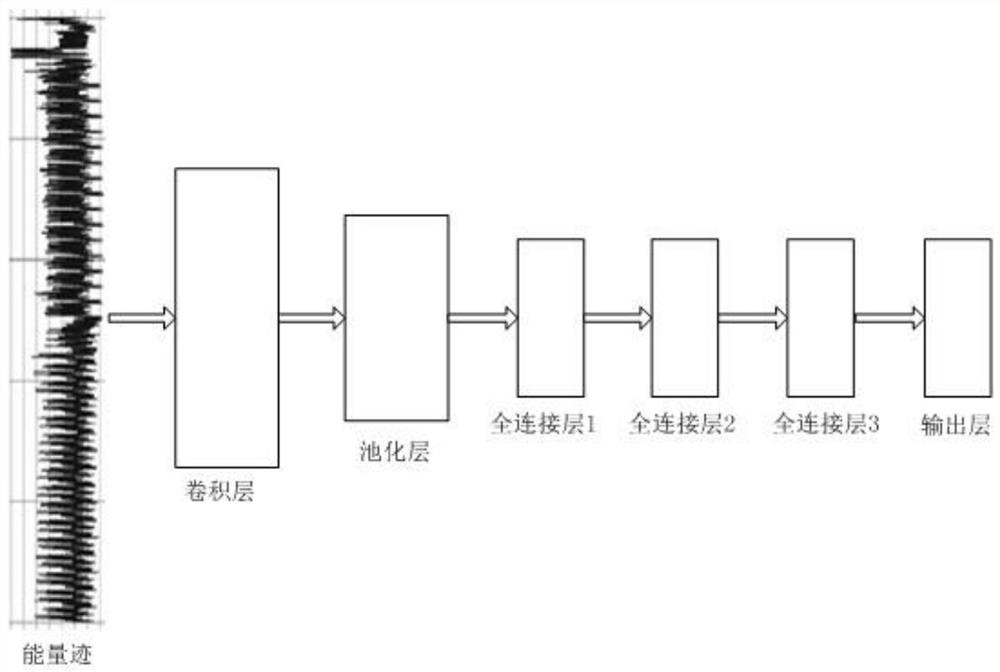
The invention relates to the technical field of side channel attacks, and discloses a side channel attack method and system based on a convolutional neural network, and the attack method comprises the following steps: S1, collecting energy trace data; s2, extracting feature points; s3, constructing a data set; s4, constructing a convolutional neural network; s5, model training; s6, model evaluation; and S7, key recovery. The problems that in the prior art, template matching is difficult, and universality is low are solved.
Owner:成都三零嘉微电子有限公司
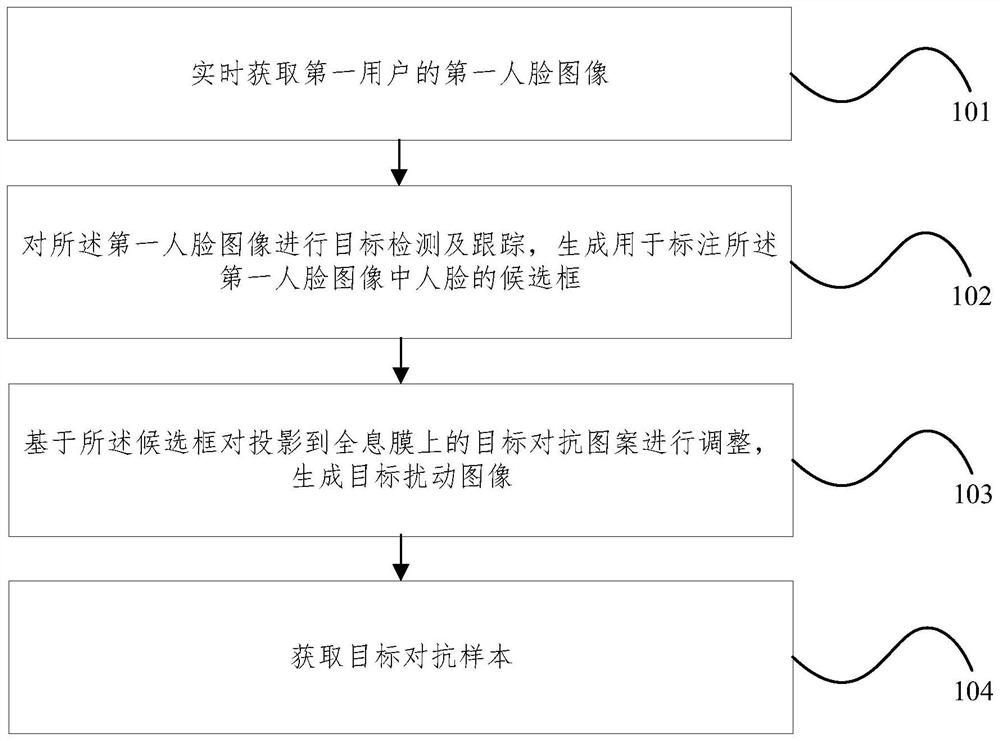
Adversarial sample dynamic generation method, device, electronic device and storage medium
ActiveCN114419704BAvoid the impact of attack success rateImprove attack success rateCharacter and pattern recognitionMachine learningComputer graphics (images)Algorithm
The present application relates to a method, device, electronic device and storage medium for dynamically generating adversarial samples. The method includes: acquiring a first face image of a first user in real time; performing target detection and tracking on the first face image, generating a candidate frame for marking the face in the first face image; adjusting the target confrontation pattern projected on the holographic film based on the candidate frame to generate a target disturbance image; acquiring a target confrontation sample, the target confrontation A sample includes the first face image and the target perturbation image. The present application can realize the conversion of the confrontation disturbance image of the digital world displayed in the electronic device into the real physical world by means of holographic imaging, without the need to print out the confrontation disturbance image, which is