Safe access method of sensitive data
A sensitive data, secure access technology, applied in digital data authentication, digital data protection, electronic digital data processing, etc., can solve problems such as data leakage, database breach, sensitive data security loopholes, etc. The effect of incognito access, compromise or reduced risk of being attacked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The embodiments of the present invention are described in detail below. This embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following implementation example.
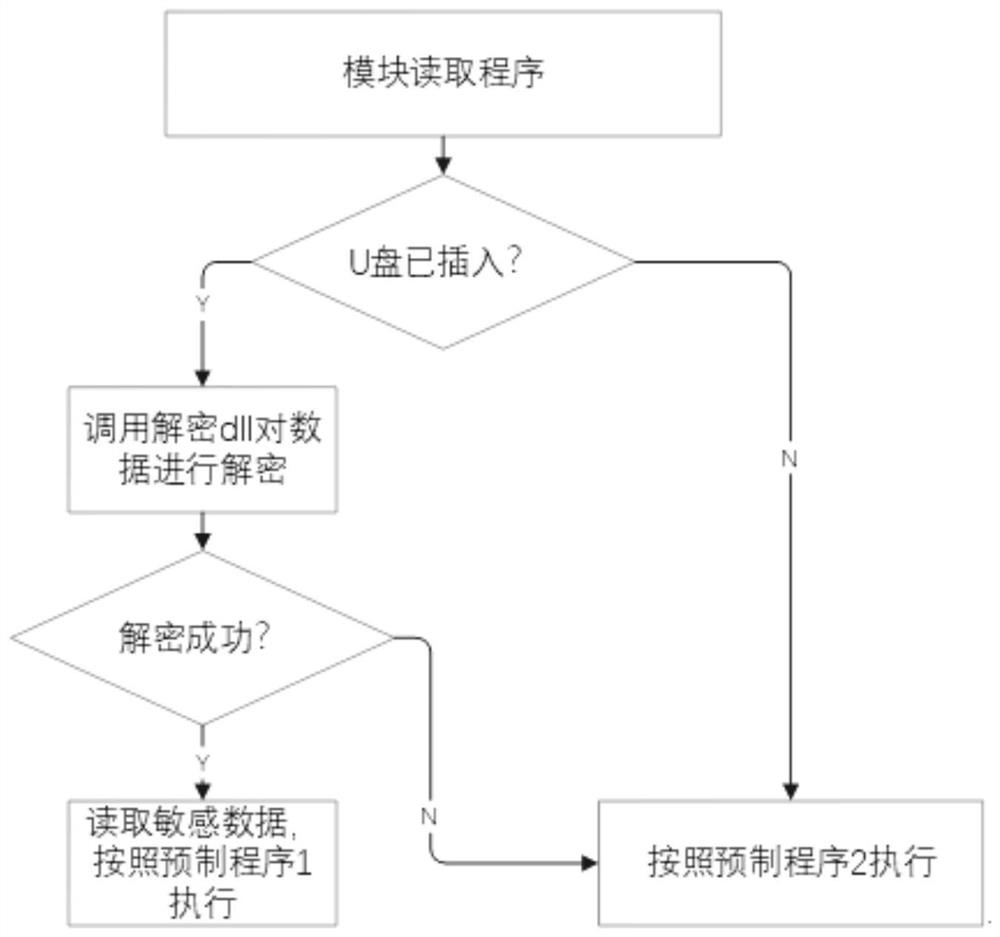
[0031] Such as figure 1 As shown, this embodiment provides a technical solution: develop a software for personnel genealogy analysis, that is, when a person is clicked, the family tree relationship diagram of the person is dynamically displayed, and when each person is right-clicked in the figure, Display the basic information of the person: name, ID number. Name and ID number are sensitive data used by this module. There is a unique custom ID for each person in the system, and the personnel data sequence PSeq (ID, name, ID number) is established and stored in the mobile medium, and the personnel information tabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com