Electronic data relation chain generation system and method based on social network data chain
An electronic data and social network technology, applied in digital data authentication, digital data protection, data processing applications, etc., can solve problems such as no way to start, data service providers can not clearly know, increase the amount of data processing, etc., to ensure independence , avoid illegal intrusion and data pollution, and ensure the effect of integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In the following, the invention will be further described in conjunction with the accompanying drawings and specific embodiments.
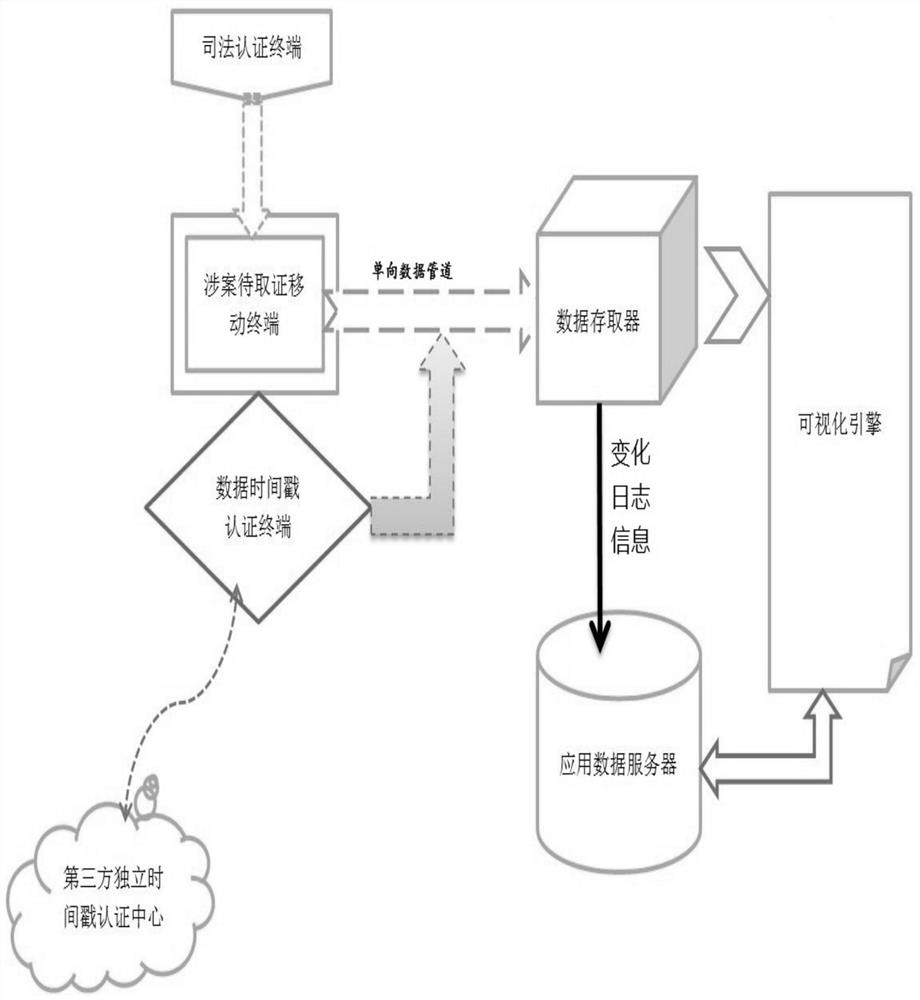
[0052] see figure 1 , is a module architecture diagram of an electronic data relationship chain generation system based on a social network data chain according to an embodiment of the present invention.
[0053] figure 1 The electronic data relationship chain generating system based on the social network data chain of an embodiment of the present invention shown in an embodiment of the present invention includes the following components:
[0054] The judicial authentication terminal is used to generate a judicial authentication login signal, and the judicial authentication login signal is generated based on the suspect information of the mobile terminal involved in the case to be obtained;
[0055] The data timestamp authentication terminal is used to connect to a third-party independent timestamp authentication center, and is used to re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com