beneficial to improve the attack success rate of the physical world confrontation sample, and It can realize the corresponding adjustment of the confrontation pattern with the adjustment of the face, and improve the matching degree between the confrontation pattern and the face in the obtained target confrontation sample.
Owner:BEIJING REALAI TECH CO LTD
A Method for ECC Algorithm Selected Plaintext Side Channel Energy Analysis in P Domain
ActiveCN103441846BEfficient analysisEasy to analyzeKey distribution for secure communicationUser identity/authority verificationPlaintextAlgorithm
The invention provides a chosen plaintext side channel energy analysis method for an ECC algorithm of a P domain, and relates to the filed of cryptographic algorithm implementation, side channel energy analysis and the like. To carry out side channel energy analysis on implementation of non-defense methods and defense methods of the ECC algorithm, the novel side channel energy analysis method of an elliptic curve on a prime field on the basis of chosen plaintext is provided, so that an energy consumption difference of multiply operation of a scalar in the ECC algorithm is produced, and secret key information is obtained. According to the technical scheme, the method includes the following steps: (1) energy tracks of two sets of kP operations are collected; (2) side channel energy analysis is carried out based on the energy tracks obtained in the step (1) to recognize hidden point add operations; (3) different portions in the point add operations are mapped to the energy tracks to carry out side channel energy analysis, and a secret key sequence of k is concluded. The method provides a theoretical basis for implementation of chosen plaintext side channel energy analysis for the ECC algorithm of the P domain.
