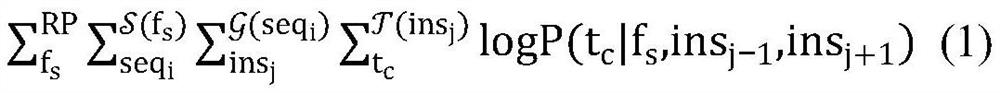Binary code similarity analysis method for vulnerability detection
A binary code and similarity analysis technology, which is applied in the field of binary code similarity analysis for vulnerability detection, can solve the problem of not considering dependency information and basic block semantic information at the same time, and achieve the effect of improving accuracy and coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
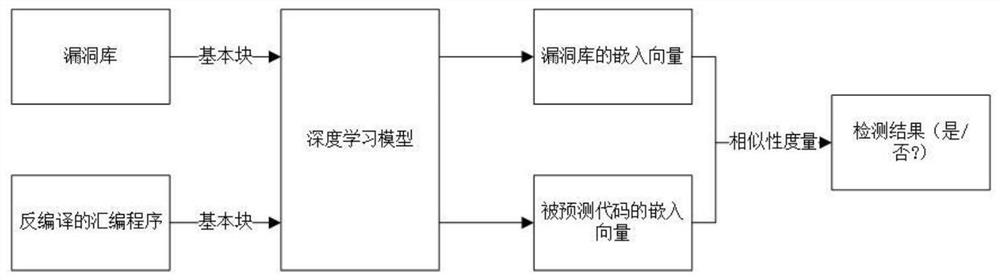
[0030] according to Figure 1-Figure 2 As shown, the present invention provides a binary code similarity analysis method oriented to vulnerability detection, comprising the following steps:
[0031] A binary code similarity analysis method oriented to vulnerability detection, comprising the following steps:
[0032] Step 1: Select the source code vulnerability library; in the step 1, select OpenSSL as the source code vulnerability library.
[0033] Step 2: Compile the code in the source code vulnerability library to form a binary file; the step 2 is specifically: compile the code in the source code vulnerability library into a corresponding binary file through different optimization levels and compilation options.
[0034] Step 3: According to the obtained binary file, train the binary file through the word embedding model to generate an embedded vector of the instruction;
[0035] The step 3 is specifically:
[0036] Step 3.1: Use the word embedding model to train the bina...
specific Embodiment 2
[0048] The purpose of the present invention is to detect whether a given binary file contains the vulnerabilities included in the specified source code vulnerability library. This paper mainly compiles the source code vulnerability database into a binary vulnerability database, uses machine learning methods to detect the similarity between a given binary file and the files in the vulnerability database, and then determines the top K matching vulnerabilities.
[0049] Step 1: Select the source code vulnerability library. In order to detect whether the binary file contains vulnerabilities as much as possible, it is necessary to select a representative and authoritative vulnerability library, which contains common vulnerabilities as much as possible. Therefore, this method selects OpenSSL as this method. Vulnerability library for method experiments.
[0050] Step 2: Compile the code in the source code vulnerability library into corresponding binary files through different optimiz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com