Sequence cipher encryption system key updating method based on hash function
A key update and hash function technology, applied in the fields of communication information security and cryptography, can solve the problems of suspending decryption operations and troublesome key security transmission, achieving high security, fast key update speed, and avoiding troubles. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
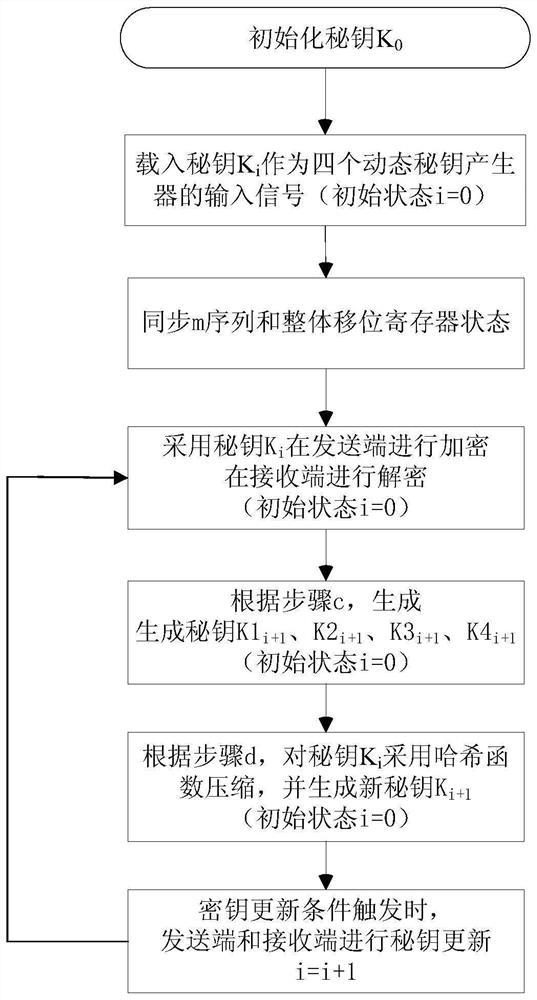
[0024] Such as image 3 As shown, a hash function-based serial cipher encryption system key update method, in this method both encryption and decryption use the same key stream generator EC, and has four dynamic key generators, through the The hash function calculation is performed on the secret key sequence to generate a new secret key sequence to realize the self-renewal of the sequence password.
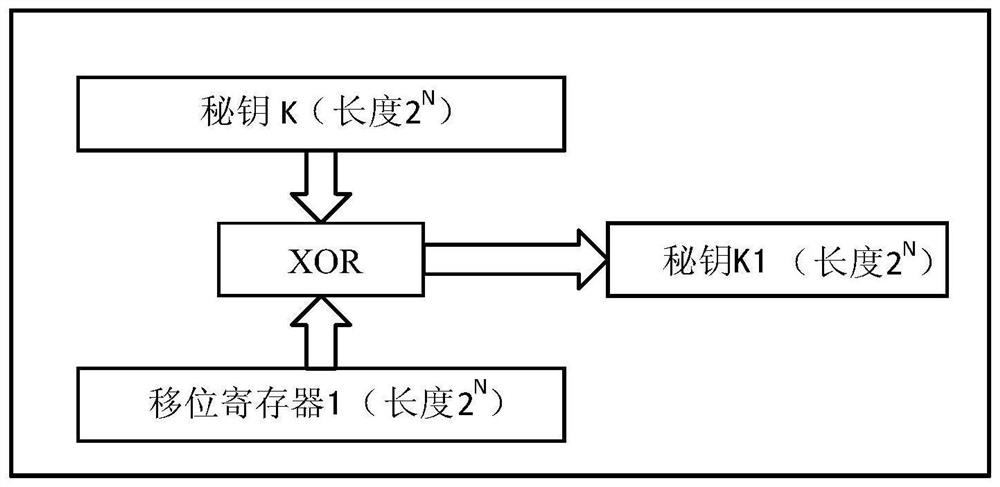
[0025] The principle of dynamic key generator 1 is as follows: figure 1 As shown, the other three dynamic key generators are the same. in:
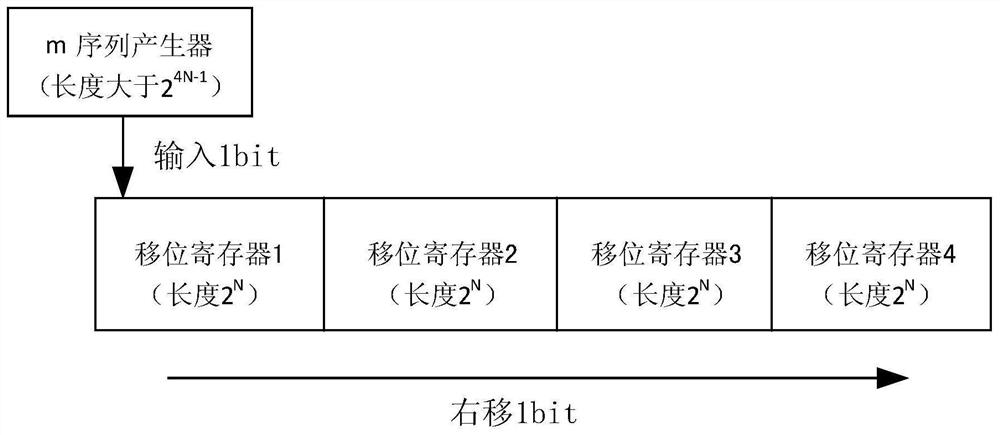
[0026] a. Dynamic secret key generation input signal description: each dynamic secret key generator inputs the current i-th working secret key K i . Key generator 1 has length 2 N long shift register 1; key generator 2 has length 2 N long shift register 2; secret key generator 3 has a length of 2 N lon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com