Policy hidden type data access control method based on block chain
A technology of data access control and access control tree, applied in the fields of access control and cloud computing, can solve problems such as privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
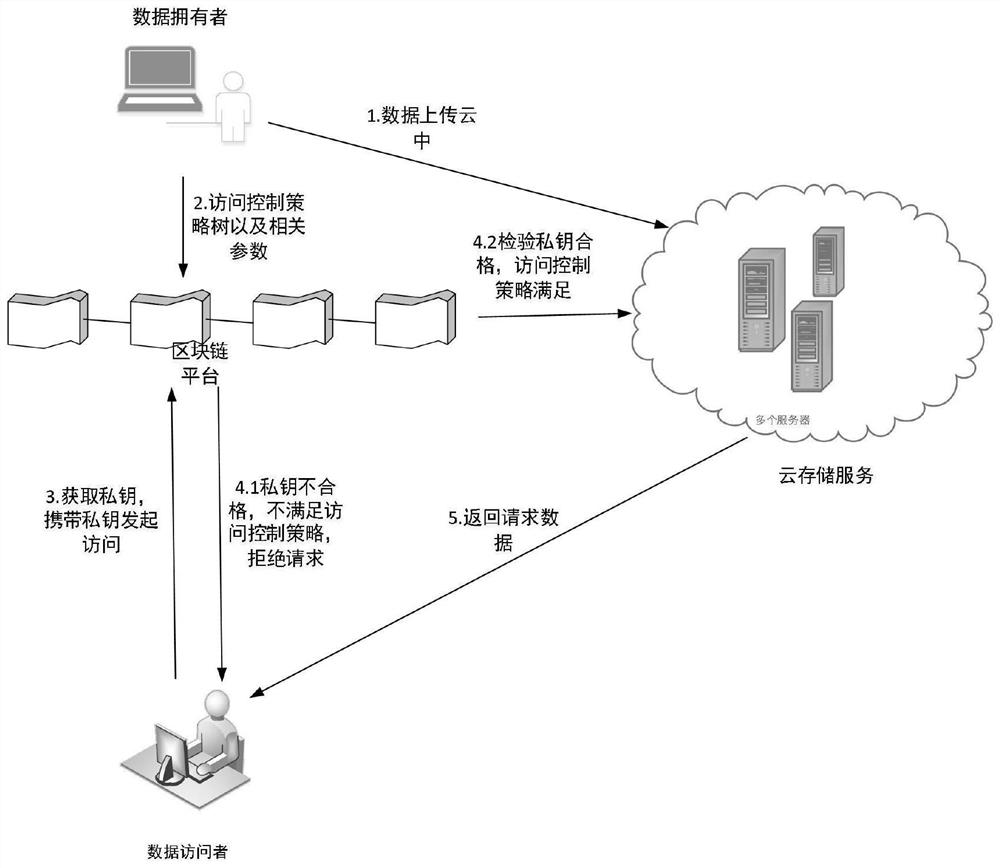
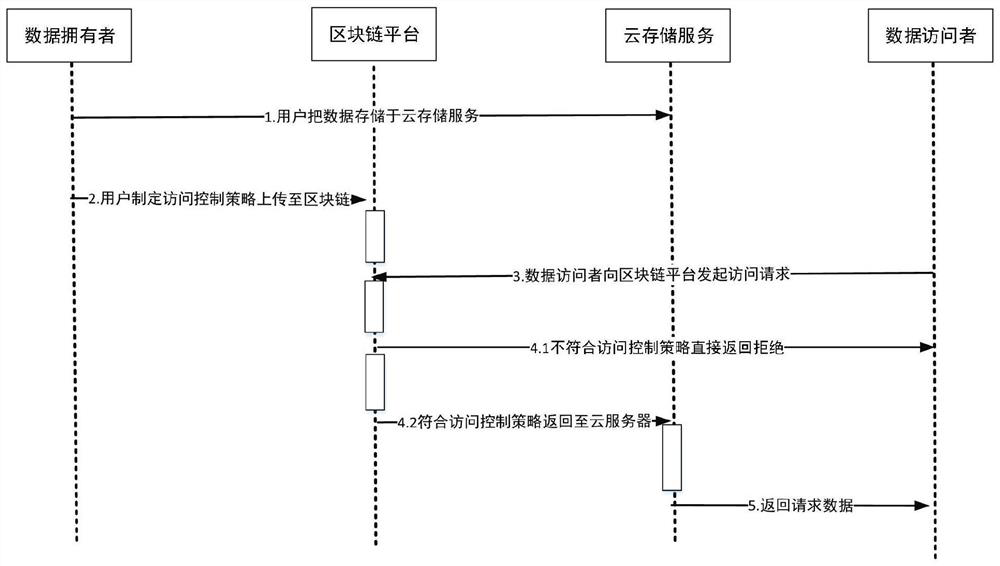
[0055] The specific implementation process of the blockchain-based policy-hidden data access control method described in the present invention is as follows: figure 2 shown, including the following steps:
[0056] Step 1: Preparation phase.
[0057] Step 1.1: The blockchain platform executes the group generation algorithm to generate relevant public parameters, see formula (1) for details.
[0058] 1) Assign corresponding attribute components to each attribute in the platform.
[0059] 2) Publish public parameters to the blockchain platform.
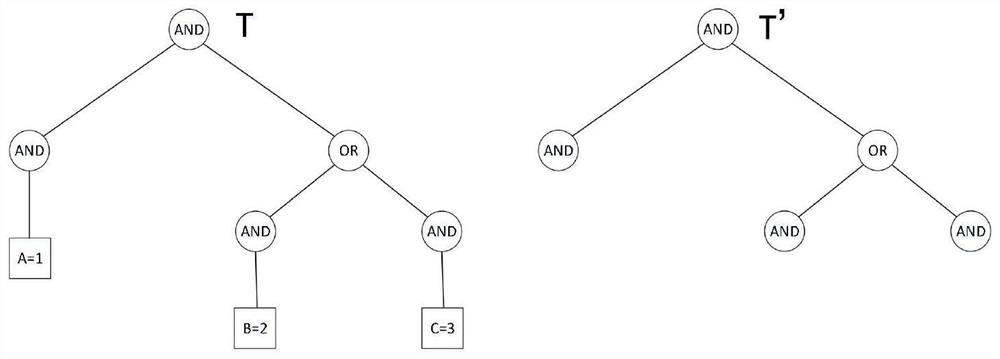
[0060] Step 1.2: The data owner constructs the access control tree and the corresponding user parameters, see formula (2-6) for details.
[0061] 1) According to the encrypted data stored in the cloud server.
[0062] 2) According to the public parameters released by the blockchain platform, select ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com