ETL methods, apparatus, devices and media based on data pipelines and security sandboxes
A data pipeline and security sandbox technology, applied in the computer field, can solve problems such as large performance loss, low ETL transmission speed, and packet conflict, and achieve the effect of improving collection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] like Figure 5 As shown, this embodiment provides an ETL method based on a data pipeline and a security sandbox, including the following steps:
[0043] S1. Start the actuator through the startup module;
[0044] S2. The executor receives the task message information of the front end, extracts the component codes corresponding to the extraction, conversion and loading according to the task message information, and instantiates the extraction component, the conversion component and the loading component respectively according to the component codes, and A data pipeline between the extraction component, the conversion component and the loading component is constructed through a lock-free memory queue, thereby constructing an ETL topology instance; wherein,
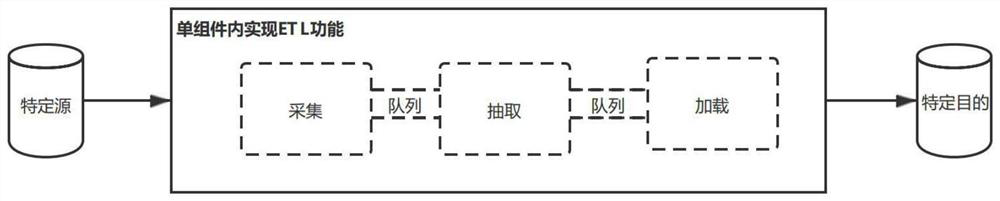
[0045] The extraction component, the conversion component and the loading component are formed by decoupling a single component that realizes the ETL function, are independent and reusable components, and can be free...
Embodiment 2
[0055] like Figure 7 As shown, in this embodiment, an ETL device based on a data pipeline and a security sandbox is provided, including:
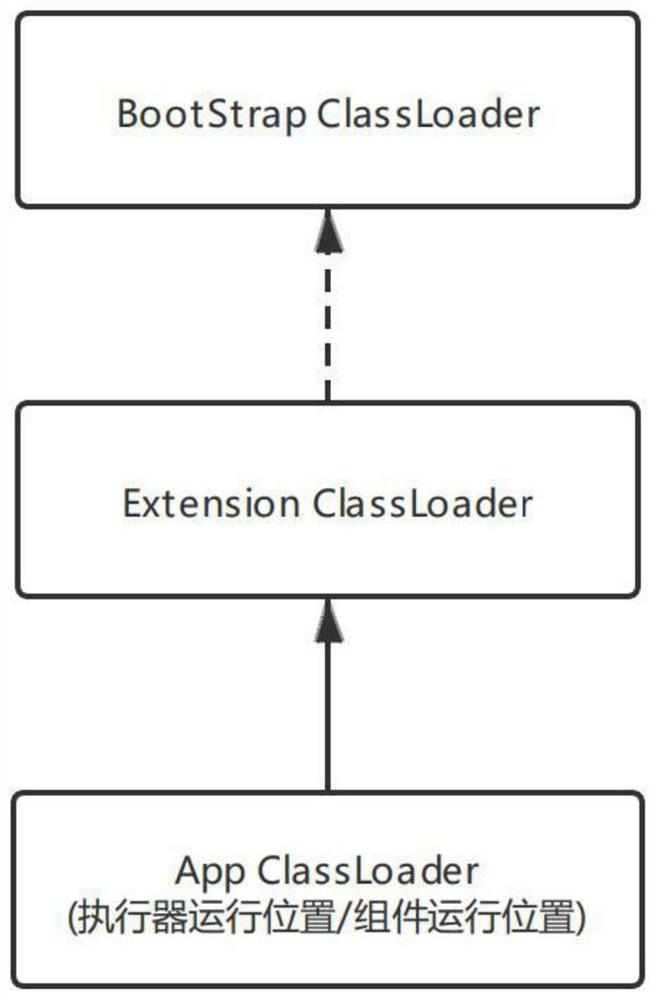
[0056] The startup module is used to start the executor, specifically using the executor ClassLoader to load the executor;
[0057] The executor is used for receiving the task message information of the front end, according to the task message information, extracts the component codes corresponding to extraction, conversion and loading, and instantiates the extraction component, the conversion component and the loading component respectively according to the component codes; And build the data pipeline between the extraction component, the conversion component and the loading component through a lock-free memory queue, thereby constructing an ETL topology instance; wherein, the extraction component, the conversion component and the loading component It is decoupled from a single component that implements the ETL function, is an independen...
Embodiment 3
[0067] This embodiment provides an electronic device, such as Figure 8 As shown, a memory, a processor, and a computer program stored in the memory and running on the processor are included. When the processor executes the computer program, any implementation manner of the first embodiment can be implemented.
[0068] Since the electronic device introduced in this embodiment is the device used to implement the method in the first embodiment of the present application, based on the method introduced in the first embodiment of the present application, those skilled in the art can understand the electronic device in this embodiment. The specific implementation manner and various modifications thereof, so how the electronic device implements the methods in the embodiments of the present application will not be described in detail here. As long as the devices used by those skilled in the art to implement the methods in the embodiments of the present application fall within the sco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com