Password-free authentication method and system based on blockchain, terminal and storage medium
An authentication system and authentication method technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as encryption method leakage, appkey and public key leakage, data leakage, etc., to improve security and avoid Easy to leak and logically coupled to reduce the effect of unavailability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059] The secret-free authentication method based on block chain of the present invention comprises:
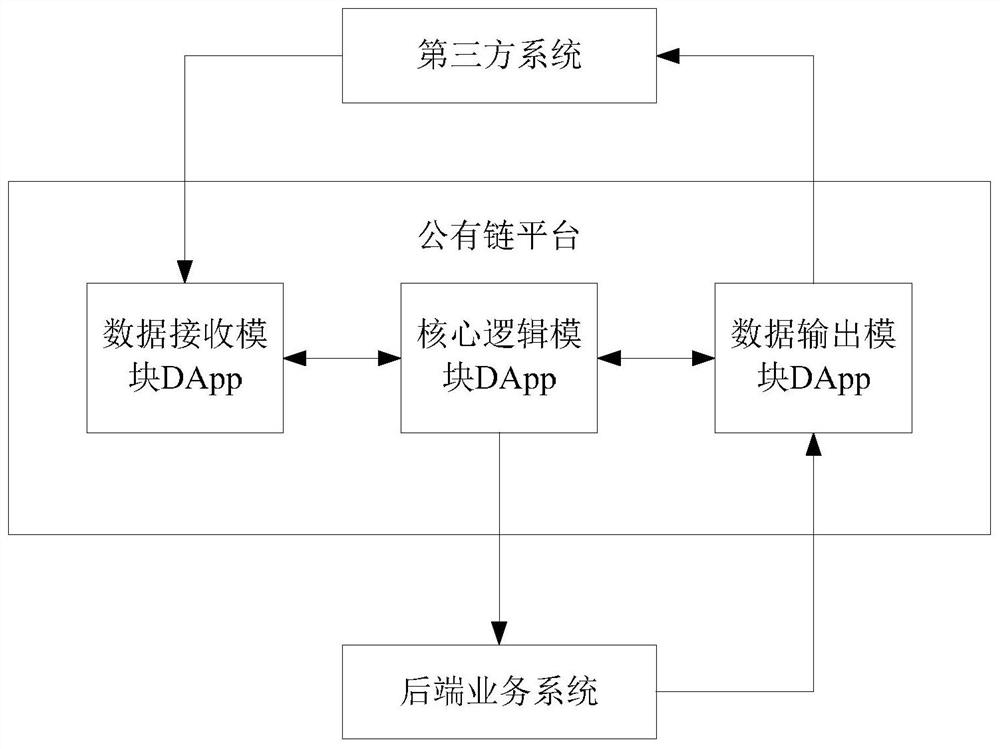
[0060] Establish a password-free authentication system, divide the password-free authentication system into functional modules and deploy them on DApps on the public chain platform. Since the security of Ethereum is higher than the fault tolerance and easy recovery of privatized deployment, the present invention uses Ethereum as a public chain platform.
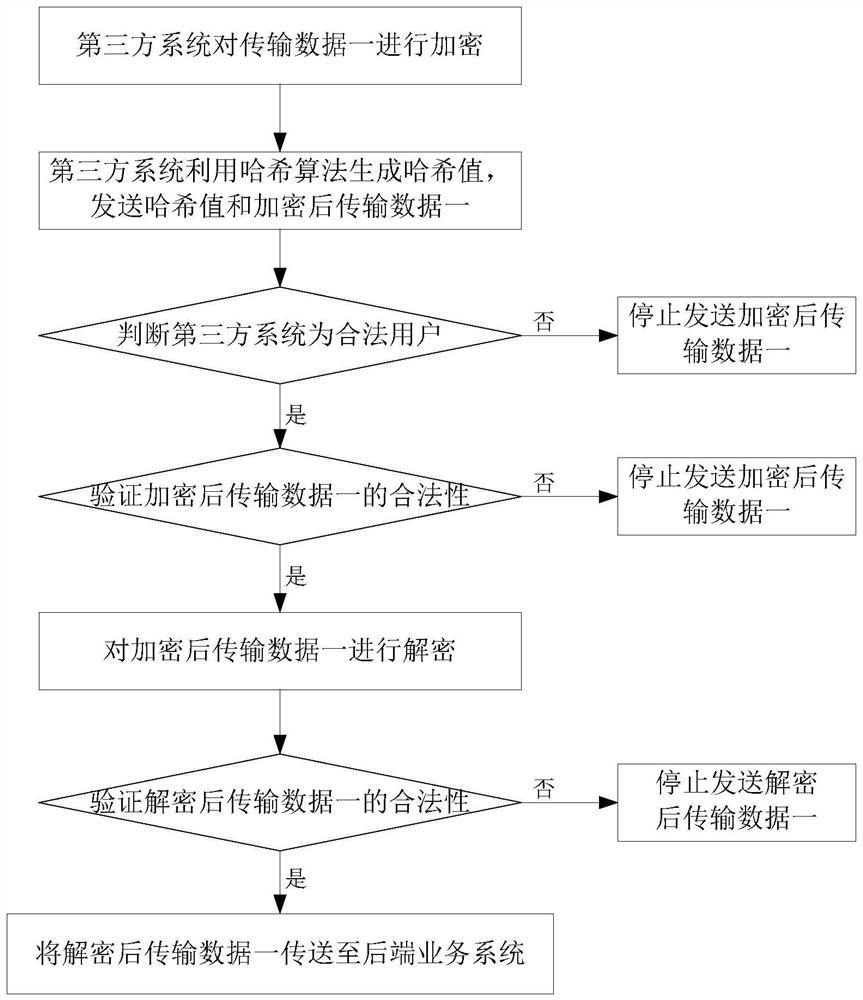
[0061] like figure 2 As shown, when the third-party system sends transmission data one to the back-end business:
[0062] (1) The third-party system uses the blockchain hash SHA-256 algorithm to encrypt the transmitted data; the third-party system performs a complete legality check on the encrypted transmitted data, and uses the hash algorithm to generate a 256-bit hash value, and send the hash value and encrypted transmission data to the password-free authentication system.
