Multi-level secret sharing method for calculating safety under standard model and resisting memory leak
A standard model and memory leak technology, applied in computer security devices, calculations, instruments, etc., can solve problems such as inability to construct instances
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
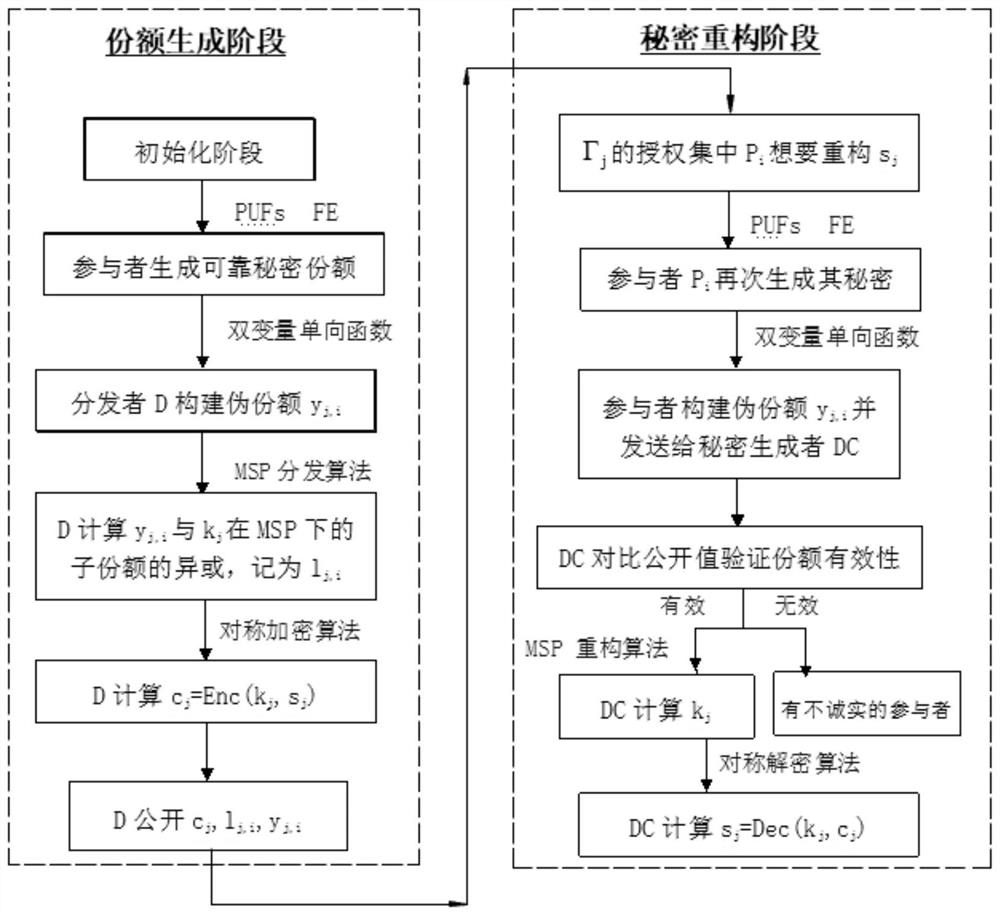
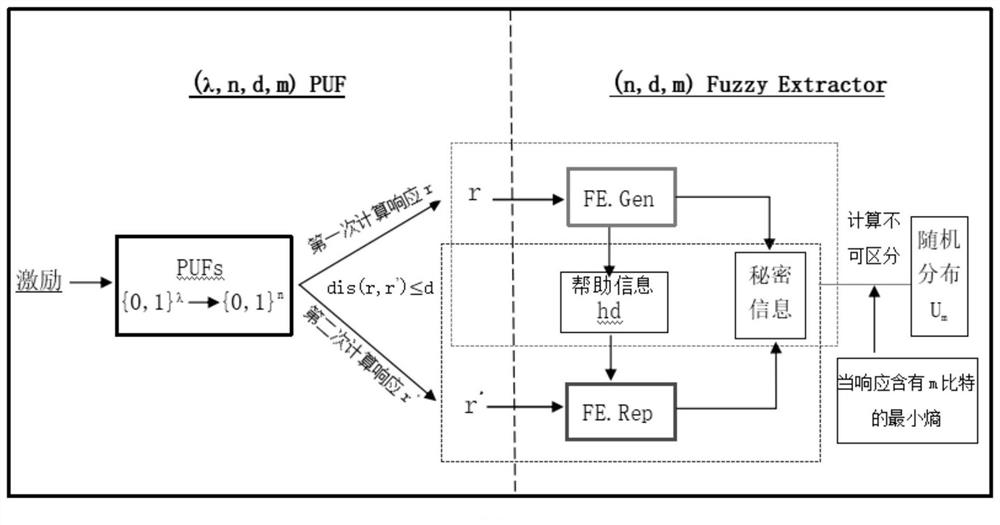
[0049] Please refer to Figure 1-3 , this embodiment provides a computationally secure multi-level secret sharing method against memory leaks under the standard model, using physical unclonable functions and fuzzy extractors to extract the same random and uniformly distributed strings to generate reliable secret shares.
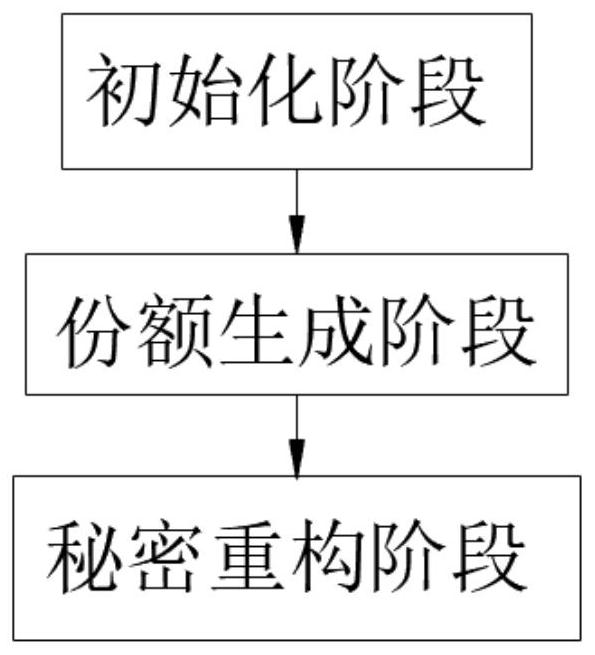
[0050] Please refer to figure 1 , figure 1 It is a flowchart of an embodiment of the multi-level secret sharing method that is computationally secure against memory leaks under the standard model in the present invention. In some embodiments of the present invention, the multi-level secret sharing method that is computationally secure against memory leaks under the standard model method, the extraction method includes: an initialization phase, a share generation phase and a secret reconstruction phase.
[0051] Please refer to figure 2 and image 3 , figure 2 It is a flow chart of another embodiment of the multi-level secret sharing method that is comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com