Network attack path prediction method based on attacker characteristic indexes
An attack path and network attack technology, applied in the field of network security, can solve problems such as practical limitations, inability to predict attack behavior, and inability to analyze network vulnerabilities, and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] In order to enable those skilled in the art to better understand the solutions of the present application, the technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application.
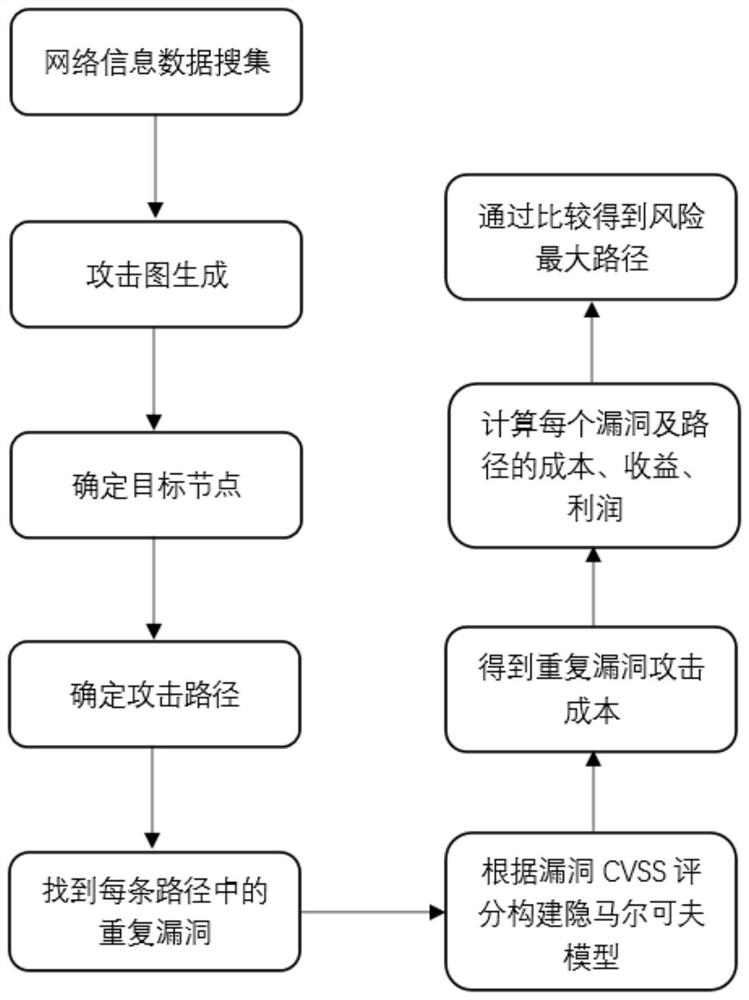
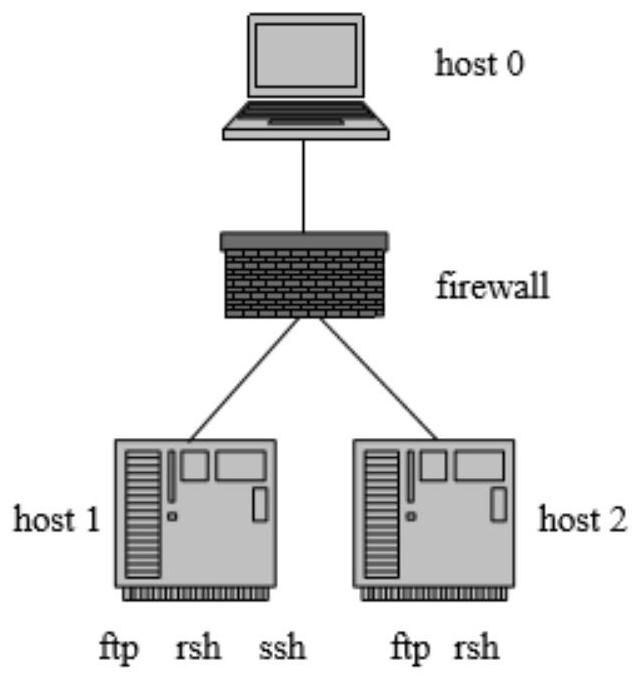
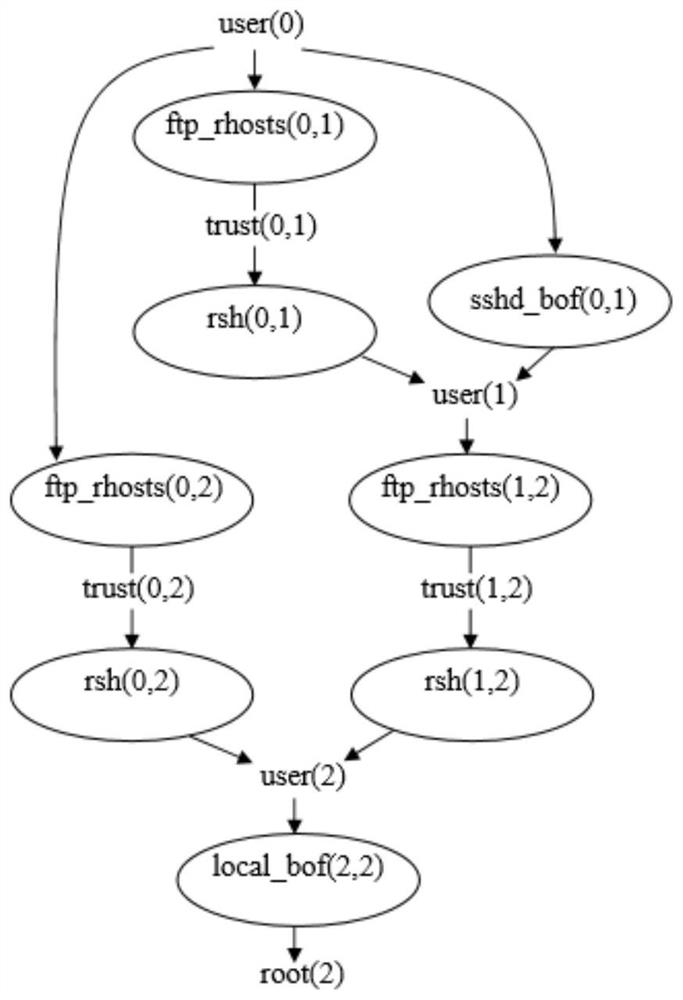
[0058] Based on the attack graph model, the present invention proposes a path quantification index with characteristics such as the attacker's behavior intention as the main research object, and uses the quantization index to predict the attack path in the attack graph. Since the real network environment and attack process of the attacker's attack are fully considered, the present invention can more accurately predict the attack path that the attacker may take. The main implementation steps of the present invention are as follows: firstly, scan the host computer in the network system and its services and loopholes, and use MulVAL to automatically generate the attack grap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com