[0063] (2) The password-free authentication...
Embodiment 2
[0073] In order to implement the blockchain-based password-free authentication method described in Embodiment 1, this embodiment provides a blockchain-based password-free authentication system, which includes:
[0074] The data receiving module DApp is used to receive the encrypted transmission data of the third-party system, and identify the third-party system through the white list to determine whether the third-party system is a legitimate user; The system encrypts and transmits data for legality verification.
[0075] The core logic module DApp is used to decrypt the legally encrypted transmitted data 1, and obtain the decrypted transmitted data 1; the password-free authentication system verifies the legality of the decrypted transmitted data 1.
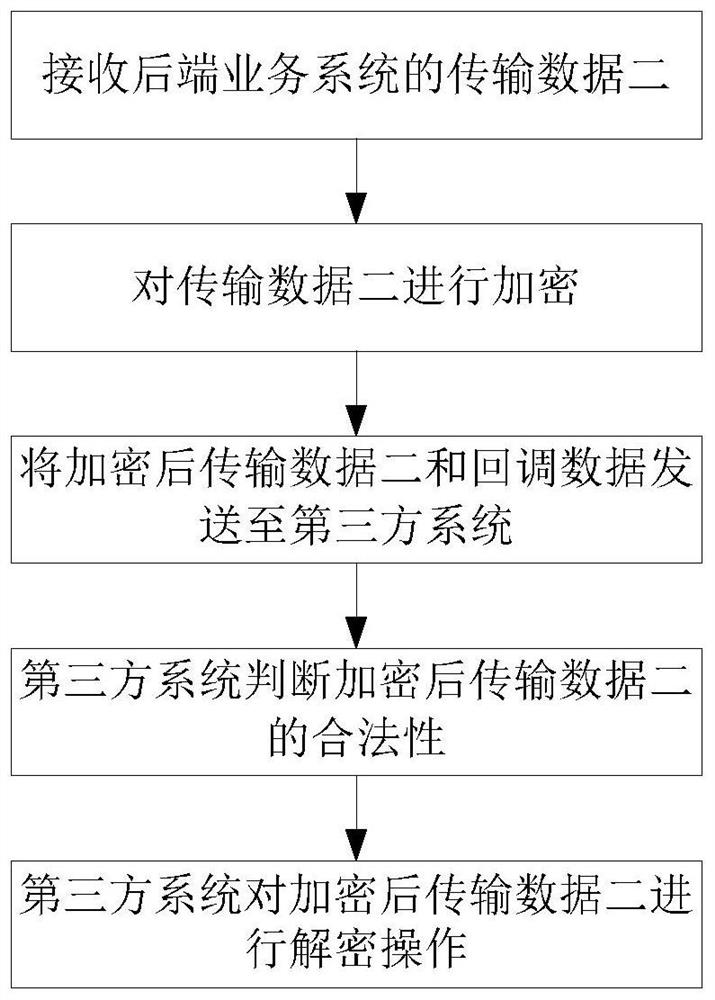
[0076] The data output module DApp is used to transmit the legally decrypted transmission data 1 to the back-end business system; and is used to receive and encrypt the transmission data 2 of the back-end business system, and sen...
Embodiment 3
[0079] In this embodiment, a password-free authentication terminal includes a processor and a memory for storing executable programs of the processor, and is characterized in that it implements the blockchain-based password-free authentication method described in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com