Owner:国家密码管理局商用密码检测中心
Adversarial sample dynamic generation method and device, electronic equipment and storage medium
ActiveCN114419704AAvoid the impact of attack success rateImprove attack success rateCharacter and pattern recognitionMachine learningComputer graphics (images)Holographic imaging
The invention relates to an adversarial sample dynamic generation method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring a first face image of a first user in real time; performing target detection and tracking on the first face image, and generating a candidate frame for marking a face in the first face image; adjusting the target confrontation pattern projected on the holographic film based on the candidate frame to generate a target disturbance image; and obtaining a target confrontation sample, wherein the target confrontation sample comprises the first face image and the target disturbance image. According to the method and the device, the anti-disturbance image of the digital world displayed in the electronic equipment can be converted into the real physical world in a holographic imaging manner, and the anti-disturbance image does not need to be printed, so that the attack success rate of the physical world anti-disturbance sample can be improved; and the confrontation pattern can be correspondingly adjusted along with the adjustment of the face, so that the matching degree between the confrontation pattern and the face in the obtained target confrontation sample is improved.
Owner:BEIJING REALAI TECH CO LTD
Method and device for generating small adversarial patches
ActiveCN112241790BSmall sizeReduced legibilityCharacter and pattern recognitionNeural architecturesFeature extractionAlgorithm
A small confrontation patch generation method and device, by randomly initializing the confrontation patch image, adding the initialized confrontation patch image to the selected pasting area on the target object in the training data to make a confrontation sample; sending the confrontation sample into the depth The learning model performs adversarial feature extraction, and the benign samples without adversarial patch images are sent to the deep learning model for benign feature extraction; the adversarial features and benign features are jointly input into the feature enhancement loss function for loss calculation, and the loss result is obtained; It is added to the model loss function, and the pixel value of the adversarial patch is updated by the optimizer after backpropagation; after a preset number of iterations, the adversarial patch makes the deep learning model output the wrong result, and the adversarial patch processing process is ended. The invention can make the size of the confrontation patch in the physical world smaller, reduce the production cost, reduce the identifiability of the confrontation patch, and make it easier to break through the detection-based defense method.
Owner:BEIJING REALAI TECH CO LTD
Rotation-robust image adversarial example generation in the physical world
ActiveCN114332446BGuaranteed rotation robustnessRobust to rotationCharacter and pattern recognitionNeural architecturesAlgorithmAttack
The invention relates to an image confrontation sample generation method with rotational robustness in the physical world, and relates to the technical field of artificial intelligence security. The main steps include: 1. Initialize the algorithm parameters and image preprocessing to obtain the current adversarial sample; 2. Use the current adversarial sample to rotate to obtain the rotated adversarial sample; 3. Determine whether the iteration termination condition is met, if yes, output the final adversarial sample and perform step 7 , otherwise go to step 4; 4. Calculate the rotation-invariant joint gradient matrix; 5. Perform mean filtering on the rotation-invariant joint gradient matrix; 6. Update the current adversarial sample, and return to step 23; 7. Use the final result in the real physical world Test against adversarial samples and observe the effect of adversarial attacks under different rotation angles. The confrontation sample generated by the invention has rotation robustness in the physical world, solves the situation that the attack of the confrontation sample fails after rotation, and further improves the attack success rate.
