A password management method and system suitable for zero trust network
A password management and key management technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of high cost and inconvenient use, and achieve the effect of convenient and flexible use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
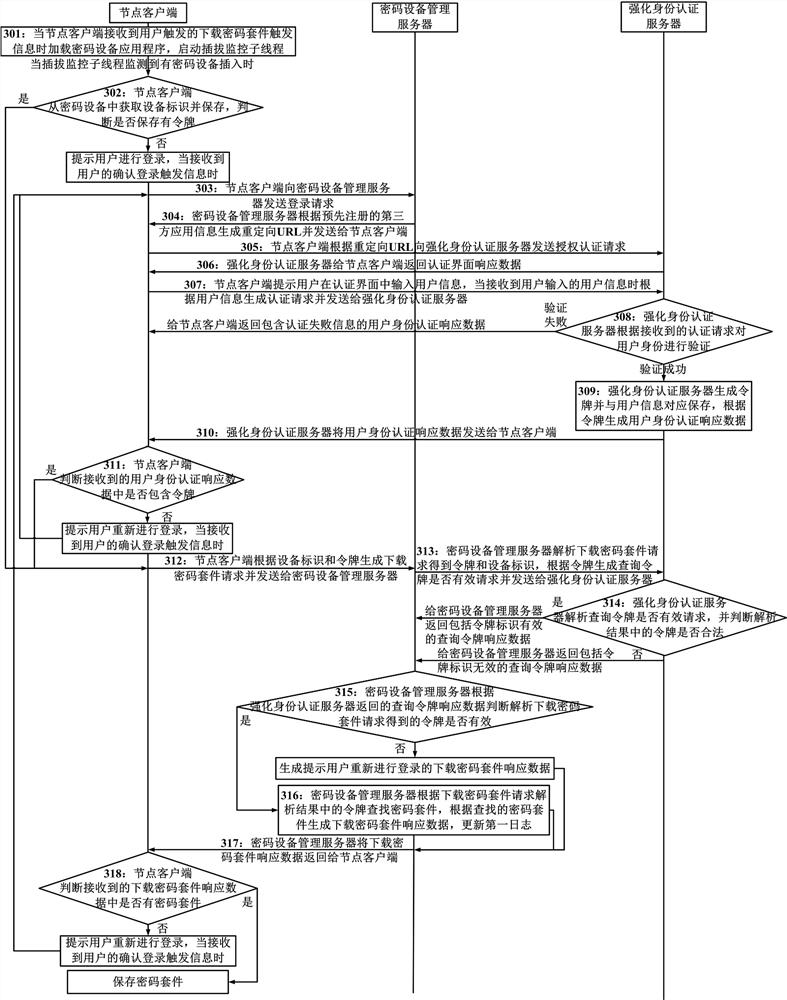
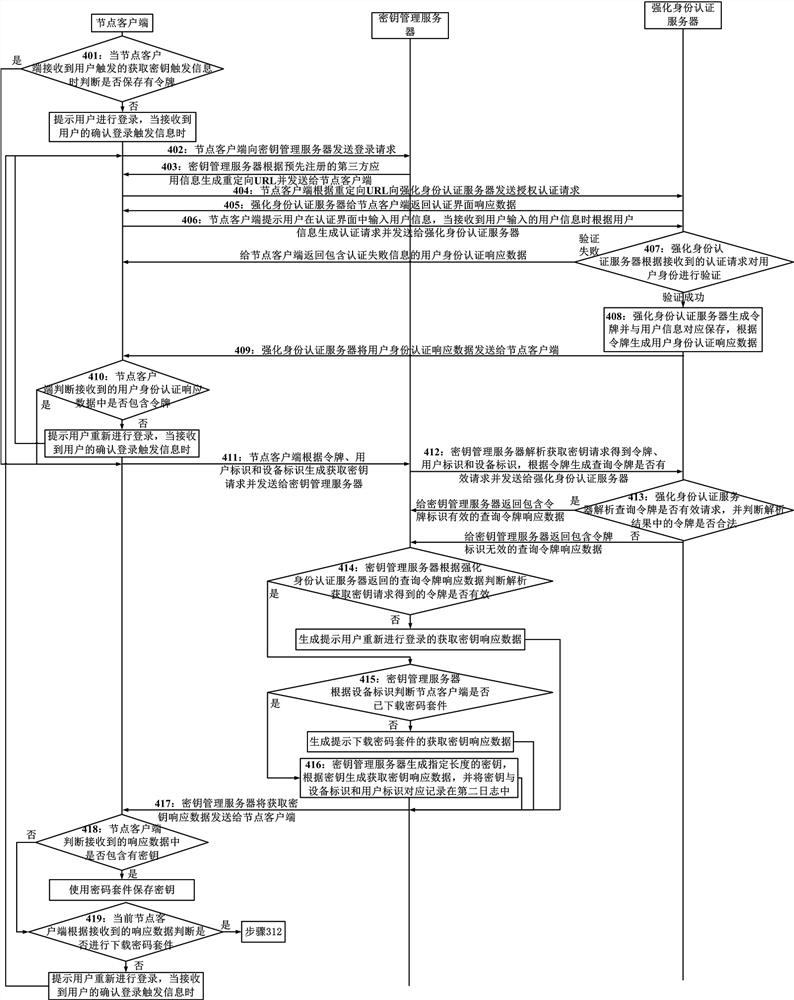
[0050] Embodiment 1 of the present invention provides a password management method suitable for a zero-trust network. The method of this embodiment is applied to a system including a password device management server, a key management server, an enhanced identity authentication server, and a node client. The node client includes Multiple, and multiple clients can work simultaneously, the method includes:
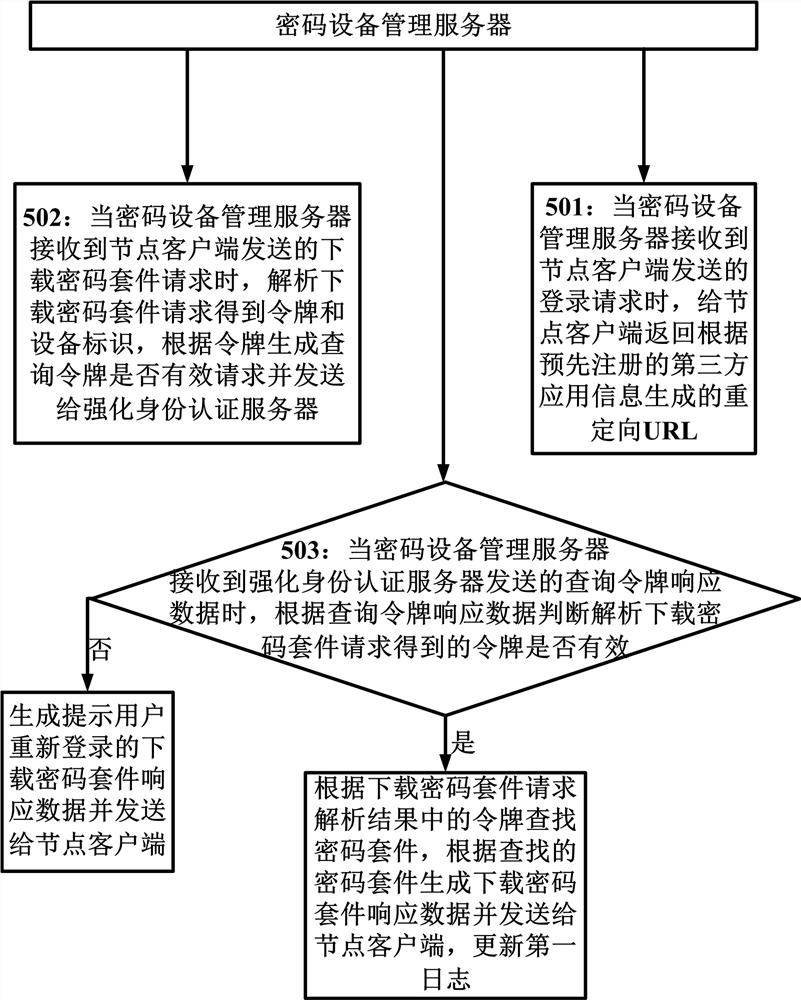
[0051] When the cryptographic device management server receives the request for downloading the cipher suite sent by the node client, it sends a query token valid request containing the token obtained by parsing the request for downloading the cipher suite to the enhanced identity authentication server, and according to the query returned by the enhanced identity authentication server The token response data judges whether the token is valid. If the token is valid, the cipher suite is retrieved according to the device ID obtained by parsing the download cipher suite request, ...
Embodiment 2
[0159] Embodiment 2 of the present invention provides a password management system suitable for zero-trust networks, such as Figure 6 As shown, the system includes a cryptographic device management server 61, a key management server 62, an enhanced identity authentication server 63 and multiple node clients 64; multiple node clients in this system can work simultaneously;
[0160] Among them, the node client 64 includes: a first sending module 641 and a first receiving module 642; the cryptographic device management server 61 includes: a second receiving module 611, a second sending module 612, a first judging module 613, a retrieval update module 614, The first generating module 615 and the first searching module 616; the key management server 62 includes: the third receiving module 621, the third sending module 622, the second judging module 623, the second generating module 624 and the third generating module 625; strengthening The identity authentication server 63 include...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com