Data transmission control method, key management method, configuration method and related devices
A technology for data transmission control and control devices, which is applied in the field of data security and can solve problems such as reducing the performance of encrypted virtual machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
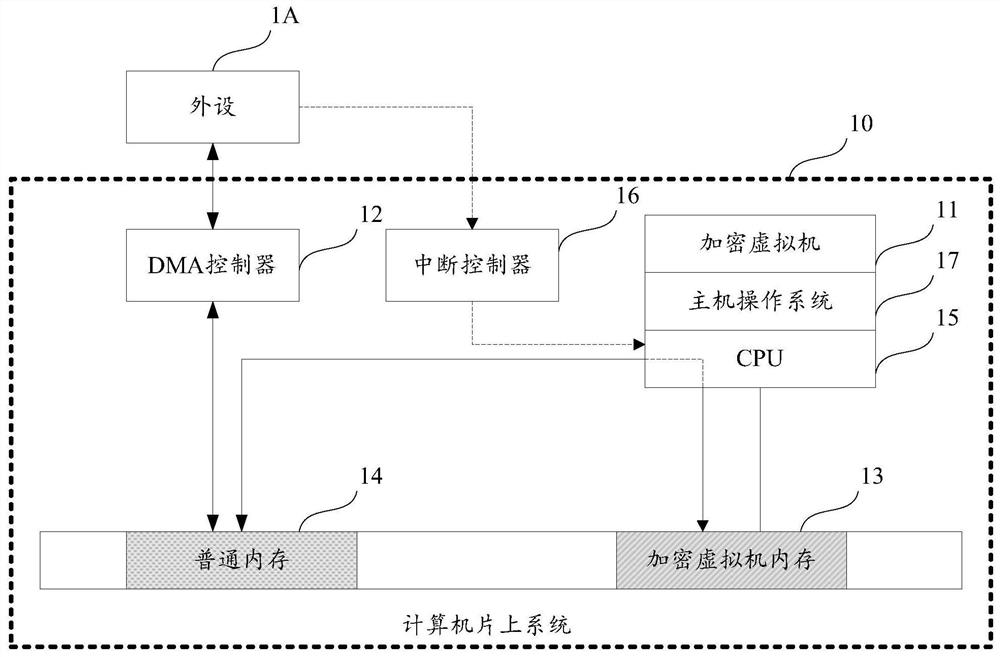
[0099] Computer peripherals refer to hardware devices connected outside the computer host, referred to as peripherals, which play the role of transmission, transfer and storage of data and information, and are an important part of the computer system.
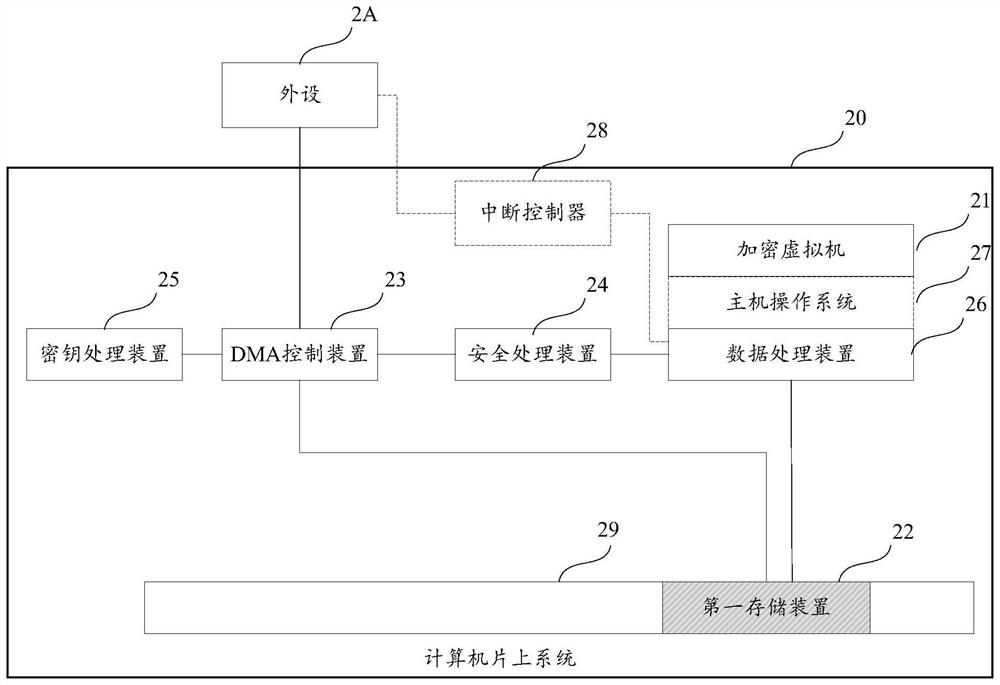
[0100] As mentioned in the background section, at present, when dealing with DMA data interaction between encrypted virtual machines and peripherals, the Bounce Buffer mechanism is generally used, that is, the encrypted virtual machine allocates an additional piece of ordinary memory, that is, non-encrypted memory, as a temporary memory for DMA transmission. The DMA control device can directly access the ordinary memory, and the CPU copies data between the ordinary memory and the encrypted virtual machine memory.
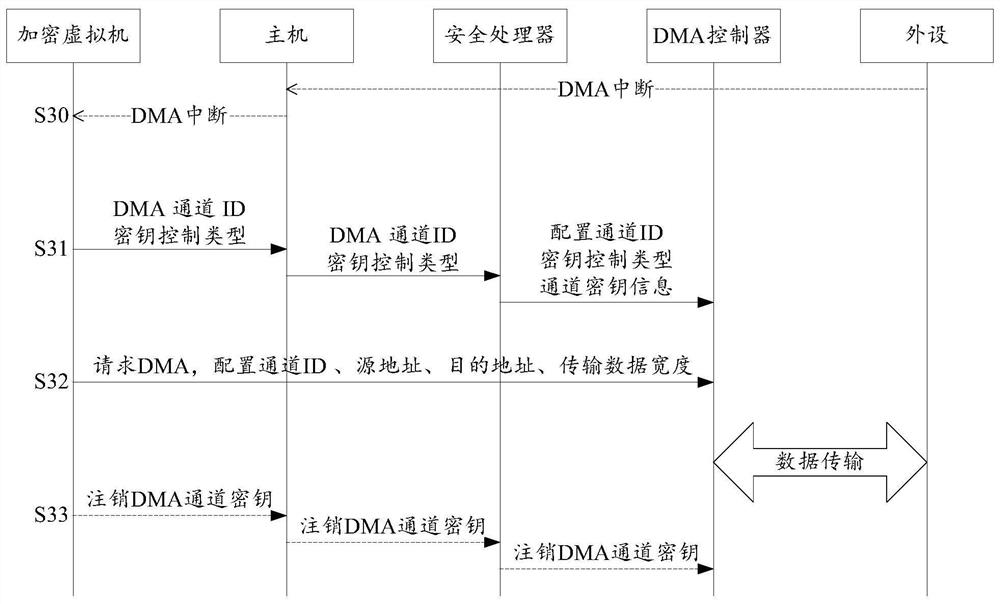
[0101] In order to more clearly illustrate the working principle of the above-mentioned Bounce Buffer mechanism, the structure and data interaction process of a DMA transmission system will be described below.
[010...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com