Owner:BEIJING INST OF COMP TECH & APPL
An image adversarial sample generation device and method based on migration
ActiveCN112215292BInquiry is not requiredNo internal parameters requiredCharacter and pattern recognitionNeural architecturesAlgorithmDimensionality reduction
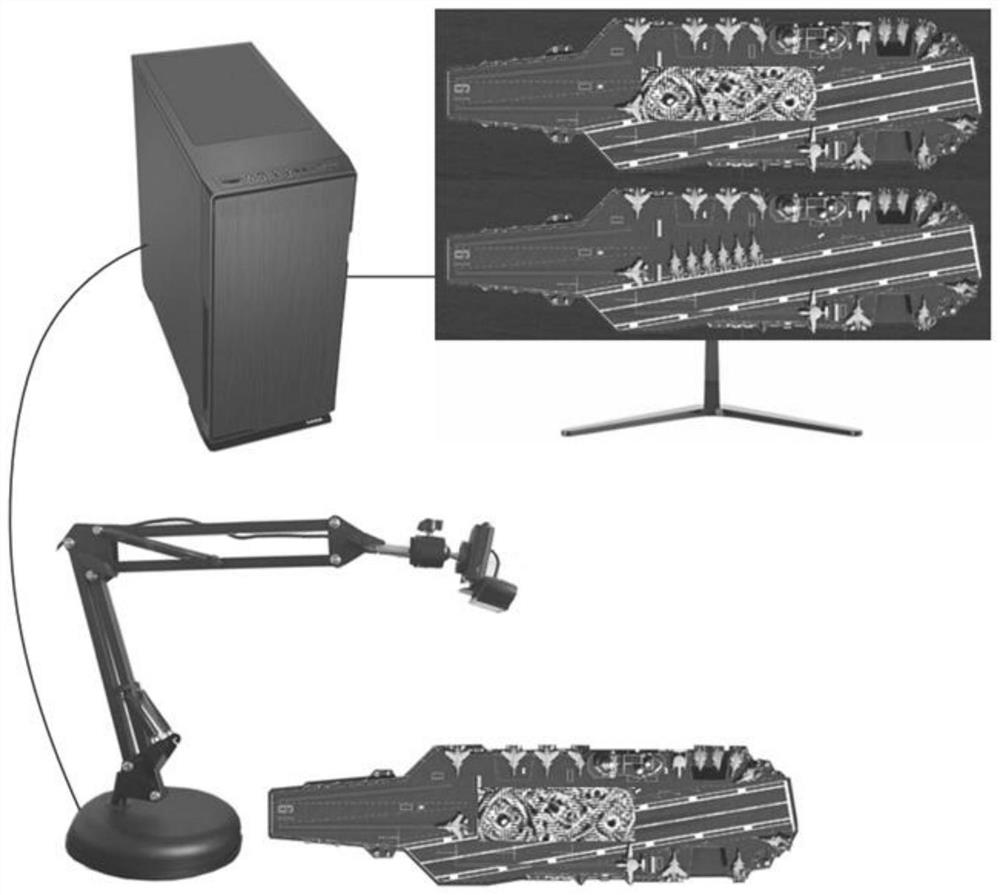
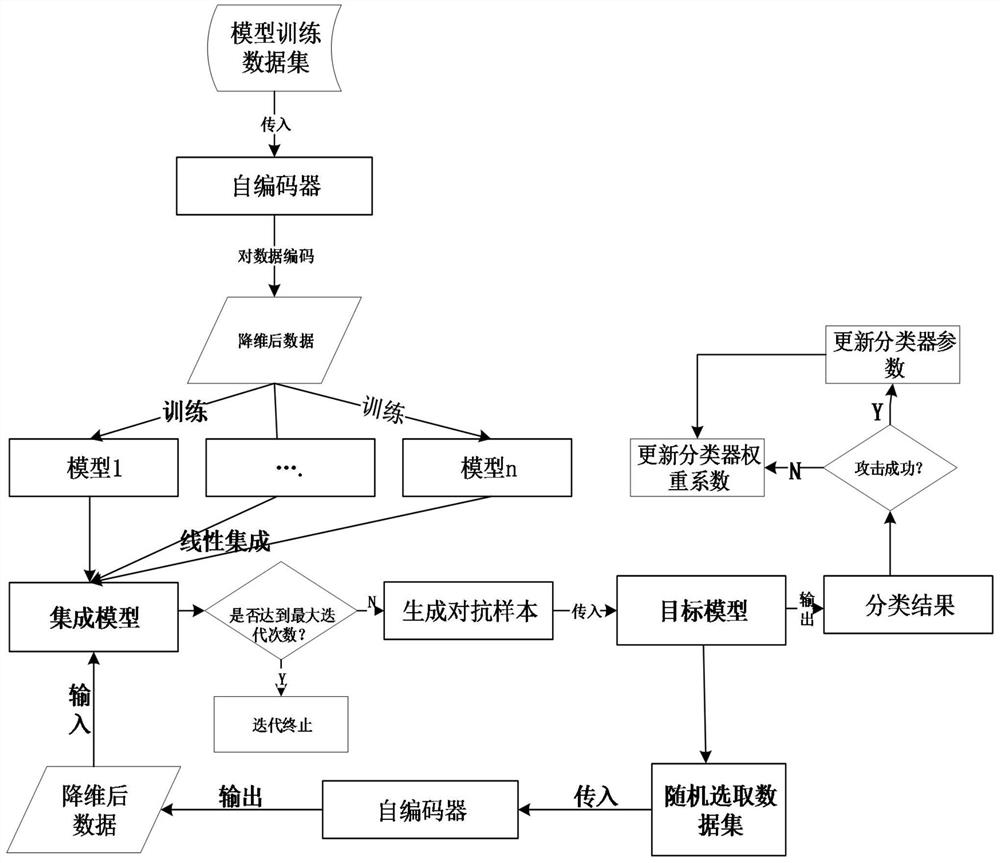
The present invention belongs to the field of computer software, and discloses a device and method for generating image confrontation samples based on migration. Aiming at the problem that a large number of inquiries are required for the above-mentioned black box attack, or the migration is not high, it can be realized under the condition of a small number of inquiries. The attack success rate of adversarial samples is improved. The main scheme is 1) input normal image samples; 2) the image samples are processed by the autoencoder to obtain the dimensionality-reduced