Safe remote access system and method
A remote access and security technology, applied in the field of secure remote access systems, can solve problems such as malware theft, single pass, information leakage, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
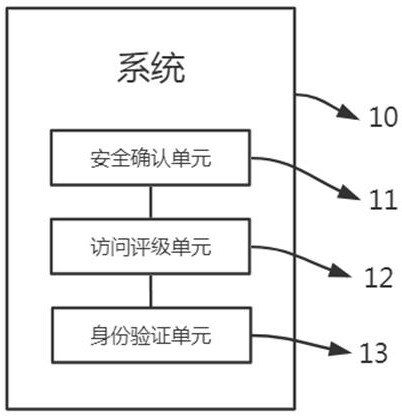
[0073] figure 2 A structural block diagram of the secure remote access system 10 is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown:
[0074] In an embodiment of the present invention, the system 10 includes:
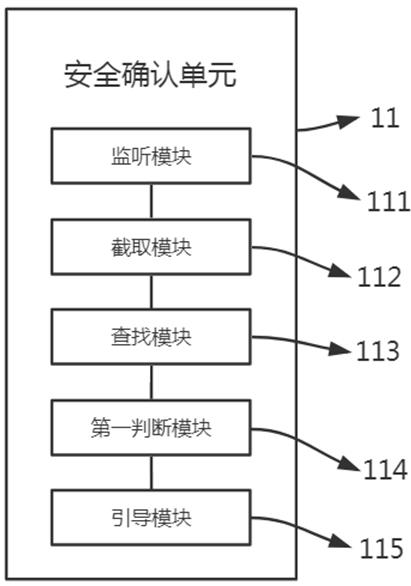
[0075] The security confirmation unit 11 is configured to receive the access request, determine the authority of the sender of the access request, and establish a connection channel based on the authority of the request sender;
[0076] The function of the security confirmation unit is to determine the source of the access. The sender of the access request here is the software, not the user. The purpose is to detect the method through which the user conducts remote access, because the purpose of the final access is the same. By restricting the source of access It is very effective and easy to improve security by means of a browser. At present, the stability of the browser is very high, and vari...
Embodiment 2
[0138] Figure 9 A block flow diagram of a secure remote access method is shown, and for ease of description, only parts related to this embodiment are shown:
[0139] In an embodiment of the present invention, the method includes:
[0140] Step S1: receiving the access request, determining the authority of the sender of the access request, and establishing a connection channel based on the authority of the sender of the request;
[0141] The step S1 is realized by the security confirmation unit 11;
[0142] Step S2: Acquiring the purpose of access, and judging the level of the purpose of access;
[0143] The step S2 is implemented by the access rating unit 12;
[0144] Step S3: Obtain verification information based on the level of the access purpose, and send access content based on the verification information;
[0145] The step S3 is realized by the identity verification unit 13;
[0146] further, Figure 10 A sub-flow block diagram showing a secure remote access meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com