Ad hoc network alarm method and device and machine readable storage medium
An ad-hoc network and machine technology, applied to alarms, instruments, network topology, etc., can solve the problems of untimely feedback of alarm information and inconspicuous alarm effects, and achieve the goal of improving intelligence, improving alarm effects, and ensuring costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
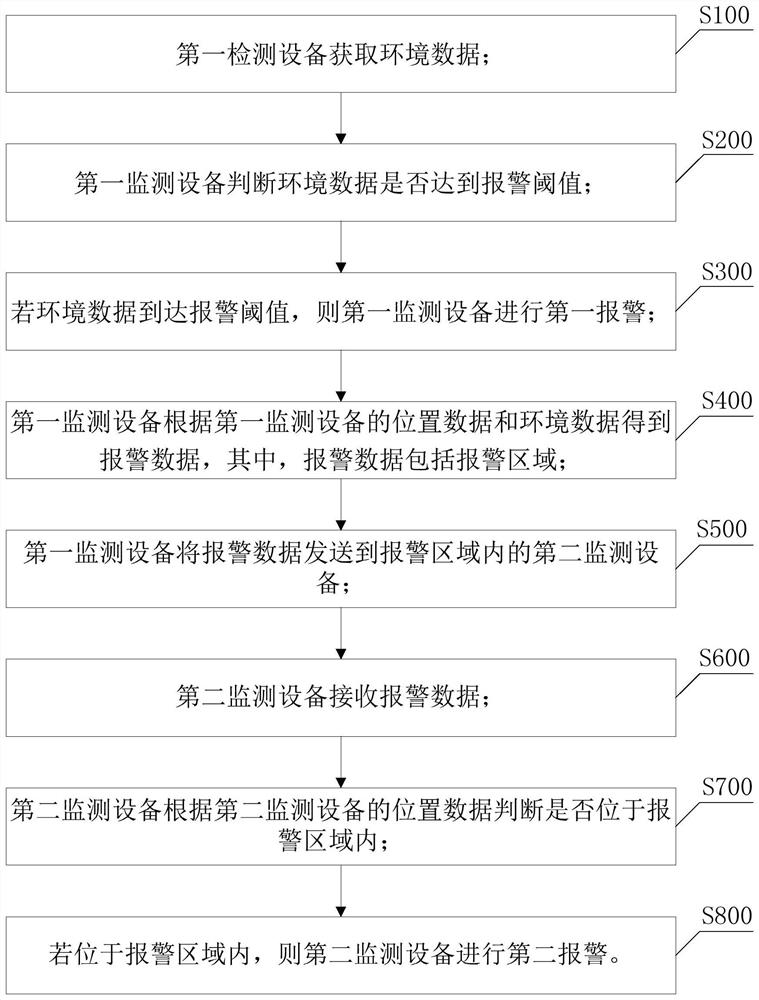
[0063] see figure 1 , figure 1 It is a schematic flowchart of the ad hoc network alarm method provided in Embodiment 1 of the present invention.
[0064] Such as figure 1 As shown, the first aspect of the present invention provides an ad hoc network alarm method. The first monitoring device and the second monitoring device perform an ad hoc network. Both the first monitoring device and the second monitoring device can include various sensors for Monitoring temperature, smoke, various gases, etc., the method includes:
[0065] Executed by the first monitoring device:
[0066] S100. Acquire environmental data.
[0067] Environmental data may include data on temperature, smoke, various gases, and the like. For smoke and various gases, concentration data are usually obtained. Of course, property data of electricity, magnetism, radiation, liquid, solid, etc. may also be included.
[0068] S200. Determine whether the environmental data reaches an alarm threshold.
[0069] S3...
Embodiment approach 2
[0085] Based on implementation mode 1, please refer to figure 2 , figure 2 It is a schematic flowchart of determining an alarm area in the ad hoc network alarm method provided in Embodiment 2 of the present invention.
[0086] Further, as figure 2 As shown, the first monitoring device is a fixed device, then the first monitoring device and at least one second monitoring device conduct an ad hoc network, the location data of the first monitoring device includes the built-in location data of the first monitoring device, and in S400 according to the first The step of monitoring the location data and environment data of the equipment before obtaining the alarm data includes:
[0087] S901. The first monitoring device acquires built-in location data of the first monitoring device.
[0088] Since the first monitoring device is a fixed device, its position coordinates are fixed, so the fixed position coordinates can be built into the first monitoring device. Of course, if the ...
Embodiment approach 3
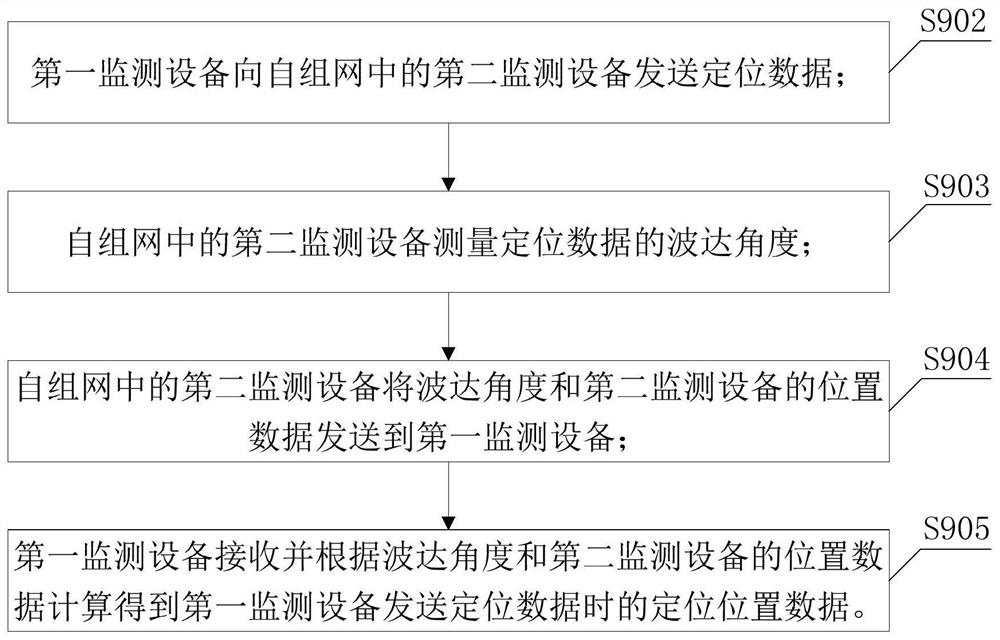
[0091] Based on implementation mode one or two, please refer to image 3 , image 3 It is a schematic flowchart of determining an alarm area in the ad hoc network alarm method provided in Embodiment 3 of the present invention.
[0092] Further, as image 3 As shown, the first monitoring device is a mobile device, then the first monitoring device and at least two second monitoring devices conduct an ad hoc network, and the location data of the first monitoring device includes the positioning position data of the first monitoring device. In S400, according to the first A step including:
[0093] S902. The first monitoring device sends positioning data to the second monitoring device in the ad hoc network.
[0094] S903. The second monitoring device in the ad hoc network measures the angle of arrival of the positioning data.
[0095] S904. The second monitoring device in the ad hoc network sends the angle of arrival and the location data of the second monitoring device to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com