LDoS attack detection and mitigation scheme based on ensemble learning and peak searching algorithm
An attack detection and integrated learning technology, applied in integrated learning, transmission systems, electrical components, etc., can solve the problems that normal users cannot effectively access the server, are not suitable for big data, and have weak real-time performance, so as to alleviate adverse effects, improve Real-time and ability to process big data, the effect of low time and space complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040]The present invention will be further described below in conjunction with the accompanying drawings.
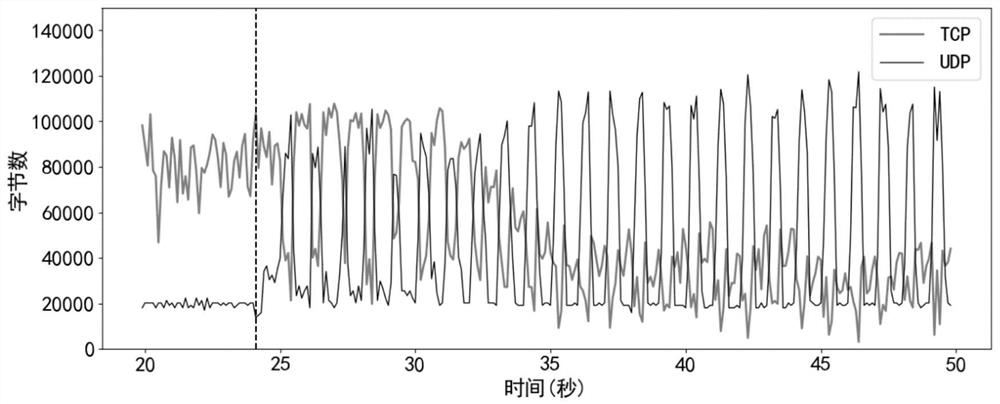
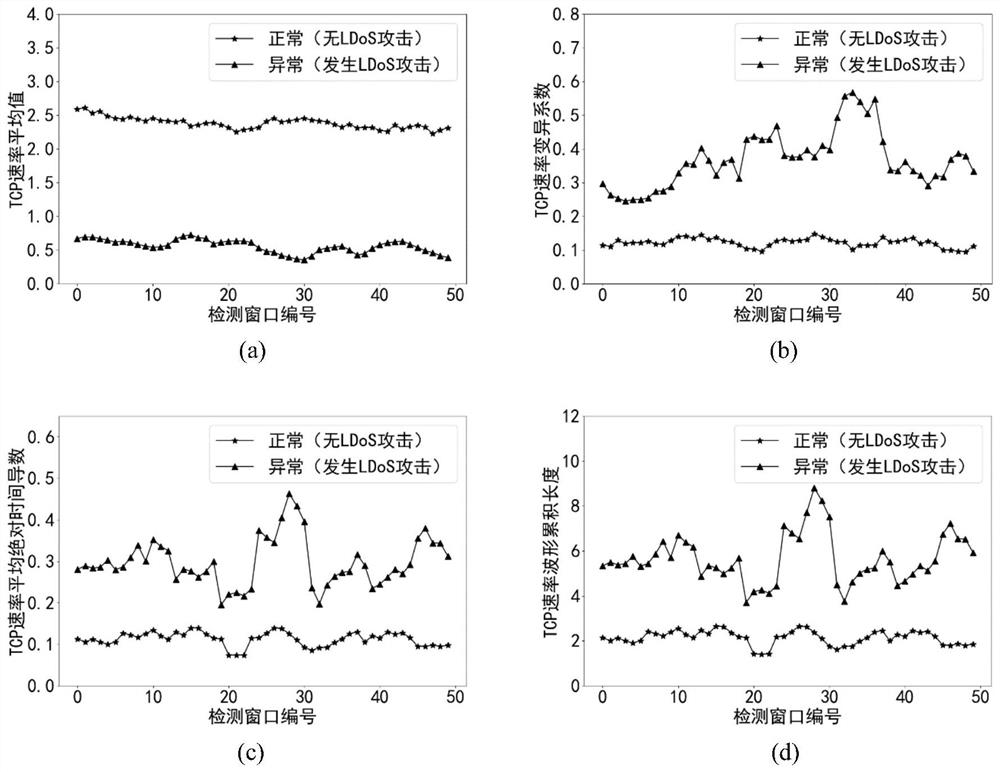
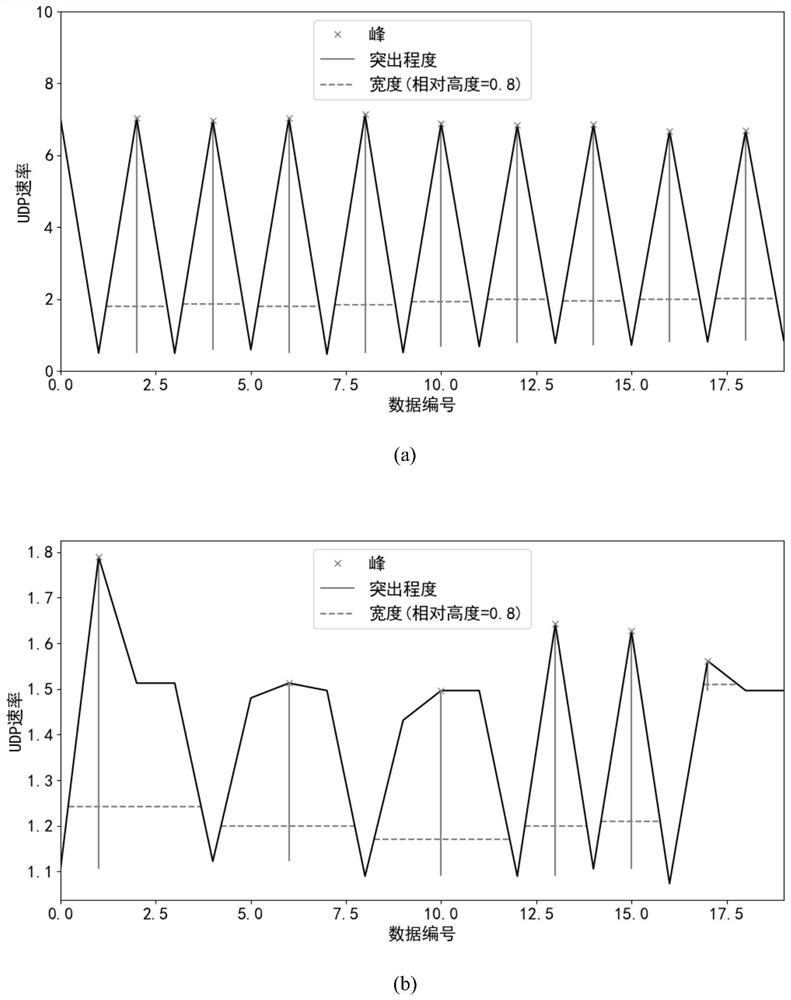
[0041] Such as Figure 5 As shown, the algorithm flow of the LDoS attack detection and mitigation scheme based on ensemble learning and peak-finding algorithm mainly includes four steps: data sampling, feature calculation, attack detection and attack mitigation. The data sampling step includes two parts: training data sampling and test data sampling. The training data obtained by sampling is divided into multiple detection windows based on the sliding window algorithm, and the detection windows are marked. The marks are divided into normal and abnormal, and the test data is based on the sliding window algorithm. The detection window is obtained by sampling in real time. The characteristic calculating step calculates the characteristic of the flow in the detection window according to the formula. The attack detection step trains an ensemble learning classifier accordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com