data D; 3) sequentially pass into the filtered local image classifier and use the PGD adversarial sample generation algorithm to obtain different Disturb r i ; 4) Linearly integrate these perturbations according to the weight coefficients to obtain the final perturbation f(D); 5) Add the perturbation f(D) to the dimensionally reduced data D and decode it with an autoencoder to obtain the final adversarial samples.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Alternative model automatic selection method, storage medium and terminal for black-box attack
ActiveCN113407939BImprove attack success rateGood alternativeCharacter and pattern recognitionPlatform integrity maintainanceAttackEngineering
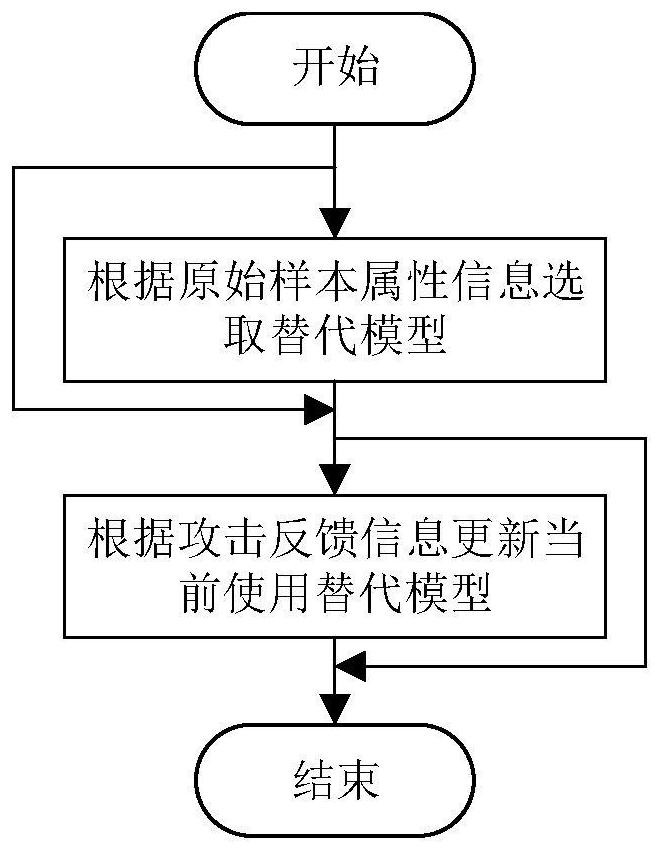
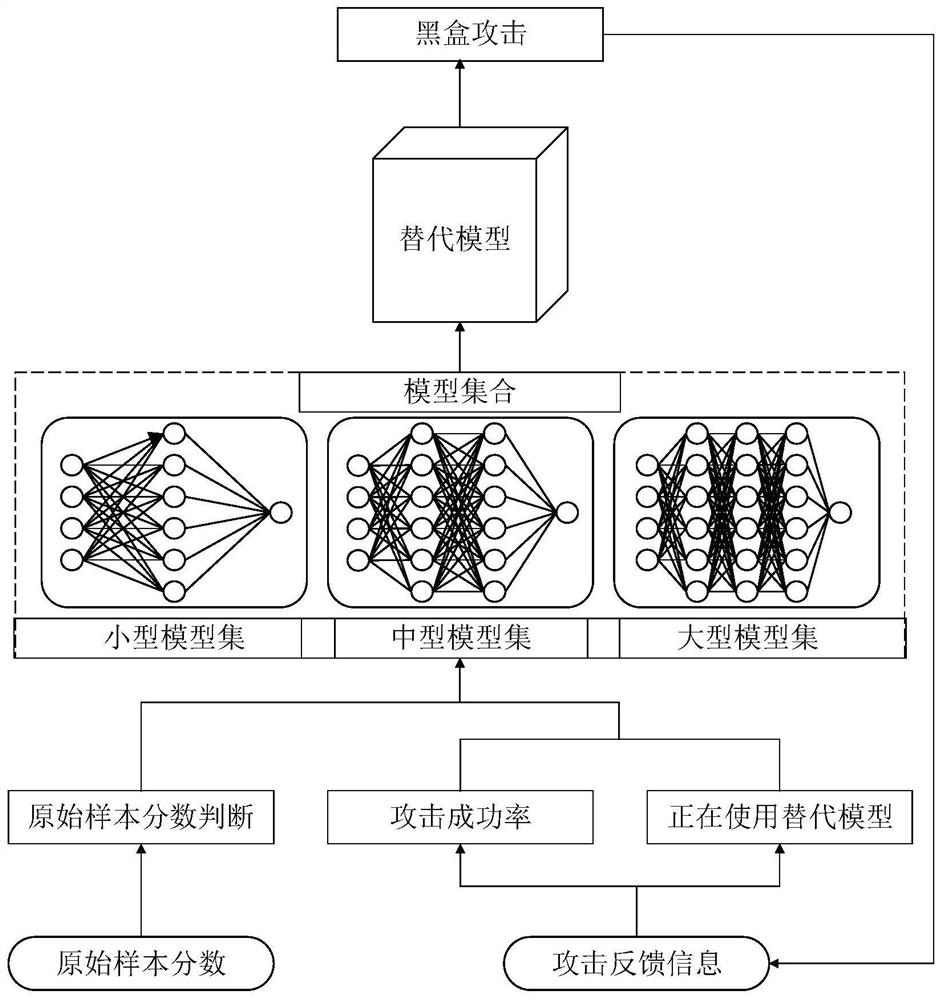
The invention discloses a method, a storage medium and a terminal for automatically selecting an alternative model for black-box attack, belonging to the technical field of deep learning. The method includes: selecting an alternative model in a neural network model according to original sample attribute information, and / or, according to Attack Feedback Updates currently use alternative models. The present invention selects an alternative model with a high degree of matching with the current black-box model according to the original sample attribute information that is related to the complexity of the black-box model, and / or updates the currently used alternative model through attack feedback information, so as to ensure that after the selection or update The surrogate model can exert excellent surrogate performance, and the generated adversarial samples have a high attack success rate in black-box attacks, which is conducive to promoting the current research on neural network model security.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com